
Case Study:
INTERNOVA TRAVEL GROUP
Discover how Avertium helps unburden Internova Travel Group's security team to have the space to start focusing on more strategic cybersecurity priorities.
In March 2023, threat actors compromised the desktop application of 3CX, a popular Voice Over Internet Protocol (VoIP) phone system software provider, in a supply chain attack. The threat actors gained access to 3CX’s build server and injected a malicious backdoor into the application’s setup package. The threat actors were then able to steal data and execute commands on infected devices.
The chaos didn’t stop there. After the initial compromise, Mandiant investigated the 3CX supply chain attack and found that the North Korean cluster UNC4736 was involved. Also, Kaspersky found that the North Korean APT, Lazarus, deployed a backdoor named Gopuram onto the devices of some 3CX customers, as a second-stage payload during the same incident. Gopuram has been known to be used by the North Korean threat actor Lazarus to target cryptocurrency companies since 2020. After much speculation, security researchers were finally able to attribute Lazarus to the 3CX attack.
What makes the breach even more interesting is at the same time, researchers were connecting the dots to a different security issue involving Lazarus and LinkedIn users. ESET researchers discovered a new campaign by Lazarus targeting Linux users. The campaign involved sending a fake job offer from HSBC to lure users into downloading malware. The malware is a Linux backdoor called SimplexTea, and it was distributed through a cloud storage account. This was the first time the group was seen using Linux malware in its operations, and it was very similar to the malware used in the 3CX supply-chain attack. Let’s look at the 3CX attack and how professional social media platforms such as LinkedIn can become gateways for security breaches.
The 3CX Phone System is used globally by more than 600,000 companies and has over 12 million daily users. The company provides its clients with software that can be accessed through a web browser, a mobile application, or a desktop program. In March 2023, it was reported that 3CX was the victim of a supply chain attack where threat actors compromised the company and used its software to distribute additional malware to some 3CX customers.
According to Mandiant, initial access to the 3CX network was obtained via a backdoor (labeled VEILEDSIGNAL) injected into the corrupted X_TRADER (owned by Trading Technologies) application, which allowed the threat actor to gain access to an employee's computer and steal their credentials. From there, the threat actors used the credentials to gain access to 3CX's network, spread laterally, and compromise Windows and macOS build systems to inject malicious code.
Volexity’s analysts were one of the first to investigate the attack, and they created a tool to identify a list of C2 servers from encrypted icons on GitHub. The tool was helpful because the threat actors didn’t embed the C2 servers directly in the intermediate states but instead used GitHub to secretly exchange information. On December 7, 2022, the initial commit was made to the GitHub page, containing an ICO file with an encrypted 3cx[.]com URL. This indicates that the threat actors might have started testing the backdoor around that time.
By April 2023, it was reported that the 3CX attack was caused by another supply chain compromise, making it a double supply chain attack. It was suspected that North Korean attackers breached the site of Trading Technologies, a stock trading automation company, and pushed Trojanized software builds. They accomplished this by using corporate login credentials on an employee’s device.
As a result, they were able to move laterally through the 3CX network and compromise their Windows and macOS build environments. Also, after the initial breach, Mandiant was retained to provide incident response to 3CX. The tech company stated that, according to earlier reports, the macOS build server was allegedly infiltrated using SIMPLESEA. However, after analysis by Mandiant Intelligence, it was determined to be the pre-existing backdoor POOLRAT rather than a new malware family.
According to ESET researchers, Lazarus had been planning the attack as early as December 2022, well before its execution. The development suggests that the threat actors had already established a foothold within the company’s network late last year. A few days before the attack was made known to the public, a suspicious Linux downloader was submitted to VirusTotal that downloaded a new Linux-based backdoor known as SimplexTea. The backdoor communicates with the same command and control (C2) server utilized by the payloads linked to the 3CX compromise.
Operation DreamJob is the name of the campaign series that Lazarus has been deploying since 2020. The campaign was named by the researchers at ClearSky and employs social engineering techniques to compromise targets, using fake job offers as bait. Operation DreamJob is a cyberespionage campaign targeting defense and aerospace companies. According to ESET, the campaign shares similarities with what is known as "Operation In(ter)ception", a series of cyber espionage attacks that have continued since September 2019. Targets include aerospace, military, and defense companies, and it uses specific malicious tools initially designed for Windows only.
In July and August 2022, ESET identified two occurrences of Operation In(ter)ception targeting macOS. One malware instance was submitted to VirusTotal from Brazil, and another attack targeted an ESET user in Argentina. Recently, a native Linux payload with an HSBC-themed PDF lure was found on VirusTotal, completing Lazarus’s ability to target all major desktop operating systems.
On March 20, 2023, someone in Georgia uploaded a ZIP archive titled “HSBC job offer.pdf.zip” to Virus Total. Based on previous Operation DreamJob campaigns, the payload was likely disseminated through spearphishing or direct messaging on LinkedIn. The archive has only one file: a Go-written native 64-bit Intel Linux binary named “HSBC job offer.pdf.” The backdoor, coded in C++, has similarities with BADCALL, a Windows-based Trojan that Lazarus has been linked to previously.
