An In-Depth Look at Ransomware Gang, LockBit 3.0
Executive Summary of lockbit 3.0
When it comes to ransomware, the infosec community has seen a boom within the past decade. Although ransomware activity has slowed within the past several months, gangs like LockBit are still slowly evolving. Cyber security experts believe that ransomware in 2022 includes trends that go far beyond the number of attacks.
Double extortion and data extortion are taking center stage as ransomware gangs use those methods to attack critical infrastructure across the globe. Many organizations are not prepared for these kinds of attacks, leaving them to question their security postures after their cyber environments are infiltrated.
Our technology partner, Sophos, published a State of Ransomware report for 2022 where they surveyed 5,600 IT professionals regarding ransomware. They discovered that 66% of the organizations surveyed were attacked by ransomware in 2021 – a 37% increase from 2020. Additionally, ransomware payments are higher partly due to ransomware gangs attacking larger corporations and enterprises.
Ransomware gangs like LockBit 3.0 come to mind when it comes to companies being forced to pay ransoms and evolving attacks. This is the gang’s second rebrand and this time; they’ve updated the way they attack organizations. Let’s take a look at LockBit 3.0’s new tactics and techniques, as well as their new bug bounty program.

lockbit's evolution
LockBit
Emerging in September 2019, LockBit functions as ransomware-as-a-service (RaaS). RaaS means that cyber criminals place a deposit down in exchange for the use of custom “for-hire” attacks. Prior to the name LockBit, the ransomware gang was known as the ABCD virus – a reference to the file extension name used when encrypting a victim’s files.
LockBit originally targeted organizations within the U.S., the UK, Germany, China, India, France, the Ukraine, and Indonesia. The gang began their attacks by researching targets with valuable data because they knew those targets would pay them a hefty ransom when faced with losing access to their data. During their initial emergence, LockBit avoided attacking systems local to Russia or countries within the Commonwealth of Independent States, likely to avoid being prosecuted in those areas.
LockBit shares behaviors with MegaCortex and LockerGoga and is considered to be a part of those malware families. These malware families are self-spreading, targeted, and use similar tools to spread (i.e., Windows PowerShell and Server Message Block). However, what makes LockBit unique from other ransomware is its ability to self-propagate - spreading on its own and directed by pre-designed automated processes.
LockBit’s earlier attacks include Accenture, one of the world’s largest tech consultancy firms. The group attacked Accenture in August 2021 and stole 6 terabytes of data from the company, while demanding $50 million in ransom.
In Accenture’s case, researchers from Cyble believe an insider helped the ransomware gang gain access to the firm’s network. It was reported that companies with annual revenues between $1 billion and $9.9 billion account for 54% of all ransomware or extortion victims. Accenture’s revenue for 2020 was $44.33 billion. Fortunately, the data stolen didn’t contain customer information, however, other organizations were not as fortunate.
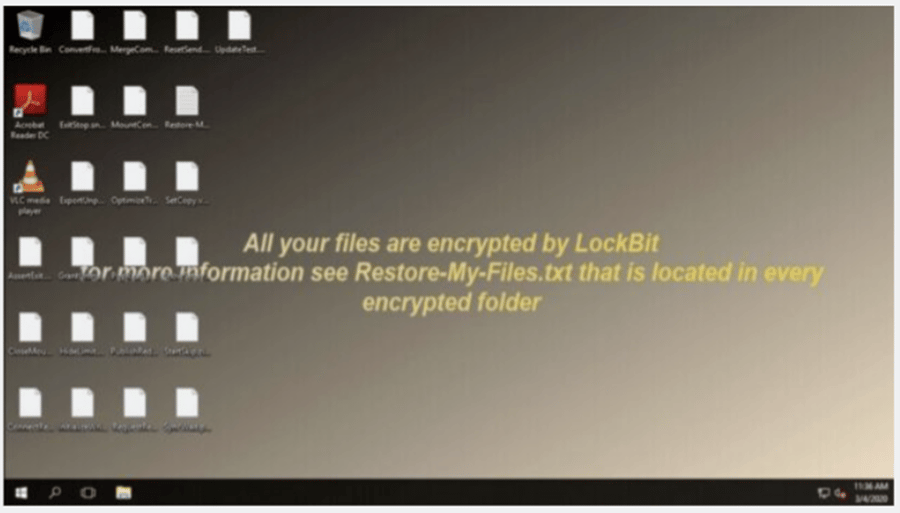
In May 2020, LockBit was able to obtain access to an administrative account at a large unnamed organization. The account had a weak password in addition to lack of multifactor authentication protection. As a result, LockBit was able to obtain all system rights before using a dual method to map out and infect their victim’s network. After executing a PowerShell script, the ransomware spread into their victim’s machines. In this case, the malicious file the PowerShell script downloaded was disguised as a PNG image. After locking up the data, the organization’s desktop appeared as the image displayed below.
