An In-Depth Look at Yanluowang Ransomware
Executive Summary
United States organizations within the financial sector are currently being attacked by a recently discovered ransomware operation named, Yanluowang. The ransomware operation is highly experienced with ransomware-as-a-service (RaaS) and could be linked to veteran RaaS groups, Fivehands and Thieflock. Although the group is primarily focused on attacking organizations within the financial sector, they have also targeted companies in manufacturing, IT services, consultancy, and engineering. Let’s take a look at Yanluowang’s techniques, tactics, and how they may be connected to Fivehands and Thieflock.
Important Note: As of now, the ransomware gang is named Yanluowang, as well as their ransomware. Therefore, the name Yanluowang will be used interchangeably throughout this report.
who is yanluowang?
In October 2021, Symantec’s Threat Hunter Team, a division of Broadcom Software, discovered that Yanluowang ransomware was actively being used by a threat actor who was seen attacking U.S. corporations since at least August 2021. What was interesting about the attack was that many of the tools, tactics, and procedures (TTPs) used were previously used by ransomware threat actor, Thieflock. Most analysts assumed that the threat actor using Yanluowang must be an affiliate of Thieflock who shifted allegiances. Although Yanluowang attempted to attack a large organization in October 2021 by deploying ransomware, they were not successful due to the ransomware being somewhat underdeveloped.
Techniques & Tactics of yanluowang
According to Symantec, their Threat Hunter Team initially discovered the use of AdFind, a legitimate command-line Active Directory query tool, on the undisclosed target’s network. Ransomware attackers often use AdFind as a reconnaissance tool. The tool also equipped attackers with resources that they needed for lateral movement by way of Active Directory. Days after discovering the suspicious use of AdFind, attackers attempted to deploy Yanluowang ransomware.
Through research, Symantec observed the following precursor tools carrying out the below actions:
- Creates a .txt file with the number of remote machines to check in the command line
- Uses Windows Management Instrumentation (WMI) to get a list of processes running on the remote machines listed in the .txt file
- Logs all the processes and remote machine names to processes.txt
After Yanluowang is deployed, it carries out the following actions:
- Stops all hypervisor virtual machines running on the compromised computer
- Ends processes listed in processes.txt, which includes SQL and back-up solution Veeam
- Encrypts files on the compromised computer and appends each file with the .yanluowang extension
- Drops a ransom note named README.txt on the compromised computer
After further research, Symantec found that most of the time, the threat actors behind Yanluowang used PowerShell to download tools to compromised systems, using BazarLoader to assist in reconnaissance. They then enable RDP via registry so they can enable remote access. ConnectWise (a remote access tool) is deployed after attackers gain initial access.
AdFind and SoftPerfect Network Scanner (netscan.exe – a tool used for discovery of hostnames and network services) is used to perform lateral movement and identify systems of interest. The next phase of Yanluowang’s attack is credential theft by way of credential-stealing tools. These tools include:
- GrabFF: A tool that can dump passwords from Firefox
- GrabChrome: A tool that can dump passwords from Chrome
- BrowserPassView: A tool that can dump passwords from Internet Explorer and a number of other browsers
Also, a number of open-source tools are used like KeeThief – a PowerShell script that copies the master key from KeePass. Yanluowang also uses customized versions of open-source credential dumping tools (secretdump.exe), which also aid in dumping credentials from the registry. Cobalt Strike Beacon was also seen deployed against at least one targeted organization.
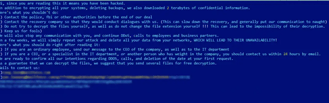
Image 1: Yanluowang Ransom Note
Source: Symantec
Additionally, the threat actors behind Yanluowang leave behind a ransom note that warns victims not to contact law enforcement or ransomware negotiation firms. If they do, the attackers will conduct a distributed denial of service (DDoS) attack and make “calls to employees and business partners”. They’ve also threatened to repeat the attack in a matter of weeks and delete their victim’s data.
how yanluowang could be connected to thieflock and fivehands
Many speculate that Yanluowang could be connected to Thieflock and Fivehands. After researchers looked into the tactics and techniques that Yanluowang uses, they noticed a possible connection to older attacks with Thieflock, which is a ransomware operation developed by the Fivehands ransomware group. Fivehands is a ransomware variant that has been used to steal information, obfuscate files, accomplish network discovery, and accomplish credential access. As of April 2021, Fivehands was used by threat actor UNC2447 to exploit a SonicWall software flaw before the flaw was fixed.
While Fivehands is relatively new to the ransomware scene, it is being linked to Yanluowang by researchers. When UNC2447 exploited SonicWall, they showed advanced capabilities to evade detection and minimize post-intrusion forensics – like Yanluowang. Also, Yanluowang relies on several tactics and techniques found in Fivehands ransomware such as using GrabFF , SoftPerfect Network Scanner, and the S3 browser and Cent browser to upload and download data.
