An In-Depth Look at APT35 aka Charming Kitten
Executive Summary
The Iranian advanced persistent threat actor and cyberespionage group, APT35, also known as Charming Kitten or Phosphorus, has been making headlines since 2014. During that time, the group launched one of the most sophisticated internet based spying campaigns organized by Iranian threat actors – a campaign conducted via social media.
Since then, the group has not slowed down and has been responsible for several other cyber attacks around the world. In 2019, APT35 was responsible for targeting several academic institutions in the U.S, France, and the Middle East region. In late 2020, the group targeted medical research organizations in Israel and in the U.S. By 2021, APT35 was abusing Microsoft Exchange Server vulnerabilities that were chained together (ProxyShell).
As of 2022, APT35 has been observed using new tactics to attack a wide range of targets. Using a new strain of malware, the threat actors were able to use the malware for intelligence collection. The group has also been seen using a new tool called Hyperscrape to quietly extract emails from victim’s mailboxes. Let’s take a look at APT35, their tactics and techniques, and what a tool like Hyperscrape can do for an advanced persistent threat actor like APT35.
Note: APT35 and Charming Kitten will be used interchangeably throughout this report.

apt35 aka charming kitten
As previously mentioned, Charming Kitten has been on the radar of the infosec community since 2014 despite being active since 2013. Over the past few months, the Cybereason Nocturnus Team has observed an uptick in activity from the Iranian APT. Charming Kitten was previously known for attacking medical research organizations in the U.S. and in Israel, using malicious PDFs to lure their victims and they have continued to include the medical sector in their attacks.
In 2020, researchers discovered Charming Kitten targeting a small but specific group of people in the medical research field – particularly oncology, genetics, and neurology. The threat actors used a spear-phishing technique and sent emails to their victims with the subject line “Nuclear Weapons at a Glance: Israel.” The emails contained information about Israel’s nuclear capabilities and a link to a malicious website which was controlled by the threat actors. Once the victim clicked on the email, they were taken to a phishing page that asked them to enter their Microsoft OneDrive credentials. The campaign was known as “BadBlood” and was highly targeted – a typical campaign for APTs in general.
It is not unusual for Charming Kitten’s phishing campaigns to target a select number of people, but it is unusual for Iranian APTs as a whole. It is suspected that Charming Kitten is associated with Iran’s Islamic Revolutionary Guard Corps due to the group’s targeting and collection aligning with the entity.
In 2019, Microsoft’s Digital Crimes Unit took over the infrastructure of APT35. At the time, APT35 was responsible for spear-phishing campaigns against several individuals and organizations (activists, journalists, defense companies, etc.). The takedown included a court order for Microsoft to assume control of 99 domains that belonged to APT35 and that the group used during their phishing campaigns. Most of the domains looked as if they belonged to Microsoft or other legitimate technology companies.
The emails associated with the campaigns contained links that eventually lead to the installation of malware and the domains were used as a part of the command-and-control infrastructure of the group. In addition to attacking journalists and medical professionals, APT35 has used their malware to gain entry into computer systems for businesses and government agencies to steal sensitive information. However, the group especially had an interest in activists and journalists involved in advocacy and reporting on issues in the Middle East.
“The action we executed last week enabled us to take control of 99 websites and redirect traffic from infected devices to our Digital Crime Unit’s sinkhole. The intelligence we collect from this sinkhole will be added to MSTIC’s existing knowledge of Phosphorus and shared with Microsoft security products and services to improve detections and protections for our customers.”
- Tom Burt – Corporate Vice President of Customer Security & Trust for Microsoft
recent attacks - tactics & techniques
APT35 is still active despite the 2019 takedown, and in February 2022, the group was seen using a new toolset that included a novel backdoor, malware loaders, a browser info stealer, and a keylogger. They were also seen using open-source tools such as the DiskCryptor library, BitLocker, and Fast Reverse Proxy.
APT35 was seen deploying a new PowerShell Backdoor called PowerLess Backdoor and they were using a stealthy technique to avoid detection. The PowerShell Backdoor was being run in a .NET context instead of spawning the PowerShell process. The PowerLess Backdoor supports the following capabilities:
- Downloading and executing additional malware and files (Keylogger module and Browsers info stealer)
- Keylogging
- Killing processes
- Stealing browser data
- Executing arbitrary commands
- Encrypted channel with the C2
While analyzing, security experts from Cybereason noticed several grammatical mistakes in the backdoor’s code, suggesting that English was likely not the native language of the backdoor’s authors. Cybereason also found links between the APT35 and Momento Ransomware – a ransomware group that initially appeared in 2021.