Image 1: Desktop After LockBit Attack
Source: Ars Technica
To make matters worse, the attacked organization didn’t have a recent backup and the organization’s leaders had no choice but to pay the demanded ransom. The ransom was paid via LockBit’s Tor site. According to Ars Technica, following this attack, LockBit began adding a variety of new capabilities, such as a privilege-escalation technique that could bypass the User Account Control requiring users to sign off before an application can run with administrative permissions.
LockBit 2.0
LockBit eventually evolved into LockBit 2.0 - a ransomware variant of the original LockBit ransomware gang. First appearing in Russian-language cybercrime forums in January 2021, LockBit 2.0 relied on tools such as Windows PowerShell and Server Message Block (SMB) to attack organizations – scanning networks to infect compromised devices.
LockBit 2.0 primarily used tools that are built-in to Windows systems (sometimes called Living off the Land Binaries, or LoLBins), which means it will be more difficult to detect malicious activity. LockBit 2.0 successfully deployed ransomware within the following industries: manufacturing, retail and food, construction, and professional services, with most of the attempts being against Chile, Taiwan, Italy, and the U.K.
After re-emerging as LockBit 2.0, the gang chose to not only encrypt systems, but they also adopted the double extortion model. This model involves locating and exfiltrating sensitive and confidential information before a system is encrypted – ensuring that the stolen data gives victims an incentive to pay the requested ransom. If the victims refused to pay, then the information gets published publicly or sold. LockBit 2.0 threatened to sell or release information on their dark website “LockBit 2.0”, which is hosted on the Tor network.
Additionally, the ransomware gang posted a recruitment flyer for insiders who work for enterprises they wished to target. The flyer promised the insiders that they would receive a percentage of the ransom if they gave the gang access to systems.
After LockBit’s attack on Accenture and other high-value organizations, LockBit 2.0 decided to be a bit more public facing. According to our partner, Advanced Intelligence, a LockBit 2.0 representative recently gave an interview (in Russian) where they alluded to a relationship between ransomware operators and the Russian political system (although this cannot be confirmed).
During the interview, the gang claimed to be unbeatable regarding encryption speed and data exfiltration. All it took was for the attacker to take control of a domain controller to encrypt their victim’s network in the shortest amount of time – exactly how much time was unclear. All data harvested was stored on LockBit 2.0’s data leak site.
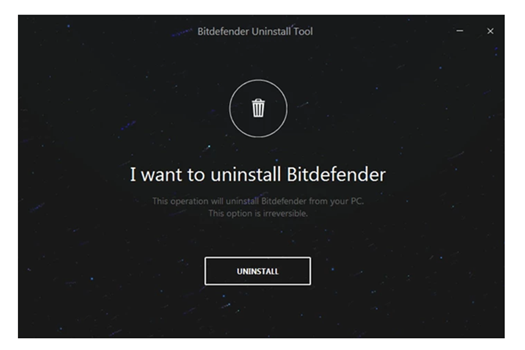
Slyly, LockBit 2.0 recommended that organizations use Bitdefender to defend against ransomware attacks. However, it was known that ransomware groups already figured out ways to bypass Bitdefender, including using the official Bitdefender Uninstall Tool to disable defenses.
Image 2: Bitdefender Tool
Source: Advanced Intel
At this time, LockBit 2.0, was heavily focused on recruiting those who worked for large enterprises. They were also completely against attacking healthcare, educational institutions, social services, and charities.
LockBit 3.0
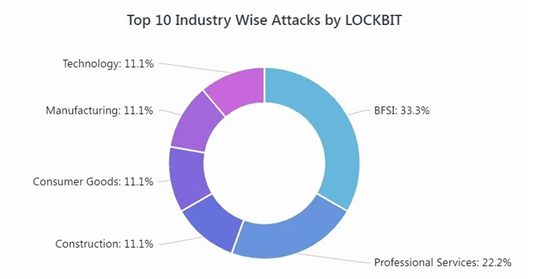
LockBit continues to target multiple sectors and organizations across the world and has recently re-branded for the second time. As of March 2022, the ransomware gang has branded itself as LockBit 3.0. LockBit 3.0, also known as LockBit Black, is active and in the wild, with 1/3rd of its victims being from the BFSI Sector.
