An Update on HIVE Ransomware
Executive Summary
During 2021, HIVE ransomware was involved in several attacks against the healthcare sector. HIVE is offered as ransomware-as-a-service (RaaS), meaning that the ransomware is used by affiliates in attacks. Avertium published a Threat Intelligence Report naming the top five cyber threats in the healthcare sector and HIVE was in the top ten of global ransomware for the third quarter of that year.
HIVE has also been used in attacks against several critical infrastructure organizations within the government, IT, communications, and manufacturing industries. Despite law enforcement’s recent crackdown on cyber criminals, the operators behind HIVE ransomware have not slowed down.
In November 2022, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of Health and Human Services (HHS) released an advisory stating that HIVE ransomware attacks have continued, and operators have attacked over 1300 businesses and have extorted about $100 million since June 2021. Let’s revisit HIVE, the attackers’ tactics and techniques, and what organizations can do to remain safe from the threat actors that use it.

previous attacks
HIVE was initially observed in June 2021 and operates as an affiliate-based ransomware gang. During 2021, HIVE was used to attack Europe’s largest consumer electronics retailer, MediaMarkt. As a result of the attack, the company’s servers were encrypted, and their IT systems had to be shutdown.
Although MediaMarkt was able to function online, their brick-and-mortar stores were not able to accept credit cards or print receipts. The ransom demand was $240 million for decryption but was eventually reduced to $50 million in bitcoin. It is common for ransomware gangs to demand an absurd amount of money initially, only to decrease that demand to a lower yet still profitable amount.
During the same year, researchers found that HIVE was used to attack critical infrastructure, specifically healthcare. Ransomware operators attacked Memorial Health System, forcing the staff to work from paper charts. HIVE operators were also responsible for an attack on the third largest medical facility in Saxony-Anhalt. At the time, an insider confirmed that HIVE affiliates estimated the organization’s revenue to be $272 million. The attackers knew that a healthcare facility would likely pay their demanded ransom because any information stolen is highly sensitive and confidential. Information within the healthcare sector is the most valuable information for cyber criminals and a single piece of data can go for hundreds of dollars on the black market.
current activity
NYRA
In September 2022, HIVE ransomware operators claimed the attack on the New York Racing Association (NYRA). The attack impacted IT operations and compromised member data. NYRA operates three of the largest thoroughbred horse racing tracks in New York – the Saratoga Racecourse, the Aqueduct Racetrack, and the Belmont Park race track.
The security breach included the exfiltration of sensitive member information, such as: Social security numbers, healthcare records, health insurance information, and driver’s license identification numbers. After the attack, the threat actors placed NYRA on HIVE’s extortion site and published a link to download a ZIP archive of the files they stole from NYRA’s systems. Due to the organization’s data being leaked, one can only assume that ransom negotiations didn’t go as planned.
BELL CANADA
Also, during September 2022, HIVE threat actors claimed responsibility for the attack on Bell Canada, a subsidiary of Bell Technical Solutions (BTS). BTS has more than 4,500 employees and specializes in Bell services for residential and small businesses across Ontario and Quebec. After the attack, a new entry for BTS was added to the HIVE extortion site where the attackers claimed to have encrypted BTS’ systems back in August 2022. During that time, the BTS website was inaccessible, and the company published a cyber security alert stating that some employee and operational company information was accessed (addresses, phone numbers, and names of residential and small business customers).
TATA POWER
In October 2022, HIVE operators took responsibility for a cyber attack on Tata Power - a subsidiary of the multinational conglomerate Tata Group. The company is India’s largest integrated power company and is based in Mumbai. After ransom negotiations failed, the attackers posted stolen Tata Power data on their extortion site.
The stolen data contained personal identifiable information, Nation ID card numbers, tax account numbers, and salary information. The threat actors even went as far as stealing and leaking engineering drawings, financial and banking records, and sensitive client information.
HEALTHCARE ORGANIZATIONS
In 2021, the FBI warned healthcare organizations that HIVE threat actors appeared to be targeting healthcare organizations. Unfortunately, that interest has not changed as they recently attacked the Lake Charles Memorial Health System (LCMH) in November 2022.
