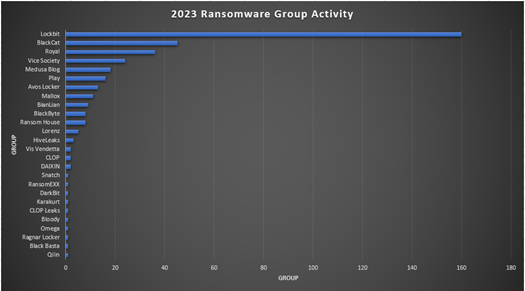
2023 Ransomware Group Activity Trends
Executive Summary
In January 2023, researchers saw a decrease in victim posting rates amongst ransomware groups. The month also showed a 41% decrease compared to December 2022. Although there was a decrease in ransomware victims amongst all ransomware groups in January, LockBit stayed at the forefront of ransomware activity. Avertium’s Threat Intelligence Report featuring the worst cyber attacks of 2022, predicted that although the return on investment was dropping for ransomware gangs, ransomware activity would continue to be a major issue for organizations in 2023.
Since the beginning of the year, the most disruptive ransomware attacks have been at the hands of five groups – LockBit, BlackCat (ALPHV), Royal, Vice Society, and Medusa. LockBit kicked off 2023 as January’s most prolific ransomware-as-a-service (RaaS) and they likely will continue to be unless forcefully stopped.
BlackCat, Royal, Vice Society, and Medusa are close behind with ransomware attacks and also show no signs of letting up. Vice Society experienced a remarkable surge of 267% in their activity, primarily targeting victims within the Education sector. Among the top five groups in January, only Vice Society showed a rise in their activity when compared to December 2022. Let’s take a look at this year’s ransomware group trends and what we can expect from the threat actors as we move forward.

ransomware group activity
In comparison to January 2022, there was a 12.9% reduction in the yearly rate of publicly reported victims, and a significant decline of 41% after December 2022. The posting rate remained constant across all groups, with a notable surge towards the end of the month. The top ten countries targeted in January were the United States, United Kingdom, Germany, Australia, Canada, France, Portugal, Belgium, India, and Italy. Below, you’ll find Avertium’s summary of 372 reported ransomware incidents between January and February of 2023.
Image 1: Reported Ransomware Incidents Between January and February 2023
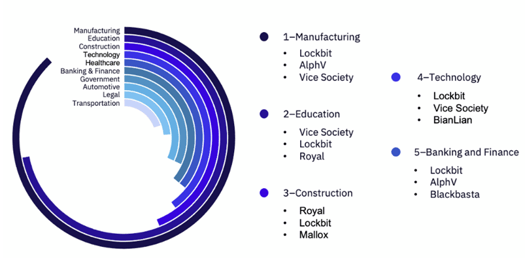
LockBit had victims in 23 countries, which is twice as many countries as any other group. Regarding the United States, LockBit, Royal, and BlackCat are the most acitve groups. So far, the U.S. represents 38.6% of all targeted victims. In January 2023, researchers observed targeting against 37 industries. Lockbit, Vice Society, and Royal were the most active groups among the top targeted industries.
The Manufacturing industry witnessed 22 publicly reported victims, whereas Education and Construction had 18 and 11 victims, respectively. Although most industries witnessed a decline in victim count, Aerospace, Defense & Military, Construction, and Telecom observed a marginal increase as compared to the previous month.
Image 2: Ransomware Group Activity Across Industries
Source: Security Boulevard
lockbit ransomware group
Located in the Netherlands, LockBit started off 2023 by continuing to be the top RaaS group. Last month, LockBit released a third version of their ransomware called LockBit Green. Previous variants are tracked as LockBit Red and LockBit Black. LockBit’s affiliates obtain LockBit Green by using the builder feature on the LockBit portal.
LockBit claims to have an unlimited amount of affiliates from all countries. Avertium’s Cyber Threat Intelligence Team (CTI) was able to find LockBit’s affiliate rules which are as follows:
- You must be active to work with our software package.
- It is strictly forbidden to give access to the panel to other people. If you work with an affiliate, you may be given a sub-account with correspondence reading rights for your affiliate. You should be aware that your partner may turn out to be a mole or be arrested by the police at any moment.
- It is forbidden not to fulfill agreements that you stated in chat before payment. For example, promising to give a file tree, and then not doing so.
- It is imperative to download valuable information from every company you attack. If you can't bypass your firewall settings and you don't have the ability to download the information, then perhaps our proprietary StealBit Stealer can help you.
- It is not forbidden to work with competitors, but be sure to report it and explain why and what you like from your competitors, we will implement any of your worthy wishes, we care very much about progress and constant development.
