An In-Depth Look at the Emotet Botnet
Executive Summary
After 10 months of darkness, Emotet came back with a vengeance in November 2021 and installed malware on Windows systems. TrickBot was used to install Emotet, and the botnet was spammed in multiple email campaigns to deploy the malware. The campaigns relied on reply-chain emails to persuade victims into opening malicious attachments disguised as Word/Excel documents or password-protected ZIP files.
After the attacks, Emotet went dark for several months – a pattern they maintain. During the first quarter of 2022, Emotet re-emerged using new Emotet variants that employed old and new techniques to trick victims into clicking on malicious links and enabling macros and other malicious content.
TA542 (also known as Mummy Spider) is the threat group behind the prolific botnet. There is substantial evidence that the group gradually changes their behavior, adjusting techniques to avoid detection and improve the likelihood of victims opening their spam emails. Let’s take a look at Emotet’s evolution, their new tactics and techniques, and why botnets are a threat to organizations everywhere.
emotet's evolution
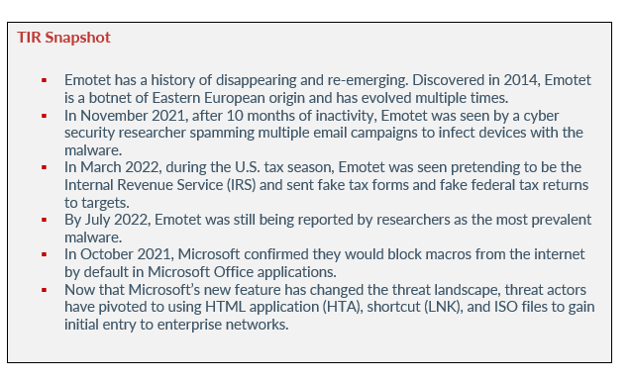
As previously stated, Emotet has a history of disappearing and re-emerging. Discovered in 2014, Emotet is a botnet of Eastern European origin and has evolved multiple times. According to Trend Micro, the botnet began as a banking Trojan before evolving into a malware downloader. From there, Emotet added more features such as a spamming module and other mechanisms to increase efficiency and evade detection.
By 2019, Emotet was being used in a spam campaign that involved over 14,000 spam emails. The emails were intended to deliver malware called Nymaim. This malware was a downloader for Nozelesn ransomware, a secondary payload. The campaign focused on sending out a large number of emails.
The threat actors also hijacked older email threads and revived them with new replies. The spam then appears to be part of an existing email exchange instead of being sent as new messages. TA542 used emails from an attack in November 2018. Emotet is known for selling access to compromised machines as a part of its malware-as-a-service (MaaS) operation. Both Conti and Ryuk are among threat actors who have used Emotet in their attacks.
In January 2021, law enforcement from Germany, Lithuania, France, Canada, the U.S, the Netherlands, and Ukraine worked together to take control of Emotet’s infrastructure from the inside. As a result, law enforcement was able to disrupt the malware’s operation. According to Europol, Emotet’s infrastructure involved hundreds of servers across the world, with each one having different functionalities in order to manage the computers of infected victims – to spread to new victims, to serve other criminal groups, and to make the network more resilient against takedown attempts.
Emotet dismantled after the takedown but resurfaced in November 2021. Our technology partner, AdvIntel, stated that their return was influenced by Conti’s operators. The operators behind Conti wanted to continue their relationship with TA542 due to the botnet malware playing an important role in the ransomware’s initial access phase.
Previous Tactics & Techniques
In November 2021, after 10 months of inactivity, Emotet was seen by a cyber security researcher spamming multiple email campaigns to infect devices with the malware. As previously stated, the campaigns used reply-chain emails to trick victims into opening malicious attachments disguised as Word/Excel documents or password-protected ZIP files. Reply-chain email attacks are another form of social engineering where the attacker sends a malicious email from a genuine, but stolen email account. Some of the reply-chain emails discovered included a missing wallet, a canceled meeting, and even political donations.
During this time, there were two malicious documents being distributed. The first document was an Excel attachment asking the victim to click on “Enable Content” to view the contents. The second document was a Word attachment that said the document was in “Protected” mode and users needed to enable “content and editing” to view it. However, after the victim opened the attachments, they enabled malicious macros that launched a PowerShell command that then downloaded the Emotet loader DLL from a compromised WordPress site.
After being downloaded, Emotet configured a startup value under the following: HKCU\Software\Microsoft\Windows\CurrentVersion\Run.
