BlackCat Ransomware & Triple Extortion (Analysis & Tactics)
During 2021, the United States observed an increase in highly sophisticated ransomware attacks against 16 U.S. critical infrastructure sectors. The sectors include Defense Industrial Base, Food and Agriculture, Government Facilities, and Information Technology. Australia and the United Kingdom also observed an increase with ransomware actors targeting charities, public services, and local government – with the United Kingdom recognizing ransomware as their biggest cyber threat.
With ransomware techniques and tactics continuing to evolve, threat actors are starting to grow in technological sophistication. Recently, threat actors (known as ALPHV) behind the new ransomware-as-a-service (RaaS) BlackCat have proven that attackers are learning from past mistakes and are developing new ways to get the financial reward they seek. Let’s look at BlackCat ransomware and how they fit into our current threat intelligence landscape.
blackcat ransomware
BlackCat ransomware was discovered by researchers in November 2021. The threat actors recruit affiliates to perform corporate breaches and encrypt devices. So far, the cybercriminals (who only go by the name ALPHV) behind the ransomware have compromised more than twenty companies and have named those companies on their leak site. Currently, ALPHV is recruiting affiliates from several ransomware gangs – including BlackMatter, REvil, and DarkSide. They have also offered affiliates up to 90% of any ransom paid by an organization.
The BlackCat leak site has been active since early December 2021 and there is speculation that the total number of victims, including those who paid a ransom, is far greater than twenty. Most of the time, victims who pay ransom don’t want to risk exposure. ALPHV’s ransom demands range from $400,000 to $3 million, with victims being given the opportunity to negotiate a lower amount if they choose to pay a ransom. They can also choose to pay in privacy-preserving monero or bitcoin, but paying in bitcoin adds 15% to the ransom amount.
Although the largest number of the threat actor’s victims are in the U.S., ALPHV and their affiliates have attacked organizations in the Philippines and Europe. The sectors being attacked are retail, transportation, construction and engineering, telecommunication, and pharmaceuticals. Although ALPHV claims to be an apolitical group who doesn’t attack the healthcare sector, one of the victims on their leak site was from the healthcare industry. However, ALPHV stated that while they don’t attack medical institutions, their rule doesn’t apply to pharmaceutical companies or private clinics.
tactics, techniques, and procedures
BlackCat ransomware is a highly customizable ransomware that allows for attacks on a wide range of corporate environments. Targeting both Linux and Windows systems, BlackCat is coded in Rust (written in Russian), which is a programming language. Researchers believe that this is the first time a ransomware group has used Rust to write a ransomware strain.
Cyber security analysts state that Rust is a much more secure programming language compared to C and C++. Because Rust is so secure, it will be difficult to find coding weaknesses. Security defenders often look for those weaknesses in ransomware strains and if more threat actors are shifting toward Rust, it will be more difficult to find the weak areas. By using Rust, ALPHV’s operators are able to compile it against various operating system architectures. Rust is a customizable programming language, which means that they have the ability to pivot and individualize attacks.
Due to its fast and high performance, powerful web application development, low overhead for embedded programming, and memory management resolution; Rust has gained momentum and is a force to be reckoned with.
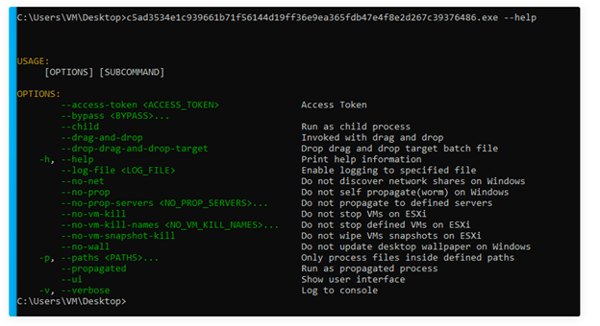
Image 1: BlackCat Execution
To maintain longevity, BlackCat uses the following flag to execute their ransomware: --access–token. This makes it harder to analyze BlackCat in sandboxed environments.
