BianLian Ransomware Changes Faces
bianlian ransomware Executive Summary
Emerging in August 2022, BianLian became known as a ransomware that encrypted files within minutes. BianLian’s name derives from an ancient dramatic art that originates in China. Artists move about a stage in brightly colored outfits and masks and completely change the face of the masks with a swipe of a fan – within a blink of an eye.
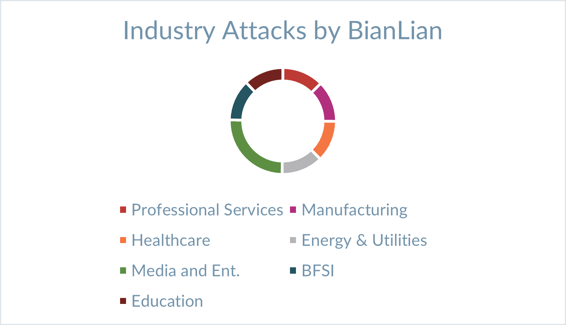
BianLian was written in Golang and was compiled as a 64-bit Windows executable. During 2022 and 2023, BianLian wreaked havoc on various industries, including media and entertainment, manufacturing, and healthcare. As of March 13, 2023, BianLian has listed 118 organizations as victims on their extortion website, with the majority (71%) coming from the United States.
At its peak, BianLian utilized methods to evade analysis by making API calls that could cause crashes in sandboxes or automated analysis systems. It aimed to encrypt all drives detected on infected devices, and once the encryption process was finished, it erased itself. The ransomware was quite successful until a team of researchers and analysts at Avast developed a decryptor for BianLian and made it publicly available. In this report we will examine the impact of the released decryptor and why it is most likely only a temporary setback.

bianlian
BianLian emerged in August 2022, but its most significant impact was observed in 2023. Known for attacking healthcare, the ransomware group listed California-based healthcare facility St. Rose Hospital as a victim in January 2023. The hospital is known as a designated cardiac arrest center in Alameda County and has a revenue of $100 million.
Image 1: Top Industry Attacks by BianLian
BianLian are a financially motivated group that will leak stolen data if they are not paid. After stealing 195 GB of staff and patient data, the ransomware group threatened to leak emails, project details, medical records, and accident reports.
BianLian continued their attacks into early March 2023 when they attacked the City of Waynesboro, Virginia, stealing 350 GB of data from the city’s network. The data included reports, investigations, and internal police station fileserver files. At that time, the group was still operating as a ransomware group, stealing data before encryption.
Unlike most ransomware encryptors which use asymmetric or public key encryption (where different keys are used for encryption and decryption). The BianLian encryptor used the symmetric AES256 algorithm (Golang package AES).This mean that the same key is used for encryption and decryption, and the key was stored in the encryptor. . The Avast team were then able to recover the encryption key and use it to write a new decryptor.
decryptor + new operation model
Not long after the attack on the City of Waynesboro, Virginia, BianLian’s ransomware operation was thwarted when Avast released a decryption tool to decrypt files encrypted by the ransomware. The tool is on Avast’s website and is free to download. The researchers at Redacted have been keeping a close eye on BianLian’s activities, releasing a report on March 16, 2023. The researchers noticed that while the group has not significantly changed their tactics and techniques, they have changed their approach to pressuring victims to pay ransoms.
BianLian uses a custom backdoor written in Golang, to maintain access to victim networks, rather than the general remote access tools used by most ransomware groups. Slight changes have been made to the backdoor over time, such as updating different support libraries and attempting to stay undetected in some cases, yet the core functionality of their backdoor remains unaltered.
The researchers at Redacted also noticed that they have seen many cases where the malware is created shortly after the activation of the command and control (C2), while in other instances, the order is reversed. Consequently, when a C2 is detected, it is likely that BianLian has already infiltrated the victim’s network. They also observed that BianLian tends to bring around 30 new C2s each month. For example, in the first half of March, they started with 11 C2s. Additionally, the average time that a C2 remains active is about two weeks.
After the release of the decryptor, BianLian acknowledged its release and shifted how they monetize their attacks. Instead of encrypting files and threatening to leak data, they are focusing on convincing victims to pay a ransom in exchange for the group’s silence. This means that the group is now operating as an extortion group and not as a ransomware group. BianLian promises that after payment, they will not make the data public or reveal the breach to anyone. They depend on their reputation, so they extend this assurance to victims.
