HIVE Ransomware: Everything You Need To Know (Attacks & Analysis)
Executive Summary of Hive ransomware
In October 2021, we published a report naming the top five cyber security threats within the health care industry. In that report, we mentioned Hive being in the top ten global ransomware gangs for the third quarter of the year. Hive is infamously known for attacking healthcare facilities but has recently decided to make an even bigger name for themselves by attacking the retail industry and demanding one of the largest ransoms in cyber security history.
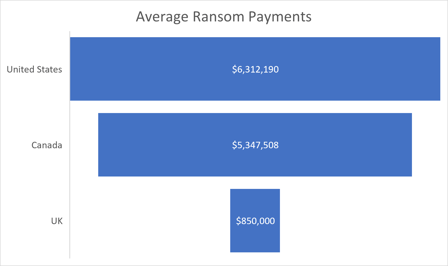
Ransomware continues to be a national security threat and ransomware gangs like BlackMatter, REvil, and DarkSide are constantly evolving, developing new tools, and changing tactics. Mimecast, a cloud security company, reported that the United States takes the lead when it comes to how much companies are willing to pay attackers following ransomware attacks. In a study where researchers spoke to 742 cybersecurity professionals, it was found that 80% of them were targeted with ransomware over the last two years – 39% of those cyber security professionals resorted to paying the ransom.
Source: Avertium
The FBI and CISA discourage companies from paying ransoms because it encourages cyber criminals to continue to attack organizations and demand ransom payments or fund illicit activities for cyber criminals. Unfortunately, when threat actors like Hive revise well-known ransomware tactics and become more detailed in their attacks, it’s hard for organizations to see any hope of recovering from an attack. Let’s take a look at Hive ransomware, their tactics, and why they are still a major concern for the healthcare industry and beyond.
Important Note: The ransomware gang is named Hive, as well as their ransomware. Therefore, the name Hive will be used interchangeably throughout this report. Researchers are not sure if Hive is a Ransomware as a Service platform or if Hive is a closed group.
hive and their tactics
Initially observed in June 2021, Hive operates as an affiliate-based ransomware gang. They have a variety of techniques and tactics that are challenging for cyber security professionals to defend and mitigate.
Over the years, analysts and researchers noticed that most ransomware threat actors focus on one platform, like Windows, to launch their attacks. Hive actually does the opposite and uses several platforms – Windows, Linux, and EXSi hypervisors. According to Adam Meyers, Vice President of CrowdStrike, the threat actor created the ability to run their ransomware against EXSi.
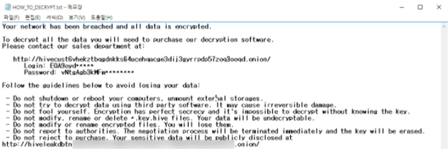
Image 1: Hive Ransomware Note
Source: AdvIntel
Hive’s ransom notes have a link to a “sales department” which allows victims to contact them through live chat – almost like customer service. Hive also uses Golang, a modern programming language that threat actors have been utilizing lately. Once in a system, Hive uses their tools to move laterally within that system and escalate privileges to steal and encrypt files.
The threat actor’s focus is faster payment, and they achieve this by increasing pressure on their victims by stealing their data before encrypting it. One of the ways Hive is able to gain access to their victim’s data is by sending out phishing emails with malicious attachments and by hijacking the Remote Desktop Protocol (RDP).
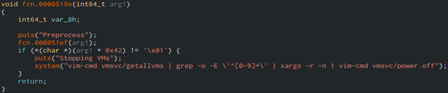
Image 2: Command Used to Shut Down VMs
Source: Twitter.com/@malwrhunterteam
linux and freebsd variants
ESET Research Labs identified Linux and FreeBSD variants of Hive ransomware. This means that the threat actor is looking to attack other operating systems as well as cloud apps. The Linux and FreeBSD variants are written in Golang, however, their malware still has some bugs in it and has yet to be exploited. John Bambenek, the principal threat hunter at NetEnrich, stated that it isn’t unusual for a threat actor’s imperfect malware to be in the wild. Hive appears to be shifting platforms by targeting public facing systems like Linux – a system that is commonly used for web-servers. They’re hoping to cause a significant impact on the lives of their victims by compromising Linux and giving the victims more of an incentive to pay their ransom demands.
Cyber security analysts are not shocked to see the evolution of ransomware. It’s evolved to now include operating systems like Linux, Mac iOS, and VMware EXSi. More organizations are starting to embrace the digital world and are securing their data center to the cloud. Attackers know this and are using that to their advantage.