Source: Palo Alto
BlackCat has several evasion tactics that are used in an effort to impair or disable system defenses and stop certain applications from locking files open on disk – which may cause problems when trying to encrypt those files. Additionally, BlackCat tries to kill several processes and services to prevent any security solutions or backups an organization may have. Please see the below partial process list:
|
agntsvc |
dbeng50 |
dbsnmp |
encsvc |
excel |
infopath |
|
Isqlplussvc |
msaccess |
mspub |
mydesktopqos |
mydesktopservice |
notepad |
|
ocautoupds |
ocomm |
ocssd |
onenote |
oracle |
outlook |
|
powerpnt |
sqbcoreservice |
*sql* |
steam |
synctime |
tbirdconfig |
|
thebat |
thunderbird |
visio |
wiword |
wordpad |
xfssvcco |
|
bedbh |
vxmon |
benetns |
bengien |
pvlsvr |
beserver |
For persistence, BlackCat excludes key system and application folders from encryption, as well as key components. This is done so the system and ransomware isn’t rendered inoperable. Folder exclusions include but are not limited to:
|
system volume information |
intel |
application data |
$recycle.bin |
|
mozilla |
boot |
appdata |
perflogs |
|
windows |
|
config.msi |
tor browser |
File name exclusions include but are not limited to:
|
desktop.ini |
thumbs.db |
ntuser.dat |
windows.old |
|
ntldr |
boot.ini |
iconcache.db |
autorun.inf |
Files with extensions matching the following are also avoided:
|
themepack |
bin |
idx |
diagpkg |
|
nls |
lock |
sys |
386 |
|
mpa |
cur |
spl |
Ps1 |
Promoted in Russian speaking hacking forums, BlackCat was named as such due to a black cat favicon being used on every victim’s Tor payment site. Researchers from Trend Micro found that not only does BlackCat encrypt data, steal data before ransomware deployment, and name-shame victims, but they also conduct a distributed-denial-of-service (DDoS) attack if victims don’t pay the ransom by the deadline.
Most are familiar with double extortion as a known technique amongst ransomware gangs. This technique typically involves ransomware gangs stealing sensitive data before infecting networks and systems with ransomware. The stolen data is then used to extort the victims into paying the demanded ransom. If the ransom is not paid, the threat actor will leak the stolen data on a data leak site. ALPHV takes things a step further by adding a third layer to their extortion model – a DDoS attack if the demanded ransom isn’t paid by their deadline. Cyber security researchers are calling the third layer triple extortion.
how do blackcat's features work?
When ALPHV interviewed with The Record, they listed the following as options available exclusively for adverts (advertisers or affiliates) who have reached the $1.5 million mark in payments:
- Calls - Outsourced solutions for calls. If communication with the victim is lost, you can try to establish contact by phone, in extreme cases, inform competitors about the leak. Not yet integrated into the panel, works in manual mode.
- DDoS - Own botnet for performing the most powerful DDoS attacks. Everything is clear here. Not yet integrated into the panel, works in manual mode.
- Brute - Own GPU data center + outsourcing rented facilities, own dictionaries, and rules. Currently is not available. In the future, it will allow adverts to break hashes in the panel.
- Mixer - This is not our mixer at all : ) There is no process of mixing coins in our platform. When performing an operation, our coins just go into the classic mixer for subsequent manipulations, and we get absolutely clean and verified coins, which even the most diligent exchange market will be happy with.
- Mega - Own distributed onion storage that simplifies the negotiation process for both our adverts and victims. Most dialogues begin with a request for a list/content of stolen files. We try to teach adverts to upload files to our data center immediately or even before the encryption process itself. In the future, this will allow sharing data on the volume/number of files, a file tree, and/or even a file shredder log to confirm the safe deletion of all existing files to the victim automatically; and today the storage allows you to avoid blocking from file hosting and simplifies the process of managing files between advert and victim. Already integrated into the panel, works automatically.” ALPHV – The Record
The success of BlackCat is likely due to the fact that they recruit affiliates by posting ads in forums like Ransomware Anonymous Market Place (RAMP). During their interview with The Record, BlackCat stated that they believe there is no comparative software on the market. They provide high-quality software as well as a full range of services related to ransom (metaverse or premium concierge). They believe they are in a different weight category, and they don’t recognize other ransomware groups as competitors or business partners.