The ransomware attack included HIVE operators leaking patients’ protected health information and employee personnel files. The threat actors had access to LCMH’s network for 12 days and stole 270 GB of files. The attackers informed the healthcare organization that although they exfiltrated data, they did not encrypt any of the data on the LCMH network. The threat actors demanded $900,000 in ransom and reached out to LCMH to negotiate the payment, but their efforts were unsuccessful.
After no response, the operators reached out for the second time and told the organization that if they paid the ransom, their data would be deleted, and the threat actors would help the organization better understand the system vulnerabilities that led to the breach. A representative from LCMH responded and stated that the organization would review the offer, but the HIVE threat actors never heard back from them. Due to the lack of response, the attackers posted some of LCMH’s exfiltrated data on their extortion site (patient and employee data).
TACTICS & TECHNIQUES
Initially observed in June 2021, HIVE encrypts files and deletes backup and file copying processes to carry out attacks. Over the years, researchers have noticed that most ransomware gangs focus on one platform, such as Windows, to launch their attacks. The operators behind HIVE do the opposite and use several platforms (Windows, Linux, and ESXi hypervisors) depending on the affiliate disseminating the ransomware. According to Adam Meyers, Vice President of CrowdStrike, HIVE’s operators created the ability to run their ransomware against ESXi.
As initial access points, HIVE’s operators have been known to use remote desktop protocol (RDP), virtual private networks (VPNs,) and other remote connection protocols not secured with MFA. HIVE attacks have also included bypassing MFA and exploiting CVE-202-12812 to access FortiOS servers. Affiliates have been seen targeting well-known Microsoft Exchange Server vulnerabilities such as CVE-2021-34523, CVE-2021-31207, and CVE-2021-34473. Operators have also been seen sending phishing emails with malicious attachments.
In 2021, ESET Research Labs identified Linux and FreeBSD variants of HIVE ransomware. The Linux and FreeBSD variants were written in Golang, however at the time, the malware still had some bugs in it and had yet to be exploited. They appeared to be shifting platforms by targeting public facing systems such as Linux – a system that is commonly used for web-servers. HIVE has evolved and as previously stated, the ransomware includes operating systems such as MacOS and VMware ESXi. As more organizations are securing their data centers to the cloud, attackers are taking full advantage.
“Cloud applications that are now running on non-Windows operating systems such as Linux, are also under attack from these cyber criminals. For many years, Linux was thought to be a safe haven from common malware and ransomware attacks due to a smaller percentage of organizations utilizing it. However, that has finally changed with cyber criminals expanding their attacks into new operating systems spaces." – Chuck Everette – Director of Cyber Security Advocacy at Deep Instinct
CISA states that after gaining access, the ransomware makes attempts to evade detection by executing processes to:
- Identify processes related to backups, antivirus/anti-spyware, and file copying and then terminating those processes to facilitate file encryption.
- Stop the volume shadow copy services and remove all existing shadow copies via vssadmin on command line or via PowerShell.
- Delete Windows event logs, specifically the System, Security and Application logs.
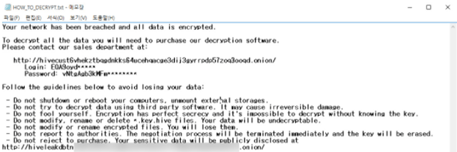
HIVE’s ransomware notes are interesting, allowing victims to contact the operators through a “sales department” link that directs them to a live chat – almost like customer service. HIVE also uses Golang, a modern programming language that threat actors have been utilizing lately. Once in a system, HIVE operators use their tools to move laterally within that system and escalate privileges to steal and encrypt files.
Image 1: HIVE Ransomware Note
Source: AdvIntel
what organizations can do
To help keep you organization safe from ransomware like HIVE, there are ransomware best practices you can implement. A ransomware incident can severely impact an organization’s day to day business, as well as leave them without the data they need to deliver critical services. Due to HIVE’s operators deleting backups, it can be difficult for organizations to restore stolen data. It can also be infeasible, causing economic and reputational devastation for most.