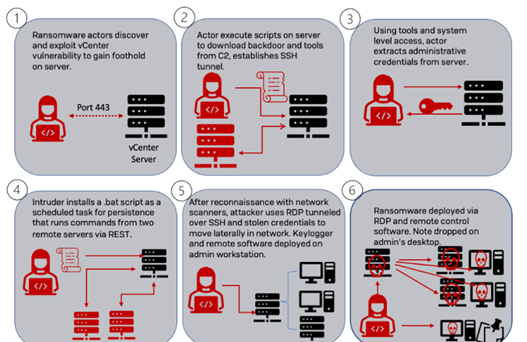
Momento exploited CVE-2021-21972 – a VMware vCenter Server vulnerability that could be exploited by remote attackers without user interaction. There were several similarities between the TTPs used by APT35 and Momento ransomware, such as shared URL directory patterns and similar file naming schemes. According to Sophos, Momento ransomware features a unique failsafe mechanism that locks files inside password-protected WinRAR archives. This is done in case the main file encryption operation fails.
Image 1: Memento Ransomware Attack Chain
Source: Sophos
Iranian groups such as APT35, typically operate as contractors on behalf of the Iranian government and scan the web for popular servers that may be vulnerable due to undisclosed vulnerabilities. Once they find the vulnerable servers, they gain control over unpatched systems.
If the compromised networks are of interest to the Iranian government, the threat actor will deploy malware and glean information from the compromised systems – ensuring that they maintain persistence for future collection efforts. If the target doesn’t have value, APT35 will sell access to the target’s systems on underground forums, or the target will be monetized for the threat actor.
log4j/log4shell
In January 2022, APT35 was seen exploited the Log4Shell/Log4j security vulnerability, seeing it as a new opportunity to strike before organizations patched their affected systems. When Log4Shell emerged, researchers observed the threat actor performing widespread scans just four days after the vulnerability was disclosed. At the tail end of December 2021, Log4Shell took cyberspace by surprise and had cybersecurity professionals panicking. Log4Shell is a zero-day critical vulnerability that was found in the Apache Log4j2 Java-based logging library.
Although conversation regarding Log4Shell has diminished, the vulnerability is still an issue for organizations and remains a permanent threat. Since the vulnerability was publicized, over 80% of Log4Shell’s exploitation attempts originated within the U.S. Because many systems are still using older versions of Log4j, the problems continue to escalate.
APT35 exploited Log4Shell via JNDI Exploit Kits – a publicly available open-source tool that has since been removed from GitHub due to its popularity following Log4Shell. Through analysis, Checkpoint observed that APT35 linked to their malware infection on their victim’s machines for as long as it took for them to achieve their goal. After their goal was achieved, they would disappear without a trace.
hyperscrape
As of August 2022, Charming Kitten was observed using a new tool called Hyperscrape to extract emails from their victims’ mailboxes. The tool allows the threat actors to extract emails from Yahoo!, Google, and Microsoft Outlook. Hyperscrape is written for Windows systems in .NET and is run on the threat actor’s computer. Once the thereat actor has possession of valid email credentials or a valid session cookie, Hyperscrape quietly extracts emails from the victim’s mailbox.
Google’s initial analysis of Hyperscrape indicated that the tool was deployed against Iranian accounts, ostensibly to collect information of Iranian dissidents. Avertium’s Cyber Threat Intelligence Team (CTI) was able to analyze a sample of Hyperscrape. This tool set is not meant to be used on remote machines, and therefore does not attempt to obfuscate its strings. The fact that it is easily caught and quarantined by Windows Defender is not a deterrence. It is the harvested credentials that matter.
Image 2: Hyperscrape - Base64 Encoded IP
Image 3: Hyperscrape
Image 4: Hyperscrape
Source: Avertium Cyber Threat Intelligence Team
Hyperscrape checks its connectivity to a particular command control server after it is executed from a folder with specific file dependencies. Hyperscrape then terminates if there is no connectivity. Next, it opens a form to specify parameters if everything is okay. Once the parameters are provided, data is sent to the command and control for confirmation. Following this action, a new form appears and APT35 provides a valid cookie file unless it was provided via command line.
After starting an embedded web browser, Hyperscrape stores the cookies in a local cache used by the browser. The browser is configured to look like it is outdated. Next, the browser navigates to the targeted email server (Gmail, Outlook, etc.).
When using Hyperscrape, all emails are saved locally in a Downloads folder with the filename corresponding to the email subject. After the emails are dumped, Hyperscrape sends status and system information to the command-and-control server before deleting any security emails from the targeted email server.
