Threat Actor Profile – “BlackMatter” Ransomware
Who is BlackMatter?
Ransomware gangs threaten the security of companies and individuals daily. Over the past year, there has been a surge in ransomware attacks leading to long-lasting destruction. Barracuda researchers found a 64% increase in ransomware attacks, targeting health care, education, and businesses in industries such as (financial services, infrastructure, and travel, among others.
First reported by The Record, BlackMatter began making its presence known as a ransomware-as-a-service (RaaS) gang in July 2021. They claim to be a combination of the best qualities of DarkSide and REvil – two ransomware groups that are now defunct.
During the same month, the ransomware gang began posting ads on cybercrime forums (XSS and Exploit) to help them hack into large enterprise networks with revenues of $100m or more within the US, the UK, Canada, and Australia, offering to pay $100,000 for exclusive access. The gang is only interested in high-value networks that have between 500 and 15,000 hosts.
In May 2021, following law enforcement retaliation after the Colonial Pipeline ransomware incident attributed to DarkSide, ransomware ads were banned on cybercrime forums. Skillfully, BlackMatter found a way around the ban by advertising for “initial access brokers” instead of directly advertising its ransomware operation. If BlackMatter gains access to these networks, they could have the ability to encrypt operating system versions and architectures, such as:
- Windows Systems (via SafeMode)
- Linux (Ubuntu, Debian, CentOS)
- VMware ESXi 5+ virtual endpoints
- NAS devices (Synology, OpenMediaVault, FreeNAS, and TrueNAS)
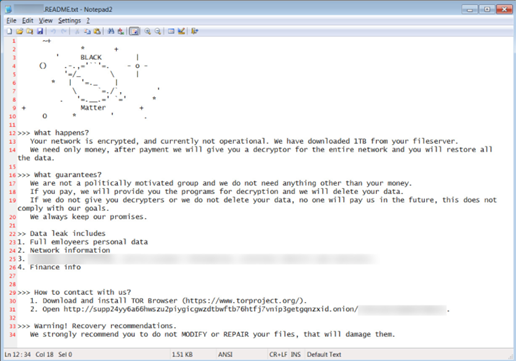
Encrypting these operating systems means that BlackMatter ransomware could take over a company’s internal systems and deploy their file-encrypting payload. The gang also has a website on the dark web called a leak site, and thehe intention is to publish stolen data from the victims of large enterprises if the hacked company chooses not to pay up in exchange for decryption.
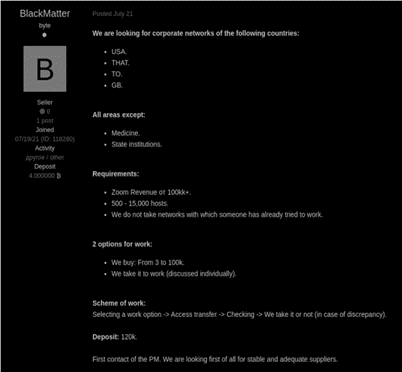
In August 2021, the Cyble research Lab discovered that BlackMatter has already started to make its rounds with exposing financial information. Pine Labs, an Indian merchant platform company providing financing and retail transaction technology, was recently attacked by the group. Not only did this ransomware attack affect multiple financial institutions that use Pine Labs services, but more than 500,000 unique records of contact information were exposed. In June 2021, BlackMatter also was successful in targeting several victims with ransom demands ranging from $3 to $4 million, eventually receiving a $4 million ransom from one victim to delete stolen data.
Ransomware Gangs – Cyberattacks on the Colonial Pipeline and Kaseya
In May 2021, a ransomware attack on a major US fuel pipeline, Colonial Pipeline, led to a supply disruption that made national headlines. The intrusion was the work of an affiliate of the ransomware-as-a-service (RaaS) ring, DarkSide. The attack was so disruptive that Colonial Pipeline had to shut down its operational technology (OT) network, cutting off much of the gasoline supply to the eastern United States.
The creators of DarkSide surfaced in the summer of 2020, claiming to have ethical standards which forbid them from targeting certain industries (non-profit organizations, healthcare organizations, hospitals, etc.). The gang also claimed that their goal was to make money, not create issues for society.
