Cybersecurity Best Practices & Principles [Updated 2022]
Updated September 2022
Executive Summary of cybersecurity best practices
In order to use more sophisticated cyber security tools, organizations need to have a decent understanding of cyber security best practices. Over the years, businesses both large and small have become victims of cyber-attacks that could have been prevented if basic cyber security principles, awareness, and best practices were followed. Some of those best practices include patching devices, inventory control, managing backups and data recovery, securing VPNs for remote work environments, and managing default passwords.
Today, remote work environments have become common, and with those environments comes an increase in cyber threats. According to a 2021 Public Sector Cybersecurity Survey report published by SolarWinds, the public sector is now facing an increasing risk of external cyberattacks due to security measures failing to keep up with the fast pace of cyber threat environments. The Public Sector Cyber Security survey noted that the hacking community (56%) is the largest source of security threats within the public sector, followed by careless and untrained insiders (52%), as well as foreign governments (47%).
Furthermore, the survey found that the public sector is especially concerned about increases in the types of security breaches they experienced – malware (65%), ransomware (66%), and phishing (63%). This is the first time in five years that insider carelessness or lack of employee training is not the biggest threat to the public sector. This means that IT threats have increased, but the ability to detect and remediate those threats has not, thus leaving organizations within the public sector vulnerable.
Developing good security hygiene could mean all the difference if your organization is attacked by a threat actor. Small security lapses lead to attacks and attacks lead to turmoil within your organization’s routine business practices. Let’s take a look at how following basic cyber security principles could help keep your organization from becoming the next big headline.
patching devices
- What it is: When cybersecurity professionals talk about patching devices, they are simply saying that you need to apply updates to your software as those updates become available. Common areas that will need patches include operating systems, applications, and embedded systems (like network equipment).
- Why it’s important: When a vulnerability is found after the release of a piece of software, a patch can be used to remediate it. Patching helps ensure that assets in your environment are not vulnerable to attackers.
- How it can be implemented/utilized: It’s important to first assess your environment to see exactly where your existing gaps are: this process includes inspecting your current security controls, reporting vulnerabilities in your ecosystem, and any other analysis depending on your environment. Once you’ve prioritized the discrepancies in your security landscape and tested your patches, you can begin patching - ideally, this would be done in small doses/batches so you can ensure everything is working as intended.
- Example case: A great example of how patching can help save your organization a lot of heartaches is the 2017 Equifax data breach. This breach affected over 145 million people and was one of the largest breaches of this kind in history. The breach was caused when an employee didn’t apply the most recent patch for Apache Struts – a patch that was available for two months before the company was breached. Another example is the 2012 data breach of Nationwide Mutual Insurance. The insurance company was breached when a vulnerability found in a web application was left unpatched for three years. The data breach exposed the data of 1.27 million and the company had to pay $5.5 million in a settlement.
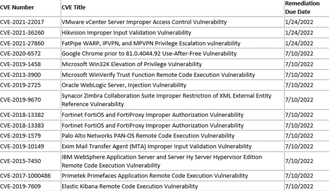
Image 1: 15 Vulnerabilities Added to CISA's Catalog
Source: CISA
Recently, CISA (Cybersecurity and Infrastructure Security Agency) added 15 known exploited vulnerabilities to their catalog. Most of the vulnerabilities on this list are two to three years old, which means that if these vulnerabilities are still being exploited, organizations are not being diligent with patching devices. Patching out-of-date and vulnerable software is crucial and should be done as soon as an update is available.
Unfortunately, many organizations fall into the habit of not prioritizing patching. Why? Simply because patching can be quite inconvenient and time-consuming. However, there is nothing more inconvenient than having your systems and networks compromised by a threat actor who took advantage of your negligence.
inventory control
- What it is: Actively managing your organization’s inventory (end-user devices, network devices, non-computing/IoT devices, and servers) is crucial to keeping your environment safe.
