
Case Study:
INTERNOVA TRAVEL GROUP
Discover how Avertium helps unburden Internova Travel Group's security team to have the space to start focusing on more strategic cybersecurity priorities.
Previously, Avertium reported that the cyber war between Russia and Ukraine would ramp up in the coming months. Towards the end of February 2023, two cyber threat intelligence firms (Recorded Future and Google’s TAG) warned that Russia had plans to escalate its cyber attacks against Ukraine. Google’s TAG team stated that they had high confidence that Moscow would increase disruptive and destructive attacks in 2023 if the war shifts “fundamentally” in Ukraine’s favor.
It’s been predicted that Russian hacktivists would support Russia’s next big military push against Ukraine. The new cyber war could infiltrate regions of Ukraine that Russia has not been able to take over with physical force, as well as NATO countries. In 2022, Russia did not expect Ukraine to be as prepared or to recover as quickly from cyber attacks. As Russia has had months to prepare and reconsider its strategy, evidence of these predictions is emerging.
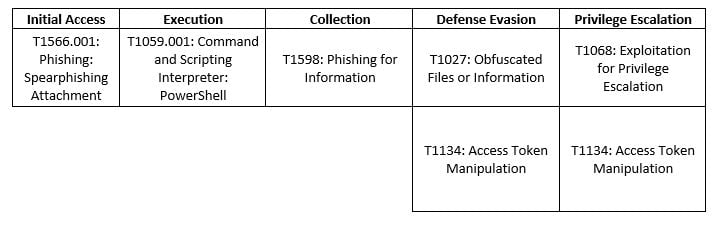
The APT Winter Vivern (also referred to as TA473 and UAC-0114) was recently seen exploiting a Zimbra software vulnerability in an ongoing cyber espionage campaign. The group is associated with the global objectives that are in line with the goals of the Belarusian and Russian governments.
Winter Vivern is notorious for their phishing campaigns, which involve replicating official government documents and distributing a malicious payload when opened. Over the past few months, the group has targeted state authorities in Ukraine and Poland, as well as government officials in India, Lithuania, the U.S., Slovakia, and the Vatican. Let’s examine Winter Vivern’s activity, tactics, and techniques.

Winter Vivern, whose name is derived from the mythical two-legged venomous dragon, is described by our technology partner, SentinelOne, as a “scrappy” threat actor that is resourceful and able to accomplish a lot with limited resources. However, what Winter Vivern lacks in sophistication, they make up for in persistence. The APT has traditionally used phishing tactics to deliver both PowerShell and JavaScript payloads, as well as credential harvesting campaigns via phishing emails.
Initially publicized in early 2021 by the DomainTools Research team, Winter Vivern is an overlooked group that operates with pro-Russian objectives. While analyzing Microsoft Excel documents with XLM 4.0 macros, the DomainTools Research team discovered a Lithuanian-language document titled "contacts". The basic macro in the document dropped a more complex PowerShell script that performed command and control (C2) communications with a domain that had been active since December 2020, yet did not appear on any industry-standard blocklists.
Upon investigation, the macro and domain mentioned uncovered documents that were aimed at Azerbaijan, Cyprus, India, Italy, Lithuania, Ukraine, and the Vatican. The DomainTools Research team informally labeled this as “Winter Vivern” because of the route employed in C2 communication during their research.
The original Lithuanian-language document named vtas_kontaktai_2021_04_20.xls, had a request to enable content if the document did not function correctly. The document stated that it included the "Contact Details of Municipal Administrations Departments for the Protection of the Rights of the Child". At the time, the document was provided by the official government of Lithuania and could be found on Google.
Image 1: Lithuanian Document
Source: DomainTools
Since December 2020, secure-daddy[.]com had been disseminating records from two URLs that suggest prior targeting of the Indian government and the Vatican. After examining Winter Vivern’s attack structure, DomainTools found that the initial C2 domain secure-daddy[.]com was registered in December 2020, and the serving domain securemanag[.]com had been active since April 2021 – suggesting that the threat actor was likely initiating a new campaign, serving documents from this address, and concealing their C2 behind infrastructure they’ve already used.
Both domains were hosted by 3NT Solutions LLP but were divided between the older domain in Sweden and the newer one in Estonia. The campaign went largely unnoticed, targeting a variety of languages. The scripts were not obfuscated and were simple, so the researchers didn't see the campaign as an APT-level campaign, as it didn't leverage any known tooling.
In 2021, Proofpoint noticed Winter Vivern concentrating on targeting European government, military, and diplomatic entities in active phishing campaigns. By late 2022, Proofpoint researchers also observed phishing campaigns that were aimed at elected officials and their staff in the U.S. Since the beginning of the Russia-Ukraine War, researchers have noticed a similarity among targets, social engineering lures, and impersonated people. Those targeted were knowledgeable of European politics and economics related to areas affected by the ongoing conflict. The APT’s social engineering lures and impersonated organizations usually pertained to Ukraine.
By early 2023, and after two years of very minimal activity, Winter Vivern began targeting specific government websites by crafting individual pages on a single malicious domain that were similar to those of the Central Bureau for Combating Cybercrime of Poland, the Ukraine Ministry of Foreign Affairs, and the Security Service of Ukraine.