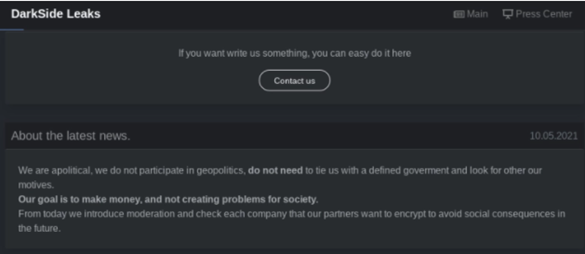
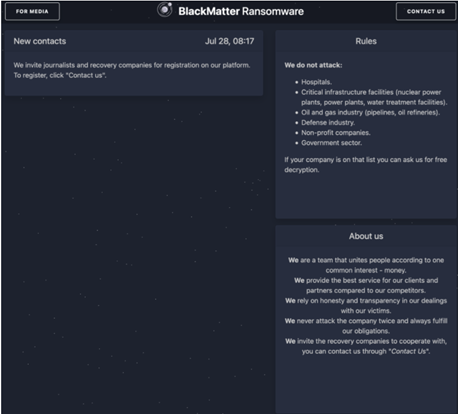
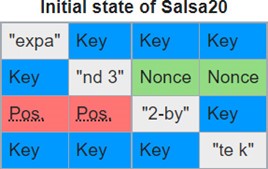
Some analysts are convinced that DarkSide and BlackMatter are one and the same due to the similarities between the goals of BlackMatter and DarkSide. Both groups have a set of rules that prohibits them from attacking critical infrastructure and both groups made it clear that their goal is to make money and “take care of their families”. In addition to appearing to have the same goals, DarkSide and BlackMatter also use the same encryption algorithm – a custom Salsa20 matrix.
In July 2021, a different ransomware gang hit Kaseya, a US-based software provider. REvil, a Russia-linked ransomware gang, targeted Kaseya by using their own remote computer management tool, Kaseya VSA. The heist affected 60 of its managed service provider customers and more than 1,000 small and medium-sized enterprises.
At one point, it appeared as if REvil and DarkSide were working side by side for almost a year. However, since the attacks on Colonial Pipeline and Kaseya, both REvil and DarkSide seem to have vanished from the internet, or have they?
Ransomware Gangs – Link Between DarkSide, REvil and BlackMatter
According to ComputerWeekly.com, BlackMatter admitted that they were inspired by DarkSide and have previously worked with some of its affiliates, but they are their own entity with their own identity. Despite BlackMatter claiming to not be involved with DarkSide, researchers aren’t so convinced.
It’s no secret that, after high profile attacks, ransomware gangs tend to disband and rename themselves to evade law enforcement. Knowing this, researchers have been trying to figure out the connection between BlackMatter, REvil and DarkSide.
Threat intelligence firm, Flashpoint, learned that an unknown user with the handle “BlackMatter” announced the launch of “BlackMatter Ransomware” on two Russian forums. On July 19, 2021, the user stated, “The project has incorporated in itself the best features of DarkSide, REvil and LockBit." Flashpoint further discovered that REvil previously labeled their Windows Registry key “BlackLivesMatter”, and that key name was present in the version of REvil used to attack Kaseya.
Additionally, ransomware expert Fabian Wosar confirmed that BlackMatter’s encryption routines match DarkSide. BleepingComputer discovered a decryptor from the ransomware gang and gave it to Wosar to analyze. Wosar stated that the group used the same encryption methods that DarkSide used in their attacks.
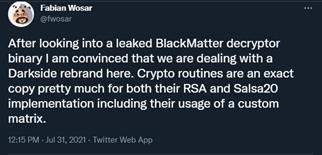
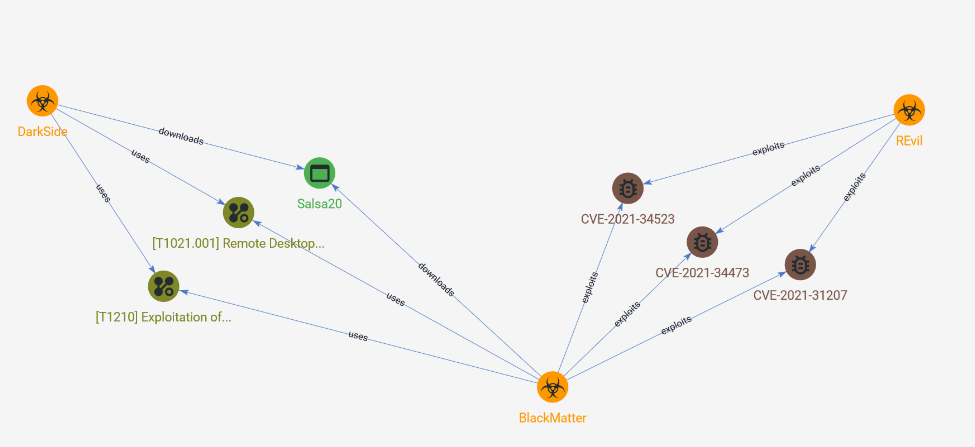
Our partner, Advanced Intel, also believes that members of ransomware gangs REvil and DarkSide are now affiliated with BlackMatter. In a report sent to Avertium, the company’s researchers discovered a BlackMatter ransomware attack that utilized some of DarkSide and REvil’s tactics.