Additionally, the researchers at vx-underground observed that LockBit made modifications to their ransomware variant designed for VMware ESXi. ESXi is a type-1 hypervisor developed by VMware for deploying and serving virtual machines in enterprise environments. The development is not unexpected, given the recent rise in ransomware attacks targeting ESXi servers.
Since at least October 2021, LockBit has been utilizing a VMware ESXi encryptor component, and they have recently updated their ESXi ransomware variant to ensure that it can still serve as a means of accessing corporate networks. However, this does not mean that the LockBit Green variant was developed from scratch. The researchers at SentinelOne analyzed a sample of the new variant and found that it is 89% similar to the leaked source code of Conti Ransomware, specifically the group’s v3 version. The modifications made to the source code to align with the LockBit brand are minimal, such as changes to the component responsible for generating the ransom note.
This year, LockBit launched a ransomware attack against the United Kingdom’s Royal Mail, threatening to leak stolen data if their ransom demands were not met. The Royal Mail faced severe disruption for six weeks and is just recently restoring international shipping. LockBit kept their word and published the Royal Mail’s stolen data but it is not clear if the mail carrier negotiated a ransom payment with the threat actors. The ransom payment was set at 80 million euros before it was lowered to 40 million euros.
Blackcat (alphv) ransomware group
BlackCat, also known as ALPHV, has also been very active this year. BlackCat is known for being a highly sophisticated ransomware variant that codes its malware in the Rust programming language. Rust presents the same benefits to malware authors as it does to any other developer, including much easier porting between platforms, improved memory management and reduced dependencies. This combined with it’s relatively recent introduction present some additional challenges for malware reversers.
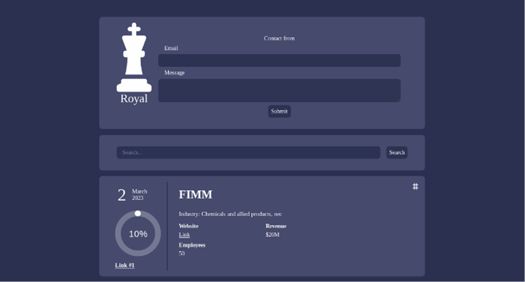
Image 3: BlackCat 'Blog' Site

BlackCat ransomware was first identified in November 2021. Although BlackCat claims to be an apolitical group that doesn’t attack the healthcare sector, one of the victims on their leak site, in 2021, was from the healthcare industry. However, BlackCat stated that while they don’t attack medical institutions, their rule doesn’t apply to pharmaceutical companies or private clinics.
In December 2022, the HHS Health Sector Cybersecurity Coordination Center (HC3) issued an advisory about BlackCat, urging healthcare organizations to remain vigilant. By February 2023, the group was responsible for a ransomware attack against Lehigh Valley Health Network (LVHN). At the beginning of the year, BlackCat claimed an attack on another healthcare organization, EHR vendor NextGen Healthcare. They posted an alleged sample of NextGen data on a leak site but later removed the listing for unknown reasons. In 2022, BlackCat was demanding ransoms as high as $1.5 million.
royal ransomware group
In addition to sounding the alarm about BlackCat, HC3 also waned healthcare organizations about Royal ransomware in December 2022. Royal is a fairly new ransomware group and was initially observed in early 2022. Their top targets are within the U.S.
What is interesting about Royal is that they originally used BlackCat’s encryptor before transitioning to their own Zeon encryptor. The Zeon encryptor generates a ransomware note similar to the now defunct group, Conti. In October 2022, the threat actors behind Zeon were impersonating healthcare patient data software. After initial infection, Royal will leverage BlackBasta, QBot, and Cobalt Strike for multi-stage attacks. The most recent malware variants of Royal Ransomware now support encrypting Linux devices, including targeted attacks on VMware ESXi virtual machines. The new Linux Royal ransomware variant is executed using the command line.
Image 4: Royal Shame Site
Ransomware groups' strategic shift towards targeting ESXi virtual machines is in line with the current trend among enterprises, who are increasingly adopting VMs due to their enhanced device management and efficient resource utilization capabilities. To illustrate how vulnerable VMware ESXi servers are, and a massive campaign was launched worldwide at the beginning of February 2023, using a new ransomware variant called ESXiArgs, to scan for and encrypt unpatched servers targeting ESXi devices.
vice society ransomware group
Next on our list for 2023 is Vice Society, who has posted victims on their leak site from 10 countries. The group is a Russian ransomware gang that is known for attacking the education and healthcare sector. In June 2022, Avertium published a Threat Intelligence Report regarding the top five cyber threats in education and ransomware was named as the number one threat.
The threat actor has been observed exploiting vulnerabilities such as PrintNightmare (CVE-2021-1675) and CVE-2021-34527 to escalate privileges. They also use tools such as SystemBC, PowerShell Empire, and Cobalt Strike to move laterally.