In March 2023, SentinelOne’s research team, SentinelLabs, investigated Winter Vivern’s most recent activity. They discovered that the APT was targeting officials in the U.S. and in Europe as a part of a cyber espionage campaign. Their research shows that Winter Vivern's current actions match up with the goals of Belarus and Russia's governments. The APT has attacked many government bodies, and in a rare case, a private telecom company.
Although patched, Winter Vivern was seen leveraging a Zimbra Collaboration software vulnerability (CVE-2022-27926). The vulnerability is a medium-severity flaw that could enable an unauthenticated attacker to execute arbitrary JavaScript or HTML code. This includes using scanning tools like Acunetix to find webmail portals that have not been fixed yet, belonging to certain organizations. The purpose of this is to send phishing emails pretending to be from government organizations.
Image 2: Winter Vivern's CSRF: Infection Diagram
Source: Proofpoint
The messages contain URLs that take advantage of the cross-site scripting (XSS) vulnerability in Zimbra to run custom Base64-encoded JavaScript payloads within the webmail portals of the victims, allowing exfiltration of usernames, passwords, and access tokens. Winter Vivern's tactics include using malicious documents, frequently constructed from genuine publicly available government records, or tailored to specific topics. Recently, Winter Vivern has started using a new lure that involves imitating government domains to distribute malicious downloads.
The group is hyperlinking a benign URL in a phishing email to a URL that exploits CVE-2022-27926. The malicious URL uses a webmail domain with a vulnerable Zimbra Collaboration Suite and adds a random hexadecimal or plaintext JavaScript code. When the code is received, it is decoded and downloads a custom JavaScript payload that steals usernames, passwords, and CSRF tokens from the user.
Also, according to SentinelLabs, the threat actor’s recent campaigns illustrate the group’s use of lures to start the infection process, utilizing batch scripts masquerading as virus scanners to prompt downloads of malware from attacker-controlled servers. The malicious files make it appear is if an antivirus scan is happening, showing how much time is left. In reality, the threat actor is secretly downloading a malicious payload using PowerShell.
Image 3: False Virus Scan Loaders
Source: SentinelLabs
Winter Vivern’s recent campaigns target those working in the governments of Poland, Ukraine, India, and Italy. The threat actor was also seen targeting high-profile state officials, as well as a telecommunications company supporting Ukraine since the Russian invasion. Although Winter Vivern’s attacks are simple, the APT uses effective tools and attack techniques. Their attack lures, as well as their ability to stay out of the public eye has made them an alarming threat actor within cyber space.
The acting deputy head of the Security Service of Ukraine’s (SSU) Cybersecurity Department stated that Moscow was responsible for almost 1,200 cyberattacks and other significant cyber incidents in the first quarter of 2023. [1]At this rate, Russia is projected to carry out 4,800 attacks this year, approximately 300 more than the number of cyberattacks attributed to Russian threat actors in 2022. Microsoft’s threat assessment from March 2023, stated that Russian threat actors launched attacks in at least 17 European countries within the first six weeks of 2023.
Also, the French defense firm Thales stated that Russia was utilizing a variety of cyber weapons to target Poland, the Nordic and Baltic nations with the intention of creating discord and promoting anti-war messages. Microsoft is continuing to monitor the development and deployment of new ransomware variants. Microsoft’s research indicates that Russia will likely continue to carry out espionage attacks against Ukraine and its allies, as well as destructive attacks within and possibly beyond Ukraine.
Highlighting the global reach of Russian threat actors, the firm said 21 percent of attacks outside Ukraine since the start of the war were against the U.S. While attacks outside Ukraine were often low-level, Microsoft said Russia may choose more damaging cyber tools in the future. The spillover risk posed by Russia’s recent targeting means that organizations and security professionals everywhere need to harden their digital defenses.
[1] Russia Ramping Up Cyberattacks Against Ukraine (voanews.com)
URLs
Domains
IP Addresses
File Hashes (SHA1)
APTs like Winter Vivern use known vulnerabilities in addition to targeted phishing campaigns to entice victims into opening malicious documents. Please don’t let your organization become a victim of a targeted campaign by not implementing cyber security best practices. In addition to practicing good cyber security hygiene, you can count on Avertium to provide the best services to help keep your organization safe:
A year of Cyber Conflit in Ukraine_CTI-2023.pdf (thalesgroup.com)
Is Russia regrouping for renewed cyberwar? - Microsoft On the Issues
Ukraine gears up for new phase of cyber war with Russia - POLITICO
Russia Ramping Up Cyberattacks Against Ukraine (voanews.com)
Winter Vivern: A Look At Re-Crafted Government MalDocs - DomainTools | Start Here. Know Now.
Winter Vivern | Uncovering a Wave of Global Espionage - SentinelOne
Winter Vivern APT Targets European Government Entities with Zimbra Vulnerability (thehackernews.com)
Winter Vivern – all Summer (lab52.io)
Russia Ramps Up Cyberattacks On Ukraine Allies: Analysts | Barron's (barrons.com)
Zimbra Releases/8.8.15/P31 - Zimbra :: Tech Center
NATO and Diplomats' Email Portals Targeted by Russian APT Winter Vivern (heimdalsecurity.com)
Winter Vivern APT hackers use fake antivirus scans to install malware (bleepingcomputer.com)
APT group Winter Vivern exploits Zimbra webmail flaw to target government entities | CSO Online
Low-Budget 'Winter Vivern' APT Awakens After 2-Year Hibernation (darkreading.com)
Related Resource:
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.