
Case Study:
INTERNOVA TRAVEL GROUP
Discover how Avertium helps unburden Internova Travel Group's security team to have the space to start focusing on more strategic cybersecurity priorities.
In 2022, Avertium published a Threat Intelligence Report on the pro-Russia threat actor Killnet. At the time, the threat actors publicized their allegiance to Russia and made several threats as the cyber war between the two nations continued. Other threat actors also declared their allegiance to either Russia or Ukraine and retaliatory attacks were in full swing. When it seemed as if Russia had the upper hand, deploying worms such as HermeticWiper and WhisperGate, Ukraine turned the tables and began attacking Russia mercilessly.
Just like the kinetic war between Russia and Ukraine, the cyber war has continued. In October 2022, Killnet made threats against not only Ukraine, but against the U.S. for its support of Ukraine. Also, in June 2022, the threat actor claimed responsibility for a DDoS attack on the European country, Lithuania. The attack was in response to the country’s decision to block transit goods sanctioned by the European Union to the Russian exclave of Kaliningrad. As a result, Killnet disrupted 1652 of Lithuania’s web resources.
Following their disbandment announcement in June 2023 and subsequent reunion the following month, Killnet is once again making headlines. Reportedly, the group has teamed up with REvil and Anonymous Sudan. Let’s look at Killnet’s most recent activity and why it’s still important for organizations to keep an eye on this threat actor.
Killnet, known as a pro-Kremlin group, has gained notoriety for directing disinformation campaigns towards European governments and infrastructure. When the Russia-Ukraine conflict began, the group immediately aligned itself with Russia. While over 100 groups have launched cyberattacks against both nations, Killnet has emerged as one of the most outspoken and engaged groups.
In contrast to other highly sophisticated Russian threat groups like Sandworm and FancyBear, Killnet does not possess the same level of sophistication and organizational structure. The group operates in a semi-structured manner, consisting of smaller, relatively unknown groups that share allegiance towards Russia. Killnet is primarily recognized for its dissemination of propaganda and disinformation. Associated with Killnet are pro-Russia groups such as Legion and Xaknet.
Using the Telegram platform as their primary mode of communication, Killnet uses the platform to publicize upcoming attacks and share details about their successful operations. The discussions within their chats frequently include Russian propaganda and express negative sentiments towards nations that do not align with Russia's interests. Also, the channel includes information regarding attacks directed at Anonymous, a pro-Ukraine hacktivist group.
By March 2022, Killnet targeted various entities in different countries through DDoS attacks. They attacked a Ukrainian news service, the Ukrainian branch of Vodafone, and the Ministry of the Interior of Latvia. They later turned their focus to Poland, starting with the Supreme Court's website, then attacking Narodwy Bank Polski (National Bank of Poland). Killnet's assault on the Polish Investment and Trading Agency resulted in a significant 20GB data leak. Their motivation behind these attacks had to do with countries openly expressing their non-support for Russia.
In April 2022, Killnet successfully carried out a DDoS attack on Bradley International Airport's website in the United States. Although the incident solely impacted the website and did not disrupt airport operations, the objective was to hinder military aid to Ukraine. Interestingly, those incidents were followed up with additional attacks, including what Killnet referred to as a "special attack" on a U.S. energy corporation (Devon Energy Corporation), aimed at paying homage to the threat actor REvil.
During January 2023, Killnet took responsibility for targeting and disabling the websites of 14 hospitals in the U.S. Among the affected institutions were Stanford Healthcare, Duke University Hospital, and Cedars-Sinai. In March 2023, reports stated that Killnet directed its focus towards healthcare applications hosted on the Microsoft Azure infrastructure. The Azure Network Security Team reported witnessing 10 to 20 attacks in November 2022, which escalated to a range of 40 to 60 daily attacks in February 2023. While some attacks reached up to 5 million packets per second (PPS), the majority stayed below 2 million PPS. Although not exceedingly high, these attacks had the potential to disrupt a website if it lacked adequate network security measures.
Due to the healthcare attacks, the Health Sector Cybersecurity Coordination Center (H3) raised concerns about the group. They warned that Killnet's DDoS attacks on critical infrastructure sectors, particularly healthcare, posed a threat to both routine and critical daily operations. Towards the end of January, Killnet executed its most significant wave of DDoS attacks to date, targeting over 90 healthcare organizations across various states. Among the targets, 55 percent were healthcare systems with at least one hospital, including those with Level I trauma centers.
The outages resulting from these attacks could have had a substantial impact on patients receiving care within these facilities.
In June 2023, Killnet announced that it had "officially dissolved." This announcement followed the resignation of one of the presumed members associated with Killnet's activities, Killmilk. However, the group's dissolution didn't last long, as they made another announcement in June declaring their intention to carry out cyber attacks against the European financial system. Their collaborators for this endeavor? REvil and Anonymous Sudan.
Image 1: Killnet's Disbandment Announcement Written in Russian
Source: Cyber News
The announcement was later shared on the official Telegram channels of both Anonymous Sudan and Killnet. According to the threat actors, their focus was on the financial system, aligning with the idea of "no money - no weapons - no Kyiv regime." The Telegram post also contained details about potential targets, including U.S. banks and the U.S. Federal Reserve System.