This startup value allowed the malware to launch upon Windows startup. Emotet then ran silently in the background, waiting for commands to execute to from its Command and Control (C2). The commands were used to steal email account information, to spread the malware to other computers, or to install additional payloads like TrickBot.
new tactics & techniques
By the first quarter of 2022, Trend Micro and Proofpoint observed a significant number of infections across different industries within various regions. Those regions impacted by Emotet included Japan, Europe, and Africa. It is suspected that TA542 targeted profitable industries such as education and manufacturing to attract other threat actors as potential customers for their MaaS operation.
In March 2022, during the U.S. tax season, Emotet was seen pretending to be the Internal Revenue Service (IRS) and sent fake tax forms and fake federal tax returns to targets. The tax documents were distributed as Word and Excel documents containing malicious macros. Once opened, the victim was tricked into enabling macros that downloaded the Emotet malware onto their computer.
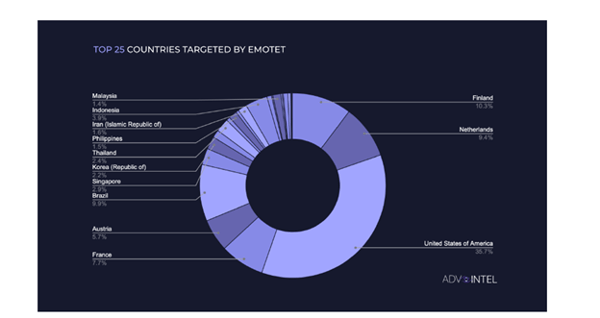
Image 1: Top 25 Countries Targeted by Emotet
Source: AdvIntel
After Emotet was installed, the malware stole the victims’ emails to use for future reply-chain attacks by sending further spam emails. This had the potential to ultimately install other malware that could lead to a Conti ransomware attack on the victim’s compromised network.
In May 2022, Trend Micro observed a surge in Emotet spam campaigns using new and old techniques to trick victims into accessing malicious links and enabling macros. The researchers at Trend Micro found that new Emotet samples still contained the same initial downloader as the one found in previous campaigns. However, they also found Excel 4.0 macros in a more recent sample.
By July 2022, Emotet was still being reported by researchers as the most prevalent malware. By this time, researchers noticed Emotet implemented new features and improvements, such as a credit card stealer module and adjustments to its spreading systems.
According to Check Point, TA542 was using Snake Keylogger (credential stealer) in June 2022, but the group decided to decrease its use. The group has replaced Snake Keylogger with XMRig, an open-source CPU software used for cryptocurrency mining. In June 2022, Emotet was seen using the mobile malware Mailbot, which they are currently still using.
Avertium’s Cyber Threat Intelligence team analyzed new samples of Emotet and found that the delivery technique used for these files were via zip file, saved to OneDrive, and shared via a link in an email. This method helps to avoid malware scanning tools by concealing the final payload. In the sample we examined, the zip file contained 4 identical .xll files with slightly different names.
Image 2: .xll Files in the Zip Folder
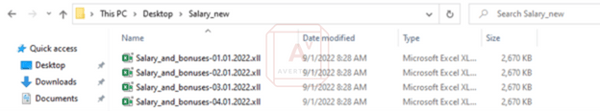
Source: Avertium's Cyber Threat Intelligence Team
XLL files are special Dynamic Link Libraries (DLL) that provide additional functionality to extend the capabilities of Excel. This can be checked using the Linux file command or viewing the raw headers of the files. When an xll file is double clicked, it will be loaded and executed by excel. This is a useful way for threat actors to avoid dependance on macros.
Image 3: File and sha1sum Comparison of the .xll Files
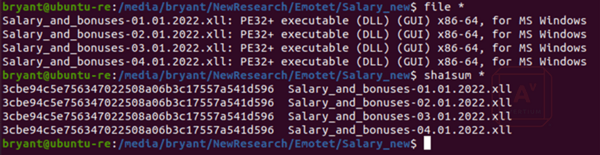
Source: Avertium's Cyber Threat Intelligence Team
So far, Emotet has been observed distributing a low volume of malicious emails and testing their new techniques. We now know this is likely due to Microsoft disabling macros. The low volume of emails could be an indicator for a potentially massive phishing campaign in the near future.
