"Bronze Mohawk" & Cyber Espionage
Executive Summary
Active since 2009, the Chinese threat actor Bronze Mohawk (also known APT40) has targeted companies, universities, and government organizations within a wide range of industries. The maritime research, robotics, and biomedical industries have all been victims of Bronze Mohawk and the threat actor has focused their attacks on the U.S., Canada, Europe, the Middle East, and South China Sea.
In July 2019, an indictment against Bronze Mohawk was unsealed by the U.S. Department of Justice. The indictment involved the state-sponsored threat actors using Hainan Xiandun Technology Development Company (Hainan Xiandun) as a front for their malicious cyber activities. Due to Bronze Mohawk’s activities, trade secrets, intellectual property, and other sensitive information has been stolen from organizations within the U.S., as well as foreign governments.
Today, Bronze Mohawk is keeping a low profile, but a recent discovery may link the threat actors to recent malware attacks. Let’s take a look at Bronze Mohawk and why we need to keep a watchful eye on cyber espionage.
bronze mohawk (apt40)
Bronze Mohawk has several names, those names include: FeverDream, APT40, G0065, Gadolinium, GreenCrash, Hellsing, Kryptonite Panda, Leviathan, MUDCARP, Periscope, Temp.Persiscope, and Temp.Jumper. In July 2019, four members of the group were charged with attacking governments, universities, and various companies across the globe on behalf of the Chinese government.
The four suspects were a part of a much larger operation which set up a company (Hainan Xiandun) as a front for their attack campaigns. According to the Intrusion Truth blog, Hainan Xiandun was under the direction of the Chinese Ministry of State Security (MSS) and an employee, Wu Shurong, worked as a hired hacker for the company. Shurong created malware and used it to compromise computer systems belonging to universities, governments, and companies.
The other three suspects were MSS officers who worked for the Hainan provincial department, their names are: Ding Xiaoyang, Cheng Qingmin, and Zhu Yunmin. The U.S. alleged that the MSS has directed Bronze Mohawk’s attack campaigns since 2011 – directing them to steal confidential business information for dissemination in China.
Tactics & Techniques
To access and operate their malware and hacking infrastructure, Bronze Mohawk (APT40) used the Tor network and often used email, GitHub, domains, servers, and Dropbox accounts to deploy their malware. GitHub was used to store malware, as well as stolen data, with the stolen data being concealed via steganography. Steganography is when threat actors hide a secret message behind something that isn’t a secret. In Bronze Mohawk’s case, they hid stolen information in images that mostly portrayed U.S. President, Donald Trump.
Between 2011 and 2018, Bronze Mohawk (APT40) was actively breaching targets in Cambodia, Germany, Indonesia, Malaysia, Norway, U.S., South Africa, the United Kingdom, Austria, Norway, Saudi Arabia, and Switzerland. The confidential information the threat actor stole includes specialty chemical formulas, sensitive technologies used for submersible and autonomous vehicles, and trade secrets related to proprietary genetic sequencing. Bronze Mohawk (APT40) also stole data from research institutes and universities which included research related to MERS, Marburg, Ebola, and tularemia.
According to the Department of Justice, the data was given to China to aid in securing contracts for state-owned enterprises within targeted countries, resulting in better contract bids for Chinese companies and gaining an edge on competitors. Hainan Xiandun was used in collaboration with Bronze Mohawk (APT40) and university staff to recruit hackers and linguists from the universities’ ranks to assist in potential intrusions.