Initially appearing in the summer of 2021, Vice Society is a group that didn’t make headlines until September 2022 when the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) warned that the group was targeting the education sector. The FBI and CISA stated that they expected an increase in attacks after the start of the 2022/2023 school year due to cyber criminal groups seeing opportunity.
At the beginning of the 2022/2023 school year, Vice Society launched a ransomware attack against the second largest school district in the U.S. – LAUSD. As predicted by the FBI and CISA, Vice Society’s attacks on education continued into 2023. In February 2023, Vice Society was found responsible for a ransomware attack against the New-York based liberal arts college,
Mount Saint Mary College. The actual attack took place in December 2022, but the details regarding the attack were published on Vice Society’s data leak site in February 2023 – a result of the college refusing to pay the demanded ransom.
A similar event happened with LAUSD. Vice Society attacked the district in September 2022, but they didn’t leak student data until February 2023. The personal health information of around 2,000 current and former students of Los Angeles schools has been leaked and made available on the dark web. The stolen records included mental health, attendance, academic results, and disciplinary records. Also in February, the ransomware group attempted to extort the United Kingdom school, Guildford County School, by posting the files of at-risk children.
medusa ransomware group
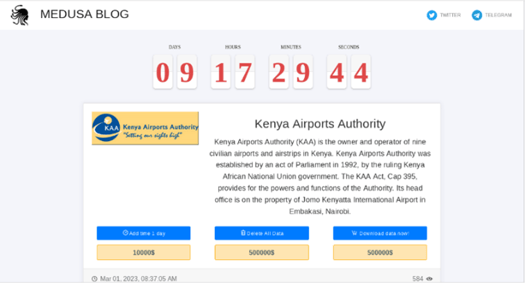
While Medusa Blog appears to be a new ransomware group that emerged in 2023, very little is known about the group other than attacks that surface on the group’s Tor site. So far, the group has claimed 13 victims, including the oil and gas regulator company PetroChina Indonesia, and Kenya Airports Authority.
Image 5: Medusa Attacked Kenya Airports Authority
Although reports discuss the ransomware group as separate from the MedusaLocker ransomware group, Avertium’s Cyber Threat Intelligence Team is not completely convinced the groups are not related. MedusaLocker is a ransomware group that emerged in 2019. During 2019, MedusaLocker took advantage of the chaos surrounding the COVID-19 pandemic and launched phishing and spam email campaigns to gain initial access to organizations, specifically targeting healthcare.
By May 2022, MedusaLocker started to rely on vulnerabilities in Remote Desktop Protocol (RDP). However, by November 2022, MedusaLocker appeared to go dark and has not attacked anyone since. Although MedusaLocker’s ticket site is active, their blog site appears to be down.
Image 6: MedusaLocker's Ticket Site
Image 7: MedusaLocker's Offline Tor Site
In January 2023, Medusa Blog surfaced coincidentally. While its predecessor, MedusaLocker, targeted the healthcare industry, Medusa Blog has been setting its sights on oil and gas, airports, and engineering sectors. However, the timing of MedusaLocker's abrupt disappearance and the emergence of Medusa Blog raises red flags and warrants a deeper investigation into the possible connection between the two Medusa strains' activities.
Also, it's worth noting that the 2023 Copyright displayed on Medusa Blog's Tor site reads "Medusa Team", rather than "Medusa Blog" or "MedusaLocker". This observation raises the possibility that the two ransomware variants are linked and operated by the same group.
Image 8: Medusa Blog Tor Site

defense: increase cyber resilience
In a recent report from the blockchain data company Chainalysis, analysis showed that extortion payments for ransomware are on the decline. The decline can be attributed to the disruption of major ransomware groups such as Conti and Hive, a decrease in cryptocurrency values, and businesses finally taking proactive measure with cyber security. However, even with extortion payments declining, that does not mean security professionals should completely shift their focus to other attack vectors and tactics.
There are plenty of high-profile ransomware attacks (Dole, Regional Medical Group, and City of Oakland) that highlight the fact that organizations cannot afford to let their guard down. Organizations may attempt to minimize their exposure to ransomware by acquiring cybersecurity insurance policies. While cybersecurity insurance is necessary, organizations should also increase their ransomware preparedness. To increase cyber resilience in ransomware response, consider the following:
- Evaluate the strategic ransomware preparedness of endpoints by identifying essential controls, such as anti-virus/anti-malware, endpoint protection, and endpoint detection and response solutions, as well as device management tools.
- Enable ransomware cyber hygiene measures across endpoints by implementing application resilience policies that ensure that critical security applications and device management tools are installed and functioning as intended.
- Evaluate the security posture of devices by continuously detecting and reporting on the status of anti-malware, detection, and response software installed on endpoint assets.