“Our business depends on the reputation even more than many others. If we will take money and spread your information- we will have issues with payments in future. So, we will stick to our promises and reputation. That works in both ways: if we said that we will email all your staff and publicly spread all your data- we will.” – BianLian (posted on their Tor site)
BianLian conducts research on victims to customize threats, citing legal/regulatory issues victims may face if a breach were made public. They even reference applicable law subsections. This extra effort indicates the criminal gang is attempting to apply maximum pressure to get their ransoms paid. The group has also been increasingly using a tactic of posting masked details about their victims on their leak site. This tactic involves posting varying degrees of detail about an organization, usually masking all but a few letters of the company's name, while still including details like the victim's industry, geographical location, and revenue numbers.
Although BianLian was using the masked victim pressure tactics prior to the release of Avast’s decryption tool, the group’s use of the technique increased significantly after the release of the tool. The group has posted details of masked victims more than half of the time since the tool was released.
Based on Avertium’s experience, has been a significant decrease in organizations paying ransom to protect their data from being exposed over the past three years. This is supported by a companies such as Chainalysis, a blockchain analysis firm, who showed that ransomware payments experienced a significant decrease in the past year, dropping to [1]$456.8 million, the lowest figure in three years. This figure is 40% lower than the $765.6 million reported the year before.
At first glance, it seems that the drastic decrease in ransomware profits is due to a decrease in ransomware incidents, however, Kim Grauer of Chainalysis says that this may not be the case.
“The evidence suggests that the decline in attacker revenues is due to victims’ increasing unwillingness to pay their ransom demands rather than a drop in the actual number of attacks. This reluctance can be attributed to a number of factors, ranging from more widespread utilisation of solutions such as backup and recovery that mitigate the impact of attacks, to a fear of running afoul of government regulations that prohibit the payment of ransoms to organisations that are potentially affiliated with sanctioned nations and groups.” - Kim Grauer – Director of Research at Chainalysis
We expect to see BianLian develop a new encryptor, most likely using public-key encryption as their attempts to generate revenue purely by exfiltrating data and threatening it’s release prove to far less effective than encryption.
[1] Ransomware payments fell to US$456.8 million in 2022 | TahawulTech.com
indicators of compromise (iOcs)
Backdoors
- 076e59781d0759de35022291c3d63bbf4227bd79561d80f52c9073a6278c5077
- 0772fb1102685def711ffe647080e1a9b6597fe60e8f1afe7b457ac97c6ac25e
- 16cbfd155fb44c6fd0f9375376f62a90ac09f8b7689c1afb5b9b4d3e76e28bdf
- 183b28fb93db1c907b32aa9fa2f83c7b0ebcc6724de85707a89e5d03c5be5d12
- 1cba58f73221b5bb7930bfeab0106ae5415e70f49a595727022dcf6fda1126e9
- 207078c70be916bb7d2ad4d206d2dca37406f84313f88699fa57fa9745a055bb
- 228ef7e0a080de70652e3e0d1eab44f92f6280494c6ba98455111053701d3759
- 38d6ec5f93f6722c3573989f1463fb1cba1c01c3a1a0579f329e0d625c57070b
- 42b0606aa2c765c0b0789b47ebd3a3f43144dc0c20b2ff6db648ac5feb0a37a3
- 45f76c5c5126501018f907f886dd23a56dd882ee7d4f41c41d732612b2e4da88
- 46fa9a69989b79b56495a1ece8a45d6d5ae43c600b8a13ef88f3eb9d84efda02
- 487f0d748a13570a46b20b6687eb7b7fc70a1a55e676fb5ff2599096a1ca888c
- 4ca84be5b6ab91694a0f81350cefe8379efcad692872a383671ce4209295edc7
- 53095e2ad802072e97dbb8a7ccea03a36d1536fce921c80a7a2f160c83366999