- Why it’s important: Assessing inventory regularly should be the foundation of every organization’s cyber security program. Because devices are constantly added and retired, and employees/users frequently come and go, it’s important to know what you have and how it’s being used.
-
How it can be implemented / utilized: If an organization doesn’t have an accurate and up-to-date asset inventory, trying to manage compliance and cyber risk will be extremely difficult. If you aren’t sure if your organization is guilty of letting inventory fall to the wayside, ask yourself these questions:
-
Have I updated my inventory list across my business or company?
-
Can I see (in real-time) the state of our overall security posture at any given minute?
-
Do I know what my asset inventory management program is, and does it help keep my organization safe?
-
Do I know which assets are critical for business operations and which ones may be less important?
If you couldn’t answer these questions fluidly, then you have a problem. Assets are like moving targets and managing their needs to be developed into a seamless process. Full visibility and control over all assets shouldn’t be optional.
Going through the initial process of accounting for every authorized/unauthorized device, application, software license, IoT, ICS, etc. can be tedious, but it’s worth it. There are cyber insurance companies who can make the process easier and can help you build a platform that allows you to discover your users, applications, and devices continuously and automatically, as well as the relationships between them. If your tools and processes work together to automatically discover and inventory the full range of your authorized IT assets, then you’ll be able to better understand and secure your asset inventory in real time.
A strong and robust security model begins with asset inventory management. Once you take this proactive approach, it will be easy to track and analyze your assets across attack vectors to identify those that are most likely compromised. Having all of your assets in the inventory means that they are readily available via real-time dashboards and are easy to search. Also, they can include automatic and continuous compliance supervisors that uncover rogue assets and unauthorized use.
managing backups & data recovery
- What it is: Managing backups and data recovery is another cyber security best practice that some organizations fall short on. Some organizations wait until they experience a data breach to start thinking about recovering their data via backups. While it can be relieving to know your data will more than likely be recovered, you really should be thinking about your backup and data recovery plan before being breached.
- Why it’s important: Backing up your data means that you have copies of your computer data on a hard drive – something that is offline.
- How it can be implemented/utilized: Some backup types include:
-
- Standard backups – these backups create copies of files from one or multiple systems across a network.
-
- System backups– these backups are copies of a system and may perform scheduled backups of files while having system backups for baseline configurations when new machines join the network.
-
- Incremental and differential backups – a differential backup will only backup files that have changed since the last backup, while an incremental backup will only backup the changed data in files. Incremental backups are considerably faster than differential backups.
In order to have a successful backup and data recovery process, your organization will need to have a clear backup strategy that includes defined data protection goals. This policy should outline what, when, and how data and systems will be backed up and restored should you become compromised. Also, it’s important to test your backups regularly to ensure they work.
- Example case: According to IBM, the average cost of a data breach in 2019 was $3.92 million, up 1.5% from 2018. The average cost was $150 for each record during that time frame. The U.S. has experienced the largest number of data breaches, followed closely by Canada and Germany.
What’s more interesting is that the average amount of time it takes for companies to realize that they’ve been breached is 197 days. Businesses with the right data breach recovery process contained their breach within 30 days and saved more than $1 million compared to companies that took longer than 30 days to intervene.
Sometimes, technology fails us, and we lose information, but most of the time we lose information due to malicious threat actors who manage to penetrate and circumvent backups. They either steal data for their own use, or strip businesses of their resources. One threat actor that is known for destroying backups is the ransomware gang, Conti. The threat actor mainly targets backup systems to guarantee that ransom payments are made.
Conti has been strategic in designing and deploying backup removal solutions, gaining access to backup user accounts with elevated privileges. After they gain access to these accounts, they are free to do anything they want with the backups they’ve infiltrated – including destroying, corrupting, and encrypting all data. This makes it extremely difficult or impossible to conduct a recovery procedure. We realize that keeping data secure comes with a hefty price tag, but price should be less of a concern when you run the risk of losing valuable data if you’re breached.
securing VPNs for remote work environments
-
What it is: Virtual private networks, or VPNs, are one of threat actors’ favorite entry points into a network. A VPN allows people to access the Internet just as they would be able to if they were connected to a private network. Securing VPNs provides effective security for organizations and can help keep certain resources hidden.