Fortunately, CISA and the FBI have some best practices that you can put into place before you become a victim of HIVE ransomware:
- Be consistent with installing updates for operating systems, software, and firmware as soon as those updates are released. Using a centralized patch management system will automate and expedite the patching process.
- Use phishing resistant MFA on as many devices as possible, especially VPNs, webmail, and accounts that access critical systems.
- Secure and monitor Remote Desktop Protocol (RDP) by:
- Limiting access to resources over internal networks.
- If you must use RDP, restrict the originating sources, and require MFA to help mitigate credential theft and reuse.
- When using RDP, use a VPN, virtual desktop infrastructure, or other means to authenticate and secure the connection.
- Monitor remote access/RDP logs and enforce lockouts after a specified number of attempts. This action will block brute force attacks.
- Properly configure devices and enable security features
- Maintain offline backups of data and test the backups consistently. This action will ensure that your business operations won’t be severely interrupted, and it will ensure that your data is not irretrievable.
- Enable PowerShell Logging: module logging/script block logging and transcription.
- Install and update anti-virus/anti-malware software on all hosts.
- Rclone and other data exfiltration command-line interface activities can be captured through correct logging of process execution with command-line arguments.
Keep in mind that relying on outdated tools and point solutions will compromise your network or system. Better technology exists to detect complex attacks.
How Avertium is Protecting Our CUSTOMERS
Because the cyber landscape is always changing, it is imperative to be aware of new cyber attack strategies and techniques. Avertium is here to keep you informed and to keep your organization safe. We recommend the following services for the best protection against ransomware attacks:
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- It is also recommended by Avertium and the FBI that your business require multi-factor authentication (MFA) to remotely access networks.
- Implementing network segmentation and filtering network traffic to stop phishing emails from reaching victims is also helpful.
- HIVE’s operators use developed social engineering techniques to lure victims (remember, they may be researching companies prior to their attacks). Avertium offers user awareness training with KnowBe4.
- Reach out to your Service Delivery Manager or Account Executive if you need assistance applying any of the above recommendations.
avertium's recommendations
Recommendations from Avertium, the FBI, and CISA if your organization is impacted by HIVE ransomware:
- Isolate the infected system. Remove the infected system from all networks, and disable the computer’s wireless, Bluetooth, and any other potential networking capabilities. Ensure all shared and networked drives are disconnected.
- Turn off other computers and devices. Power-off and segregate (i.e., remove from the network) the infected computer(s). Power-off and segregate any other computers or devices that share a network with the infected computer(s) that have not been fully encrypted by ransomware. If possible, collect and secure all infected and potentially infected computers and devices in a central location, making sure to clearly label any computers that have been encrypted. Powering-off and segregating infected computers and computers that have not been fully encrypted may allow for the recovery of partially encrypted files by specialists.
- Secure your backups. Ensure that your backup data is offline and secure. If possible, scan your backup data with an antivirus program to check that it is free of malware.
- Decryptor released. After you have done the above, you can find the decryptor for HIVE ransomware here.
In addition, the FBI, CISA, and HHS urge all organizations to apply the following recommendations to prepare for, mitigate/prevent, and respond to ransomware incidents:
- Review the security posture of third-party vendors and those interconnected with your organization. Ensure all connections between third-party vendors and outside software or hardware are monitored and reviewed for suspicious activity.
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, and secure location (i.e., hard drive, storage device, the cloud).
- Require all accounts with password logins (e.g., service account, admin accounts, and domain admin accounts) to comply with National Institute of Standards and Technology (NIST) standards for developing and managing password policies.
- Review domain controllers, servers, workstations, and active directories for new and/or unrecognized accounts.
- Segment networks to prevent the spread of ransomware. Network segmentation can help prevent the spread of ransomware by controlling traffic flows between—and access to—various subnetworks and by restricting adversary lateral movement.
- Consider adding an email banner to emails received from outside your organization.
- Disable command-line and scripting activities and permissions. Privilege escalation and lateral movement often depend on software utilities running from the command line. If threat actors are not able to run these tools, they will have difficulty escalating privileges and/or moving laterally.
