New Phishing Campaign uses Morse Code to avoid detection
Overview of TIR-20210221
This report is about a new phishing campaign that uses a unique method of obfuscation to avoid detection by traditional security appliances. The method of obfuscation is Morse code which is used to hide URLs. Given its ability to successfully bypass security tooling this campaign is quite dangerous if a user is socially engineered.
Tactics, Techniques, and Procedures
Before an attack begins the target is selected carefully and often is someone of importance within the organization. When observing the email and any associated attachments, the malicious URL is hidden using dots and dashes. The attacker sends the email with an attached HTML file that, when opened with a text editor presents JavaScript with Morse code. The HTML attachment is usually named to look like an Invoice with a fake company name such as avertium_invoice_ 1308._xlsx.hTML.
The encoded text looks like this:
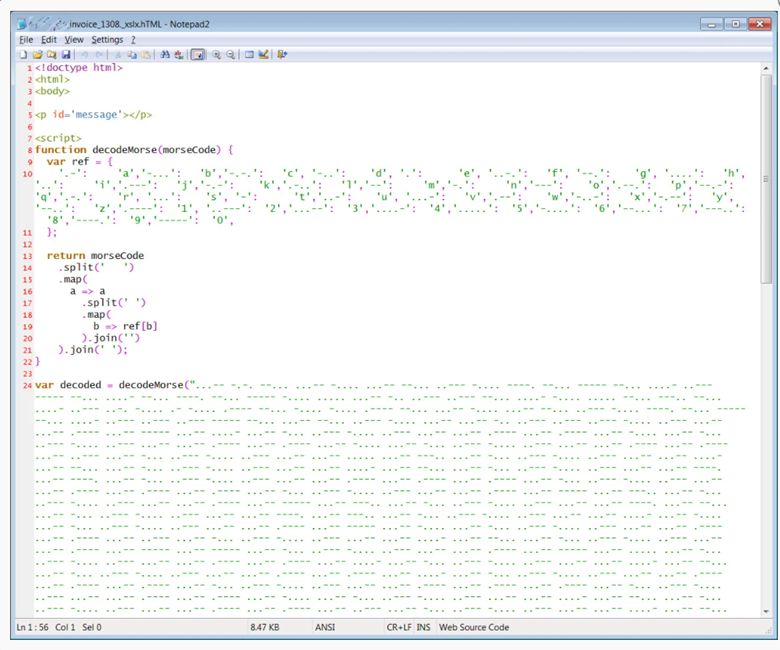
The file pulls external elements from the encoded malicious URL which then displays the phishing page if the file is opened with no editing software. The web page is asking for the user’s Office365 credentials saying that the session has timed out. If the user enters their Active Directory credentials into the page they are sent off to the bad actor. The web page comes complete with the recipient’s organization logo, but if the logo cannot be found it will provide the generic Office 365 one.
Business Unit Impact
- May lead to the loss of credentials which can be abused.
- Could provide lateral movement opportunities with minimal effort depending on the user’s level of access.
- Has the potential to allow for a network-wide compromise by a highly resourceful threat actor.
Our Recommendations
It is highly encouraged that you block any attachment file names with a double extension using the mail security gateway. Consider ensuring that Windows file extensions are enabled to help users spot a phishing attempt. Invest in routine security awareness training that includes a robust section on avoiding social engineering situations.
Sources
Supporting Documentation
MITRE Mapping(s)
- https://attack.mitre.org/techniques/T1566/
- https://attack.mitre.org/techniques/T1598/001/
- https://attack.mitre.org/techniques/T1132/002/
- https://attack.mitre.org/tactics/TA0006/
Note: The Avertium Threat Report analyzes one current threat that has been shared by threat intelligence networks across the globe. Used internally by the Avertium CyberOps Team, this report will outline a “top-of-mind” threat and how it ought to be addressed accordingly.
This informed analysis is based on the latest data available.