An In-Depth Look at Ransomware Gang, Sabbath
Executive Summary of Sabbath ransomware
Just before 2021 ended, cyber security professionals stated that although organizations faced their fair share of ransomware attacks, those attacks would become more targeted and would continue well into 2022. They further predicted that ransomware operators would begin to use more sophisticated methods of extortion that would resemble nation-state advanced persistent threat attacks (APT), skipping data encryption and going straight to data exfiltration and extortion.
In December 2021, ransomware gang Sabbath left their mark when they publicly shamed a U.S. school on a dark web site because the school refused to pay their demanded ransom. The gang has flown under the radar for over a year for various reasons, but they recently made headlines because of their unique attack method. Instead of encrypting data and hoping for a big pay day, Sabbath simply steals data and extorts – a technique that is quite aggressive, yet lucrative.
As organizations attempt to stay two steps ahead of threats, cyber-criminal gangs, like Sabbath, are changing their tool kits and attack techniques to reflect those attempts. Sabbath has made it a point to target critical infrastructure with their attacks with no clear signs of slowing down. Let’s take a look at Sabbath and why they’ve gone generally unnoticed for well over a year.
who is sabbath?
ERUPTION - JULY 2020
In order to understand who Sabbath is, we will need to breakdown how many name changes the group has undergone. Sabbath is a mid-sized ransomware gang that targets critical infrastructure like education and healthcare. They were originally known as UC2190, and first appeared in July 2020 under the branding name, Eruption. During that time, cyber security analysts at Mandiant observed Eruption deploying ROLLCOAST ransomware, but they did not see samples of ROLLCOAST submitted to VirusTotal. The names of the businesses Eruption targeted were never disclosed, nor were the ransom payments.
ARCANE - JUNE 2021
Eruption appeared to fall off the grid and all was quiet until June 2021. During that month, Eruption came back under a different name – Arcane. It was during this time that analysts observed the group targeting the education, health, and natural resources sectors in the U.S. and Canada. This was also the time that the group launched their public shaming website on the dark web in an attempt to further extort victims. Researchers observed the group extorting three victims via their public shaming website in June 2021 – their names were not disclosed.
Arcane has been in operation since 2020 and has victimized 12 organizations in North America, Seven in the United States, and at least two in Canada since that time. According to Tyler McLellan, Mandiant’s principal analyst, Sabbath aka UNC2190 blurs the line between operator and affiliate and operates more along the lines of a temporary group.
“The operator appears to control how and where the ransomware is deployed, and the affiliate is providing the initial access and in exchange receives a cut of any ransom payment.” said McLellan.
Again, during this time, there were no specific reports regarding who the group attacked and how much the group was paid in ransom money. The group went dark for a while, but it wasn’t long before they re-emerged.
SABBATH - SEPTEMBER 2021
At this point, Arcane was still not on the public’s radar, but they were certainly on the radar of cyber security professionals. In September 2021, Mandiant discovered the threat actors posting on the hacker forum, exploit[.in], seeking partners for their new affiliate ransomware program, but this time they were operating under the name Sabbath/54BB47h. The posts were written in Russian. Arcane was actively seeking people who had access to commercial networks. Sabbath offered to pay a percentage of the ransom received to people who could exfiltrate stolen data, delete backups, and carry out certain portions of their ransomware operations.
Fortunately, Mandiant dismantled that operation and started connecting the dots between all three groups. Between September and October of 2021, Mandiant discovered a public shaming website called “Sabbath” that was publicly shaming a Texas based school because the school refused the pay the ransom after Sabbath deployed ransomware into the school’s network and systems. Sabbath even went as far as emailing students, teachers, and parents directly to apply further pressure on the school. Mandiant noticed that the group’s new public shaming website looked almost identical to the site that Arcane published in June 2021. Both sites had the same text, content, and grammatical errors – with only minor changes to logo and color scheme.