Bronze Mohawk (APT40) used several tactics and techniques, as well as a large library of custom and open-source malware to gain initial access via user and administrator credentials. Their tactics and techniques also allowed them to enable lateral movement once inside a network and locate valuable assets to exfiltrate data. Bronze Mohawk used tool frameworks and malware to accomplish their goals which include:
- Using steganography to hide stolen data inside other files stored on GitHub
- Use of domain typosquatting for C2 infrastructure
- Protocol impersonation by using API keys for Dropbox accounts in commands to upload stolen data to make it appear that the activity was legitimate use of the Dropbox service
- Protocol tunneling and multi-hop proxies including the use of Tor
- Archive, encrypt, and stage collected data locally and remotely for exfiltration
- Exfiltration over C2 channel – CISA
Spearphishing emails
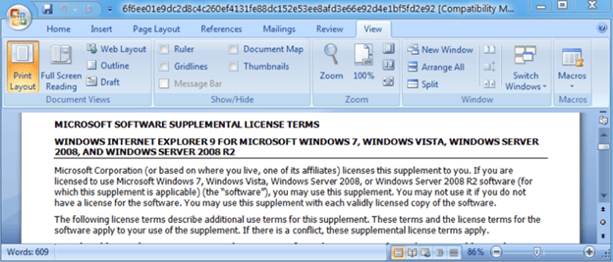
In September 2017, Proofpoint observed spearphishing emails from a group targeting a U.S. shipbuilding company, as well as a U.S. university research center with ties to the military. The emails contained “Apply for Internship Position” in the subject and an attachment titled “resume.rtf”. A second attachment was titled “ARLUAS_FieldLog_2017-08-21.doc” and contained “Torpedo recovery experiment” as bait.
The email attachments were designed to exploit CVE-2017-8759 and the targeted spearphishing emails with malicious URLS were sent to multiple defense contractors. Additionally, Bronze Mohawk exploited vulnerability CVE-2017-0199 to deliver the payload and many documents, domains, and payload domains misused the brand of a provider for ships, submarines, and other military vessels. Other victims were targeted via social engineering and were lured into opening and starting an embedded PowerPoint presentation. The presentation contained an embedded JavaScript[5] that was triggered by clicking “Enable” in a warning dialog box – causing the payload to download.
The spearphishing campaigns primarily targeted South China Sea. Bronze Mohawk (APT40) was discovered to be behind the attacks, utilizing Microsoft Excel and Word documents with macros to target an international law firm, as well as the Philippines Department of Justice. The backdoor Bronze Mohawk used includes:
- Information gathering (IE version, OS version, OS 64-bit/32-bit, etc.)
- Overwriting registry settings to reduce malware visibility on system
- Download file
- Upload file
- Execute a command with cscript
- Execute JavaScript
- Execute shell command
- Execute a dll (via an embedded ‘MockDll')
- Get proxy info
- Get process list
- Terminate process
- Get drive info
- GET request to a URL
- POST request to a URL – com
Image 1: Email Sent with Malicious Intent to a Well-known Shipbuilder
Source: Proofpoint.com
china chopper
According to Talos Intelligence, one tool that Bronze Mohawk (APT40) used heavily is China Chopper – a tool that allows them to remotely control the target system that needs to run a web server application before it can be targeted by the tool. Various state-sponsored threat actors have used the tool and Talos Intelligence observed Internet Information Services and Apache web servers compromised with China Chopper web shells. However, there is no data that reveals how the web shell was installed.
How Does China Chopper Work?
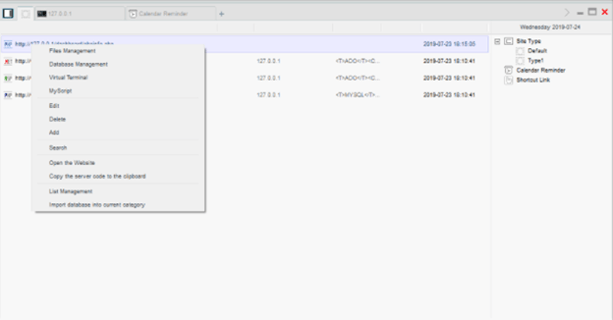
China Chopper is a public hacking tool. Threat actors are provided with a GUI that allows them to configure servers to connect to, as well as generate sever-side code that needs to be added to the targeted website code to communicate. The simple sever-code contains a single line of code and the backdoor supports .NET Active Server Pages or PHP.
Image 2: China Chopper GUI
Source: Talointelligence.com
Researchers aren’t sure if the simplicity of the server code was an intentional decision for the China Chopper developers to make detection more difficult. Additionally, researchers found a remote shell (Virtual Terminal) function in China Chopper that has an initial suggested command of ‘Netstat an|find “ESTABLISHED.”
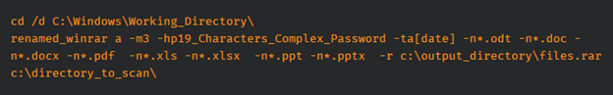
Talos observed China Chopper in a few cyber espionage campaigns. The tool was used in a campaign targeting an Asian government organization. In the observed campaign, China Chopper was installed on web servers used to store confidential documents. The attackers’ goal was to obtain documents and database copies, which were automatically compressed using WinRAR.