On August 17, 2021, BlackMatter leaked critical information from a Louisville, Kentucky based law firm. The gang was able to access this information by compromising the firm’s RDP (Remote Desktop Protocol)– the same method used in the cyberattack against Colonial Pipeline. Advanced Intel’s research shows that DarkSide has specifically been initiating attacks by using infrastructural compromises including RDPs, VPNs, and VDNI to move from the target victim’s perimeter to the core domain. After using RDP as an entry point, the group investigates the environment and network until they can quickly and silently steal major critical data. By deferring the encryption phase of attack, they position themselves to maximize damage and profit.
Advanced Intel also discovered that BlackMatter has a very developed set of victim access verification and attack moderations, which were created to prevent random attacks such as the one that occurred against Colonial Pipeline by a DarkSide affiliate. Because of these countermeasures, Advanced intel believes it is likely that former DarkSide leadership is behind the firm’s breach.
A representative from BlackMatter told the Recorded Future’s expert threat intelligence analyst, Dimitry Smilyanets, that they learned several lessons from the supposed disbandment of REvil and DarkSide, believing that their exit had something to do with the “geopolitical on the world stage”. The representative further stated that the group took the United States’ offensive cyber operations and other political factors into account and are now confident that they can withstand those offensive cyber capabilities.
How is REvil linked to all of this? It appears that some of REvil’s tactics are also incorporated by BlackMatter. Advanced Intel stated that the group even mimics REvil’s ransom note. In the spring of 2021, REvil weaponized a novel attack vector for ransomware purposes, exploitation of software and protocol vulnerabilities.
Advanced Intel identified several zero-day vulnerabilities throughout Microsoft Exchange Server environments which were exploited and successfully used by REvil to conduct data exfiltration attacks. REvil was especially prominent in this method, using the server’s CVE to compromise Acer’s assets in March 2021. Advanced Intel considers these CVE’s a likely attack vector for the compromised law firm.
Recently, an organization was hit by REvil in what appears to be a new attack. The victim was attacked by what looks like a patched REvil payload. Woser believes that whoever is behind this most recent attack may be affiliated with one or more ransomware-as-a-service operations. However, he does not believe the attacker is an original member of REvil, rather someone who just had access to the REvil source code.
While it is not clear if DarkSide and REvil have rebranded as BlackMatter, there are many similar characteristics between the ransomware gangs that make it hard to believe they haven’t. What is clear is that BlackMatter has a different strategy than previous ransomware-as-a-service gangs and is in it for the long-run.
Indicators of Compromise (IoCs) – DarkSide
- Rumahsia[.]com
- dark24zz36xm4y2phwe7yvnkkkkhxionhfrwp67awpb3r3bdcneivoqd.onion
- f6fba207c71d1f53f82d96a87c25c4fa3c020dca58d9b8a266137f33597a0b0e
- 3ba456cafcb31e0710626170c3565aae305bc7c32a948a54f0331d0939e0fe8a
- 4d03e3db39adaf57df53181429706aa854878026
- 156335b95ba216456f1ac0894b7b9d6ad95404ac7df447940f21646ca0090673
- 2715340f82426f840cf7e460f53a36fc3aad52aa
- f587adbd83ff3f4d2985453cd45c7ab1
- baroquetees[.]com
- 176.103.62.217
Indicators of Compromise (IoCs) – REvil
- e2a24ab94f865caeacdf2c3ad015f31f23008ac6db8312c2cbfb32e4a5466ea2
- d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e
- 8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd
- 2093c195b6c1fd6ab9e1110c13096c5fe130b75a84a27748007ae52d9e951643
- e1d689bf92ff338752b8ae5a2e8d75586ad2b67b
- d56cc8832fbf9af171359f34847588afbeb41249
- 656c4d285ea518d90c1b669b79af475db31e30b1
- 5162f14d75e96edb914d1756349d6e11583db0b0
- a47cf00aedf769d60d58bfe00c0b5421
- 7ea501911850a077cf0f9fe6a7518859
Indicators of Compromise (IoCs) – BlackMatter