Image 1: Sabbath Public Shaming Site
Source: Mandiant.com
Image 2: Arcane's Public Shaming Site
Source: Mandiant.com
Sabbath also targeted a wine manufacturer in Belgium; however, the amount of the ransom and ransom payment is unknown. Mandiant has also seen Sabbath’s ransomware in India, Sweden, Germany, Mexico, and Japan – implying that Sabbath’s activity may be global. Sabbath has utilized public data leaks to extort their victims to pay ransom demands.
TACTICS AND TECHNIQUES
As we mentioned earlier, Sabbath was observed (by Mandiant) deploying ROLLCOAST ransomware in July 2020. Mandiant also noticed that the ransomware is a Dynamic Linked Library (DLL) with no named exports. ROLLCOAST also encrypts files on logical drives attached to a system – with only one ordinal export 0x01 to avoid detection. According to Mandiant, Sabbath could have designed the sample this way to avoid detection and be invoked within memory, through Cobalt Strike BEACON provided to affiliates.
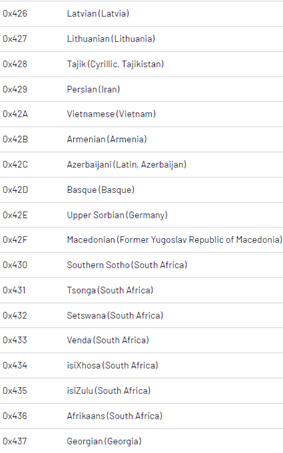
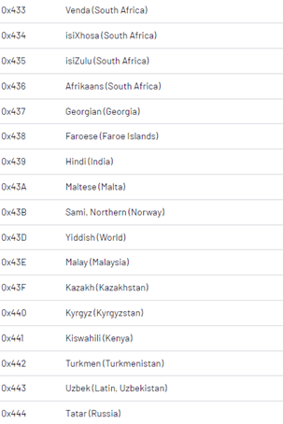
If a system language matches any of the language codes found below, ROLLCOAST will exit the system. Their malware begins by checking the system first to detect non-supported language code. Other ransomware families have adopted this style to avoid encrypting systems that could attract the attention of law enforcement in countries where the ransomware operator and affiliates are more likely to reside.
Image 3: Language Exclusions
Source: Mandiant.com
The way analysts concluded that the three groups were one in same was through Mandiant finding similarities in their techniques. By analyzing Sabbath’s infrastructure, Mandiant was able to see the link between Eruption, Arcane and Sabbath.
Cobalt Strike BEACON
Unlike other ransomware affiliate programs, Sabbath provides their affiliates with pre-configured Cobalt Strike BEACON backdoor payloads. Sabbath has been operating for over a year and has only made minor changes to their strategies and tool kit. They recently introduced a commercial packer and rebranded their service offering. This is a good example of how well-known tools like Cobalt Strike BEACON can lead to lucrative and impactful attacks even if leveraged by smaller and unknown groups.
The use of Cobalt Strike BEACON to deploy ransomware is not unusual for ransomware gangs. What is unusual is a ransom affiliate program operator providing Cobalt Strike BEACON. This presents a challenge for attribution efforts while also offers additional avenues for detection. After bulk data is stolen as leverage, Sabbath then attempts to destroy backups.
NAME CHANGES
The constant name changes may be a technique Sabbath uses to continue their ransomware campaigns and to put up a front to obfuscate who is carrying out their operations. It minimizes attention to their campaigns and gives them leverage over generating more revenue.
These kinds of ransomware attacks will appear frequently over the course of 2022. Ransomware operators are focusing on servers, as well as cloud providers – making sure to weaponize the data they exfiltrate. Trying to stop the attacks from happening (or mitigate) can be a challenge for organizations that won’t invest in securing their servers as much as they invest in securing their end points.
Sabbath has been able to keep their operations going while changing very few things about the way they attack. The fact that they don’t have to change much says more about the level of cyber security within organizations than it does about Sabbath. It’s important for organizations to go back to security basics and continue to be vigilant with protecting servers.
how avertium is protecting our customers
- Avertium offers vulnerability management as a service (VMaaS) to remove any unnecessary applications and implementing XDR tools to prevent ransomware and phishing attacks. Include an EDR, MDR or XDR strategy to stop ransomware before it spreads.