Image 3: Command for WinRAR
Source: Talointelligence.com
China Chopper was also observed in a campaign targeting an organization in Lebanon. The campaign involved an auxiliary public website compromised by several attackers for different reasons. Also, Talos Intelligence observed China Chopper being used to compromise Asian web-hosting providers – with the most significant compromise involving several Windows servers over a 10-month period.
China Chopper has proven to be an effective entry point for attackers like Bronze Mohawk (APT40). It’s an old tool but it has allowed threat actors to install additional tools like web shells. China Chopper is still being used by threat actors who have various goals because it’s easy to use and very hard to connect to a specific group. Here is a list of other tools used by Bronze Mohawk (APT40):
- AIRBREAK
- BlackCoffee
- Cobalt Strike
- Derusbi
- Derusbi Trojan
- FUSIONBLAZE
- GREENCRASH
- HOMEFRY
- Metasploit
- Metasploit/Meterpreter
- MURKYTOP
- NANHAISHU
- Orz
- ScanBox
- SeDII
shadowpad malware attacks
The tool ShadowPad is a great example of the advanced nature of Chinese threat actors. In February 2022, researchers linked ShadowPad malware attacks to China’s civilian and military intelligence agencies. ShadowPad is a modular backdoor that’s recently been adopted by Chinese threat groups. According to a report by Secureworks, ShadowPad is decrypted in memory using a custom decryption algorithm.
“ShadowPad extracts information about the host, executes commands, interacts with the file system and registry, and deploys new modules to extend functionality." - Secureworks
ShadowPad is a remote access trojan that has been used by the government-sponsored threat group, Bronze Atlas (also known as APT41). The trojan maintains persistent access to compromised computers and executes arbitrary commands and next-stage payloads. So far, ShadowPad has been used in supply-chain attacks, distributed via NetSarang, ASUS, and CCleaner.
Bronze Atlas (APT41) was initially the only threat actor attributed to ShadowPad Malware attacks, but ShadowPad has been used by multiple Chinese threat actors since 2019. Secureworks attributed distinct activity clusters to Chinese nation-state groups that cooperate with the People’s Liberation Army Strategic Support Force (Chinese military).
Although Secureworks has not attributed Bronze Mohawk (APT40) to the ShadowPad malware attacks, Bronze Mohawk has been linked to Chinese military in the past. In 2016, an incident occurred that paralleled with China’s cyber activities. According to Mandiant, a U.S. Navy unnamed underwater vehicle (UUV) was seized by China’s People Liberation Army Navy (PLAN). Within one-year, Bronze Mohawk began targeting universities that conducted naval research, while masquerading as a UUV manufacturer. Given the use of ShadowPad by other MSS affiliated threat groups, there is reasonable probability that Bronze Mohawk could have access to ShadowPad or a similar type of tool.
cyber espionage
Advanced persistent threat (APT) actors like Bronze Mohawk (APT40) and Bronze Atlas (APT41) continue to use spear-phishing and social engineering techniques to gain access to systems and networks for the sole purpose of leaking sensitive information. Their motives are varied and can include anything from trying to gain a competitive advantage to gaining information they can use to later carry out attacks for financial gain.
Although APT attacks can be difficult to attribute, data theft can still be detected. Unfortunately, sometimes, data theft may be the only clear indicator an organization has to lean on when they are under a cyber attack. There are two ways that your organization can recognize APTs in their networks and systems:
- APT attacks are often carried out in multiple phases, reflecting the same sequence of gaining access and maintaining access. They will also attempt to remain undetected in their victim’s network until their goals are accomplished.
- APTs establish multiple points of compromise. They will attempt establish several entry points to their targeted networks – enabling them to retain access even after malicious activity is noticed and incident response is triggered.
Your organization can detect advanced persistent threats by remembering the following:
- Unusual account activity needs to be investigated immediately.
- APTs use Trojan horse malware as a backdoor.
- Odd database activity, for example a spike in database operations involving increased data reads, should be investigated immediately.
- Unusual data files can indicate data that has been bundled into files to assist with exfiltration.