Earlier versions of Hyperscrape, allowed APT35 to download data from Google TakeOut, which is a service for customers to download data from Good Documents, Google Calendar, Gmail, and more. After researchers analyzed the tool, they found that functionality may differ for Microsoft and Yahoo! accounts.
In July 2022, researchers found that APT35 had an additional tool that they used to target Telegram accounts. The tool needed access to the victim’s email box to be successful, so it’s suspected that APT35 operates Hyperscrape before using the email data for compromising tools such as the Telegram account dump.
what can organizations do?
In the hands of an APT like Charming Kitten, Hyperscrape is a dangerous tool. However, it’s only successful when the threat actor is already in possession of valid credentials or a valid session cookie of their victim’s mailbox. The way this threat actor obtains credentials and session cookies in the first place is not known. Fortunately, it is quite difficult for threat actors to collect session cookies by way of other means other than using malware. This fact is why users should ensure that their security software is always up to date and patched on their devices.
Another way to keep your environment secure is by using multi-factor authentication to access mailboxes. If your second channel of authentication is one that a threat actor cannot access, your systems and networks will be that much more secure. Keeping your operating system and software up to date/patched will also help ensure that you won’t be compromised by a known vulnerability.
How Avertium is Protecting Our CUSTOMERS
APTs like Charming Kitten can gain unlimited access to networks and systems, furthering reconnaissance. Avertium is here to keep your organization safe and to mitigate any attacks caused by Charming Kitten and other APTs:
- To identify the source of your breach and the scope that it reached; you’ll want to include Avertium’s DFIR (Digital Forensics and Incident Response) services in your protection plan. We offer DFIR to mitigate damage from a successful breach. This service is provided as an on-demand crisis response service, as well as a retainer-based program.
- Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- MDR provides an in-depth investigation into potential threats to an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step. MDR is an outsourced security control solution that includes the elements of EDR, enhanced with a range of fundamental security processes.
- Avertium offers Vulnerability Management to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium offers user awareness training through KnowBe4. The service also Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
Avertium’s Recommendations
- Tabletop Exercises: Have a good cyber incident response plan in place that has been tested with tabletop exercises.
- Security Review: Be sure to review the plan and improve it every time it’s tested on real cyber threats.
- Risk Analysis: Prevent an attack by ensuring your organization has a detailed defense strategy based on a risk analysis approach.
- Cybersecurity Education: Educate your employees on cyber security preparedness and the dangers of opening potentially malicious documents. Annual or quarterly training modules can help prevent threat actors from tricking employees into opening malicious email attachments.