- You should also include a Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Avertium offers DFIR retainers so your organization can respond quickly in the event of a breach.
- Reach out to your Service Delivery Manager or Account Executive if you need assistance applying any of the above recommendations.
avertium's recommendations
Prioritizing network visibility is important. Avertium recommends:
- Prevent lateral movement by implementing network hierarchy protocols with network segregation and decentralization.
- Use whitelisting tools to audit or block command-line interpreters (AppLocker).
- Rclone and other data exfiltration command-line interface activities can be captured through correct logging of process execution with command-line arguments.
- Have security protocols in place for Veeam to avoid account takeover. Enabled backups decrease Sabbath’s ransom demands and can lead to data recovery without you having to pay them.
- Externally exposed RDPs are dangerous and can expose your organization to a DoS attack. Set up a VPN and only allow remote RDP access over the VPN as an extra layer of security.
- Relying on outdated tools and point solutions will compromise your network or system. Better technology exists to detect complex attacks like Sabbath ransomware.
- It’s also recommended by Avertium and the FBI that your business require multi-factor authentication to remotely access networks. Implementing network segmentation and filtering network traffic to stop phishing emails from reaching victims is also helpful.
- If your organization is impacted by a ransomware attack, the FBI and CISA recommend the following:
- Isolate the infected system.
- Turn off other computers and devices.
- Secure your backups.
MITRE TTPs:
- [T1016] System Network Configuration
- [T1486] Data Encrypted for Impact
- [T1055] Process Injection
- [T1136] Create Account
- [T1059] PowerShell
- [T1027] Obfuscated Files for Information
- [T1057] Process Discovery
- [T1518] Software Discovery
Indicators of Compromise (IoCs):
BEACON
- probes[.space]
- probes[.site]
- datatransferdc[.com]
- farhadl[.com]
- markettc[.biz]
- [space]
- tinysidney[.com]
- helpgoldr[.com]
- franker[.com]
- greentuks[.com]
- 79.55.129:443
- 146.166.24:443
- 147.230.221:2002
- probes[.website]
- cofeeloveers[.com]
- doratir[.com]
- gordonzon[.com]
- probes[.site]
- probes[.website]
- 79.55.129:80
- 141.84.182:443
- 147.230.137:3001
- ef3363dfe2515b826584ab53c4bb7812
- 3357fd8d5a253b7d84101e902480bf2dd2f7773c
- da92878c314307a5e5c9df687ec19a402d93126b3818e5fb6b7241ab375d1e12
- f1b2f83aa08b8f6f01cac6bf686786d2
- 366390c3cd829d1172f02e564d35cfb2c667e9fc
- 0fb410b9a4d32a473b2ee28d4dc5e19a64524e107b980fc1ce8de2ad0dcc3302
- 6bd1a3849bb9d5f9ac5b4f4049081334
- a0928456f12e909ec03eadce449bc80f120bfbf8
- 298662f3fed24d757634a022c16f4124919b653f8bf7717e4f7a5b7d741729c0
- e94089ff2e0b93ce38076cca370cf8cc
- dc3c26f305648a12484c17d6166397a002a93707
- afd61168c1fae6841faa3860dca0e5839f1b7a3169184a1c04de5a9b88adfe5d
- ac76d6c5c223688edf2d53745036d594
- 5972b873977912adf06203b61685f32a6ccb9eee