- Accelerate the recovery process by collecting accurate insights, executing customized workflows, and automating commands for device recovery. This can be achieved by leveraging a library of custom scripts to facilitate tasks such as identifying infected and encrypted machines, quarantining endpoints by disabling networking or unlocking specific device ports, or supporting device re-imaging.
- Identify sensitive data by scanning devices for financial information, social security numbers, personally identifiable information (PII), protected health information (PHI), and intellectual property. This process enables organizations to locate at-risk devices and ensure that proper backup measures are in place using existing tools.
- Implement a data protection program that includes policies, classification, encryption/DLP, and proactive monitoring across all sensitive data.
how avertium is protecting our customers
Because the cyber landscape is always changing, it is imperative to be aware of new cyber attack strategies and techniques. Avertium is here to keep you informed and to keep your organization safe. We recommend the following services for the best protection against ransomware attacks:
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Fusion MXDR is the first MDR offering that fuse together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- It is also recommended by Avertium and the FBI that your business require multi-factor authentication (MFA) to remotely access networks.
- Implementing network segmentation and filtering network traffic to stop phishing emails from reaching victims is also helpful.
- Reach out to your Service Delivery Manager or Account Executive if you need assistance applying any of the above recommendations.
News: How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber Efforts
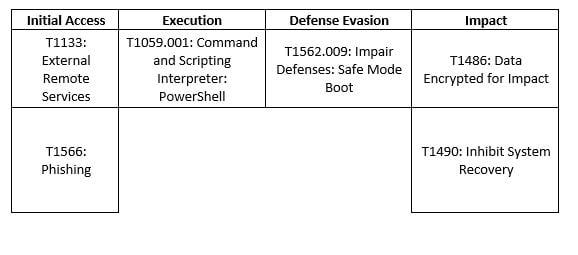
MITRE MAP
LockBit
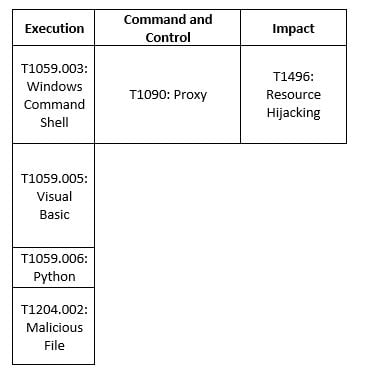
BlackCat

Royal
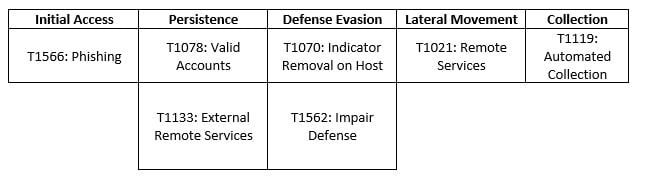
Vice Society
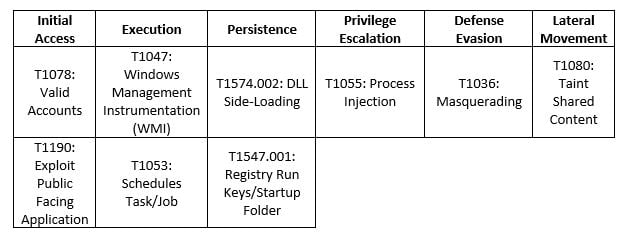
Medusa
INDICATORS OF COMPROMISE (IoCs)
For up-to-date IoCs, please click on the links below for each Threat Actor:
SUPPORTING DOCUMENTATION
Ransomware Gang Conti Has Re-Surfaced and Now Operates as Three Groups: TRM Labs (coindesk.com)
GRIT Ransomware Report: January 2023 - Security Boulevard
Ransomware review: February 2023 (malwarebytes.com)
Ransomware Attacks: Don’t Let Your Guard Down - SecurityWeek
CrowdStrike2023GlobalThreatReport.pdf
#StopRansomware: Vice Society | CISA
Vice Society ransomware attack confirmed by Mount Saint Mary College | SC Media (scmagazine.com)
Lehigh Valley Health Network Hit By BlackCat Ransomware Attack (healthitsecurity.com)
LockBit ransomware gang releases LockBit Green version | Cybernews
Royal Mail restores global shipping weeks after LockBit ransomware attack | TechCrunch
202301121300_Royal & BlackCat Ransomware_TLPCLEAR (hhs.gov)
Linux version of Royal Ransomware targets VMware ESXi servers (bleepingcomputer.com)
Ransomware gang leaked Los Angeles student health records online | Reuters
Lockbit Ransomware Attack - France Location - AlienVault - Open Threat Exchange
BlackCat/ALPHV Ransomware - AlienVault - Open Threat Exchange
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.