The Rise of RaaS Gangs + What You Need to Know
Since the beginning of the global pandemic, the FBI’s Internet Crime Complaint Center (IC3) has seen a 300-400% increase in daily cybersecurity complaints - many of which are ransomware-related - as both domestic and international hackers look to take advantage of Americans' move to less secure, remote working environments.
As we move into 2021, ransomware attacks continue to rise and are increasingly executed through Ransomware as a Service (RaaS) gangs. With few primary bad actors developing ransomware code, then working with ransomware gangs (and in some cases botnets) to proliferate the malware on a Software as a Service (SaaS)-like model (hence, RaaS), RaaS has transformed a once-complex hacking operation into a real, for-profit business.
As a result, ransomware is now more accessible and more efficient for RaaS gangs to spread across the globe in 2021.
Related Reading: Threat Focus: What Is Ransomware-as-a-Service?
Noteworthy Ransomware as a Service (RaaS) Gangs
Thanks to emerging RaaS gangs, the same PC that was behind a corporate firewall and web filter before is no longer. With more businesses moving to work-from-home environments, the attack surface has grown exponentially for these attackers.
Targeting entities within the private sector, national and local government, as well as critical infrastructure, RaaS gangs use lateral movement to target sensitive information and spread ransomware through entire networks. Once inside, they threaten to sell or release exfiltrated data or authentication information if victims do not pay, in addition to publicly identifying and shaming victims as a secondary means of extortion.
Beyond that, ransomware gangs have increasingly employed strategies that render the process of restoration and remediation, such as removing system backups, making it more difficult or impossible for affected organizations to recover.
So… who are the major RaaS Gangs and what do we need to know about them?
The short answer is that there are many and the list constantly changes. Some RaaS gangs are taken down by law enforcement and some morph themselves to evade detection. That said, let’s take a closer look at a few noteworthy players...
Related Reading: Ransomware Prevention to Incident Response
Doppelpaymer
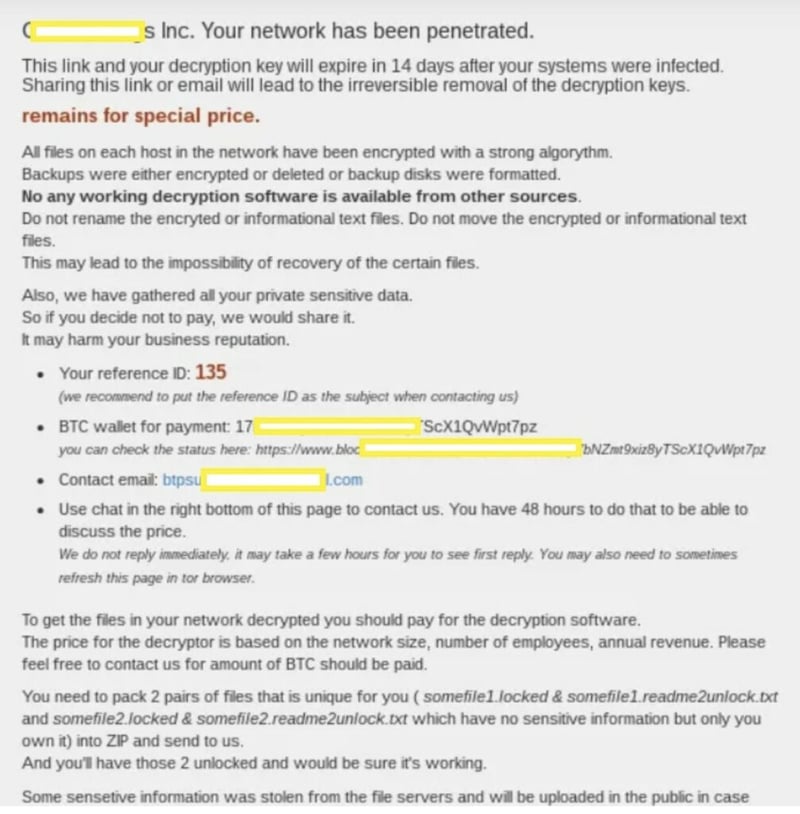
Doppelpaymer ransom note
Doppelpaymer Background + Tactics
The FBI reports that, in addition to sending the obligatory ransom note, the Doppelpaymer Ransomware Gang has been cold calling its victims, sometimes even threatening to send representatives to people’s homes if they don’t pay.