-
Why it’s important: Attackers gain access to networks if organizations don’t patch their VPNs and other externally facing devices. VPNs provide threat actors with a stable foothold onto target networks through the VPNs' internet exchange point (IXP). If an employee is connecting to a company’s VPN to access a company database that’s stored on a server, a threat actor who has infiltrated the IXP can monitor all data that passes through.
-
How it can be implemented / utilized: There are several reliable VPNs on the market, so once you choose the one that’s right for you, it’s simple to install and use. Usually, all it takes to set up your VPN is to download it onto your computer, sign in, and choose your server. Once you’re connected, continue to use the Internet as you normally would - with an added layer of anonymity and security.
-
Example case: VPNs establish encrypted connections between devices, but an attacker can’t monitor VPN-encrypted traffic from outside the VPN. All it takes is one compromised account or device for an attacker to gain access to a VPN and steal what should be gated data. In September 2021, it was reported that a threat actor leaked 500,000 Fortinet VPN login credentials from 87,000 devices over the course of two years. The culprit was a member of the ransomware gang, Babuk. Although the VPN vulnerability had already been patched, the stolen credentials were still valid.
Fortinet stated the attackers were able to obtain the credentials from systems that didn’t implement the patch. The vulnerability, tracked as CVE-2018-13379, is a path traversal vulnerability in Fortinet’s FortiOS SSL VPN web portal which allows unauthenticated users to read arbitrary files (including the sessions file).
Although it was never confirmed that the leaked credentials belonged to remote employees, we can only assume that some of them did. VPNs are virtual, which means that they are often given to remote workers to access company resources. Setting up identity and access management (IAM) solutions and secure web gateways could help keep remote employees secure by filtering content and preventing data from leaving your organization’s network.
managing default passwords
- What it is: Passwords should be unique, complex, and private - so default passwords that are pre-determined by the application, website, and organization should not be used past their initial login. Managing default passwords means updating your passwords to something that only you know and protecting them with a password management system.
- Why it’s important: Managing default passwords is basic in theory but complicated in practice. Most don’t consider updating passwords to be difficult to manage, but when a company has thousands of employees who are responsible for making sure they update their passwords and don’t re-use passwords, things can get tricky. It’s important for organizations to develop a password management system that has a secure way to store passwords and access them when required.
-
How it can be implemented/utilized: Password best practices include:
-
Never reveal a password to anyone
-
Different accounts need different passwords – don’t reuse!
-
Use multi-factor authentication – this adds another layer of protection
-
Long passwords are best – 16 characters or more
-
Your passwords should be hard to guess and easy to remember
- Use a password manager if you need to – Lastpass and Password Safe are great options
-
- Example case: Most cyber security professionals know the details surrounding the attack on Colonial Pipeline. The ransomware gang, DarkSide, launched a ransomware supply chain on the company in May 2021. The threat actor gained access to Colonial Pipeline’s virtual private network (VPN) account due to a single compromised password. The account that was compromised allowed employees to remotely access the company’s computer network. At the time of the attack, the account wasn’t in use but could still be used to access the fuel company’s network.
After the ransomware attack, researchers discovered that the password for the account was inside a batch of leaked passwords on the dark web. It’s suspected that the Colonial Pipeline employee probably re-used that password on another previously hacked account. The VPN account that was compromised, did not use multifactor authentication and it isn’t known how DarkSide obtained the correct username and password.