recent attacks
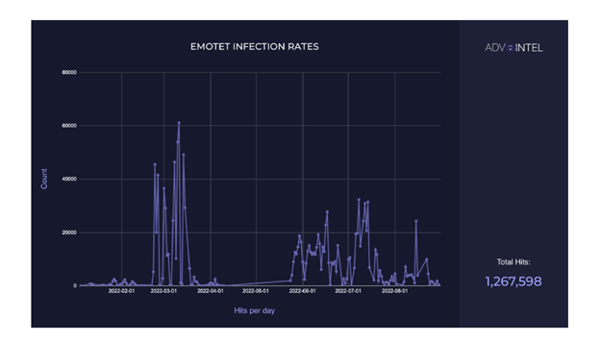
AdvIntel observed Emotet attacking several organizations throughout 2022. According to their research, they observed a total of 1,267,598 Emotet infections worldwide. Activity from Emotet peaked between February and March, kicking off during the start of the Russian-Ukraine conflict.
Also, in June and July of 2022, the botnet’s usage was attributed alongside post-Conti groups such as Quantum and BlackCat. AdvIntel also stated that from November 2021 to Conti’s dissolution in June 2022, Emotet was an exclusive Conti ransomware tool. The ransomware group Roy/Zeon has also been seen utilizing Emotet as a dropper for ransomware.
Image 4: Emotet Infection Rate
Source: AdvIntel
On August 8, 2022, AdvIntel confirmed that two education entities in Kansas City were infected with the botnet. Additionally, on August 12, 2022, it was confirmed that the botnet infected seven organizations within the financial, legal, and manufacturing sectors. The largest organization in AdvIntel’s breach pulse was a finance firm in India with an annual revenue of $9 million.
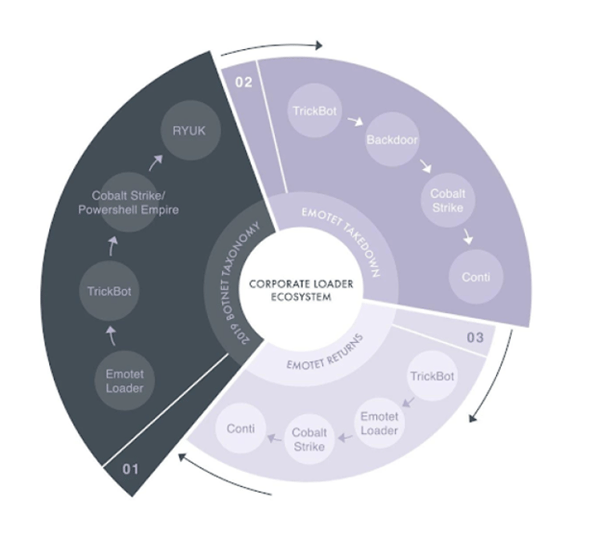
Image 5: Emotet Taxonomy Attack Flow
Source: AdvIntel
microsoft blocking macros
In October 2021, Microsoft confirmed they would block macros from the internet by default in Microsoft Office applications. According to Microsoft, VBA macros are a common way for malicious actors to gain access and deploy malware or ransomware. To improve security, Microsoft changed the default behavior of Office applications to block macros in files that come from the internet.
As a result of Microsoft’s security improvement, when users open an Office file that contains macros via email, a security risk message is displayed notifying the user that Microsoft has blocked macros from running. As a result of this change, threat actors like those behind Emotet are starting to move away from exploiting Microsoft Office macros.
The security provider “Expel” released new research surrounding this topic in August 2022. They found that the initial attack vector in 55% of pre-ransomware incidences during the first quarter of the year were from macro-enabled Word documents or Excel 4.0 macro documents. That incidence number fell to 9% during the second quarter of the year after Microsoft started blocking macros – a 46% decrease.
Now that Microsoft’s new feature has changed the threat landscape, threat actors have pivoted to using HTML application (HTA), shortcut (LNK), and ISO files to gain initial entry to enterprise networks. Moving forward, organizations will need to keep an eye out for those kind of files attached to emails.
According to Sentinel Labs, LNK files are becoming extremely popular among threat actors for malware deployment and persistence. The researchers observed intense advertising of new versions of the mLNK and QuantumBuilder tools for building malicious LNK files in the dark web. The QuantumBuilder and mLNK tools allow adversaries to build malicious LNK files conveniently.
Emotet has been constantly evolving since its creation in 2014. While the disabling of macros by Microsoft will help to slow the spread, we can already see the developers testing new techniques to increase infection rates. In order to combat threats such as these organizations need to take a layered approach to security, ensuring that if one defense fails there is another to back it up.