Avertium’s threat intelligence uncovered quite a bit of engineering built into this code. It seems the samples can differ in that obfuscation techniques are built in to avoid detection by Sandbox, or APT Technologies.
Doppelpaymer Impact
According to a 2021 Chainalysis Report, Doppelpaymer accrued somewhere in the neighborhood of $50m in 2020 by extorting its victims. The reported total earned by ransomware gangs in 2020 was somewhere close to $350m, so in terms of revenue, Doppelpaymer was one of the top earners.
Revil
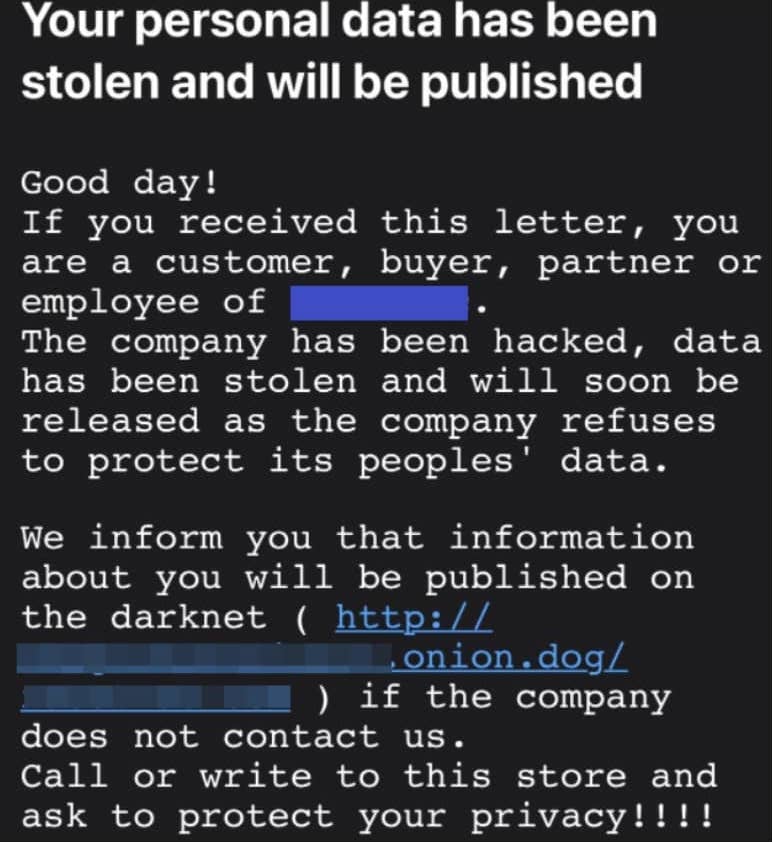
Source: Krebsonsecurity.com
Revil Background + Tactics
Revil is a criminal for-profit organization, having some success with high-profile attacks against targets such as former President Trump, singer Lady Gaga, and other prominent figures.
While Revil's origin is not 100% clear, many suspect that the ransomware gang operates in Russia since their targets typically reside outside of the Russian / former Soviet Bloc Area.
Recently, Revil launched a “recruitment drive” by depositing $1m in bitcoin on a Russian Speaking Hacker website. Just like a typical SaaS company’s “partner program”, Revil aims to expand its reach via affiliates, splitting the proceeds of successful hacks with their counterparts. Upon recent speculation, this could be a result of Revil purchasing the source code for the trojan KPOT for only $6,500 in a recent online auction reported at ZDnet.