Image 3: Industries Targeted by LockBit 3.0
Source: Cyble
new tactics + techniques
The question begs, what’s different about LockBit 3.0? According to Cyble, the latest version of the ransomware encrypts files on victim’s machines and appends the extension of encrypted files as “HLjkNskOq”. It then requires a key from the command-line argument “-pass” to execute.
Resolving its API functions dynamically, LockBit 3.0 is encrypted and decrypts the strings and code during runtime. Additionally, the ransomware creates various threads to perform numerous tasks in parallel for faster encryption. The threads are responsible for querying system information, as well as ransom note creation, getting file attributes, deleting services, etc.
To successfully encrypt files, LockBit 3.0 deletes a few services. However, before encryption, the ransomware uses the WMI query to enumerate Volume Shadow copies by using the command “select *from Win32_ShadwoCopy”. This is done before deleting the copies using “Win32_ShadowCopy.ID”, preventing attempts to restore a system after the files are encrypted.
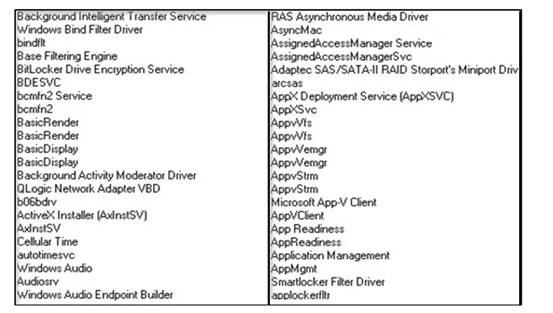
The ransomware deletes the following services before it calls the OpenSCManagerA() API to get the service control manager database access, before changing their victim’s wallpaper to reflect that they’ve been hacked.
Image 4: Services for Deletion
Source: Cyble
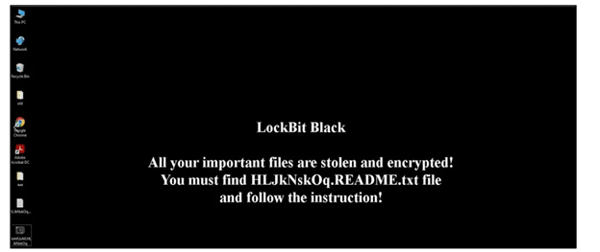
The victims then are instructed on how to pay the demanded ransom via a ransom note that is dropped onto the victim’s computer. Also, victims are threatened and told their data will be leaked on LockBit 3.0’s data leak site if the ransom isn’t paid in Bitcoin.
Image 5: Desktop Image
Source: Cyble
Additionally, LockBit 3.0 has a new extortion model – a model that allows them to buy the data that was stolen during attacks. Found in one of the JavaScript files used by the threat actor’s new leak site, a new HTML modal dialog allows people to buy stolen data from the site. People will be able to buy the data and download it through a Torrent or directly on the site. The options will more than likely be based on the size of the stolen data. Torrents will be used for larger data dumps, while direct downloads will be used for smaller data dumps.
Currently, there are no victims on the new data leak site, therefore it’s unclear If the new extortion tactic will be successful or implemented. However, time always tells the story. Like the gang’s earlier days, LockBit 3.0 claims their latest ransomware strain is the world’s fastest and most stable ransomware in existence.
lockbit's bug bounty program
Once the victim visits the Tor link mentioned in the previously mentioned ransom note, they are directed to the attacker’s leak site page. The site also contains a link that redirects users to a page where LockBit 3.0 proudly announced their bug bounty program – a program specifically for security researchers, unethical, and ethical hackers to find flaws in their ransomware project. LockBit 3.0’s goal is to make their ransomware bug free and more stable.
The page contains rules for the bug bounty program, as well as affiliate program details and ransomware functionalities. The bounties are between $1k and $1 million for finding and reporting various issues within the LockBit 3.0 structure. Anyone who shares their ideas for improving the ransomware operations and doxing the affiliate program manager, will receive a reward. Take a look at LockBit 3.0’s list of what qualifies as eligible for a bounty:
- Website bugs (i.e., MySQL injections and XSS).