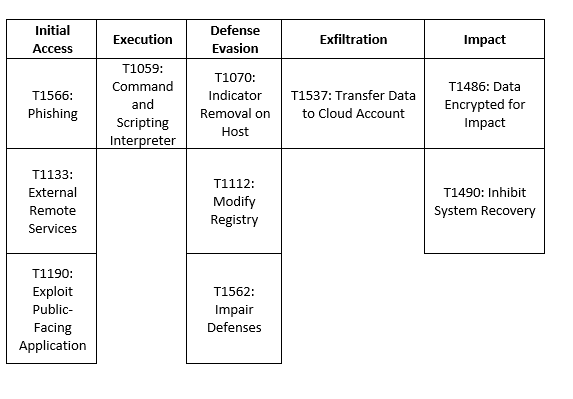
MITRE Map
Indicators of Compromise (IoCs)
IP Addresses
- 32.188[.]57
- 32.188[.]238
- 115.26[.]251
- 8.105[.]67
- 231.81[.]239
- 8.105[.]112
- 111.136[.]37
- 53.123[.]202
- 69.36[.]149
- 166.161[.]123
- 62.118[.]190
- 166.161[.]93
- 247.71[.]106
- 166.162[.]125
- 61.37[.]207
- 166.162[.]96
- 8.105[.]103
- 166.169[.]34
- 199.162[.]220
- 115.25[.]139
- 199.162[.]229
- 115.27[.]148
- 147.109[.]208
- 97.20[.]81
- 61.37[.]207
- 199.162[.]220
- 199.162[.]229;
- 166.161[.]93
- 166.161[.]123;
- 166.162[.]96
- 166.162[.]125
- 166.169[.]34
- 97.20[.]81
- 32.188[.]238
- 32.188[.]57
- 147.109[.]208
- 115.25[.]139
- 115.26[.]251
- 115.27[.]148
- 62.118[.]19
- 231.81[.]239
- 8.105[.]67
- 8.105[.]103
- 8.105[.]112
- 247.71[.]106
- 111.136[.]37
- 53.123[.]202
Logged Processes
- exe cl system
- exe cl security
- exe cl application
- exe delete shadows /all /quiet
- exe SHADOWCOPY /nointeractive
- exe shadowcopy delete
- exe /set {default} bootstatuspolicy ignoreallfailures
- exe /set {default} recoveryenabled no
Files
- txt (typically in directories with encrypted files)
- *.key (typically in the root directory, i.e., C:\ or /root)
- bat
- bat
- r77vh0[.]pw (Server hosted malicious HTA file)
- d6shiiwz[.]pw (Server referenced in malicious regsvr32 execution)
- swhw71un[.]pw (Server hosted malicious HTA file)
- s7610rir[.]pw (Server hosted malicious HTA file)
- dll
- exe
- dll
- exe
- Linux_encrypt
- Esxi_encrypt
Supporting Documentation
Hive ransomware claims attack on New York Racing Association (bleepingcomputer.com)
#StopRansomware: Hive Ransomware | CISA - AlienVault - Open Threat Exchange
Hive claims ransomware attack on Tata Power, begins leaking data (bleepingcomputer.com)
FBI: Hive ransomware extorted $100M from over 1,300 victims (bleepingcomputer.com)
HIVE Ransomware: Everything You Need To Know (Attacks & Analysis) (avertium.com)
Hive Ransomware Gang Hits 1,300 Businesses, Makes $100 Million | SecurityWeek.Com
#StopRansomware: Hive Ransomware | CISA
Lake Charles Memorial Health system victim of cyberattack and data leak by Hive (databreaches.net)
NY: Empress EMS hit by Hive ransomware (databreaches.net)
Hive Ransomware Hackers Begin Leaking Data Stolen from Tata Power Energy Company (thehackernews.com)
Hive ransomware claims cyberattack on Bell Canada subsidiary (bleepingcomputer.com)
HiveV5_file_decryptor/README.md at main · reecdeep/HiveV5_file_decryptor · GitHub
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.