- 55016f61b9880be414cc4e1280d6bb620cfbe5e1e8e12e305a304d3dff7e209c
- 597c492a5af56d935d360fcfd2c1e89928dde492c86975f2c5cc33ec90b042ce
- 60b1394f3afee27701e2008f46d766ef466caa7711c45ddfd443a71efc39a407
- 61dfe2ccdc7cee55cf0530064499a52bf93bc6c3d8996ed013fcc5692e94c73a
- 667821f5996855bf83507fb1009f5d8d36c1258aa3c776106d453200f3bb0ed3
- 77617775dc6fa8b893607d52c3282ece1912bcdd0b583b418399af2eade249b8
- 7b15f570a23a5c5ce8ff942da60834a9d0549ea3ea9f34f900a09331325df893
- 93953eef3fe8405d563560dc332135bfe5874ddeb373d714862f72ee62bef518
- 93fb7f0c2cf10fb5885e03c737ee8508816c1102e9e3d358160b78e91fa1ebdb
- 96e02ea8b1c508f1ee3c1535547f9b89396f557011e61478644ae5876cdaaca5
- a8e999a7a77d3b9846250a34ebda7d80ea83a79b3714b1f7ac8f92bc52a895fd
- a92dd4885af317d36cd62dac31d0d5c93febd367e8f4412e7593fb48c9f34256
- ac1d42360c45e0e908d07e784ceb15faf8987e4ba1744d56313de6524d2687f7
- adefaad2a9c449d0e9fabb5035422a6ce31d0f26b0109a7c2911f570a6c74144
- afb7f11da27439a2e223e6b651f96eb16a7e35b34918e501886d25439015bf78
- b4249f2effb8dd651458c831d38155346c1e2d30b191bf37197ffa5164d25f7c
- ba3c4bc99b67038b42b75a206d7ef04f6d8abaf87a76c373d4dec85e73859ce2
- c62371f129d19707870c0f9a89b0f8a65970aed02537e358e532e4416bc8678e
- dcc7115496faa0797c32bb6d5d823821f19f5177e09e05dbe0151a6b9e1edfb7
- dd03ea7ba369fc9df641c09f29e4abcb8378b5a8dadd3d7c14d47449525f1716
- e136d635de39d23cef600cc53efd671f1e8aba7d982bde152b21ea1f7c04703e
- e7e097723d00f58eab785baf30365c1495e99aa6ead6fe1b86109558838d294e
- ea5c88fe464562227f483e8fc4eb2cf43e98a897aaaa3e94de4d236d5dc6e7e7
- f3a4fb09a0498e7ab3b33338ca6bc03460e43d437d9f3afbfc1a521c1029ff19
- f3f3c692f728b9c8fd2e1c090b60223ac6c6e88bf186c98ed9842408b78b9f3c
- f6669de3baa1bca649afa55a14e30279026e59a033522877b70b74bfc000e276
- f84edc07b23423f2c2cad47c0600133cab3cf2bd6072ad45649d6faf3b70ec30
Encryptors
- 117a057829cd9abb5fba20d3ab479fc92ed64c647fdc1b7cd4e0f44609d770ea
- 3a2f6e614ff030804aa18cb03fcc3bc357f6226786efb4a734cbe2a3a1984b6f
- 46d340eaf6b78207e24b6011422f1a5b4a566e493d72365c6a1cace11c36b28b
- 7f91e10c39e0a77c83af3ef48061cbb73194c793f9c3c8bc7fa1aa0fc75eb385
- f77433e517f493ca54e6a4603e51739053ebfac03d2764ad9d1f7e00cfadefa0
IP Addresses
- 223.0[.]85
- 234.118[.]129
- 238.35[.]26
- 94.160[.]243
- 232.2[.]41
- 99.133[.]112
- 161.48[.]51
- 152.203[.]94
- 123.119[.]100
- 157.43[.]44
- 86.163[.]228
- 53.186[.]224
- 144.145[.]126
- 85.156[.]83
how avertium is protecting our customers
Even with anti-malware solutions installed, BianLian is a great risk to organizations. BianLian’s evolving operating model makes organizations everywhere vulnerable to an attack. However, Avertium has advanced services that can help keep your organization safe:
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a malware attack.
- MDR provides an in-depth investigation into potential threats on an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
- Avertium offers security consulting services to develop robust internal security policies.
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- Avertium offers user awareness training through KnowBe4. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
SUPPORTING DOCUMENTATION
Stung by Free Decryptor, Ransomware Group Embraces Extortion (bankinfosecurity.com)
BianLian Ransomware Gang Continues to Evolve | [redacted]
Virginia city claimed to be attacked by BianLian ransomware | SC Media (scmagazine.com)
BianLian Ransomware Encrypts Files in the Blink of an Eye (blackberry.com)
Decrypted: BianLian Ransomware - Avast Threat Labs
BianLian ransomware crew swaps encryption for extortion • The Register
A Deep Dive Into BianLian Ransomware (securityscorecard.com)
BianLian Ransomware Lists St Rose Hospital As Victim (thecyberexpress.com)
Ransomware payments fell to US$456.8 million in 2022 | TahawulTech.com
BianLian ransomware group shifts focus to extortion | CSO Online
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.