As a result of the attack, Colonial Pipeline had to shut down the fuel pipeline, leaving gas stations, businesses, and households without fuel. Additionally, the news of a cyber-attack made its rounds and people started panic buying which resulted in gas shortages along the east coast. DarkSide stole about 100 gigabytes of data from the company and threatened to leak it if they refused to pay a ransom. Colonial Pipeline ended up paying DarkSide $4.4 million in ransom.
Antivirus software
- What it is: A preventative data security tool that’s installed in computers to protect your system from unauthorized software like malware, ransomware, viruses, rootkits, spam, spyware, and more.
-
Why it’s important: It detects viruses and other threats that a human operator would otherwise miss. Without installing an antivirus system, you’re leaving the door open to malicious hackers and software. A computer that’s infected with a virus:
-
Performs more slowly
-
Crashes / fail more frequently
-
Loses data / deletes files
-
Is unable to perform regular tasks like using the internet or accessing apps
- How it can be implemented / utilized: It’s simple: you simply download an antivirus program of your choice and, without any maintenance from you, blocks incoming viruses and threats.
Multi-Factor Authentication
- What it is: Multifactor authentication is a stronger alternative to regular passwords that requires an external verification in order for the user to log in.
-
Why it’s important: Authentication in any form relies on one of three things: something you know (a password or PIN), something you have (a pass card or key), or something you are (fingerprint or retina). MFA adds a layer of security by requiring at least TWO of these things to be present before granting access - making unauthorized access significantly harder.
-
How it can be implemented / utilized: There are several forms of MFA that an organization can adopt - the primary types include:
-
A text / call to the user’s phone
-
Entering a code or answering security questions
-
A notification to an external app
-
Biometrics like fingerprint or facial recognition
Avoid suspicious links
- What it is: Receiving a link from an unknown or suspicious source can often mean that it contains malicious software or came from a bad actor. Even if you think you might recognize the sender, hackers often disguise themselves to gain trust and trick recipients into clicking the link.
- Why it’s important: Clicking on suspicious links often downloads viruses or malware onto your computer, giving the hacker access to your personal data and possibly disastrous power.
-
How it can be implemented / utilized: Train your employees to stay alert and cautious towards all links they receive in emails, texts, and other forms of communication. They should never click a link unless they completely trust and know the sender from whom they received it. Some measures employees can take to validate whether a link is legitimate to include:
-
Hovering their mouse over the link to preview the URL it’s sending you to
-
Copy and paste the link into an Open Source scanner tool like Virus Total to see if the URL has been linked to any malicious activity
Don't Give Away Personal Data
- What it is: Hackers will often request personal information under the guise of a false identity - for example, you may receive an email from “your bank” requesting that you confirm your login information or other personal data. If a suspicious source is requesting personal information from you, it might be a sign you’re being phished - personal information is often a key component for a hacker to enter your private accounts and exploit your data.
- Why it’s important: Giving away personal data, as harmless as it may seem, can give hackers the information they need to get into your accounts, systems, and more. Even if it’s as simple as a birthday, that can be enough to figure out a password or authenticate a login.
- How it can be implemented / utilized: Don’t give any personal information away online, especially to an unverified source. Do your research into whether the individual asking for your information is legitimate, and even if they are, avoid exchanging the data over platforms that lack strong security.
Access Control
- What it is: Access control determines who can and cannot view or utilize assets in a network, like a computer or a cloud storage system.
- Why it’s important: Setting barriers on your files, accounts, and data prevents unauthorized individuals from viewing, using, downloading, or sharing them. If anyone can get into your sensitive folders or systems, there’s nothing in place to stop hackers from not just accessing but tampering with your data.
- How it can be implemented/utilized: There are both physical and logical access controls that you can implement.
Physical access controls prevent unauthorized users from entering a physical location or object, like a building, room, or IT asset. Logical access controls require that users authenticate their identity before proceeding. This is done by requiring a user to re-authenticate before accessing the secure resource.
Network Monitoring
- What it is: Network monitoring is an ongoing process in which network users or administrators determine whether or not it is running as it is supposed to. Factors that are monitored include bandwidth, traffic, uptime, and how the network is being used.