Bronze Mohawk’s espionage activities targeting the U.S. and Western Europe are concerning. Although the threat actor has not made any large waves recently, the fact that they have access to remote access Trojans, such as ShadowPad, is enough to stay guarded. If you implement cyber security best practices and remain alert, then you can help keep your organization safe from APTs like Bronze Mohawk.
How Avertium is Protecting Our CUSTOMERS
Once an APT like Bronze Mohawk (APT40) is inside a network, it can give them unlimited access to do further reconnaissance. Chinese APTs are some of the world’s oldest and most skilled when it comes to cyber espionage. Avertium is here to keep your organization safe and to mitigate any attacks caused by Chinese APTs like Bronze Mohawk:
- To identify the source of your breach and the scope that it reached; you’ll want to include Avertium’s DFIR (Digital Forensics and Incident Response) services in your protection plan. We offer DFIR to mitigate damage from a successful breach. This service is provided as an on-demand crisis response service, as well as retainer-based program.
- Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- MDR provides an in-depth investigation into potential threats on an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
Avertium’s Recommendations
Avertium recommends the following recommendations issued by CISA:
- Maintain up-to-date antivirus signatures and engines.
- Keep operating system patches up to date.
- Disable File and Printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
- Restrict users' ability (permissions) to install and run unwanted software applications. Do not add users to the local administrators’ group unless required.
- Enforce a strong password policy and implement regular password changes.
- Exercise caution when opening e-mail attachments even if the attachment is expected and the sender appears to be known.
- Enable a personal firewall on agency workstations, configured to deny unsolicited connection requests.
- Disable unnecessary services on agency workstations and servers.
- Scan for and remove suspicious e-mail attachments; ensure the scanned attachment is its "true file type" (i.e., the extension matches the file header).
- Monitor users' web browsing habits; restrict access to sites with unfavorable content.
- Exercise caution when using removable media (e.g., USB thumb drives, external drives, CDs, etc.).
- Scan all software downloaded from the Internet prior to executing.
- Maintain situational awareness of the latest threats and implement appropriate Access Control Lists (ACLs).
MITRE TTPS
[T1583.001] Acquire Infrastructure: Domains
[T1585.002] Establish Accounts: Email Accounts
[T1585.001] Establish Accounts: Social Media Accounts
[T1133] External Remote Services
[T1566.001] Phishing: Spearphishing Attachment
[T1566.002] Phishing: Spearphishing Link
[T1189] Drive-by-Compromise
[T1190] Exploit Public-Facing Application