In March 2023, the Trustwave SpiderLabs research team began monitoring Anonymous Sudan. The group conducted a series of Distributed Denial of Service (DDoS) attacks against organizations in Sweden, the Netherlands, Australia, and Germany. Allegedly, these attacks were in response to perceived anti-Muslim actions that occurred within these countries. However, upon further investigation, the research team found that Anonymous Sudan was a subsidiary of Killnet, as they have openly associated themselves with Killnet.
SpiderLabs cannot definitively establish the group's location in Sudan or the nationalities of its members. Nevertheless, evidence strongly suggests that Anonymous Sudan is a Killnet initiative, potentially involving some individuals from Eastern European regions. If you are curious about the reason behind Anonymous, a pro-Ukraine group, aligning with a pro-Russia group, it's important to know that the main “Anonymous Operations” has explicitly disavowed any connection with Anonymous Sudan on their Telegram channel.
There are several indications suggesting that Anonymous Sudan is, in essence, Killnet and not an entirely different group. The main evidence is that both groups heavily rely on DDoS attacks as their preferred method, a tactic predominantly used by Killnet. Additionally, other circumstantial evidence suggesting a Russian connection includes the majority of Anonymous Sudan's Telegram posts being in Russian (with some in English), and their targets being nations that support Ukraine in its conflict against Russia.
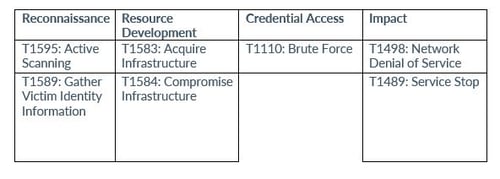
Forescout researchers have noted that Killnet predominantly employs DDoS as its attack method. They do not create or utilize customized tools, and the ones they employ are not highly sophisticated. The group favors brute-forcing credentials on TCP ports 21 (FTP), 80 (HTTP), 443 (HTTPS), and 22 (SSH).
Forescout's observations revealed that when employing brute-force tactics, Killnet focused solely on port 22, suggesting their intent to establish persistence/proxying capabilities. It also appeared that this approach might serve as a means of reconnaissance or credential harvesting for future use. The observed password attempts did not exhibit any specific pattern, except for the passwords being weak.
Following a DDoS attack, Killnet defaces the target's website and posts pro-Russia messages, reflecting their emotional and retaliatory approach. The group seems driven by a sense of revenge and responds with DDoS attacks against those they perceive as having wronged Russia. Killnet has frequently been labeled as a nuisance due to their lack of sophistication and occasional empty threats. Their tactics are confined to DDoS attacks, limiting their range of techniques and strategies.
Killnet’s tactics and techniques have not changed since Avertium reported last on the group. Despite their persistent threats, Killnet is primarily a DDoS-focused group with primitive tactics. While they can bring down a server for a temporary period, their main objective appears to be seeking publicity rather than inflicting significant damage. Indeed, if Killnet manages to cause harm to a target, it often reflects more on the target's cybersecurity readiness than the capabilities of the threat group. Although Killnet's impact may not match their bark, organizations should not dismiss their intent, which is centered on disruption. For critical infrastructure, any form of disruption is a risk that cannot be ignored.
Despite Killnet's claim of working with the re-emerging form of REvil, there is no concrete evidence to support their partnership. As you may remember, REvil faced a significant setback in 2022 following a Russian takedown. The sole indication of a possible re-emergence is a Telegram channel named "REvil," created on June 15, 2023. This channel circulated a shout-out ("Hello Killnet"), which was then extensively reposted in a Killnet-affiliated Telegram channel.
Although Killnet might lack sophistication as a threat group, their intentions remain malicious. If your organization does not possess robust cybersecurity measures, it can pose a significant problem. Cybersecurity involves actively protecting data from internal and external threats. Implementing a cybersecurity governance and risk management program can effectively protect data and fortify systems against threat actors.
For guidance, organizations can refer to the National Institute of Standards and Technology (NIST) for framework profiles, aligning functions, categories, and subcategories with their specific requirements, risk tolerance, and resources. These profiles aid in creating a roadmap to mitigate cybersecurity risks and align with organizational goals, acknowledging the unique needs of each organization. Also, NIST includes five concurrent and constant functions:
In addition to establishing a strong cybersecurity governance and risk management program, Avertium recommends that organizations do the following to help keep their websites and data safe from threat actors like Killnet.
Basic cybersecurity best practices:
Related Resource:
An In-Depth Look at Russian Threat Actor, Killnet (avertium.com)
Killnet hacktivists say they’re disbanding | Cybernews
Killnet threatens imminent SWIFT, world banking attacks - Urgent Comms
Russia Takes Down REvil Ransomware Operation, Arrests Key Members (darkreading.com)
Pro-Islam Hacktivists Likely a Front for Russia's Killnet (darkreading.com)
HC3 Raises Concern Over KillNet DDoS Attacks Targeting Healthcare Sector (healthitsecurity.com)
Killnet: Inside the World’s Most Prominent Pro-Kremlin Hacktivist Collective - Security Boulevard
Pro-Russian hackers take credit for cyberattacks on U.S. airport websites : NPR
Anonymous Sudan: Religious Hacktivists or Russian Front Group | Trustwave
KillNet-DDoS-Blocklist - AlienVault - Open Threat Exchange
Final Act? Killnet Rallies Attackers to DDoS NATO Targets - Security Boulevard
Killnet DDoS attacks inflicting damage on healthcare: 'This is war' | SC Media (scmagazine.com)
Killnet: The Hactivist Group That Started A Global Cyber War - ReliaQuest
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.