Botnet Attack DDoS Guide: TIR-20211011 & The Meris Botnet
Executive Summary
Distributed Denial of Service (DDoS) is disruption to internet-based services that can make any internet connected machine unavailable to perform its intended purpose. The objective of this attack is to maliciously attempt to disrupt traffic on a server, service, or network, with a flood of Internet traffic. Think of the attack as a traffic jam on a busy highway – disrupting the normal flow of traffic and eventually causing all traffic to stand still. Any business that depends on internet access for business processes and services (SaaS services, B2B/B2C, etc, Remote Access, etc.) should ensure continuity plans to address DDoS attacks are in place.
DDoS attacks can be devastating and have affected some of the most powerful businesses, including Yandex, a Russian tech giant. In September of 2021, the company was attacked by Meris, a recently discovered botnet attack DDoS that’s infecting machines at record-breaking speed. Meris has also infiltrated systems in New Zealand and in the United States. Let’s take a look at how DDoS botnets work and why the recently discovered botnet, Meris, is a major concern for cyber security specialists tasked with the responsibility of mitigation.
What is a ddos attack?
As one of the most powerful types of cyber attacks, DDoS typically utilizes an array of compromised and non-compromised computer systems (computers and IoT devices) to flood their intended targets with bogus Internet traffic. The attacks are accomplished through the networks of Internet-connected devices, which have been infected with malware and allow them to be controlled by attackers. The individual devices used to carry out these attacks are called bots, while a group of bots is called a botnet. Attackers can send remote instructions to each bot with the goal of sending spam, stealing credentials, spying on people and organizations and, of course, orchestrating a DDoS attack.
After a victim’s server or network is confirmed by the botnet, BoTs can use multiple methods to send large amounts of traffic to the targeted IP addresses – causing an overwhelming flood of traffic and resulting in a denial-of-service to the server or network’s normal traffic. Trying to separate the attack traffic from normal traffic can be difficult because each bot is a legitimate Internet device.
Cloudfare, yandex and krebsonsecurity attacked by meris botnet
In the early summer of 2021, Cloudfare, an internet infrastructure firm, experienced a DDoS attack that was almost three times larger than any previous DDoS attack they’ve seen. Cloudfare detected and mitigated 17.2 million bogus traffic requests-per-second (RPS) on average. The attack was launched by a botnet named Meris and it targeted a customer in the financial industry. As a result, Meris was able to bombard Cloudfare with over 330 million attacks. Cloudfare reported that the attack traffic came from more than 20,000 bots in 125 countries, with 17% being from India and Brazil.
Discovered in June 2021, Meris is also responsible for attacking the Internet tech giant, Yandex, between August 29 and September 5, 2021. The botnet successfully launched about 250,000 malware infected devices globally and has sent 21.8 million bogus RPS – making it the biggest DDoS attack in history. Apparently, Meris is exploiting a security vulnerability within internet routers produced by MikroTik. The attackers are taking advantage of a 2018 bug found in more than 56,000 MikroTik hosts. The bug is found in routers owned by businesses, as well as consumers who use them at home. Owners of the MikroTik routers have more than likely left them unpatched since 2018. The United States is home to 42% of MikroTik’s routers, followed by China at 18.9%.
In September 2021, Brian Krebs of KrebsOnSecurity.com announced that his site was also briefly attacked by Meris, but fortunately the botnet attack was successfully mitigated by Akamai. The attack was among the largest they had ever seen with the difference being that Meris doesn’t appear to be using tried and true attack methods seen in a DDoS attack.
Typically, DDoS attacks rely on the DNS reflection method to leverage unmanaged DNS servers on the Web, creating large traffic floods. The DNS reflection attack method counts on unmanaged routers belonging to businesses or consumers. Attackers can then send spoofed DNS queries to those servers and forge the request, so it appears as if it’s coming from the target’s own network. When the servers respond, the response gets sent to the spoofed address.
Additionally, attackers amplify the reflective attack by creating DNS queries, creating responses that are much larger than the requests. Krebs stated that when their Meris attack was analyzed, the attackers didn’t rely on DNS reflection or amplification. Instead, their attack method included requiring a legitimate connection between the attacker and the target, including SYN, GET, and POST floods. The attack involves a browser requesting a connection to a server, then without waiting for a response, more requests are sent. The attack technique is exploiting HTTP pipelining, which allows Meris to achieve high RPS numbers.
Krebs further said that the largest portion of the Meris attack came in the form of traffic designed to look like generic routing encapsulation (GRE) data packets. GRE allows two people to share data they wouldn’t be able to share over the public network itself. Seeing this large of an attack come from GRE is highly unusual.