Indicators of Compromise (IoCs)
Bronze Mohawk (APT40)
- f5ce889a1fa751b8fd726994cdb8f97e
- bc4c189e590053d2cf97569c495c9610
- a7e4f42ad70ddd380281985302573491
- 28c6f235946fd694d2634c7a2f24c1ba
- ab662cee6419327de86897029a619aeb
- e195d22652b01a98259818cfbab98d33
- b6c12d88eeb910784d75a5e4df954001
- 31a72e3bf5b1d33368202614ffd075db
- ba629216db6cf7c0c720054b0c9a13f3
- c0ad63a680fbdc75d54b270cbedb4739
- ce26e91fc13ccb1be4b6bf6f55165410
- cd049c2b76c73510ae70610fd1042267
- e3867f6e964a29134c9ea2b63713f786
- 7f7d726ea2ed049ab3980e5e5cb278a3
- 7c49efe027e489134ec317d54de42def
- 7b3f959ab775032a3ca317ebb52189c4
- 2f0a52ce4f445c6e656ecebbcaceade5
- 2c9737c6922b6ca67bf12729dcf038f9
- 5064dc5915a46bfa472b043be9d0f52f
- 4b18b1b56b468c7c782700dd02d621f4
- 1c35a87f61953baace605fff1a2d0921
- 166694d13ac463ea1c2bed64fbbb7207
- 8c80dd97c37525927c1e549cb59bcbf3
- 5d9c3cb239fa24bed2781bcf2898f153
- 838ceb02081ac27de43da56bec20fc76
- 83076104ae977d850d1e015704e5730a
- e1512a0bf924c5a2b258ec24e593645a
- 2366918da9a484735ec3a9808296aab8
- 2e5b59c62e6e2f3b180db9453968d817
- 2dd9aab33fcdd039d3a860f2c399d1b1
- 8a9ac1b3ef2bf63c2ddfadbbbfd456b5
- 6e843ef4856336fe3ef4ed27a4c792b1
- 6c67f275d50f6bfee4848de6d4911931
- 6b7276e4aa7a1e50735d2f6923b40de4
- 3c2fe2dbdf09cfa869344fdb53307cb2
- 35f456afbe67951b3312f3b35d84ff0a
- d59a77a8da7bec1f4bad7054a41b3232
- 043f6cdca33ce68b1ebe0fd79e4685af
- Mlcdailynews[.com]
- Mihybb[.com]
- microsql-update[.info]
- cnnzapmeta[.com]
- chemscalere[.com]
- thyssenkrupp-marinesystems[.org]
- thestar[.live]
- teledynegroup[.com]
- scsnewstoday[.com]
- [com[
- 0476fd740f7ead15054e0f8f641ad1041e74dae7
- 05e5632ca8c205457d537a6206314e17aad9c9e5
- 1875db18a7c01ec011b1fe2394dfc49ed8a53956
- 1d1d37b9a1c35f8e352abe33af5164e61fb61f29
- 37bb800b2bb812d4430e2510f14b5b717099abaa
- 4648d63cabd3cdd2a1acd19561f7c71c0e2ae998
- 4e6efde1d54f641450aa371c97f4d561dc68336a
- 5ef9515e8fd92a254dd2dcdd9c4b50afa8007b8f
- 80216b2b4d48086fc063da550af9757543ec0d8c
- 893b083a8eea329c4d16c72b7ff11697a268c2ac
- 8cb454058441ecfd9e68717b9ed1e7178cf9a614
- b6643ff79369bbc3aa3c62599671b5b166505432
- bf8a297b4a1fd8ee1666be74afca80a8addb145d
- db8603ac6cac7eb3690f67af7b8d081aa9ce3075
- e9a9ce1ff07834d6ba9a51ba0d9e7c7a0b68d3e5
- f3b5333a0a8a97d605d4c1e2b5e8755538862fac
- f599b5d61d2dfc4ad5096f3d6516a10a1b3c0acf
- fcc9cb750629346bfe638d5264b188d9fce8c5a3
- 15292172a83f2e7f07114693ab92753ed32311dfba7d54fe36cc7229136874d9
- 2cc3db96957b473cd15f5a80096365882ec64a0104ff7a5016c5acee9cd3f88d
- 305f331bfb1e97028f8c92cbcb1dff2741dcddacc76843e65f9b1ec5a66f52bc
- 39c952c7e14b6be5a9cb1be3f05eafa22e1115806e927f4e2dc85d609bc0eb36
- 51db2e43952929af6a4374d140c7131b7372d96448175a356dcea8ec29a576f7
- 5860ddc428ffa900258207e9c385f843a3472f2fbf252d2f6357d458646cf362
- 6f6ee01e9dc2d8c4c260ef4131fe88dc152e53ee8afd3e66e92d4e1bf5fd2e92
- 7c54e1a5dbabf54d0cd43028218d38e5f83158f3f5235599723907b40389ac5d
- 986c3796ceadfcd7cb6f5cc81e9e0c2d4e3622d2ef0763bf342f32286574bebb
