Vishing vs. Smishing- Stay Educated on the Latest Cyber Attacks
Executive Summary of vishing and smishing
We’ve all been there. Someone calls your phone claiming to be from the IRS and threatens to have you arrested for non-payment of taxes. Or perhaps you receive a text message from your boss saying that he needs a favor from you and asks if you could purchase gift cards for him. Both situations sound a bit off, but no one wants to go to jail for tax evasion or get fired for saying no to their boss. So, you proceed with giving all the information needed for either scenario only to find out that you didn’t actually owe any money to the IRS or that your boss never sent you a text message. You eventually discover that you fell victim to a vishing or smishing attack, but it’s too late. The damage is already done.
Unfortunately, vishing and smishing attacks like these happen to people every day and there are no exclusions when it comes to an attackers’ next victim. Some can sense when phone calls or text messages are disguised attackers, but many fall prey to the bait. Let’s look at the differences between vishing and smishing attacks, and why it’s important for organizations to stay educated on both
what is vishing?
Vishing is a cybercrime that involves stealing information via telephone. Most of the time, an attacker will call or leave a voicemail with a message of urgency, like the phone call mentioned above regarding tax money. Vishing attacks have become popular since VoIP users are not required to provide caller ID. According to First Orion, in 2019, over 40% of all mobile calls were vishing attacks. It also appears that attackers are now focusing on the quality of their vishing attacks, rather than quantity.
First Orion also reported that 75% of all scam victims were called by scammers who already had their personal information. As a result, major companies are being victimized through vishing attacks that expose billions of customers personal data. Attackers now use this stolen information to disguise themselves as trusted companies in a sneaky strategy called Enterprise Spoofing. Because people have become aware of these vishing calls and ignore them, attackers are now impersonating legitimate businesses by spoofing their main outbound calling number.
You are more than likely to answer a phone call if your cell phone caller ID says “call from XYZ Bank” than if it was a random number, you have never seen.
Some of the information that attackers use in vishing attacks are passwords, usernames, mother’s maiden name, and social security numbers. Personal information coupled with the ability to pose as a trusted source leaves attackers with the ultimate edge over their victims. Ongoing data breaches expose billions of personal records and give attackers the ability to appear credible. A victim is six times more likely to experience loss when an attacker has their personal information.
In August 2020, the FBI and CISA issued a warning about a vishing campaign which exploited remote-working arrangements throughout the COVID-19 pandemic. Attackers were spoofing login pages for corporate Virtual Private Networks (VPNs). The goal was to steal employee credentials and use them to obtain additional personal information about the employee. Unattributed VoIP numbers were also used to call employees on their mobile phones. Attackers masqueraded as IT helpdesk professionals and faked a verification process using the stolen credentials, earning the employee’s trust.
The initial steps of the vishing campaign included threat actors registering for domains and creating phishing pages that looked like a company’s internal VPN login page. This page also captured two-factor authentication and one-time passwords. Threat actors also obtained Secure Sockets Layer (SSL) certificates, registered domains and used a variety of fake domains.
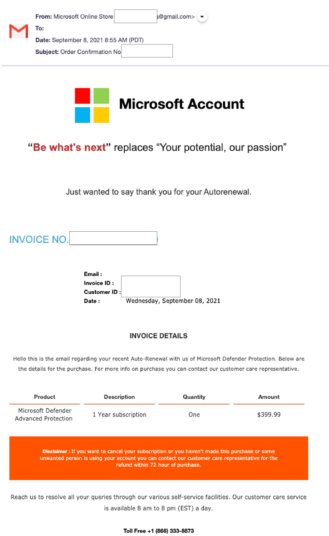
Another vishing attack includes targeting Windows PC users and allows attackers to take over their victim’s computer. The attack starts with a spoofed Microsoft Defender email, including an invoice.
Image 1: Fake Invoice
Source: Komando.com
The incredibly real email doesn’t include the typical red flags, like attachments, links, or misspellings – but it does come with a telephone number. After calling the number, the attackers will try to get their victim to download software that allows them to access their computer remotely. Once the software is downloaded, the victim leaves the door open for the attackers to steal all kinds of data and information.
what is smishing?
Smishing happens when you become a victim of a fraudulent SMS (short message services) or text message attack. Like phishing attacks, smishing attacks involve cybercriminals phishing for information for financial gain. When you receive a phishing email, the attacker laces that email with malicious links and attachments in the hopes that you will click on it. Smishing uses text messages instead of emails.
Unfortunately, when people use their cell phones, they are less wary of attacks. Part of the reason is because most people don’t see their cell phones as computers - they only see it as a way to communicate. However, like desktop computers, cell phones can be compromised as well.
According to the FBI, this phone-based version of phishing cost victims across America over $54 million in 2020. Texting is one of the most common uses of smartphones, and cybercrime aimed at mobile devices is skyrocketing. Android devices are the perfect target for malware, primarily because there are so many of them and the platform offers greater flexibility for cybercriminals. iPhone and iPad users are not immune to these attacks despite Apple’s iOS mobile technology having a good reputation for security. There isn’t a mobile operating system that can protect you from smishing attacks.
Typically, you hear about people being attacked through smishing scams after they were sent a text asking to confirm a bank transfer. By now, most are aware that this is likely to be fraudulent. But what happens when an entire company is attacked via a SIM smishing scam? In 2019, an unnamed wireless mobile company was scammed out of $16,847.47. The attackers executed a phishing and vishing attack to trick an employee into giving them their login credentials.