Early Warning Signs of Meris
Previously, we mentioned that Meris was exploiting an unpatched vulnerability (CVE-2018-14847) within MikroTik routers from 2018. At the time, the exploit was new and was used against the routers - giving them the ability to execute remote code on affected smart devices, put a root shell on said device, and bypass the router’s firewall. Next, the attacker gains access to the internal network and loads malware onto their victim’s system undetected.
Rated medium in severity, the attack affected Winbox, a management component and a Windows GUI application for MikroTik’s RouterOS software. The vulnerability tied to Winbox allowed attackers to read files that flow through the router without authentication. The attacker also had the capability of writing files to the router. Tenable Research warned that this exploit needed to be taken seriously due to the new hacking technique that allowed for remote code execution on MikroTik routers.
MikroTik’s patch was able to stop all the attack techniques associated with CVE-2018-14847, but only 30% of MikroTik’s routers were patched, leaving 200,000 routers vulnerable. By August 2018, 3,700 MikroTik routers were used in a cryptojacking campaign, and 7,500 routers were used to forward the owners’ traffic to eavesdropping cybercriminals.
the future of ddos attacks
Cyber security researchers say that Meris has yet to exploit the MikroTik vulnerability to full capacity. The attackers behind Meris have the capability to execute a much larger attack, it just hasn’t happened yet. Although it’s unclear how MikroTik’s routers are being compromised on such a large scale, Qrator labs believes that the most recent exploits could be due to “some vulnerability that was either kept secret before the massive campaign’s start or sold on the black market”.
Researchers at Qrator Labs also said that the Meris attacks are substantial with dozens of thousands of host devices. They saw a total of 30,000 host devices being used through several attacks, with Yandex collecting the data of about 56,000 attacking hosts. However, they believe that number is probably higher due to the rotation and the attackers not wanting to show what they are capable of all at once.
Additionally, our partner, Lumen, reported that the number of DDoS attacks they’ve mitigated has increased 14% during the second quarter of the year, with a 10% increase in the number of sites attacked. The top three verticals targeted in the 500 largest attacks during the second quarter of the year were, telecommunications, software and technology, and government. Lumen’s threat intelligence arm, Black Lotus Labs®, also found that the country with the most DDoS botnet hosts was Brazil, going from 12,000 in the first quarter of the year, to 33,200 in the second quarter. Globally, Black Lotus Labs tracked more than 150,200 infected hosts.
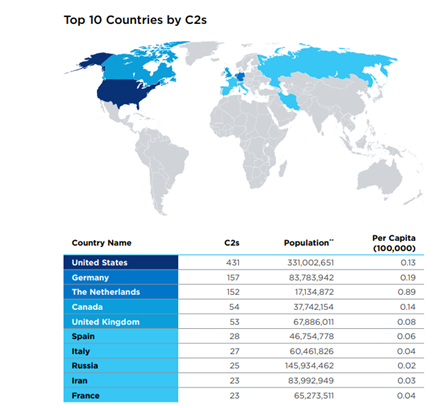
Table 1: Countries Hosting the Most DDoS C2s
Source: Lumen
According to Lumen’s research, the country hosting the most DDoS Command and Control Servers (C2s) was the United States – with a total of 431. Germany and the Netherlands tied for second place with over 150 C2s each.
It’s clear from Lumen’s statistics that DDoS has the ability to devastate any business that relies on the internet. Even if you think you or your business won’t fall victim to such an attack, think again. Yandex is one of the largest technology companies in Russia and it was hit with the most massive DDoS attack in history. Typical targets for a DDoS include: any online business or organization that provides online services, shopping sites, and online betting. If your business falls into any of those categories and you don’t want to be the next victim, take a look at Avertium and Lumen’s collaborative recommendations to see how we can help protect you.
avertium's recommendations for ddos attack prevention
- Patching is always an excellent way to prevent being an unwilling participant of a BotNet or DDoS attack. If you have a MikroTik router, you can find the update here.
- According to MikroTik, if someone stole your password in 2018, simply patching will not help due to this being an old vulnerability. You will also need to change your password, re-check your firewall, and look for scripts you didn’t create. When keeping your passwords / logins safe, it’s best to frequently change your credentials or implement 2FA (two-factor-authentication) methods.
- You can use a network intrusion detecting signature, which detects if attackers compromised the MikroTik router (not necessarily DDoS).