Emotet is particularly challenging as it will change payloads for different campaigns, moving from credential harvesting, to cryptomining to banking trojan depending on which is providing the greatest return. Avertium is continuing to monitor trends in the malware space and tracking changing tactics. At this time, threat actors using HTA, LNK, and ISO files are still effective in tricking users to open their attacks. Some actions that can be taken to help prevent these file types are:
- Unregister ISO file extensions in Windows Explorer. Windows won’t recognize the file if it is unregistered, thus preventing users from accidentally executing malware if they click on a malicious file.
- Because phishing is one of the most common ways employees accidentally download malicious files, deploy a secure email gateway (SEG) to monitor emails for signs of an attack. SEGs can filter malicious emails by providing a solution that is deployed at the mail server.
How Avertium is Protecting Our CUSTOMERS
It’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. Avertium offers the following services to keep your organization safe:
- Increasing visibility within your environment is crucial when trying to prevent or mitigate a potential attack from botnets like Emotet. Avertium offers EDR protection through SentinelOne, Sophos, and Microsoft Defender.
- SentinelOne prevents threats and extends protection from the endpoint to beyond. Find threats and eliminate blind spots with autonomous, real time, index-free threat ingestion and analysis that supports structured, unstructured, and semi-structured data.
- Our Partners, Microsoft and Sophos, also offer endpoint protection. Sophos can help secure your environment by protecting and prioritizing potential threats. Microsoft Defender provides real-time threat detection, as well as firewall and network protection. The program comes standard with Windows.
- Avertium also offers user awareness training and phishing simulation campaigns using KnowBe4.
- Penetration testing will help your employees understand malware and will help prevent attacks. It’s easier for an organization to avoid malware if employees understand the “what” and “why” behind it.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
Avertium’s Recommendations
- Block communication to C2s to prevent Emotet from dropping payloads on compromised devices.
- Apply security patches to your devices when they are released.
- Provide awareness training for employees regarding the dangers of phishing emails.
- Ensure that your employees are aware of what botnets could look like and how to avoid any links that may be hazardous.
- Work with the right Managed Security Service Provider (MSSP) that is able to consistently monitor and combat vulnerabilities in your attack surface.
- Regularly check schedule backup routines – this includes integrity checks and/or offsite storage.
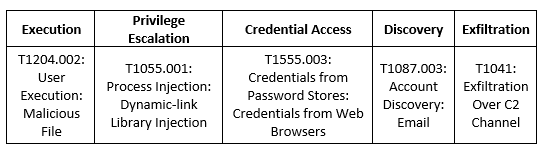
MITRE Map
Emotet
Indicators of Compromise (IoCs)
New Emotet IP Addresses
- 234.2[.232]
- 234.21[.73]
- 9.116[.246]
- 54.89[.58]
- 118.115[.99]
- 176.232[.124]
- 55.222[.11]
- 30.40[.196]
- 91.7[.5]
- 91.76[.89]
- 254.140[.238]
- 227.42[.236]
- 15.201[.15]
- 143.187[.147]
- 172.212[.216]
- 165.152[.127]
- 207.28[.33]
- 23.45[.86]
- 50.0[.91]
- 43.46[.182]
- 70.28[.102]
- 75.201[.2]
- 132.242[.26]
- 182.225[.142]
- 232.117[.186]
- 193.124[.41]
- 232.188[.93]
- 100.24.[231]
- 122.66[.193]
- 197.109[.175]
- 59.226[.45]
- 56.131[.28]
- 106.112[.196]
- 126.146[.25]
- 69.222[.101]
- 65.88[.10]
- 16.142[.56]
- 68.99[.3]
- 99.115[.35]
- 172.253[.162]