blackmatter & darkside
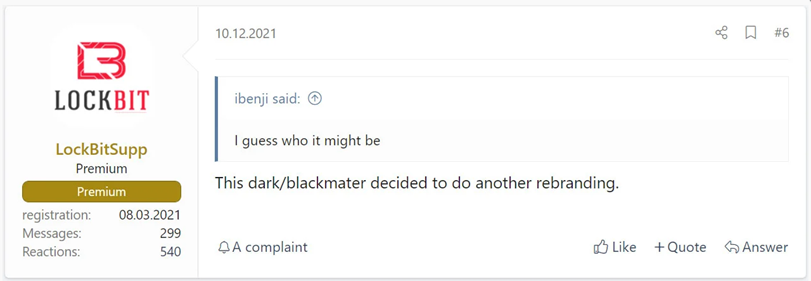
Cyber security researchers believe that BlackCat’s ransomware operators may be associated with DarkSide and BlackMatter. In November 2021, a representative from ransomware gang, LockBit, stated that BlackCat is a rebrand of DarkSide/BlackMatter.
Image 2: A Forum Post from a LockBit Representative
Source: BleepingComputer
BlackCat representatives claim that they are only DarkSide/BlackMatter affiliates who launched their own ransomware operation, but researchers believe otherwise. Last year, we published a report on BlackMatter and their re-brand as DarkSide. BlackMatter was responsible for ransomware attacks on at least four healthcare or healthcare-related organizations (a pharmaceutical consulting company, a dermatology clinic, and a medical testing and diagnostics company). DarkSide was the threat actor behind the attack on Colonial Pipeline.
During the same interview with The Record, an ALPHV representative admitted that REvil, BlackMatter, Maze, and LockBit are all connected in some way because they are adverts (advertisers or affiliates). ALPHV went on to say that adverts write software and pick a brand name. Partnerships are nothing without adverts and there is no rebranding because they have no direct relation to the partnership programs. Admittedly, APLHV borrowed the named groups advantages and eliminated their disadvantages.
Image 4: Twitter Thread from Brett Callow
Brett Callow from Emsisoft stated ALPHV is more than likely BlackMatter and he explained his reasoning in a series of four tweets via Twitter.
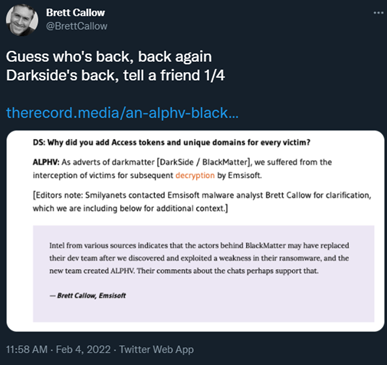
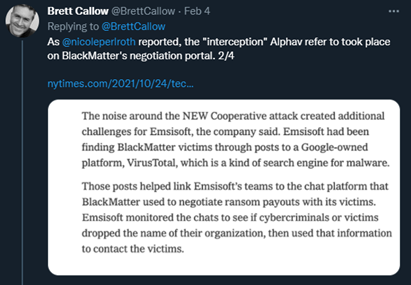
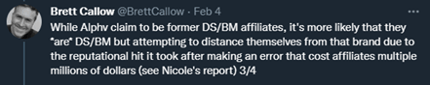
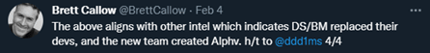
Source: Twitter
colonial pipeline & european oil port
In May 2021, BlackCat ransomware was used in the attack on Colonial Pipeline. This attack sparked a political firestorm and although the Russian threat actor DarkSide was attributed to the attack, the threat actor blamed an affiliate for having gone rogue. DarkSide ended up walking away with 63.7 bitcoins ($4.4 million) in exchange for a decryptor. The FBI eventually recovered $2.3 million of the ransom payment and DarkSide went dark shortly after U.S. President Joe Biden told Russian President Vladimir Putin to crackdown on Russian ransomware groups or risk becoming a target for the U.S. By July 2021, Darkside rebranded as BlackMatter
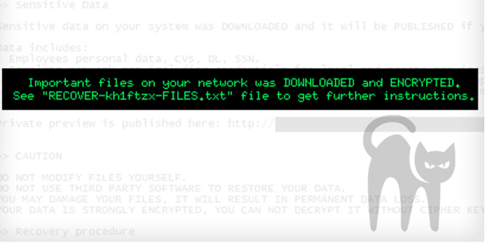
Image 5: BlackCat Ransomware Encryption Alert
In BlackMatter’s case, there were encryption errors in the gang’s malware that allowed security professionals to quietly reach out to victims and restore data before a ransom was paid – which was a massive blow to BlackMatter’s profits.
