You're Secure - But are Your Vendors? Assessing Third Party Risk
This post was guest-written in partnership with Avertium by Bob Maley, CSO at Black Kite.
Foreword: Bob Maley on The Left / Right of Bang Approach
As Chief Security Officer at Black Kite, there’s a military concept that I regularly apply to cybersecurity and 3rd party risk. It’s called Left of Bang. In any military conflict, there is a timeline of events:
- Left of Bang: Left of Bang refers to everything we could have done or used - situational awareness, procedures, intelligence, etc. - that’s designed to either mitigate the damage done or prevent the conflict from happening in the first place.
- Bang: Think of “bang” as the catalyst or trigger that separates the events leading up to the battle and the battle itself.
- Right of Bang: Right of Bang is purely about the reaction to the bang, and all events that follow.
A big part of the “Left of Bang” ideology is centered on situational awareness - understanding the threat environment and the indicators of risk leading up to the big “bang.”
Time and time again, we see that most organizations orient their ransomware strategies around the response - a Right of Bang approach. When security teams are focusing their efforts on what to do AFTER an attack happens - remediation and containment - they’re addressing only a fraction of the equation.
3rd Party Risk in Cybersecurity - And the shortcomings in addressing it
Recently, Black Kite gathered a research team to analyze the top-5 lessons learned from the largest 3rd party breaches and concluded their root causes:
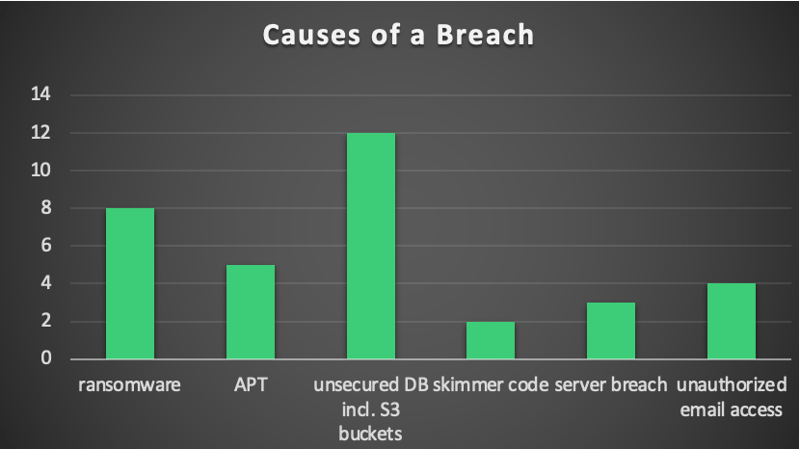
Source: Black Kite
During the research, the team also addressed the top five areas third-party cybercrime could potentially begin:
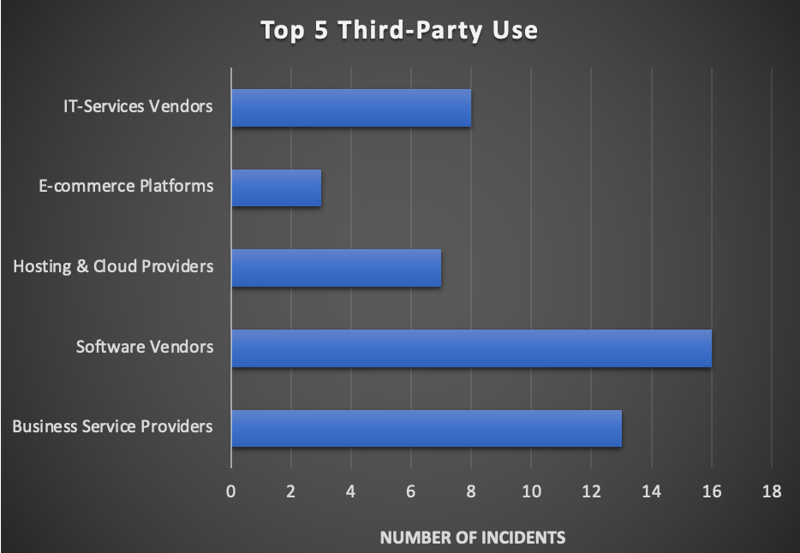
Source: Black Kite
Beyond that, a recent study by Opus and Ponemon, involving more than a thousand CISOs across the US and UK, found that 59% of companies said they have experienced a data breach caused by one of their vendors.
As companies embrace new digital platforms and processes that involve data sharing, it’s good to keep in mind that third parties can introduce new threats to your security systems, accounting for high potential risk. And yet, despite our best efforts, cybersecurity teams fall short of this mandate seemingly all the time. It’s led to this fatalistic (and frankly concerning) mindset amongst cybersecurity professionals:
“There’s nothing we can do about it right now...getting ransomware IS inevitable. So, we might as well spend ALL of your time, money, and effort on preparing our response to the ransomware attack that WILL happen at some point.”