- Why it’s important: When a network is regularly monitored, it’s more readily apparent when something is awry or there’s been foul play from a hacker. It makes the detection of bad actors, viruses, and more clearer to those who are familiar with the network - and if you’re routinely checking on your network, you’ll catch abnormalities more quickly.
- How it can be implemented / utilized: Network administrators employ network monitoring systems that keep track of the metrics mentioned above. The most common network monitoring systems are SIEMs, such as LogRhythm and Alien Vault, that can track activity across an entire network where endpoint security products (such as anti-virus software) are typically blind. Your system will alert you when something unusual has been detected, and after assessing the situation you can react accordingly.
Employee Training
- What it is: Bringing your teams + employees to a common understanding of best cybersecurity practices in your organization will provide them with the proper knowledge and consensus regarding how to navigate cybersecurity.
- Why it’s important: Employees are the first line of defense that your company has - no matter how fortified your security infrastructure maybe if your employees aren’t prepared, it doesn’t matter. The best way to ensure employees are following correct protocol and acting on the right values is to teach them exactly what that looks like. Aligning employees internally will create structure, repeatability, and reliability in your processes and protocols in the case of a security incident.
- How it can be implemented/utilized: When there’s the element of human error at play employers can’t rely on technology solutions alone to keep their personnel aligned. To ensure that protocol is followed correctly, it must be made as easy and straightforward as possible for employees. Either an external firm or your internal team can organize and provide company-wide cybersecurity training. Before executing this presentation, however, it’s important to determine as a company what is most important in your security landscape, where your biggest gaps are, and what best practices are depending on your needs.
how avertium is protecting our customers
Putting cyber security basics into practice can help your organization protect business processes and reduce the risk of a cyber attack. Updating software, securing files, managing passwords, and managing inventory are the first principles you should follow before diving into more sophisticated cyber security tools. Avertium offers the following services to help your organization stay on the right path toward securing your environment:
- Avertium has virtual CISOs who can provide a high level of service by helping you develop a plan to conduct a physical hardware inventory assessment. This service includes a visibility study to help discover what devices are on your network. This can be done remotely or in person.
- Avertium offers vulnerability management to remove any unnecessary applications and implement XDR tools to prevent ransomware and phishing attacks. Include an EDR, MDR or XDR strategy to stop ransomware before it spreads.
- Avertium also offers a Zero Trust Network Architecture, like AppGate, to stop malware lateral movement.
- Avertium offers a Cyber Maturity service so your organization can gain visibility, get control, and know where it stands. Our Cyber Maturity service can help facilitate insight and accountability around the controls your organization uses to protect its sensitive data.
avertium's recommendations
Avertium, the FBI, and CISA recommend the following regarding cyber security best practices:
-
Maintain offline, encrypted backups of data and regularly test backups
-
Identify a resilience plan that addresses how to operate if you lose access to—or control of—the IT and/or OT environment.
-
Identify OT and IT network interdependencies and develop workarounds or manual controls to ensure ICS networks can be isolated if the connections create a risk to the safe and reliable operation of OT processes.
-
Regularly test contingency plans, such as manual controls, so that safety-critical functions can be maintained during a cyber incident. Ensure that the OT network can operate at the necessary capacity even if the IT network is compromised.
-
Regularly test manual controls so that critical functions can be kept running if ICS or OT networks need to be taken offline.
-
Implement data backup procedures on both the IT and OT networks. Backup procedures should be conducted on a frequent, regular basis. Regularly test backup procedures and ensure that backups are isolated from network connections that could enable the spread of malware.
-
In addition to backing up data, develop recovery documents that include configuration settings for common devices and critical OT equipment. This can enable more efficient recovery following an incident.
-
-
Regarding passwords, require multi-factor authentication for all users, without exception.
-
Require accounts to have strong passwords and do not allow passwords to be used across multiple accounts or stored on a system to which an adversary may have access.