- 9c780f7b06a006211e1393ada39ebf71cb24cd93e84802dcd61ea5be23a96d7f
- b45d5e477070a1116e6f7f1ea48ed350900240ccf509c135dc75fa0899ee1e28
- ced7ca9625543d3d3d09f70223cc19f0d99e21792854452df5ba84b3a59d17b8
- ed1544835e4ee92a3b19ecaa97d6e8fe63c28274f25d85b748361f82e0701986
- f0df80978b3a563077def7ba919e2f49e5883d24176e6b3371a8eef1efe2b06a
- fc0fad39b461eb1cfc6be57932993fcea94fca650564271d1b74dd850c81602f
- fd0c9c28781de60ed70f32b9e138ab7d95201a5f08a4bc0230b24493597022d7
- http://nmw4xhipveaca7hm.onion.link/en_US/[all.js]
- http://www.yorkshire-espana-sa.com/english[/servicios/]
- chickenkiller[.com]
- chickenkiller[.com]
- ignorelist[.com]
- onion[.link]
- chickenkiller[.com]
- chickenkiller[.com]
- chickenkiller[.com]
- mooo[.com]
- chickenkiller[.com]
- mooo[.com]
- yorkshire-espana-sa[.com]
- uk[.to]
- airbusocean[.com]
- cargillnotice[.com]
- ccidmeekparry[.info]
- ccvzvhjhdf[.website]
- cdigroups[.com]
- checkecc[.com]
- corycs[.com]
- deltektimes[.com]
- gttdoskip[.com]
- huntingtomingalls[.com]
- indiadigest[.in]
- jack-newnb[.com]
- louisdreyfu[.com]
- masterroot[.pw]
- net
- msusanode[.com]
- newbb-news[.com]
- nfmybb[.com]
- onlinenewspapers[.club]
- onlineobl[.com]
- oyukg43t[.website]
- pacifichydrologi[c.org]
- philippinenewss[.com]
- philstarnotice[.com]
- santaclarasystem[.us]
- secbkav[.com]
- [com]
- teledyneinstrument[.com]
- thrivedataview[.com]
- thyssemkrupp[.com]
- trafficeco[.com]
- transupdate[.com]
- troubledate[.com]
- ultrasocial[.info]
- usdagroup[.com]
- yootypes[.com]
- uk[.to]
- 022bd2040ec0476d8eb80d1d9dc5cc92
- 25b79ba11f4a22c962fea4a13856da7f
- 280e5a3b9671db31cf003935c34f8cf9
- 2bf998d954a88b12dbec1ee96b072cb9
- 3647d11c155d414239943c8c23f6e8ec
- 3bf8bb90d71d21233a80b0ec96321e90
- 3eb6f85ac046a96204096ab65bbd3e7e
- 3fefa55daeb167931975c22df3eca20a
- 40528e368d323db0ac5c3f5e1efe4889
- 51e21a697aec4cc01e57264b8bfaf978
- 67dbecfb5e0f2f729e57d0f1eda82c67
- 693a4c2fcaa67fb87e62f150fb65e00e
- 6e97bf1b7c44edc66622b43e81105779
- 72a7fd2b3d1b829a9f01db312fdd1cd7
- 8361b151c51a7ad032ad20cecf7316f4
- 9e592d0918c029aa49635f03947026e8
- a6cab9f2e928d71ed8ecf2c28f03a9a2
- aaafb1eeee552b0b676a5c6297cfc426
- c808d2ed8bb6b2e3c06c907a01b73d06
- e6348ee5beb9c581eeeaf4e076c5d631
- e6a757114c0940b6d63c6a5925ade27f
- f0881d5a7f75389deba3eff3f4df09ac
- 1b41728fced7b356f6d6b52375a224d5eb1f5427
- 1da0867848f15ed27a2bcc2044f008ad184029f1
- 1ede7c4b35b423312ca23c0d424df9799986b4a5
- 2f15388c73bb9c72ba82025d9f90b91ef2e78fd4
- 35493e06b0b2cdab2211c0fc02286f45d5e2606d
- 3611975f9836b7122d88540007703f5dc483d46c
- 3d981823b7573c52580f0c1188281d85887f7bbb
- 450fa23cfc11d8ee326f43fa7675e21271598c48
- 48e7aeb484918e02c59ac48e94d9976f463b04c0
- 52867d687b4bca88fa609c7bc4489de0ae4ad9ce
- 5b8c6e81e8e09b9d000283d44b26d3d5bf8a42b6
- 5e39ea9a92662270f616860546277eaa3703ca8a
- 61a11dde01187732606b024977556e9f32eddab3
- 70bae228bb1c0c59dad7b3935dc94d561027cab8
- 726d20d4d7ed373289da035178674b9cc74775e6