- bc1qlv2qdmylyuw62zw8qcd4n3uh84cy2edckv3ds7
- 379ebd1eff6f8685f4ff72657626bf6df5383d87
- ba375d0625001102fc1f2ccb6f582d91
- 72ed32b0e8692c7caa25d61e1828cdb48c4fe361
- 10d6d3c957facf06098771bf409b9593eea58c75
- a55bc3368a10ca5a92c1c9ecae97ced9
- 3f9a28e8c057e7ea7ccf15a4db81f362
- 6a7b7147fea63d77368c73cef205eb75d16ef209a246b05698358a28fd16e502
- e48c87a1bb47f60080320167d73f30ca3e6e9964c04ce294c20a451ec1dff425
- 2c323453e959257c7aa86dc180bb3aaaa5c5ec06fa4e72b632d9e4b817052009
- c6e2ef30a86baa670590bd21acf5b91822117e0cbe6060060bc5fe0182dace99
- d9006d5c753c364b27388831f03332f404b719a66f344ce8b1a340da24e93d53
- 51.79.243.236
- Mojobiden[.]com
- 206.188.197.206
- 7f6dd0ca03f04b64024e86a72a6d7cfab6abccc2173b85896fc4b431990a5984
- 22d7d67c3af10b1a37f277ebabe2d1eb4fd25afbd6437d4377400e148bcc08d6
- e324a2c8fae0d26b12f00ac859340f8d9945a9c1
- 80a29bd2c349a8588edf42653ed739054f9a10f5
- d0512f2063cbd79fb0f770817cc81ab3
- 598c53bfef81e489375f09792e487f1a
- 072158f5588440e6c94cb419ae06a27cf584afe3b0cb09c28eff0b4662c15486
- b06e2455a9c7c9485b85e9bdcceb8078
- a63304592f422656d7abcb086915f9e799ad4641
- paymenthacks[.]com
Avertium’s Recommendations
- Maintain offline, encrypted backups of data and regularly test backups
- Create, and exercise a basic cyber incident response plan and a communications plan
- Mitigate internet-facing vulnerabilities and misconfigurations
- Reduce the risk of phishing emails by enabling strong span filters and implementing a cybersecurity user awareness training program
- Practice good cyber hygiene
- Ensure antivirus and antimalware software signatures are up to date
- Implement application allow listing
- Ensure user privileged accounts are limited
- Employ MFA
- Implement cybersecurity best practices
How to Respond to a Ransomware Attack
- Contact Avertium for DFIR (Digital Forensics and Incident Response).
MITRE TTPs
[T1595] Active Scanning
[T1589] Gather Victim Identity Information
[T1590] Gather Victim Network Information
[T1190] Exploit Public-Facing Application
[T1133] External Remote Services
[T1040] Network Sniffing
[T1486] Data Encrypted for Impact
[T1039] Data from Network Shared Drive
[T1219] Remote Access Software
Terms
Ransomware – A form of malware used to encrypt files on a device, rendering any files and the systems that rely on them unusable. Ransomware attacks target and threaten to sell/leak data or authentication information if a ransom is not paid.
Initial Access Brokers – Individuals with access to hacked enterprise networks.
Ransomware-as-a-service (RaaS) – A subscription-based model that enables affiliates to use already-developed ransomware tools to execute ransomware attacks. Affiliates earn a percentage of each successful ransom payment. Ransomware as a Service (RaaS) is an adoption of the Software as a Service (SaaS) business model.
Salsa20 Matrix (also called a cipher) – A family of 256-bit stream ciphers designed in 2005.
Supporting Documentation
https://www.cisa.gov/stopransomware/ransomware-101
https://www.cisa.gov/sites/default/files/publications/CISA_MS-ISAC_Ransomware%20Guide_S508C_.pdf
https://news.sophos.com/en-us/2021/08/09/blackmatter-ransomware-emerges-from-the-shadow-of-DarkSide/
https://www.bankinfosecurity.com/revil-ransomware-operation-returning-as-blackmatter-a-17160
https://www.crn.com/news/security/revil-ransomware-targets-acer-s-microsoft-exchange-server-source
https://cr.yp.to/snuffle/salsafamily-20071225.pdf
https://attack.mitre.org/techniques/T1595/
https://attack.mitre.org/techniques/T1589/
https://attack.mitre.org/techniques/T1590/
https://attack.mitre.org/techniques/T1190/
https://attack.mitre.org/techniques/T1133/
https://attack.mitre.org/techniques/T1040/
https://attack.mitre.org/techniques/T1486/
https://attack.mitre.org/techniques/T1039/
https://attack.mitre.org/techniques/T1219/
Note: The Avertium Threat Report analyzes one current threat that has been shared by threat intelligence networks across the globe. Used internally by the Avertium CyberOps Team, this report will outline a “top-of-mind” threat and how it ought to be addressed accordingly.
This informed analysis is based on the latest data available.