Flash Notice: Critical Citrix Zero-Day Exploited by Attackers
overview
A critical zero-day vulnerability was found in Citrix ADC and Gateway. CVE-2022-27518 is an unauthenticated remote code execution vulnerability that is being leveraged by a Chinese state-sponsored threat actor known as APT5 or MANGANESE.
APT5 is currently exploiting CVE-2022-27518 by targeting vulnerable Citrix ADC and Gateway Devices. The US National Security Agency (NSA) stated that the threat actors have bypassed normal authentication controls and have gained illegitimate access to targeted organizations.
Citrix released a security update stating that they are aware of a small number of targeted attacks in the wild and those using an affected build with a SAML SP or IdP configuration should install their recommended builds immediately.
CVE-2022-27518 affects the following versions of Citrix ADC and Citrix Gateway:
- Citrix ADC and Citrix Gateway 13.0 before 13.0-58.32
- Citrix ADC and Citrix Gateway 12.1 before 12.1-65.25
- Citrix ADC 12.1-FIPS before 12.1-55.291
- Citrix ADC 12.1-NDcPP before 12.1-55.291
Citrix stated that customers should update to the 12.1 build (including FIPS and NDcPP variants) or to the current 13.0 build (13.0-88.16).
The NSA released threat hunting guidance to help organizations investigate their Citrix ADC environments. The NSA further stated that organizations should treat the detection mechanisms as independent ways of identifying potentially malicious activity on impacted systems. Findings may vary based on the environment and stage of activity. The NSA recommends investigating positive results even if other detections require no findings.
Citrix has provided permanent downloadable fixes for Citrix ADC and Citrix Gateway, and organizations should apply those fixes as soon as possible.
How Avertium is Protecting Our CUSTOMERS
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Avertium offers Zero Trust Network as a Service (ZTNaaS) for any organization that wants to control their attack surface. The zero-trust security model delivers exactly what the name promises: it is an IT security concept that specifies no access is allowed until the successful completion of authentication and authorization processes.
Avertium's recommendations
Avertium recommends following Citrix’s guidance below:
Citrix strongly urges affected customers of Citrix ADC and Citrix Gateway to install the relevant updated versions of Citrix ADC or Citrix Gateway as soon as possible:
- Citrix ADC and Citrix Gateway 13.0-58.32 and later releases
- Citrix ADC and Citrix Gateway 12.1-65.25 and later releases of 12.1
- Citrix ADC 12.1-FIPS 12.1-55.291 and later releases of 12.1-FIPS
- Citrix ADC 12.1-NDcPP 12.1-55.291 and later releases of 12.1-NDcPP
Note: Citrix ADC and Citrix Gateway versions prior to 12.1 are EOL and customers on those versions are recommended to upgrade to one of the supported versions.
Customers can determine if their Citrix ADC or Citrix Gateway is configured as a SAML SP or a SAML IdP by inspecting the ns.conf file for the following commands:
- add authentication samlAction
- Appliance is configured as a SAML SP
OR
- add authentication samlIdPProfile
- Appliance is configured as a SAML IdP
Note: If either of the commands are present in the ns.conf file and if the version is an affected version, then the appliance must be updated.
Avertium also recommends following the NSA’s mitigation guidance below:
- Move all Citrix ADC instances behind a VPN or other capability that requires valid user authentication (ideally multi-factor) prior to being able to access the ADC.
- Isolate the Citrix ADC appliances from the environment to ensure any malicious activity is contained.
- Restore the Citrix ADC to a known good state.
- Even if you do not have any indications of malicious activity, ensure that your Citrix ADC appliances are running a current version with the latest updates.
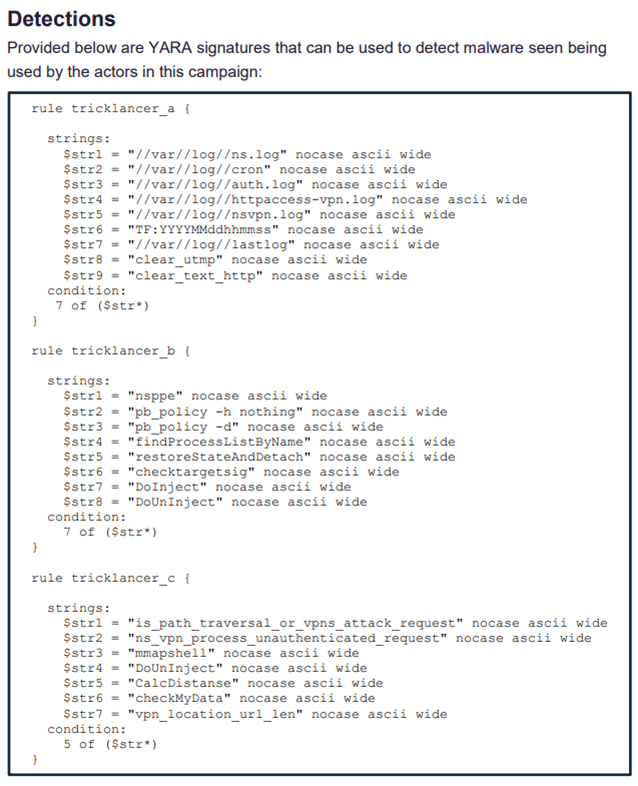
INDICATORS OF COMPROMISE (IOCS):
SUPPORTING DOCUMENTATION
Citrix ADC and Citrix Gateway Security Bulletin for CVE-2022-27518
Released: Citrix ADC and Citrix Gateway (security bulletin CTX474995) security update | Citrix Blogs
Hackers exploit critical Citrix ADC and Gateway zero day, patch now (bleepingcomputer.com)
CSA-APT5-CITRIXADC-V1.PDF (defense.gov)