Image 1: Timeline of Events
Source: ESET
ESET reported detecting similarities between artifacts used in the Operation Dream Job campaign and those found during the 3CX supply chain attack, including the C2 domain “journalide[.]org," which was named as one of the four C2 servers exploited by malware families detected within the 3CX environment. Also, ESET’s research shows that SimplexTea likely corresponds to the SIMPLESEA macOS malware seen in the 3CX breach. SimplexTea is a part of Operation DreamJob, Lazarus’s flagship campaign, that uses fake job offers to lure victims.
As for the double supply-chain attack, Mandiant was asked by 3CX to provide incident response. The tech company stated that this was the first time they have seen a software supply chain attack result in a sequential software supply chain attack. This highlights the potential impact that such breaches can have when an attacker is able to chain intrusions. While the motive for the attack has not been shared, it is speculated that the threat actor’s goal was to deploy information-stealing malware, as Lazarus is a nation-state threat actor.
When it comes to using professional social media networks, there is a certain level of awareness that people need to have. Although professional social media networks are for connection and communication, there are malicious actors who gather information from those networks and use it to their benefit. Any detail you post on your social media accounts is a possible source of data that threat actors can use to build a comprehensive profile of you.
If you are the target of an attack, it is possible that a threat actor could use the publicly available information across your social accounts to their advantage. Therefore, it is important to be aware that even small pieces of data could be dangerous, including your job history, career path, work industry, education history, and connections to other people. In Lazarus’s case, the aforementioned was all they needed to lure their targets on LinkedIn.
After an attacker collects the data they need, it’s only a matter of time before they try to impersonate a brand, write malware, and specifically target a business or gain access to account credentials. Social media is now a vital business tool, but it's also a potential security risk. Attackers are finding more creative ways to use social media to target employees and gain access to sensitive information. Organizations need to establish a clear policy and be vigilant in monitoring and enforcing it to protect themselves from attacks.
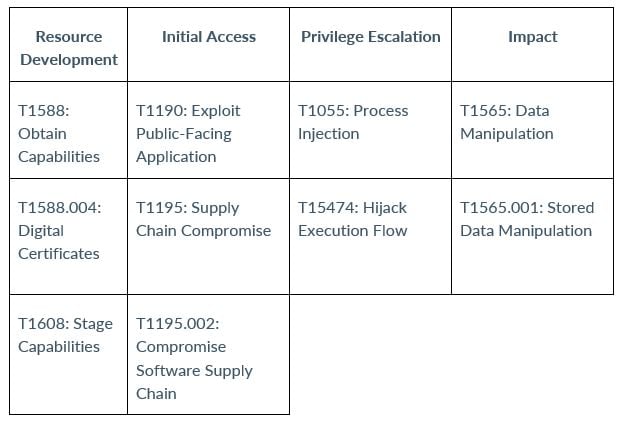
When a threat actor hacks into a software supply chain, it's hard for network defenders to fix it quickly. This is because the organizations don't always control the entire software supply chain, so they can't force everyone to fix the problem right away.
It’s better to follow software-supply chain best practices before an attack happens, rather than trying to fix it later. By following these best practices, organizations can make it harder for threat actors to infiltrate their network and be better prepared to respond to attacks. CISA recommends the following:
[1] Defending Against Software Supply Chain Attacks (cisa.gov)
It’s important to get ahead of the curve by being proactive with protecting yourself and your organization, instead of waiting to put out a massive fire. Avertium offers the following services to keep you and your organization safe:
SHA-1
IP Address
FileHash-SHA256
Related Resource:
Mandiant Security Update – Initial Intrusion Vector | 3CX
What is a Social Media Threat? Attacks & Security | Proofpoint US
Lazarus X_TRADER Hack Impacts Critical Infrastructure Beyond 3CX Breach (thehackernews.com)
Linux malware strengthens links between Lazarus and the 3CX supply‑chain attack | WeLiveSecurity
3CX Security Update 11 April 2023 | Mandiant Initial Results
3CX confirms North Korean hackers behind supply chain attack (bleepingcomputer.com)
3CX Supply Chain Attack: Big Questions Remain | CRN
3CX Supply Chain Compromise Leads to ICONIC Incident | Volexity
5 Ways Social Media Impacts Cybersecurity | eWEEK
Lazarus Group Adds Linux Malware to Arsenal in Operation Dream Job (thehackernews.com)
Mandiant Security Update – Initial Intrusion Vector | 3CX
Hackers compromise 3CX desktop app in a supply chain attack (bleepingcomputer.com)
3CX hack caused by trading software supply chain attack (bleepingcomputer.com)
Defending Against Software Supply Chain Attacks (cisa.gov)
Dream-Job-Campaign.pdf (clearskysec.com)
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.