- a053408747e9b32721d25c00351c4ce9286208e8714780416f18cbe2536672a9
- 64da229042dffddf5bb30a4a1d8b1f1e
- 3dc46fa5ebc87e8adcb6eaa0b407574506c957bb
- b2ffd7d83e004308a97355a18529fe3528dcbbd7901fb28aaad9d46194469947
- 1789f6177300d503289c482910f223d9
- 5c3f297bab8a5e93aac91a9df920c54bee2c836d
- e302a958856208adeab4ab3cd6d2991e644798fabd57bb187a0aede314a4baa0
- dbfa3eb08d858d5bbb0cc72f497192b0
- 182e9d1026c63503aadb78bbc3788b7ba2cdb69a
- 8ddb23c90cb4133b4624127a1db75335a51e90d557c01e996ce33fe23f638e71
- 79c6c4329a36df20a6abf67b01352b20
- fc7b3d8beab604cf47203f4f9a2aa8594bd54fb7
- 1bbb11e526141af7bafb5d4db3671b1a01bb277fda047920995c1f2a4cb6654c
- 6ae156c0a1900b6ff2c903a950d50dce
- 7b178842e1b53f163f869d9da3da32032fe29abb
- 1cd586852d2c06b0f7209c7a4da8f3d0de794f92e97b7c4405ad71c859dc2f50
- b0333d840e136326a2bd612fcf73fff0
- 8467b4f784156f2e508a3fed0ef0b6ddcf330c0d
- 79b47780382f54ca039ad248d8241e42a7ed6b1e4b75af836890e4e46c0f8737
- 7669f00b467e2990be182584b341c0e
- 2eaa91f38461d708ee6e94ec2f738f3cdfb229b7
- f4ac75a045acee2cadbe9fa0e02bfd4ab4124018e00193930966b8141351115f
- 60aec56cb2262ae46fc39c45fc814711
- bb22515f2e8e4d5660dc8565869d966502a0123e
- 3edb237aeee6efad6f21f0f2c2037ec0f9f817197432de9759b0a772a4c8f311
- f7e7201325892dcc287c60a0748edb16
- 35f02a778ea7504331ddd025f0d927e0773ffd31
- a4891cc85802833d9a89e2522a42a7e3c8dc6de1d2bbed5945497ee4006c8ddb
- c4a369880e3e5c3dc42ebf8cdacc9d6c
- 037889e6d714c7ff6341bdb8a8bebbddc21fc36e
- 756ed760cbf4b35054c78a75009f748f0f6cd5eb2cbd44bb3a2d964da3c419cf
- 98f2b23eb265d73a05b2cce17d53eba4
- 41cc9afc79aaee60f6436192c6582907e41d89f7
- 87cdcbc55aed4267f47a913b17f4bc697634bf633659c639f87a4dbf00f853c1
- 38667bc3ad2dcef35a5f343a5073e3f2
- 22cf10ec5047a86a49c1819c4943290321a29918
- a8741f6f400c7fedfbdc7a298ab4a636be42d379eb4ecc3cccd81eadca09f8d0
- aa2a14e1819f4b1cc685801e07186b0
- 101930bbec76ee4a147117cdfcb56aa2208a579d
- 5a6b7569c2b8e91f5bd8a67322af384cfad5ddaf3ea9de271093a0879b88c438
- 61bbe1c1b2aa40c0d8aa7e00c2c4f7b6
- 6eff4b7b5ccf92eb0f134591237fe1db7c71826a
- f883f7d7c068b6f1eb62804591d748c28c584fbfb769628d9567c22aa00f26f6
- 0b6757090d9ebc8d497e71b177acf256
- 25b175a71906e354a24003803574c4420f02a82f
- e25f2284fc6e80011587bf95829d8ff30ecae06a2d2bbe494d8af3bd05f9e43f
terms
Malware - any intrusive, unwanted software that is designed to compromise, damage, or destroy your computer, device, network, or the data contained within (example: viruses, trojans, adware, etc.).
Ransomware - malicious software that infects a device and stops users from accessing data and files until a ransom is paid.
Supporting Documentation
Sabbath ransomware group rebrands, continues attacks (itbrief.com.au)
Sabbath Ransomware Targeting Healthcare, Mandiant Warns (healthitsecurity.com)
Hack 'Sabbath': Elusive new ransomware detected (techtarget.com)
Kitten.gif: Meet the Sabbath Ransomware Affiliate Program, Again | Mandiant
Ransomware Group Continually Rebrands to Slip Under Radar | Decipher (duo.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of the Client's compliance with any law, regulation, or standard.