“Cloud applications that are now running on non-Windows operating systems such as Linux, are also under attack from these cyber criminals. For many years, Linux was thought to be a safe haven from common malware and ransomware attacks due to a smaller percentage of organizations utilizing it. However, that has finally changed with cyber criminals expanding their attacks into new operating systems spaces." – Chuck Everette – Director of Cyber Security Advocacy at Deep Instinct
The Linux version of Hive ransomware may still have a few kinks in it, but there is no doubt that the gang will continue to develop the malware because of the potential opportunities it will provide. Because the original ransomware is written in Golang (which is a cross-platform), the majority of the encryption code won’t need too much modification to run in a Linux environment.
mediamarkt attack
In November 2021, Hive attacked Europe’s largest consumer electronics retailer, MediaMarkt. The company’s servers and workstations were encrypted by Hive and their IT systems had to be shut down to prevent further spread. The attack affected numerous stores throughout the Netherlands and other countries within Europe. The company was still able to function online, but the brick-and-mortar stores were not able to accept credit cards or print receipts. As a result, the stores had to disconnect their cash registers from the network.
After encrypting MediaMarkt’s server, Hive demanded that the company pay $240 million in ransom for decryption– a number that has since been reduced to a fraction of that number ($50 million in bitcoin). It’s common for ransomware gangs to demand an extremely high initial ransom to negotiate a much lower (but still profitable) amount. As of now, there are no public reports confirming that the company paid the ransom.
This is not the first time Hive has wreaked havoc on a large enterprise. In August 2021, the ransomware gang attacked Ohio’s non-profit, Memorial Health System, forcing the staff to work from paper charts - disrupting scheduled surgeries.
Additionally, researchers from AdvIntel reported that Hive recently compromised the networks of the third largest medical facility in Saxony-Anhalt. An insider confirmed that Hive estimated the organization’s revenue to be $272 million. Operators of the ransomware gang mentioned that because they attacked a healthcare facility, it’s likely that they will quickly pay the ransom. Attackers know the information within the healthcare industry is the most valuable information and goes for hundreds of dollars on the black market.
ransomware gangs use financial events to target organizations
In early November, the FBI released a report about threat actors using significant time-sensitive financial events (mergers, stock valuation, and acquisitions) against organizations. Threat actors are starting to research major financial transactions between companies as leverage. If victims don’t pay up, the threat actor will threaten to disclose the information publicly, which causes investor backlash.
In early 2020, a ransomware gang called Unknown posted on a Russian hacking forum encouraging members to use the NASDAQ stock exchange to influence the extortion process. Following the posting, threat actors began negotiating payment with the victim and mentioned the victims’ stocks. The attacker threatened to leak the victim’s data to NASDAQ if they refused to negotiate a ransom. Between March and July 2020, there have been at least three publicly traded U.S companies who were victims of ransomware attacks during their mergers or acquisitions.
While there are no official statements surrounding the reason behind MediaMarkt’s attack, we do know that in 2017, the once independent retailer was acquired by a retail company now known as Ceconomy AG. We also know that prior to this acquisition, MediaMarkt was owned by German billionaire, Erich Kellerhais.
Ceconomy AG, a retail company formed through a demerger of Metro Group, owns, and operates MediaMarkt. They also operate more than 1,000 consumer electronics stores in 12 countries and 35% of their sales are generated online. MediaMarkt is Europe’s largest consumer electronics retailer and employs 53,000 people. The company’s total sales equal €20.8 billion.
avertium's recommendations
Research from the U.S. Financial Crimes Enforcement Network (FinCEN) discovered that payments linked to ransomware attacks amount to $590 million. This exceeds the total for 2020 and is continuing to rise. Because the cyber landscape is always changing, it’s imperative to be aware of new cyber attack strategies and techniques. Avertium is here to keep you informed and to keep your organization safe. We recommend the following for the best protection against ransomware attacks:
- Avertium offers vulnerability management as a service (VMaaS) to remove any unnecessary applications and implementing XDR tools to prevent ransomware and phishing attacks. Include an EDR, MDR or XDR strategy to stop ransomware before it spreads. You should also include a Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- It’s also recommended by Avertium and the FBI that your business require multi-factor authentication to remotely access networks. Implementing network segmentation and filtering network traffic to stop phishing emails from reaching victims is also helpful.
- Reach out to your Service Delivery Manager or Account Executive if you need assistance applying any of the above recommendations.
Recommendations from Avertium and our partner, Advanced Intelligence:
- Hive uses developed social engineering techniques to lure victims (remember, they may be researching companies prior to their attacks) . Avertium offers user awareness training with KnowBe4.
- Prevent lateral movement by implementing network hierarchy protocols with network segregation and decentralization.
- Use whitelisting tools to audit or block command-line interpreters (AppLocker).
- Rclone and other data exfiltration command-line interface activities can be captured through correct logging of process execution with command-line arguments.
- Have security protocols in place for Veeam to avoid account takeover. Enabled backups decrease Hive’s ransom demands and can lead to data recovery without you having to pay them.
- Externally exposed RDPs.