Source: SentinelLabs
After the errors were discovered, DarkSide/BlackMatter fired its development team, hired a new team, then went dark in November 2021 before launching again during the same month as ALPHV (BlackCat).
Using BlackCat ransomware, attackers were able to infect computers at Mabanaft GmbH and Oiltanking GmbH Group in February 2022. The attack took down part of Germany’s fuel-distribution system and stopped payments at some filling stations. Another energy-storage company that has had IT issues recently is the Evos Group, which is located in Belgium and the Netherlands.
How Avertium is Protecting Our CUSTOMERS
It’s important for you to remember that paying the ransom doesn’t automatically erase the security problems that allowed your organization to be attacked in the first place. Discovering what went wrong and why are the first steps to fixing your security problems. Avertium offers the following service to help protect our organization from being exposed to ransomware like BlackCat:
- We offer EDR endpoint protection through SentinelOne, Sophos, and Microsoft Defender.
- SentinelOne prevents threats and extends protection from the endpoint to beyond. Find threats and eliminate blind spots with autonomous, real time, index-free threat ingestion and analysis that supports structured, unstructured, and semi-structured data.
- SentinelOne prevents threats and extends protection from the endpoint to beyond. Find threats and eliminate blind spots with autonomous, real time, index-free threat ingestion and analysis that supports structured, unstructured, and semi-structured data.
- Avertium’s XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions. All organizations have varying XDR services, but Avertium’s XDR is designed to utilize enterprise-grade workflows and remediation, as well as leverage advanced AI and analytics.
- MDR provides an in-depth investigation into potential threats on an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
- Include a Zero Trust Architecture, like AppGate, to stop malware lateral movement.
Avertium’s Recommendations
- Backups – please ensure your organization has secure offsite backups.
- Run up-to-date security solutions to ensure your organization’s computers are protected with the latest security patches against ransomware like BlackCat
- Encrypt sensitive data wherever possible
- Educate your staff about the various ways cybercriminals launch attacks and steal data.
- Practice good cyber hygiene
- Ensure antivirus and antimalware software signatures are up to date.
- Implement application allow listing.
- Ensure user privileged accounts are limited.
- Employ MFA.
- Implement cybersecurity best practices.