The attackers were seen on a trading forum asking for help with crafting a site that looked like T-Mobile’s employee login page, but T-Mobile has not been confirmed as the victim. The credentials were used to conduct unauthorized SIM swaps which aided in redirecting their victim’s phone number to bypass the two-authentication process. After completing the swap, the attackers had $16,847.47 in crypto currency transferred from their victim’s account. SIM swapping attacks like these are why AT&T faced a lawsuit for allegedly neglecting to put a stop to SIM swapping in 2018. The suit was eventually dismissed.
red flags for vishing & smishing attacks
How to recognize a Vishing attack:
- The caller has a sense of urgency
- The caller claims to represent someone of importance
- The caller asks you for personal information
- The caller asks you to “verify” your identity using passwords or account information
- The caller may say they need access to your computer
How to recognize a Smishing Attack:
- The text message has a sense of urgency
- The text message asks for personal information
- The text message asks you to validate a transaction
- The text message is immediately followed by a phone call
what is being done to stop these attacks
The Federal Communications Commission tried to stop vishing attacks by giving mobile carriers the ability to block calls by default instead of forcing them to opt-in to block calls. The legislation also accelerates the roll-out of an industry wide call-authentication standard called STIR/SHAKEN. STIR is a work group within the IETFT, an internet standards body. The IEF developed a set of protocols used to create a digital signature for a call.
The call includes information about the party calling and allows for verification of the signature by the provider. SHAKEN are simply standards for how STIR should be deployed by service providers. However, neither of these solutions address the challenges of handling legitimate business-to-business calls. If you find yourself the victim of a vishing campaign or smishing campaign, the Federal Trade Commission requests that you call them at (888) 382-1222.
avertium's recommendations for vishing
- Employee accounts should have multi-factor authentication (MFA) enabled.
- Review employee network access rights and grant new hires network access on a least-privilege scale.
- Be sure to scan for signs of unauthorized access and unusual network activity.
- To increase oversight and control network activity, break up larger networks into smaller segmented networks.
- Give network administrators separate accounts with varying access for system administrative activities.
- com states that when in doubt, you should follow the golden rule: Hang up, look up, and call back. Hang up from your call, look up the contact information of whoever just called you, and call them back to verify you aren’t being attacked.
avertium's recommendations for smishing
- Financial institutions and merchants won’t send text messages asking for updated account information or for confirmation of an ATM card code. If you receive a message from your bank or a business and it asks you to click on something, its likely fraudulent. Call the number on the back of your bank card or look the business up online and call them immediately.
- Don’t click on reply links or a phone number in a text message you’re unsure about.
- Phone numbers that don’t look like real mobile numbers, like “5000” are probably fraudulent. Attackers try to mimic email-to-text services so they can avoid providing their real phone number.
- Storing your credit card or banking information on your smartphone is not a good idea. If information is not there, attackers can’t steal it.
- Don’t respond to sketchy text messages. Simply refuse to take the bait.
how avertium is protecting our clients
- Avertium offers Incident Response Table-Top exercises (IR TTX) and Core Security Document development through KnowBe4. These exercises involve sitting down with executive staff or security team of a company and walking through a scenario of vishing or smishing. This exercise helps customers strengthen their policies and procedures surrounding these attacks.
- Avertium also offers a comprehensive new-school approach that integrates baseline testing using mock attacks through KnowBe4.
- For more information on these services, please reach out to your Account Executive.
terms
Enterprise Spoofing – When an attacker changes their caller ID to mimic a real business telephone number.
Phishing Attack – When an attacker sends you an email pretending to be from a legitimate source with the sole purpose of stealing your information.
VPN – Virtual Private Networks gives you online privacy and anonymity by creating a private network from a public internet connection. They mask your internet protocol (IP) address.
Indicators of Compromise (IoCs):
COVID-19 Vishing Attack Naming Schemes
- support-[company]
- ticket-[company]
- employee-[company]
- [company]-support
- [company]-okta
MITRE TTPs:
- [T1592] Gather Victim Host Information
- [T1586] Compromise Accounts
- [T1566] Phishing
- [T1451] SIM Card Swap
Supporting Documentation
First-Orion-Scam-Trends-Report_Summer-2019.pdf (firstorion.com)
What is a VPN? | Virtual Private Networks Explained | Norton
Smishing and Vishing: What You Need to Know About These Phishing Attacks - Tessian
What is Vishing? Voice Phishing Scams Explained - Panda Security Mediacenter
FBI Warns Companies of Vishing Attacks | CyberScout
Cyber Criminals Take Advantage of Increased Telework Through Vishing Campaign (krebsonsecurity.com)
El Paso FBI warns of new scam called 'SMiShing' that targets smartphones - KVIA
What is Smishing & How to Defend Against It | Kaspersky
Two SIM swappers phished a phone company so they could steal $16K in crypto - The Verge
Vishing Warning Signs (futurelearn.com)
This fake invoice is scaring Microsoft Windows users into paying up (komando.com)
SMS About Bank Fraud as a Pretext for Voice Phishing – Krebs on Security
Enterprise Call Spoofing Targets Consumers With Personal Data (calleridreputation.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of the Client's compliance with any law, regulation, or standard.