- 776e7079734bc4817e3af0049f42524404a55310
- 7a87ceb3806aa5eda9eb87d907bc0637e0846e1f
- 7c13c9357f4d9aec2bd568297aa848354405c58a
- 7d8319a8387d285eed3c612fe52183e71027daa7
- 8404f2776fa8f7f8eaffb7a1859c19b0817b147a
- 844733bb6b3016fb818bdc69442b3b600bde2f16
- 848cdddfda987f6400d2702073d6010391262c41
- 8d39faee860d607de5e655b6183b3760190bef01
- 972ab587cdb63c8263eb977f10977fd7d27ecf7b
- 9a491d8a3c139aadc01dca18037c807874cdec26
- 9d4aa4b062b63abc54665487326278455ca087e4
- a2c8d0a902e51e5261e7e7c7f69aa4935643dbad
- a8875b34633e30d62354e27abc0a3dc6c500c172
- b85368d79231edf57b8f840c876b539657f2d3ae
- c90f05d04b8ef36bf61cc0d29565affe29cfd8c1
- ca1d5cbb92f017f4893715f050904f405f43a058
- cc13255a309004c76055201d9e9a571165128821
- d0208ab4e095c352082373659c7d6fd2499aa460
- d058567274b5d10f78eebefde62e35f6a389272f
- d5b6bd94292178b529cc957f2c95a32d43b1142a
- d76896ee771a5fb0a0d4ec3e3ab67ab6eeb398e1
- d8be779cc6ecedbe8d64df5b385da6956c656917
ShadowPad
- 188.33[.106]
- 06539163f71f8bd496db75ccb41db820
- 0ddd78208c16e9f8174868bdf92eac9b
- 1480d2856e4d57d0c8394ade835493db
- 17268032c7562fa9473bb85018cb1c2c
- 17e812958704f4ced297731ce47de020
- 246d233f4fcda6f4c1ec1177dbad31b4
- 27d889c351ac2f48d31b91d06061ec8d
- 299980c914250bac7522de849f6df24f
- 3520e591065d3174999cc254e6f3dbf5
- 373eacf3ffd1b5722f9d3c1595092b4c
- 3e372906248b215ea0ee853cb4e29dd8
- 40e7f1a18735819d6cf5f5cff0fb72f4
- 41ff21ea773b73812d91f91b68280ed3
- 59961f8c3d8d6cfb7a378f58ff5c5f30
- 5fe99a8f8cbfe46832478aa9c9634ed6
- 6538263d35b9bb438a9648e904ed7394
- 9d686ceed21877821ab6170a348cc073
- b1a9afc937a6e7e0d09e5ccd8b2198f5
- b40dec21d0c3061bef422bb946366cba
- bda94af893973fe675c35e5699d90521
- c3292a51c1b92d7dd08518095bb851f8
- dfd3b637fc35e850138b33758934f3f7
- ea6be331b5fa349a2fa464b062043b0e
- f977be4ebb0d06c9a19b37d8bbb37178
- fac0b4fe5372d76607c36ccb51e6b7bb
- ffbadead054d1eac270f1a24d02e8a1f
- 363e32fafd2732b3cfb53dfd39bef56da1affd7f
- 3dfa0fc7da98d0efbd6dbc4b47e01f669e54ea07
- 3ebeb4e08c82b220365b1e7dd0cc199b765eed91
- 47cdaf6c5c3fffeeff1f2c9e6c7649f99ab54932
- 57b5ca13d7b2dd9287bdda548ccf7b21c1201464
- 78f59be833fe8a504a0def218d72aef62823bdaf
- 880fa69a6efd8de68771d3df2f9683107fb484c0
- 8d0be3bca6c93b1ab396ec4a93a33371c82b6567
- 92c091453295536aef0bac93aa24a294624266da
- 952614358b37d2a519d66ee7759c70e31218ed36
- c62b977c93979effb48a1614956c2a788abb22fe
- c73329dfbe99de4abb93b4fda6310a0c5eedd8f9
- ea60a4100d7a893079c29a6027d604759f62c63b
- f5b7ea5e705655a1bc08030b601443088a5af4dd
- fa639e82ae481a70dffff2c50745ada660c93aa8
- 0371fc2a7cc73665971335fc23f38df2c82558961ad9fc2e984648c9415d8c4e
- 0942f4a488899d5d78b31a0065e49c8689ccda88efc28186e29ee76861ba99da
- 244e22147cc1e37543159a95cf4674a61f290af305c1c1e37b69c45b444f9097
- 2e07d66155987216dc8cc095b48dd971415f0da261b5b26c58a0e3d34f446038
- 2e6ef72d05b395224a03a73a50eaee1c9dc682976c99dde5317b76938cb669a4
- 4557e923602730aab7718b61eeaf3a93edd0339a3c89c8f7061b9818c2df5203
- 69eb1aa0021c9b6905b8f0a354884a67f18d20aa045db20b5b5d59f41c7f201f