The current intellectual thought-leadership of 3rd party risk management consists of archaic assessments and outdated frameworks. The problem is that the techniques and tactics that bad actors employ today don’t always follow the traditional “rulebook” that these assessments are built upon.
The result? Security teams get bogged down in mandated, time-consuming assessments that largely focus on the current state of the business compliance, rather than addressing the risks that could lead to potential problems in the future.
At Black Kite and Avertium, we believe that there are more vulnerable systems out there than there are hackers. Therefore, when organizations get breached, it’s because they have poor cybersecurity hygiene - not because there are too many attackers out there.
Instead of making the decision of whether to pay the ransom or not, it’s better not to get to that point at all. Organizations need to get to the Left of Bang - at the beginning of the timeline BEFORE an attack happens.
Related Reading: Threat Focus: What Is Ransomware-as-a-Service?
3rd Party Breach Scenario: Quanta Computers + Apple
A recent 3rd party vendor breach case involved a Taiwan computer company called Quanta Computers (QT). QT displayed a high third-party risk index of 0.623 on Black Kite’s Ransomware Susceptibility Index (on a scale of 0 to 1, where anything greater than 0.6 indicates a high degree of risk).
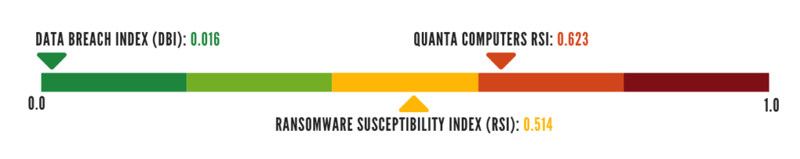
Source: Black Kite's Scale (adjusted graphic)
During this attack, certain Apple hardware blueprints were attained by a ransomware group. Now the hit wasn’t directly within Apple’s headquarters, but they were still ransomed for their intellectual property due to poor third-party risk security framework.
Related Reading: Taiwan Probes Alleged Cyberattack on Top Apple Supplier
Getting to “Left of Bang” in addressing 3rd party risk in cybersecurity
Getting to the Left of Bang requires a degree of situational awareness. It means being proactive. So, how can your organization best manage third-party vendor risk?
- Look at open source intelligence already available to you (and to the hackers).
- Seek for Ransomware as a Service (RaaS) groups and learn their techniques, tactics, procedures (TTPs).
- Assess your company’s cyber hygiene by identifying what sensitive data you’re sharing with your third parties.
- Assess your vendors’ cyber hygiene as well. You can start by asking the following questions:
-
How are you protecting my information? Understanding your third parties’ method to protect your information - whether it’s an encryption process or two-factor authentication - is important to have a holistic view of where your data is being stored and notice if there are any vulnerabilities with their procedures.
-
What are you doing with my information? Learning how your information is being used will help you determine if it’s necessary to share with your vendors. On top of that, knowing what it’s being used for will lead to other questions such as, are your vendors’ servers and firewalls updated and protected?
- Do you have a Business Continuity Plan (BCP) and Disaster Recovery Plan (DRP)? Third parties may have a BCP or DRP, but it’s important that they also have a well-documented backup plan for your organization’s data as well.
-
- Lastly, continuously monitor your third-party vendors to stay up-to-date and aware of everything that happens within your walls. Fortunately, this can be done with the Ransomware Susceptibility Index™ (RSI™).
Related Reading: Left of Bang: How the Marine Corps Combat Hunter Program Can Save Your Life
Conclusion
“Billions and billions of stars,” as Carl Sagan has once said. And just like stars, Black Kite has completed a ton of research, capturing “billions” of data points. By leveraging Black Kite’s platform, Ransomware Susceptibility Index™, it will enable your organization to deploy a *three-pronged approach to proactive ransomware protections.
And the reality is, when it comes to cybersecurity, the best offense is a good defense… or, as Avertium says, “Showing No Weakness.” With a risk-based approach, you dedicate your security team to strengthening your wall, making it harder for bad actors to infiltrate. So at the end of the day, that’s what Left of Bang is really all about.
About Black Kite’s Ransomware Susceptibility Index

*Black Kite’s three-pronged approach to proactive ransomware protection
The patent-pending RSI™ uses mathematical processes and machine learning to calculate your 3rd party risk. The platform understands that there are pieces of information from all the data collected to help us be predictive of who might be susceptible to ransomware.
Inspecting, transforming, and modeling data collected from various open-source intelligence sources (OSINT), the RSI™ leverages mathematical processes and machine learning across 219 data points to pinpoint vendor risk against 26 control points.
Where to Find More Information on 3rd Party Risk - Regulations and Compliance
For regulations regarding third parties:
For detailed cybersecurity processes:
- NIST Cybersecurity Framework
- MITRE ATT&CK
- Vulnerability Assessment and Penetration Testing
- Threat Detection and Response
- CIS Controls