- Locker bugs allowing for file decryption without the decryption.
- TOX messenger bugs.
- Tor network bugs which expose the site’s servers.
- Ideas for improving LockBit’s ransomware operations.
- Doxing the affiliate program manager.
To receive payment, LockBit 3.0 has chosen Zcash and Monero, which are privacy coins that are hard to trace. Although the bug bounty program is open to ethical hackers and bug bounty hunters, it wouldn’t be ethical to participate because then you would be aiding and assisting criminals.
ransomware gangs are business-minded
Today, ransomware gangs are operating more like a tech firm and less like cyber criminals. They rent out office space, hire graphic designers to design their websites, and they even provide customer service for victims. LockBit 3.0 has a chat feature on their Tor site where victims can communicate with the attackers and test an encrypted file’s decryption via the “Trial Decrypt” option on the site.
These features favor the Fortune 500 companies threat actors are known to attack and they market their services and products just like any other business. Threat actors also have investments in development and often times are more disciplined than legitimate tech companies. With LockBit 3.0 now offering a bug bounty program, it’s likely that other threat actors will follow suit.
From LockBit to LockBit 3.0, this ransomware gang proves that they are dynamic within the ransomware business. The group has acquired skills from other groups that have been successful in business practices (Conti) and have taken those skills a step further. By introducing the same kind of bug bounty program that tech companies like Microsoft and Google offer, they are making organized cybercrime that much more appealing – even to the infosec community.
How Avertium is Protecting Our CUSTOMERS
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium’s offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills.
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a malware attack.
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
- Avertium offers Vulnerability Management to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium uses whitelisting tools like AppLocker to audit or block command-line interpreters.
- Avertium offers user awareness training through KnowBe4. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
Avertium’s Recommendations
- Require multifactor authentication to protect employees’ accounts from being used by attackers to obtain account credentials and use them to escalate privileges and move laterally within the network.
- Perform daily backups and keep them offline to avoid losing data.
- Disrupt network movements/investigation by way of creating separated segments of network, clear access hierarchy, and additional security for active directory, domain admin, and local domains – thus complicating LockBit 3.0’s operations.
- Relying on outdated tools and point solutions will compromise your network or system. Better technology exists to detect complex attacks like LockBit 3.0 ransomware.
- Use anti-ransomware technology as a prevention method. Deploy prevention that works like next-generation antivirus and explicit anti-ransomware technology.
- Reduce the target by including these technical practices: close vulnerabilities, augment security hygiene, create and enforce strong general policies, and sustain backup and recovery practices.
- It’s likely that LockBit 3.0 monitors the latest CVEs. Monitor exposed endpoints and application of CVE-addressing patches.
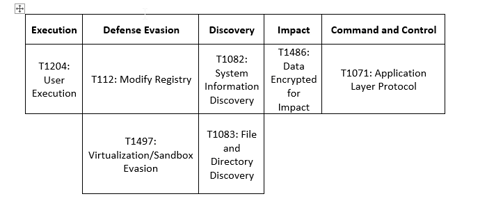
MITRE Map
Indicators of Compromise (IoCs)
- 80e8defa5377018b093b5b90de0f2957f7062144c83a09a56bba1fe4eda932ce
- f2a72bee623659d3ba16b365024020868246d901
- 8745539b71cf201bb502437f891d799
Supporting Documentation
LockBit ransomware — what is it and how to stay safe (kaspersky.com)
LockBit, the new ransomware for hire: A sad and cautionary tale | Ars Technica
Vulners - Accenture Confirms LockBit Ransomware Attack
Ransomware in 2022: Evolving threats, slow progress (techtarget.com)
Cyble — Lockbit 3.0 - Ransomware group launches new version
LockBit 3.0 introduces the first ransomware bug bounty program (bleepingcomputer.com)
LockBit 3.0 Ransomware Launches ‘Bug Bounty Program’ (latesthackingnews.com)
Lockbit 2.0 Ransomware: An In-Depth Look At Lockfile & LockBit (avertium.com)
Lockbit 3.0 Ransomware Group Target Multiple Sectors (cybersecuritynews.com)
https://latesthackingnews.com/2022/06/29/lockbit-3-0-ransomware-launches-bug-bounty-program/
LockBit 3.0: "Making the ransomware great again" - Cluster25
Accenture responds to LockBit ransomware attack (techtarget.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: LockBit 2.0 Ransomware - An In-Depth Look at LockFile and LockBit