- 104.251[.154]
- 212.193[.249]
- 56.128[.118]
- 104.106[.96]
- 111.227[.137]
- 4.135[.165]
- 8.212[.130]
- 157.82[.211]
- 84.80[.182]
- 44.20[.25]
- 126.111[.200]
- 218.30[.83]
- 242.150[.244]
- 94.166[.162]
- 114.109[.124]
Hashes
- 0102166f5148a12ab7f503b52337a68f
- 0168bbe72780def8098bbec4f72487b5
- 196bb3d50113e0f8af16634ec06266e2
- 27e8527bd11df4e8b28012a9559c7cf6
- 2a0d5f0a16800cab48b9e934762f4bff
- 2e10b11effcf71f450ea0ba74cb072de
- 3f94ae29a90ee05fe872cdadc3804a13
- 438ae93e8e79f5aa1fde4df8da3586b2
- 4f61fa04b44a86f852bd5d41d518660b
- 585667db6b255e5ea87cedc6af796949
- 8722dfe74062e4fe82902e7e90c469ac
- 8b7914d6e2e7fd2d08e54a336d943b95
- e958840b7dba65e16b50015e26ba4e49
- fce0034a078407063df4343964c2f461
- ff0ee3e531b7e0ed820e15f0fc675e4b
- 37fc44529452f234e714bcc1820ffaf66bc30cb4
- 41575120f40f6c4936c0ba262d558bf08fa25eff
- 46a0515e48938151efcd4dfc4abf15d610becf7b
- 4be300a01c6d11120fcc277e0b62523eedcc2538
- 6fd4a069b72236b1c842ac4b8ebd509d1f85fa8c
- 768bd066476b81379758c1e7f5d733b1c08695bf
- 860879aab43dc0af0b4531df0db712c838d9a162
- c0e0b7f101e681ca90a86a37b3a8db9620aca05c
- ccaef99976bbd4f3c09978a7a9ea6e7ee4ec2b42
- ceb00bbf764423285eb4a5f6c3aeb8b0c5eead1a
- e29a35b7620660549b3bc2b19a3adf7213d0a6fa
- f48e592042bd73d5e38dc3bcb430ec3cce2702c3
- f50b6c9e7a4db58ad93e2a83baf2197a5519452b
- f5de283a8afd231ce769721ff1c42c27eb99610d
- fd56df930972e755effa3030361c6975897b6887
- 021f94e166b2081342c1f184ac3697b067626d07f44899e0e8cf0a44644401ad
- 03dd0a294f5686a3b6396e367f3489c0a6fafcabfdb4996840d9a5fcc7157421
- 412a79efbeadd5928465d1ff9b0da28c80605393ce7348abe19460910186c4aa
- 4c7d042c9f08708b99f630b21d2b34728dabde2331110b766465ea6a513130e4
- 57e14a6beb49329165057d51a2d5120774c8094639c493c97c1320fb9a9558f2
- 5d3c1f725cd6074778f1ba9cf0fc576c2d41594a4f4b786a528818ffbf1876d1
- 6b2e52cc4a323fa3363965044db4a333eb5d7e84bcac89953119aefd16b9f23c
- 7b166ddb1c6ead1135b763671172463126e77c93c89a8bea3f1ddfc8df90b61e
- 888a9ccbe278a2d7898189d14e6fbcadd9bf184f1850ccbdf5b7d0345b097367
- 9a0e5c39d692256e45a343911f269a46acd4f03d2ec937142ecac03c8b7a81a0
- 9bdfff47da46f2dde07603682efcad8bfb1beb58ec1d8dbafc8f8ddaa86114d0
- a546388efe68b719d3c94e38af5650be0f12dcb5275f0a3006688b0d4b39b704
- b0c6511eead772dc0ca8a17d5b41235aaaf002dd0307411154332aa9feb7bfbd
- b916719c597f7b16d97141776036469016fc1927b3b78b93f2f179adcfee9474
- f93357e0aefaa4a721c99f1dfa33b768aa7f354ab7bee99258a08fb238f9bd71
Domains
- skbroadband[.com]
- skbroadband[.com]
- hetzner[.de]
- dreamscapenetworks[.com]
- co[.id]
- cabletelco[.com]
- dcc[.bg]
- godaddy[.com]
- ovh[.com]
- ovh[.com]
- com
- skbroadband[.com]
- bpstudios[.com]
- Contabo[.com]
- Szerverplex[.hu]
- Ionos[.com]
- Prohost[.kg]
- Ovh[.com]
- co[.id]
- co[.id]
- maxhost[.vn]
- co[.th]
- ishangroup[.com]
Supporting Documentation
AdvIntel Intelligence Team. (2022, September 6). AdvIntel 2022 Emotet Trends. New York, New York ; AdvIntel.
Bruised but Not Broken: The Resurgence of the Emotet Botnet Malware (trendmicro.com)
Macros from the internet are blocked by default in Office - Deploy Office | Microsoft Docs
World’s most dangerous malware EMOTET disrupted through global action | Europol (europa.eu)
Emotet botnet disrupted after global takedown operation (bleepingcomputer.com)
Flash Notice - Emotet Botnet is Back with New Spam Campaigns (avertium.com)
Emotet malware campaign impersonates the IRS for 2022 tax season (bleepingcomputer.com)
Ransomware gangs move away from exploiting Microsoft Office macros | VentureBeat
Emotet retains hold as most prevalent malware (digit.fyi)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.