- MikroTik also recommends that you disable SOCKS and look in the System -> Scheduler menu. Disable all rules you can't identify. By default, there should be no Scheduler rules, and SOCKS should be off. MikroTik also recommends blocking the following domains:
- .eeongous[.com]
- .leappoach[.info]
- .mythtime[.xyz]
- .eeongous[.com]
- .leappoach[.info]
- .mythtime[.xyz]
- Bestmade[.xyz]
- Gamesone[.xyz]
- mobigifs[.xyz]
- myphotos[.xyz]
- onlinegt[.xyz]
- Picsgifs[.xyz]
avertium's recommendations for ddos attack mitigation
- Our partner, Lumen, can help mitigate a DDoS attack with Lumen® DDoS Hyper®. This online service, currently available in North America, allows you to order, configure, and turn up services in minutes – even during an active attack. With nine global security centers (SOCs), Lumen offers support 24/7 and proactive monitoring. Contact your Avertium account executive or service delivery manager for more details.
- If you need a more advanced DDoS service, beyond what is offered by Lumen DDoS Hyper, Lumen also offers DDoS Mitigation and Application Security through 15 global scrubbing centers and Cloud WAF solutions. The global DDoS Mitigation Service uses Black Lotus Lab’s global threat intelligence as countermeasures to block DDoS bots on the network as traffic hits a scrubbing center. This mitigation method is called Rapid Threat Defense.
- With this service Lumen has been able to help organizations reduce DDoS threat potential, avoid additional costs associated with DDoS attacks, protect brand reputation, and enhance digital customer experience.
- Although Lumen® DDoS Hyper® and DDoS Mitigation and Application Security differ, both solutions use the same underlying platform (SOCs, scrubbing architecture, etc.).
Indicators of Compromise (IoCs):
- 1abcnews[.xyz]
- 1awesome[.net]
- 7standby[.com]
- Audiomain[.website]
- Bestmade[.xyz]
- Bestony[.club]
- Ciskotik[.com]
- Cloudsond[.me]
- Dartspeak[.xyz]
- Eeongous[.com]
- Fanmusic[.xyz]
- Gamedate[.xyz]
- Gamesone[.xyz]
- Globalmoby[.xyz]
- Hitsmoby[.com]
- Leappoach[.info]
- Massgames[.space]
- Mobigifs[.xyz]
- Mobstore[.xyz]
- Motinkon[.com]
- my1story[.xyz]
- myfrance[.xyz]
- myphotos[.xyz]
- mythtime[.xyz]
- onlinegt[.xyz]
- phonemus[.net]
- picsgifs[.xyz]
- portgame[.website]
- senourth[.com]
- sitestory[.xyz]
- spacewb[.tech]
- specialword[.xyz]
- spgames[.site]
- strtbiz[.site]
- takebad1[.com]
- tryphptoday[.com]
- wchampmuse[.pw]
- weirdgames[.info]
- widechanges[.best]
- zancetom[.]com
MITRE TTPs:
- [T1595] Active Scanning
- [T1589] Gather Victim Identity Information
- [T1584] Compromise Infrastructure
- [T1583] Resource Development
- [T1498] Network Denial of Service
Terms
Botnet – a network of computers infected by malware that are remotely controlled by an attacker.
DDoS (Distributed Denial of Service) – takes advantage of capacity limits that apply to any network resources. A DDoS attack sends multiple requests to the compromised web resource, trying to exceed the site’s capacity. This prevents the site from functioning properly.
IoT Devices (Internet of Things) – computer hardware, such as appliances, machines, and sensors. They transmit data over the internet or other networks.
GET Flood – a request that is used to retrieve standard, static content like images.
SYN Flood – a network-tier attack that floods a server with requests without responding to corresponding acknowledgements.
POST Flood – a request that is used to access dynamically generated resources.
Supporting Documentation
KrebsOnSecurity Hit By Huge New IoT Botnet “Meris” – Krebs on Security
Cloudflare thwarts 17.2M rps DDoS attack — the largest ever reported
Yandex Pummeled by Potent Meris DDoS Botnet | Threatpost
MikroTik Routers and Wireless - Software
What Is a SYN Flood DDoS Attack? | F5
PoC Attack Escalates MikroTik Router Bug to ‘As Bad As It Gets’ | Threatpost
What is a botnet? When armies of infected IoT devices attack | CSO Online
Botnet - Definition (trendmicro.com)
What is a DDoS Attack | DDoS Meaning | Kaspersky
DDoS Mitigation and Web Application Security | Lumen
The Total Economic Impact™ Of Lumen Technologies DDoS Mitigation Service
APPENDIX II: Disclaimer
This document and its contents do not constitute and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of the Client's compliance with any law, regulation, or standard.