- 73bb7e7d0743d40a1d967497a5fbb79c07132eb15a546fa25bbecaf43993a1d2
- 8065da4300e12e95b45e64ff8493d9401db1ea61be85e74f74a73b366283f27e
- 8d1a5381492fe175c3c8263b6b81fd99aace9e2506881903d502336a55352fef
- 9c28c1b2ff0a84c8b667f128626f28b173feb07481192e214b5a29b98964a7f9
- a8e5a1b15d42c4da97e23f5eb4a0adfd29674844ce906a86fa3554fc7e58d553
- d8f695730fcf2cb5a894107740be0a0fa9bbae6851b83d396976a678236dec30
- dbb32cb933b6bb25e499185d6db71386a4b5709500d2da92d377171b7ff43294
- 255.179[.186]
- 180.141[.16]
- 202.198[.246]
- 197.18[.30]
- 200.21[.190]
- 56.228[.89]
- Rolesnews[.com]
- symantecupd.[com]
- epac[.to]
- casacam[.net]
- dnset[.com]
- mrbonus[.com]
- musicweb[.xyz]
- videocenter[.org]
- dnsdyn[.net]
- kozow[.com]
- lubni23[.com]
- microsoft.msglocalmicro[.com]
- wikimedia[.vip]
- ekaldhfl[.club]
- casacam[.net]
- cloudvn[.info]
- nslookup[.club]
- 0b75c1507d6849b303fb496ab8afa60c6c3e8624
- 0d0c5e63a9daf3c322667310e1c06c8b896f7b4c
- 41b78af0a34f2d1da8d52d895ee50da26f2a5ab4
- 56ff0a3f5d8f67468f1771d38cc6d017a0cd6462
- 5f751bab830f5470fcbac04b1c165bc0b6e6ecff
- 680bcd1b172a3658954931131f8248bf66dbc5b1
- 9605ad1bf0432ffb148d422099e23eaa26bed4c8
- 9a035477c1ef725309ae4afac50ffc18d8194a90
- b224ae9ffd8119d773dedb1863d46725c29143f8
- e76049ee244e74729a20f666328d5eeff8d6488f
- 04089c1f71d62d50cbd8009dfd557aa1e6db1492a9fa2b35902182c07a0ed1c1
- 0dfd91a0dd5d1143697413ebd50efde2411d07b4113d7d282ca0ec3c9d77d5ed
- 136848cfbd59af5dcba0fcfb3257bb714184129f94d1a67def618f39dde7c17d
- 1402ed922a7efc05a6d9482136598fdb52afd95cb4e40190ea44a3ba087a58ab
- 18c4a15e587b223a3fb4d27eedeb16b81e5c75409d9ffbbe8aeeb7c4c2bd5041
- 253f474aa0147fdcf88beaae40f3a23bdadfc98b8dd36ae2d81c387ced2db4f1
- 9981b9d2024665b7312b673926be96df34be2dc9779956ff49690968e0265d2d
- bc0c31be0d4784a6f8ad6333767580e61e7bbe500139fe0d111c39475470a312
- bf3de88459f85ddd85245e3f1ce3bba6568919bbe46a808ad5d94d5415014926
- c602456fae02510ff182b45d4ffb69ee6aae11667460001241685807db2e29c3
- d48e671df571b76ee94c734bdd5272e12fcd1362f1d75138ff547bc2bc0c31ef
- ec6852c341aff9d770debc1ef72fb5795c4d71c1327d57d79d65136cc2a670a4
Supporting Documentation
MAR-10331466-1.v1: China Chopper Webshell | CISA
What is advanced persistent threat (APT)? Definition from SearchSecurity (techtarget.com)
APT40: Examining a China-Nexus Espionage Actor | Mandiant
US indicts four members of Chinese hacking group APT40 - The Record by Recorded Future
ShadowPad Malware Analysis | Secureworks
HainanXiandun – Intrusion Truth (wordpress.com)
Leviathan: Espionage actor spearphishes maritime and defense targets | Proofpoint US
Researchers Link ShadowPad Malware Attacks to Chinese Ministry and PLA (thehackernews.com)APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
READ OUR LATEST BLOG >>> THE ART AND SCIENCE OF THREAT HUNTING - A GUIDE TO PREVENTING CYBER ATTACKS
Learn what threat hunting is, what it has gained so much popularity, how your business can benefit from its true value, and more.