- Relying on outdated tools and point solutions will compromise your network or system. Better technology exists to detect complex attacks like Hive ransomware.
Recommended mitigations for Hive ransomware from the FBI:
- Monitor cyber threat reporting regarding the publication of compromised VPN login credentials and change passwords/settings if applicable.
- Keep computers, devices, and applications patched and up to date.
- Review the following additional resources.
- The joint advisory from Australia, Canada, New Zealand, the United Kingdom, and the United States on Technical Approaches to Uncovering and Remediating Malicious Activity provides additional guidance when hunting or investigating a network and common mistakes to avoid in incident handling.
- The Cybersecurity and Infrastructure Security Agency-Multi-State Information Sharing & Analysis Center Joint Ransomware Guide covers additional best practices and ways to prevent, protect, and respond to a ransomware attack.
- gov is the U.S. Government’s official one-stop location for resources to tackle ransomware more effectively.
If your organization is impacted by a ransomware attack, the FBI and CISA recommend the following:
- Isolate the infected system.
- Turn off other computers and devices.
- Secure your backups.
Because cyber criminals are beginning to do their homework on large financial transactions between companies and are using that information as ammunition, the FBI published a list of recommendations for organizations to consider implementing:
-
- Backup critical data offline
- Ensure copies of critical data are in the cloud or on an external hard drive or storage device.
- Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the original data resides.
- Install and regularly update anti-virus or anti-malware software on all hosts.
- Only use secure networks and avoid using public Wi-Fi networks.
- Use two-factor authentication for user login credentials, use authenticator apps rather than email as actors may be in control of victim email accounts and do not click on unsolicited attachments or links in emails.
- Implement least privilege for file, directory, and network share permissions.
MITRE TTPs:
- [001] Impair Defenses: Disable or Modify Tools
- [001] Indicator Removal on Host: Clear Windows Event Logs
- [T1486] Data Encrypted for Impact
- [T1133] External Remote Services
- [T1566] Phishing
- [T1190] Exploit Public Information
- [T1598] Phishing for Information
Indicators of Compromise (IoCs):
Hive
- b5045d802394f4560280a7404af69263
- 321d0c4f1bbb44c53cd02186107a18b7a44c840a9a5f0a78bdac06868136b72c
- exe
- exe
- C:\Windows\SysWOW64\winlo.exe
- txt
- *.key.hive
- exe /set {default} recoveryenabled no
- exe /set {default} bootstatuspolicy ignoreallfailures
- exe cl application
- bat
- exe delete shadows /all /quiet
- exe cl system
- exe SHADOWCOPY /nointeractive
- hivecust6vhekztbqgdnkks64ucehqacge3dij3gyrrpdp57zoq3ooqd[.onion]
- http://hivecust6vhekztbqgdnkks64ucehqacge3dij3gyrrpdp57zoq3ooqd[.onion/]
Anonymous File Sharing Links
- [http:/]/hiveleakdbtnp76ulyhi52eag6c6tyc3xw7ez7iqy6wc34gd2nekazyd[.onion] (Hive TOR site)
- https://anonfiles[.com]
- https://mega[.nz]
- https://send.exploit[.in]
- https://ufile[.io]
- https://www.sendspace[.com]
terms
EXSi Hypervisors – a hypervisor is a virtual machine monitor or VMM. It’s a type of virtualization software that supports the creation and management of virtual machines by separating a computer’s software from its hardware. EXSi partitions hardware to consolidate applications. It also minimizes hardware resources needed to run the hypervisor.
Ransomware – malicious software that infects a device and stops users from accessing data and files until a ransom is paid.
Phishing Emails – when attackers send emails to victims containing malicious links and files. The emails are designed to scam people into revealing sensitive information that can be used for an attackers’ financial gain.
Remote Desktop Protocol (RDP) – technical standard for using a desktop computer remotely.
Average ransomware payment for US victims more than $6 million, survey says | ZDNet
State of Ransomware Readiness Report (mimecast.com)
What is a Bare Metal Hypervisor? | VMware Glossary
What is ESXI? | Bare Metal Hypervisor | ESX | VMware
Why Hive Attacks Are the Latest Menace to Healthcare Sector (govinfosecurity.com)
FBI shares technical details for Hive ransomware (bleepingcomputer.com)
FBI issues alert about Hive ransomware | Healthcare IT News
What is the Remote Desktop Protocol (RDP)? | Cloudflare
FBI Flash - Hive Ransomware IoCs - DocumentCloud
What Is Phishing? - Definition, Types of Attacks & More | Proofpoint US
The Top 5 Cyber Threats in the Healthcare Industry (avertium.com)
Hive ransomware group extends to cloud-based Linux variants | SC Media (scmagazine.com)
MediaMarkt hit by Hive ransomware, initial $240 million ransom (bleepingcomputer.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of the Client's compliance with any law, regulation, or standard.