MITRE Map
APT35 aka Charming Kitten
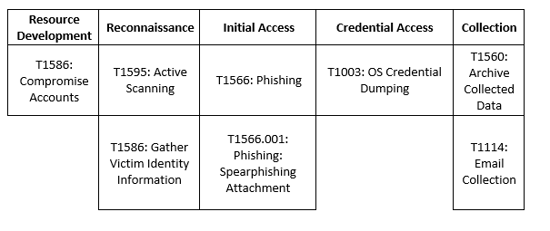
Indicators of Compromise (IoCs)
Avertium IoCs for Hyperscrape
SHA256sum
- 35a485972282b7e0e8e3a7a9cbf86ad93856378fd96cc8e230be5099c4b89208
- 03d0e7ad4c12273a42e4c95d854408b98b0cf5ecf5f8c5ce05b24729b6f4e369
- 5afc59cd2b39f988733eba427c8cf6e48bd2e9dc3d48a4db550655efe0dca798
- 767bd025c8e7d36f64dbd636ce0f29e873d1e3ca415d5ad49053a68918fe89f4
- ac8e59e8abeacf0885b451833726be3e8e2d9c88d21f27b16ebe00f00c1409e6
- cd2ba296828660ecd07a36e8931b851dda0802069ed926b3161745aae9aa6daa
MD5sum
- a1d378111335d450769049446df79983
- ccfb3ba3329e02641c2ed075eb88070a
- 3a62b26311583a23767c35d56b95175d
- 10f5561b7515bc0d66916bef04b63dae
- 5c91c1d833173f6ae599ef1d4133f235
- 45c3592373ba9e5f8f23c6b30fb4d2e4
SHA1sum
- bb700e1ef97e1eed56bb275fde2c5faed008c225
- 221f66582841ec2ef79a46d4f90b0e32642887ba
- aa791a0a98a30e10119b8cc13998b1306275fc1f
- 36fa5a020aca2cfab25661cf2ae7637de1aaf8d4
- 2cb21b71e23cf108067bd02070343883618a5837
- 1f56c3f36800acac714bf78f870d7f066ad25edf
IP Addresses
- 209.51[.54]
- 243.108[.14]
Hyperscrape
- hyperrscraper-3: PE32 executable (GUI) Intel 80386 Mono/[.Net] assembly, for MS Windows
- hyperscraper-1: PE32 executable (GUI) Intel 80386 Mono/[.Net] assembly, for MS Windows
- hyperscraper-2: PE32 executable (GUI) Intel 80386 Mono/[.Net] assembly, for MS Windows
- hyperscraper-4: PE32 executable (GUI) Intel 80386 Mono/[.Net] assembly, for MS Windows
- hyperscraper-5: PE32 executable (GUI) Intel 80386 Mono/[.Net] assembly, for MS Windows
- hyperscraper-6: PE32 executable (GUI) Intel 80386 Mono/[.Net] assembly, for MS Windows
SSDEEP
- ssdeep,1.1--blocksize:hash:hash
- 6144:+E2pEoECPE0ywiiv4O5Zg0L6rAfrwZbEbYTXVl:nwiie0mrAsXxl,
- 6144:o+INEmc27E46Uz1X3Jh+AA37eqtK1QJI2sQVmbdb3TpWe:yZzZ38eqzJPsQVOQe
- 3072:WjR1JpHP6Rh/Lt6SugT7uAVUeP78lgUGG3a8+CP+glE1a2l+rovA1dLfCQYPTQVO:6RGwFgT7uAr8643aMh6XvA3gPcVbHK
- 3072:tQNQeWJtxOIrY41HTTLJFtA92zvLmNph5JCWb7JX9q2ByV:tQEJaIrY4JJ092GJOWbOd
- 1536:iM/X49KS43CIZpKXlXCdHlHOKtEg9FlIG481VbnUiaThuTndyoQTM:i0X49KS46XlypzFlIG48vbtagndypM
- 3072:K3H3xhBL9LUSk4JvVP6k0I8Bt2bxPT6gG0uG:u3xjL9LUSfoz2bLH
Other IoCs
|
§ 00b5d45433391146ce98cd70a91bef08 |
|
§ 07fb3f925f8ef2c53451b37bdd070b55 |
|
§ 0a3f454f94ef0f723ac6a4ad3f5bdf01 |
|
§ 0e3cb289f65ef5faf40fa830ac9b1bf6 |
|
§ 1c00fd5e1ddd0226bd854775180fd361 |
|
§ 1db12ec1f335ee5995b29dea360514a2 |
|
§ 20f2da7b0c482ab6a78e9bd65a1a3a92 |
|
§ 253b4f5c6611a4bc9c7f5269b127c8e9 |
|
§ 276befa70cff36860cd97e3e19f10343 |
|
§ 30124b5c56cecf2045abd24011bdf06b |
|
§ 3261d45051542ab3e54fa541f132f899 |
|
§ 356439bfb9b2f49858897a22dd85df86 |
|
§ 365482f10808ddd1d26f3dc19c41c993 |
|
§ 3bb2f304a59255dddc5ef6bb0a32aec7 |
|
§ 3c01793380fbd3f101603af68e96f058 |
|
§ 3edec580845d7ab85fa893afb391fbfb |
|
§ 5e9a458dcdfc9d2ce996081ec87c30e0 |
|
§ 5ec9f484603b89f80f351bb88279ebb1 |
|
§ 60753796905458fa6a4407f48309aa25 |
|
§ 6bd505616e12e3dd7f2287f24f34609f |
|
§ 6cfa579dd1d33c2fa42d85c2472f744c |
|
§ 7df3a83dfcce130c01aabede3cfe8140 |
|
§ 7e1cf48d84e503499c9718c50e7a1c52 |
|
§ 9c7ae44baf8df000bb614738370d1171 |
|
§ 9d0e761f3803889dc83c180901dc7b22 |
|
§ a43b7cc495741248f3647e647f776467 |
|
§ a9117da1cb51adbc88a52a6e3b16a6c4 |
|
