XDR: Tech Stack, Service, Process, or All Three?
You could ask ten security professionals in a room what eXtended Detection and Response (XDR) is and you would get ten different answers.
According to Gartner, “XDR is a unified security incident detection and response platform that automatically collects and correlates data from multiple proprietary security components.”
Seems simple, in theory, yet there is so much confusion in the market about what exactly an XDR solution looks like
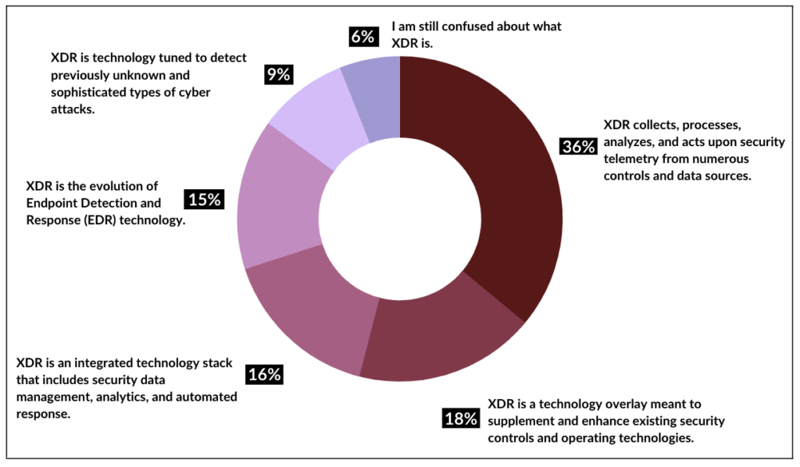
Source: Gartner
This is because eXtended Detection and Response (XDR) is a subjective set of processes, tools, and people established to provide new efficiencies in the traditional security operations center (SOC) by better integrating security control data and operations through cloud-based analytics, detection, and response.
The Varied Perspectives of XDR
Since XDR has no direct definition, its meaning varies from vendor to vendor. With this in mind, it also means that each vendor offers a different set of solutions they claim to be XDR. For example:
- Some companies may sell just the tech stack
- Some manage an existing tech stack
- Some may view their XDR offering as less about technology and more about a comprehensive approach aimed at connecting multiple data sources to drive toward prevention
Really, XDR is simply a collection of cybersecurity tools that bring together control points, security data, analytics, and operations into a unified business solution. Each tool covers a different aspect of cybersecurity and optimizes detection, prevention, and data collection. In short, in order for something to be “XDR,” it should probably have the following:
- Centralization of normalized data
- Correlation of security data and alerts
- A centralized incident response capability
EDR vs. XDR
Endpoint Detection and Response (EDR) is the process of managing and mitigating cyber threats based on end-point-level behaviors and data. XDR is a more advanced security solution than EDR offerings, with the capability to identify and neutralize threats. The service employs experienced, high-skill-level analysts with a more comprehensive roster of cutting-edge security tools at their disposal. This provides an enhanced level of proficiencies that go beyond the scope and cost-effectiveness of most internal security budgets, resources, and personnel.
Related Reading: EDR vs. MDR: Which Threat Detection is Right for You?
MDR vs. XDR
Managed Detection and Response (MDR) and eXtended Detection and Response (XDR) both aim to detect and eliminate malware users; however, XDR advances these services by combining these tools, people, and processes that MDR might utilize separately. As cybersecurity continues to progress, XDR leads a new mindset towards prevention, while MDR remains a singular step within this process.
Related Reading: We Have an MDR… Do We Still Need a SIEM?
Why Companies are Moving toward XDR
- CISOs are under pressure to move from reactive to proactive cybersecurity strategy – XDR integrates tools and operations that eliminate any areas of weakness within your security, preventing malware users from reaching your organization in the first place.
- CISOs want to automate what they can within security operations – XDR solutions can offer real value in improving security operations productivity with alert and incident correlation, as well as built-in automation.
- XDR enables companies to get a more comprehensive view of their attack surface – Gain a broader outlook on where you stand within the digital landscape in order to better understand your cyber strengths and weaknesses.
- Contextualizing raw data – Many XDR solutions reduce complexity through the logical convergence of multiple systems, particularly Security Incident and Event Management (SIEM) tools and MDR.
Related Reading: What Is Extended Detection and Response (XDR), and Why Is It Gaining Momentum as a Security Solution?
XDR and your Managed Security Service Provider (MSSP)
The role of an MSSP is to monitor, manage, and improve a company’s cybersecurity posture. That said, the scope of a managed security service provider is much greater than that of just MDR or XDR.
A MSSP should have a well-equipped, fully staffed security operations center (SOC), including security platform administrators, security analysts, malware analysts, a threat intelligence lab, and incident response analysts. All of these members should also be equipped with the right technology (typically a SIEM-based platform). In general, an MSSP has the capability to provide MDR, EDR, and XDR functions as a whole package.
Learn more about cybersecurity costs and savings through our MSSP ROI Calculator +
How Avertium Sees XDR: Fusion XDR
Rather than building an eXtended Detection and Response (XDR) platform that is limited to the technology of the vendor and the development of the vendor’s tools, Avertium approaches XDR with a fusion philosophy.
What does it mean to have a fusion philosophy? It means we take a more business-oriented, more strategic, more programmatic approach to cybersecurity. We call it Fusion MXDR.
Fusion MXDR is the first MDR offering on the market that fuses point solutions, cybersecurity assessments, and a human element into something greater than the sum of its parts - something that’s proactive, agile, and future-proofed.
Avertium’s Fusion MXDR is a living, breathing, programmatic approach to MDR. It gives you everything you need to bring context to the chaos... and everything you need to adapt, attack, evolve, and show no weakness.
Fusion MXDR equips you to adapt, attack, and evolve proactively alongside the threat landscape.
Fusion MXDR also combines the expertise of professional cyber services with the extended detection and response of our Cyber Fusion Centers, transforming once-tactical managed security into a truly integrated cybersecurity strategy. The result of this fusion delivers the clarity to see every threat, the context to extend your reach, and the agility to adapt and attack swiftly.
Don’t let ransomware users even get the chance to invade your cyber network. Stay up to date and prepared for any assault with Avertium’s eBook: Ransomware Trends in 2022