Researchers and analysts are curious about the connection between Yanluowang, Thieflock, and Fivehands, but right now, there isn’t a ton of evidence confirming a connection between Yanluowang, Thieflock, and Fivehands. Researchers still stand firm on their belief that the cyber criminals behind Yanluowang could just have a former affiliate of Thieflock in their arsenal.
double extortion
Because law enforcement is cracking down on ransomware operations, there are many new variants that have surfaced over the year. Many new strains have been used in double-extortion attacks where attackers encrypt stolen data and threaten to leak it if demands aren’t honored. In October alone, 314 organizations worldwide became the victims of double-extortion attacks with the worst offenders being Conti, LockBit, Hive, and BlackMatter.
Yanluowang’s goal is to locate and steal as much information (passwords, usernames, etc.) as possible to use against their victims. Their ransom note indicates the threat of double extortion if victims don’t comply with their demands. If organizations are going to protect themselves from threat actors like Yanluowang who will stop at nothing for financial gain, it’s important to become familiar with their tactics and techniques.
how avertium is protecting our clients
Research from the U.S. Financial Crimes Enforcement Network (FinCEN) discovered that payments linked to ransomware attacks amount to $590 million in 2021. This exceeds the total for 2020 and is continuing to rise. Because the cyber landscape is always changing, it’s imperative to be aware of new cyber attack strategies and techniques. Avertium is here to keep you informed and to keep your organization safe. We recommend the following for the best protection against ransomware attacks:
- Avertium offers vulnerability management as a service (Vulnerability Management) to remove any unnecessary applications and implementing XDR tools to prevent ransomware and phishing attacks. Include an EDR, MDR or XDR strategy to stop ransomware before it spreads. You should also include a Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- It’s also recommended by Avertium and the FBI that your business require multi-factor authentication to remotely access networks. Implementing network segmentation and filtering network traffic to stop phishing emails from reaching victims is also helpful.
- Reach out to your Service Delivery Manager or Account Executive if you need assistance applying any of the above recommendations.
avertium's recommendations
Recommendations from Avertium and our partner, Advanced Intelligence:
- Prevent lateral movement by implementing network hierarchy protocols with network segregation and decentralization.
- Use whitelisting tools to audit or block command-line interpreters (AppLocker).
- Rclone and other data exfiltration command-line interface activities can be captured through correct logging of process execution with command-line arguments.
- Have security protocols in place for Veeam to avoid account takeover. Enabled backups decrease Hive’s ransom demands and can lead to data recovery without you having to pay them.
- Externally exposed RDPs.
- Relying on outdated tools and point solutions will compromise your network or system. Better technology exists to detect complex attacks like Hive ransomware.
If your organization is impacted by a ransomware attack, the FBI and CISA recommend the following:
- Isolate the infected system.
- Turn off other computers and devices.
- Secure your backups.
MITRE TTPs:
Yanluowang
- [001] Impair Defenses: Disable or Modify Tools
- [001] Indicator Removal on Host: Clear Windows Event Logs
- [T1486] Data Encrypted for Impact
- [T1133] External Remote Services
- [T1598] Phishing for Information
Fivehands
- [T1486] Data Encrypted for Impact
- [001] Local Groups Discovery
- [002] Domain Groups Discovery
- [003] Cloud Groups Discovery
Indicators of Compromise (IoCs):
Yanluowang
- d11793433065633b84567de403c1989640a07c9a399dd2753aaf118891ce791c
- 49d828087ca77abc8d3ac2e4719719ca48578b265bbb632a1a7a36560ec47f2d