§ ae797446710e375f0fc9a33432d64256 |
|
§ af5c01a7a3858bc3712ab69bc673cec4 |
|
§ bd0a6fe7a852fdd61c1da37cf99103d2 |
|
§ be207941ce8a5e212be8dde83d05d38d |
|
§ bfd21f2847c1d7aa0f409ef52ed52e05 |
|
§ c7760dc8f7baf67f80ab549af27df9e9 |
|
§ c96453247ee1ecbd4053da8bbb4cf572 |
|
§ ccaf21e122ca9d2e2397a9e28eb4cc87 |
|
§ d6ea39e1d4aaa8c977a835e72d0975e3 |
|
§ d6fa439f0278babb1edff32d8dc31c59 |
|
§ da1f6a5f2a5564c2131b4a311c55f487 |
|
§ e7dd9b8fe7ae14faad304d139f71b629 |
|
§ e93992f26f224ea53d9bdd9564e8e1c0 |
|
§ edd4011696ddd349575278aed7031a47 |
|
§ f5763b8b796b1c5d04febcc65f853967 |
|
§ f7f9806af42adb80d100e55f35cfa86c |
|
§ f9255e0d492eb20df1e78ccc970b121a |
|
§ fac158623b0e3ed3bea6e24b1795cb95 |
|
§ 07a36f5080c69ee38554d89ee112168a25ae4ab7 |
|
§ 09c84dfaa0cc98df0e6be7da5822ccb8e40ed7ba |
|
§ 09f7e481298386e5ff6fe6bcd89c3eeecd3a3186 |
|
§ 1454f00690cf4229e2cd9125bec2eba4dc913c1b |
|
§ 1ac5d658da42413c4e087bb45193f855a140835a |
|
§ 282aa9ed59cf097836accb7e04c60677aa156d4e |
|
§ 29175a0015909186f69f827630ef3fe2c1c5302c |
|
§ 2c650247e410fdcc0ac8e3d363adf12c18f3730c |
|
§ 317628615d85dcab0a46343d3ad0709de5286f12 |
|
§ 453305beccbb0eae70771ca37a5f419ab673b471 |
|
§ 479e1e02d379ad6c3c7f496d705448fa955b50a1 |
|
§ 4b1673e0aafb32b279f26ee295fd876b6fc77654 |
|
§ 4c06518abfa767095e18074f7cca42874b18b4dc |
|
§ 4f2e8efdb11a2b34447fd3770762b94c3d33a2e3 |
|
§ 610fac8675cb9df3af83449ccdb814052a7f66c3 |
|
§ 670078a71f121f8a1d1386750991a87669837e92 |
|
§ 67bb83bbe82ffa910386216619c5ebf9eecf13e6 |
|
§ 6cacf83033fa97f4ac27eb27e4aa265afa4dc51d |
|
§ 7649c554e87f6ea21ba86bb26ea39521d5d18151 |
|
§ 7c9a685581feb04a73edeac69e2ec0db34df5d11 |
|
§ 7f6f48c9fb0e8ab8dae274430e9fd4f7e166ad7c |
|
§ 8408ff6d145302607c4c4922004c5b33ca23563e |
|
§ 8a898c8654b1aaf945ed093d29f81c69ad734588 |
|
§ 8da1630e72857008a8ce59d855f44179c25f5086 |
|
§ 904bd36b6d3eac4121a24e21631f8813fd83023a |
|
§ 9b59a840cd2e8fd6f14755c78e5b9f35fe9456c5 |
|
§ a064008b89e572851bf4ff12ab8142cfd436503b |
|
§ a2f17906ca39e7f41a8adeea4be5ffb7d1465c4a |
|
§ b030729cbcbc045528fb13df8c57f1d2a385e176 |
|
§ b5cf1dcd8f4bff9d618924f58cca26ccfb740c59 |
|
§ ba2ea7dd2fa220862e397d64bd842a57eb26bf14 |
|
§ c184aa43cff0140e17b3030ff5a3454d966a3c2e |
Supporting Documentation
New Iranian APT data extraction tool (blog.google)
Charming Kitten - AlienVault - Open Threat Exchange
Iranian Hackers Target Nuclear Experts, US Officials (darkreading.com)
Remain Vigilant: Log4Shell Still Being Exploited (avertium.com)
Iranian cyberespionage group uses Hyperscrape to extract emails (techrepublic.com)
Iranian state-sponsored group APT35 linked to Memento ransomware - The Record by Recorded Future
Experts warn of a spike in APT35 activity and a link to Memento opSecurity Affairs
APT35 Executes PowerShell-Based Malware in Log4j Flaw Attacks | Decipher (duo.com)
New steps to protect customers from hacking - Microsoft On the Issues
Microsoft Got 99 Domains Used to Phish Someone | Decipher (duo.com)
PowerLess Trojan: Iranian APT Phosphorus Adds New PowerShell Backdoor for Espionage (cybereason.com)
Iranian cyberespionage group uses Hyperscrape to extract emails (techrepublic.com)
https://blog.google/threat-analysis-group/new-iranian-apt-data-extraction-tool/
https://www.mei.edu/publications/iranian-apts-overview
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.