-
Secure credentials. Russian state-sponsored APT actors have demonstrated their ability to maintain persistence using compromised credentials.
-
Use virtualizing solutions on modern hardware and software to ensure credentials are securely stored.
-
Disable the storage of clear text passwords in LSASS memory.
-
-
Updating Software
-
Update software, including operating systems, applications, and firmware on IT network assets, in a timely manner. Prioritize patching known exploited vulnerabilities, especially those CVEs identified in this CSA, and then critical and high vulnerabilities that allow for remote code execution or denial-of-service on internet-facing equipment.
-
Consider using a centralized patch management system. For OT networks, use a risk-based assessment strategy to determine the OT network assets and zones that should participate in the patch management program.
-
-
Managing Inventory
-
Disable all unnecessary ports and protocols.
-
Review network security device logs and determine whether to shut off unnecessary ports and protocols. Monitor common ports and protocols for command and control.
-
Turn off or disable any unnecessary services (e.g., PowerShell) or functionality within devices.
-
MITRE TTPs:
Patching
- [T1591] Gather Victim Org Information
- [T1190] Exploit Public Facing Application
- [T1598] Phishing for Information
- [T1211] Exploitation for Defense Evasion
Inventory Control
- [T1586] Compromise Accounts
- [T1190] Exploit Public Facing Application
- [T1213] Data from Information Repositories
Managing Backups & Data Recovery
- [T1562] Impair Defenses
- [T1485] Data Destruction
- [T1486] Data Encrypted for Impact
- [T1561] Disk Wipe
Securing VPNs
Managing Default Passwords
Indicators of Compromise (IoCs):
Conti
- fb49dce92f9a028a1da3045f705a574f3c1997fe947e2c69699b17f07e5a552b
- 106.160[.]77
- 106.215[.]61
- 82.19[.]173
- Gojihu[.com]
- Sazoya[.com]
- Yawero[.com]
- Conti uses remote access tools that beacon to domestic and international VPS infrastructure over ports 80, 443, 8080, and 8443.
- Conti may use port 53 for persistence.
- New accounts and tools (especially Sysinternals) that were not installed by your organization.
- Disabled endpoint detection and constant HTTP and DNS beacons.
DarkSide
- fb49dce92f9a028a1da3045f705a574f3c1997fe947e2c69699b17f07e5a552b
- 106.160[.]77
- 106.215[.]61
- 82.19[.]173
- Gojihu[.com]
- Sazoya[.com]
- Yawero[.com]
- Conti uses remote access tools that beacon to domestic and international VPS infrastructure over ports 80, 443, 8080, and 8443.
- Conti may use port 53 for persistence.
- New accounts and tools (especially Sysinternals) that were not installed by your organization.
- Disabled endpoint detection and constant HTTP and DNS beacons.
Supporting Documentation
External cybersecurity threats on the rise in public sector, report says (police1.com)
SolarWinds Public Sector Cybersecurity Survey Report
What is Patch Management? Benefits & Best Practices | Rapid7
The consequences of not applying patches (pandasecurity.com)
What is Asset Inventory Management? | Balbix
Ransomware Conti Is Set To Infiltrate Backups (lifars.com)
Data Backup & Recovery | Certitude Security | Cyber Security
Oversight finds 'small lapses' in security led to Colonial Pipeline, JBS hacks | TheHill
cybersecuirty_sb_factsheets_all.pdf (ftc.gov)
AA22-011A_Joint_CSA_Understanding_and_Mitigating _Russian_Cyber_Threats_to_US_Critical_Infrastructure_TLP-WHITE.pdf
Threat Actor Leaks Login Credentials Of About 500,000 Fortinet VPN Accounts - CPO Magazine
Password Best Practices | UC Santa Barbara Information Technology (ucsb.edu)
End of Year Recap for 2021 (avertium.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of the Client's compliance with any law, regulation, or standard.