The Revil group is also unique in that they contact the customers and partners of their victim’s company. Think about if you were the third party in this instance... Would you feel secure knowing your sensitive partnership data could potentially be exposed due to this ransomware breach?
Revil Impact
With respect to the noteworthy targets of President Trump and Lady Gaga, no confirmation on whether ransoms were paid or not could be substantiated.
That said, according to a March 2021 BleepingComputer report, as of late, a Revil collaborator claimed a successful attack against Acer Corporation, linked to the recent Microsoft Exchange Server Data Breach. It is said that at first, a $50m, then $100m ransom was to be paid to retrieve sensitive data.
Netwalker
Netwalker Background + Tactics
Although Netwalker was disrupted by U.S. and Bulgarian authorities recently, this gang was one of the 2020s most active ransomware gangs. It’s believed that Netwalker got its start in 2019, likely somewhere in Russia. The main method of infection was through phishing, presented with malicious links and executables infecting systems of unsuspecting users.
Read Related Threat Report: Netwalker Ransomware Offered as Ransomware-as-a-Service Creating Increased Prevalence
On Russian dark web message boards, the admin had invited interested cybercriminals to join as collaborators to spread the malware. They then cooperated with other ransomware gangs, or affiliates, that carried out their RaaS attacks - often partnering with botnet operators to spread the malware faster and wider. These gangs would split ransom funds with the creators or administrators from each fruitful attack.
Rendering itself as a reflective DLL injection, this code is different from others, as it is a fileless attack. Because of this, it makes the attack more difficult to trace and a more formidable task for security analysts to investigate. In short, it affects several critical .dlls on the system, ultimately placing ransomware DLL in the memory space explorer.exe, dropping ransom notes in several folders within the system with the goal of extorting funds from its victim.
Netwalker Impact
According to US authorities, NetWalker has impacted at least 305 victims from 27 different countries, including 203 in the U.S. It’s difficult to show exact revenue numbers for these groups, as many successful attacks go unreported for various reasons. That said, according to a Chainalysis 2021 Estimate, Netwalker may have brought in as much as $46m in revenue in Jan 2021 - putting it in the top 5 grossing ransomware strains.
The Fight Against Ransomware
While ransomware is a very real threat, there have been some triumphs in recent months.
We saw Microsoft take down most of the servers belonging to TrickBot, a large botnet composed of at least one million infected devices that operators would regularly rent to ransomware gangs.
Emotet, another prominent global botnet used to distribute ransomware and other malware was taken down by a worldwide crime-fighting effort composed of Europol, the FBI, and the UK National Crime Agency. These activities by law enforcement resulted in some of the most significant disruptions of cyber-criminal operations in recent years.
If you are a victim of ransomware, there are several options:
- Contact your local FBI field office to request assistance, or submit a tip online.
- File a report with the FBI’s Internet Crime Complaint Center (IC3).
- Report it immediately to CISA at www.us-cert.gov/report, or Secret Service Field Office.
- For immediate mitigation assistance, Avertium DFIR experts can work with your team to tackle cyber emergencies. Contact us here.
The FBI does not support paying a ransom in response to a ransomware attack since doing so doesn’t guarantee that you or your organization will get any data back. On top of that, it also encourages perpetrators to target more victims and offers an incentive for others to get involved in this type of illegal activity.
Ransomware Resources:
- 2021 Alerts on Ransomware Attacks
- 2021 Chainalysis Crypto Crime Report
- How to Leverage Your SIEM to Detect and Respond to Ransomware
Read Related Blog: 5 Ways to Prevent Ransomware
CONTAIN + COMBAT RANSOMWARE VIA ZTNA
With the prevalence, severity, and sophistication of cybersecurity attacks growing by the day, businesses of all types and sizes are scrambling to protect themselves. By dividing your network into smaller segment chunks, you limit the lateral spread of ransomware/malware. Patient Zero may be infected, but the rest of the network should be spared as the malware looks to proliferate.