- 2c2513e17a23676495f793584d7165900130ed4e8cccf72d9d20078e27770e04
- a710f573f73c163d54c95b4175706329db3ed89cd9337c583d0bb24b6a384789
- 2c2513e17a23676495f793584d7165900130ed4e8cccf72d9d20078e27770e04
- 43f8a66d3f3f1ba574bc932a7bc8e5886fbeeab0b279d1dea654d7119e80a494
- 9aa1f37517458d635eae4f9b43cb4770880ea0ee171e7e4ad155bbdee0cbe732
- 85fb8a930fa7f4c32c8af86aa204eb4ea4ae404e670a8be17e7ae0adf37a9e2e
- e4942fde1cd7f2fcfb522090fd16298bce247295fe99182aecf7b10be3f5dc53
- fe38912d64f6d196ac70673cd2edbdbc1a63e494a2d7903546a6d3afa39dc5c4
- c77ff8e3804414618abeae394d3003c4bb65a43d69c57c295f443aeb14eaa447
- 2fc5bf9edcfa19d48e235315e8f571638c99a1220be867e24f3965328fe94a03
- 4ff503258e23d609e0484ee5df70a1db080875272ab6b4db31463d93ebc3c6dd
- 1c543ea5c50ef8b0b42f835970fa5f553c2ae5c308d2692b51fb476173653cb3
- 0b9219328ebf065db9b26c9a189d72c7d0d9c39eb35e9fd2a5fefa54a7f853e4
- b556d90b30f217d5ef20ebe3f15cce6382c4199e900b5ad2262a751909da1b34
- 5e03cea2e3b875fdbf1c142b269470a9e728bcfba1f13f4644dcc06d10de8fb4
- 49d828087ca77abc8d3ac2e4719719ca48578b265bbb632a1a7a36560ec47f2d
- Myeeducationplus[.com]
- 53.46.115
Fivehands
- 132071dc69b875d239f133984655a26a
- 1f6495ea7606a15daa79be93070159a8
- 4d3d3919dda002511e03310c49b7b47f
- 9cfd524557c76097bbf6cf493b351a04
- abb0fbecd6ac93d3271fc34269a1fb68
- e0c3c5376abe535e255bd8893540abc4
- 398d769e0d478175acbdbe9a790b2f6982110e8d
- ae16aea46540f2013c92e2a9ba3310824c949554
- b16a1eb8bc2e5d4ded04bfaa9ee2b861ead143ba
- e50d9e3bd91908e13a26b3e23edeaf577fb3a095
- f9667504eb648527038adc3932d4c5b7c8443a65
- fc09069b25f42cb8dc6960eea76980a0ea8a768c
- fdf9b1098480dd4145d7d39dc1b75fb6180e09ec
- 18229920a45130f00539405fecab500d8010ef93856e1c5bcabf5aa5532b3311
- 2703aba98d6ecf0bf0b5aafe70edc4bc14d223a11021990bfb10acf5641d3a12
- 3337e3875b05e0bfba69ab926532e3f179e8cfbf162ebb60ce58a0281437a7ef
- 495a0ccc38fb8f22b48025f030617978cf5fdc3df3fed32b1410ad47747ae177
- 4de1bd4b1bb28ed0897b9d3c5d16a4b1442c7f53cb389cbed82af189696d3f40
- 5608c12872229acd84f33bf6c667a1b43d112594b2b5f47f923d631bcce6090c
- 5f312e137beb1ce75f8fdf03a59e1b3cba3dc57ccc16e48daee3ee52c08fa149
- 7d57e0ba8b36ec221b16807ce4e13a1125d53922fa50c3827a5ebd6811736ffd
- 911a88fe16efca24206f1786242615596e67a9336bc670c1e44a33727987d886
- a710f573f73c163d54c95b4175706329db3ed89cd9337c583d0bb24b6a384789
- a7f5097c0d991c9bbd5f2694ec8c9b484e2ab583d362c42c30556f1271cc8aaa
- bfc50bf40aae3b41d77169fba45c332b8c60406b403af647f1bb083918a33b9e
- c0a214a60daac6f0ba01ce9128d42bb2d8e81909f4b87963de340ab8627a6b0b
- c5a1dbb49ff72a69ac7c52b18e57a21527bc381077b1cea12c3a40e9e98ae6cd
- ccacf4658ae778d02e4e55cd161b5a0772eb8b8eee62fed34e2d8f11db2cc4bc
- d3d5e5a8a40f34fc8d89b2d74d89a4b101d8b95a79e990e3b4161282aa6aca32
- dec8655cdd7214daf9579ef481d0b0c6ed8120c120d3bd8ec27cb6e1874eb291
- e4b67b8ffcc1ed95d3ff26622ab4c67a329f76bd76d0f523f5986e67969354b7
- feticost[.com]
- operond[.com]
terms
DDoS - disruption to internet-based services that can make any internet connected machine unavailable to perform its intended purpose.
PowerShell – used for automating the management of systems. Can also be used to build, test, and deploy solutions, often in CI/CD environments.
Ransomware - malicious software that infects a device and stops users from accessing data and files until a ransom is paid.
RDP - technical standard for using a desktop computer remotely.
Supporting Documentation
Yanluowang: Further Insights on New Ransomware Threat | Symantec Blogs (security.com)
New Yanluowang Ransomware Used in Targeted Attacks | Symantec Blogs (security.com)
Yanluowang ransomware operation matures with experienced affiliates (bleepingcomputer.com)
FiveHands Ransomware Overview (avertium.com)
Zero-Day Attacks Threaten Healthcare Cybersecurity (healthitsecurity.com)
Hacking group exploited SonicWall zero-day for ransomware attacks, FireEye says (cyberscoop.com)
New Ransomware Variant Could Become Next Big Threat (darkreading.com)
What is PowerShell? - PowerShell | Microsoft Docs
APPENDIX II: Disclaimer
This document and its contents do not constitute and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of the Client's compliance with any law, regulation, or standard.