MITRE TTPS
- [T1592] Gather Victim Host Information
- [T1586] Compromise Accounts
- [T1490] Inhibit System Recovery
- [T1590] Gather Victim Network Information
- [T1486] Data Encrypted for Impact
- [T1040] Network Sniffing
- [T1133] External Remote Services
Indicators of Compromise (IoCs)
- id7seexjn4bojn5rvo4lwcjgufjz7gkisaidckaux3uvjc7l7xrsiqad[.onion]
- sty5r4hhb5oihbq2mwevrofdiqbgesi66rvxr5sr573xgvtuvr4cs5yd[.onion]
- htnpafzbvddr2llstwbjouupddflqm7y7cr7tcchbeo6rmxpqoxcbqqd[.onion]
- aoczppoxmfqqthtwlwi4fmzlrv6aor3isn6ffaiic55wrfumxslx3vyd[.onion]
- alphvmmm27o3abo3r2mlmjrpdmzle3rykajqc5xsj7j7ejksbpsa36ad[.onion]
- 2cuqgeerjdba2rhdiviezodpu3lc4qz2sjf4qin6f7std2evleqlzjid[.onion]
- zujgzbu5y64xbmvc42addp4lxkoosb4tslf5mehnh7pvqjpwxn5gokyd[.onion]
- mu75ltv3lxd24dbyu6gtvmnwybecigs5auki7fces437xvvflzva2nqd[.onion]
- f815f5d6c85bcbc1ec071dd39532a20f5ce910989552d980d1d4346f57b75f89
- c3e5d4e62ae4eca2bfca22f8f3c8cbec12757f78107e91e85404611548e06e40
- 74464797c5d2df81db2e06f86497b2127fda6766956f1b67b0dcea9570d8b683
- 4e18f9293a6a72d5d42dad179b532407f45663098f959ea552ae43dbb9725cbf
- 1af1ca666e48afc933e2eda0ae1d6e88ebd23d27c54fd1d882161fd8c70b678e
- 15b57c1b68cd6ce3c161042e0f3be9f32d78151fe95461eedc59a79fc222c7ed
- 13828b390d5f58b002e808c2c4f02fdd920e236cc8015480fa33b6c1a9300e31
- c8b3b67ea4d7625f8b37ba59eed5c9406b3ef04b7a19b97e5dd5dab1bd59f283
- bd337d4e83ab1c2cacb43e4569f977d188f1bb7c7a077026304bf186d49d4117
- 7b2449bb8be1b37a9d580c2592a67a759a3116fe640041d0f36dc93ca3db4487
- 38834b796ed025563774167716a477e9217d45e47def20facb027325f2a790d1
- 2cf54942e8cf0ef6296deaa7975618dadff0c32535295d3f0d5f577552229ffc
- 28d7e6fe31dc00f82cb032ba29aad6429837ba5efb83c2ce4d31d565896e1169
- 0c6f444c6940a3688ffc6f8b9d5774c032e3551ebbccb64e4280ae7fc1fac479
- f8c08d00ff6e8c6adb1a93cd133b19302d0b651afd73ccb54e3b6ac6c60d99c6
- 731adcf2d7fb61a8335e23dbee2436249e5d5753977ec465754c6b699e9bf161
- 59868f4b346bd401e067380cac69080709c86e06fae219bfb5bc17605a71ab3f
- 3d7cf20ca6476e14e0a026f9bdd8ff1f26995cdc5854c3adb41a6135ef11ba83
- 7e363b5f1ba373782261713fa99e8bbc35ddda97e48799c4eb28f17989da8d8e
- cefea76dfdbb48cfe1a3db2c8df34e898e29bec9b2c13e79ef40655c637833ae
Supporting Documentation
2021 Trends Show Increased Globalized Threat of Ransomware | CISA
Who Wrote the ALPHV/BlackCat Ransomware Strain? – Krebs on Security
BlackCat ransomware - what you need to know | The State of Security (tripwire.com)
Cyberattack Cripples European Oil Port Terminals (bankinfosecurity.com)
BlackCat (ALPHV) ransomware linked to BlackMatter, DarkSide gangs (bleepingcomputer.com)
LockBit, BlackCat, Swissport, Oh My! Ransomware Activity Stays Strong | Threatpost
Ransomware: Alphv/BlackCat Is DarkSide/BlackMatter Reboot (bankinfosecurity.com)
Black Cat Ransomware Tied to German Fuel Attacks and Colonial Pipeline Hackers - Bloomberg
Threat Assessment: BlackCat Ransomware (unit42.paloaltonetworks.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
 DOWNLOAD OUR LATEST EBOOK >>>
DOWNLOAD OUR LATEST EBOOK >>>
In this eBook, you will learn:
- The newest and growing trends in cybersecurity tools, processes,
and data storage. - Major cyber attacks that occurred in 2021, their impact, and what
we can learn. - Our expectations for what cybersecurity will look like in 2022,
based on the data collections and observations from Avertium
security experts, as well as commentary from Avertium's partners. - The tools and services your organization needs to show no
weakness in 2022.