MITM Attacks - EvilProxy and Evilginx
Executive Summary
Towards the end of 2022, Avertium published a Threat Intelligence Report featuring the year’s most significant cyber attacks and what to expect for 2023. One of the attack vectors to watch was business email compromise (BEC) attacks. There are a number of methods by which a threat actor can gain access to a victim’s email address, and the standard recommendation is to enable Multifactor Authentication (MFA) as a method of protecting against exploitation of stolen passwords.
However, Man in the Middle Attacks (MITM) can be used to steal session cookies and bypass MFA. Avertium’s Cyber Threat Intelligence Team predicted that there would be an uptick in these kinds of attacks for 2023, as the return on investment increases relative to ransomware.
At the end of December 2022, the Federal Bureau of Investigation (FBI) issued a cyber alert, warning organizations that cyber criminals are targeting the food and agriculture sectors via BEC attacks. In 2021, there were losses of almost $2.4 billion, based on 19,954 recorded complaints linked to BEC attacks targeting organizations and individuals. Let’s take a look at MITM attacks, the threat actors who use them, and what organizations can do to prevent becoming a victim.

Man-in-the-middle (MITM) attacks
Before we dig into the types of MITM attacks, let’s break down the definition of a MITM attack. A MITM attack occurs when a threat actor is able to intercept or interrupt existing communication or data transfer. In the early days of the internet, data interception was relatively easy as most protocols were not encrypted. Once encrypted communications became more common it became necessary to trick the victim into routing their communications through a host controlled by the threat actor.
Recently we have seen tools such as Evilginx and EvilProxy that act as a proxy, this requires tricking the victim into thinking they are logging into a legitimate site and then forwarding the credentials to the real site. This will also bypass most MFA mechanisms as the proxy either presents the verification code request or forwards verification request directly to the victim. Once access is gained the threat actor will have collected the victims password, but more importantly session cookies which allow them to authenticate directly with the server. The link to the proxy is generally delivered via a phishing email that appears to contain a legitimate link to the victim’s mailbox.
Business Email Compromise (BEC)
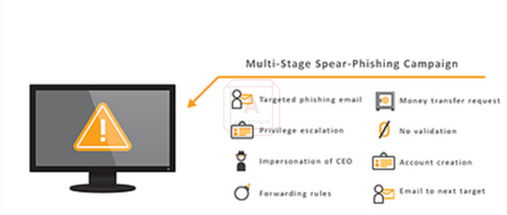
The FBI calls business email compromise (BEC) the “Billion Dollar Scam”. We have seen a significant increase in BEC cases over the past year and have identified MITM proxy attacks being used to gain access to victims Microsoft 365 accounts. In addition to spear-phishing emails, attackers will also spoof a website or use malware to infiltrate networks to gain access to email chains.
In BEC cases the threat actor will target users who are likely to have access to financial transactions, using sites such as LinkedIn to identify potential targets. Once access is gained to a victim’s mailbox, they will identify email threads relating to the transfer of funds, before injecting themselves into the thread - instructing one party to either change bank payment details or sending fake invoices with updated payment details. In some cases, we have seen emails sent internally appearing to come from the CFO or CEO instructing that ‘special’ payments be made. Some of the cases we have worked, have resulted in millions of dollars of losses from a single victim.
Image 1: Stages of Spear-Phishing Campaigns
evilproxy and evilginx
EVILPROXY
EvilProxy (also known as Moloch) is a phishing-as-a-service (PhaaS) toolkit available on dark web forums. The tool helps threat actors bypass MFA protections employed against online services.
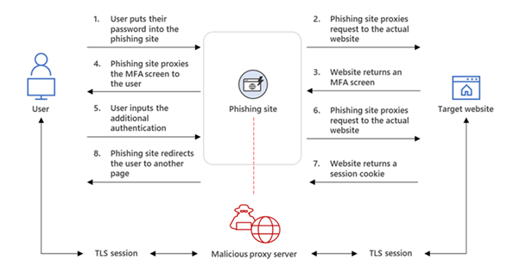
Because EvilProxy is an inexpensive and easy service to use, many threat actors have taken advantage of it. EvilProxy is used to create targeted phishing emails that include links to customized phishing websites. To the average person, the websites appear to be legitimate sign-in pages for services like Microsoft 365 and Google Workspace. Once the victim logs in, the phishing site redirects or “proxies” traffic from the victim to the legitimate login site. From there, the threat actor intercepts the victim’s credentials, valid session cookies, and sits “in the middle” of the MFA process.
When a threat actor has access to valid session cookies, it allows them to continually log in to services (i.e., Microsoft Exchange Online) without the need to reauthenticate.
Image 2: EvilProxy Attack Method
Source: Radius.com
Although this kind of proxy attack framework is not new, EvilProxy is easier to set up than earlier frameworks. EvilProxy also provides threat actors with in-depth training and instructional videos, and user-friendly GUI. EvilProxy also offers a wider library of fake phishing websites for platforms such as Facebook, GoDaddy, GitHub, Dropbox, Yahoo, Yandex, Apple iCloud, and Google. As more organizations adopt MFA, user-friendly reverse proxy tools like EvilProxy will become in demand.
EVILGINX
Evilginx is another MITM framework used for phishing credentials and session cookies. Like EvilProxy, the framework can be used to bypass 2FA. According to Cloud consultant and security researcher, Jan Bakker, Evilginx uses phishlets to mirror a website and trick users into entering credentials for platforms such as Netflix, Gmail, and Office 365. Phishlets are open-source and are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. Due to phishlets being open source, there are many that are available and ready to use.
Evilginx remotely captures credentials and session cookies from any web service. The framework uses a Nginx HTTP server to proxy a legitimate login page, capturing credentials and session cookies quickly. Remotely, Evilginx uses custom domains and valid SSL certificates.
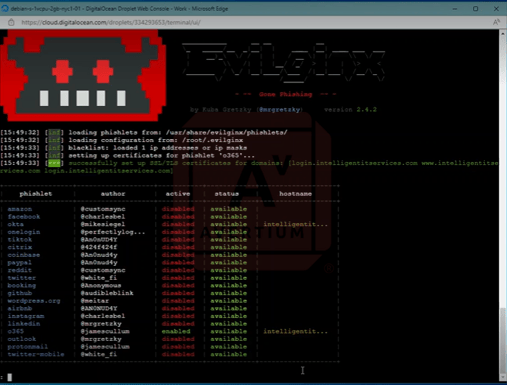
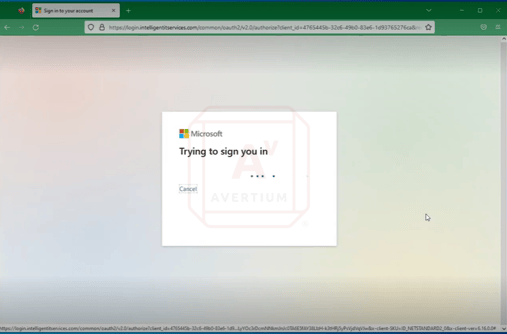
Avertium’s Threat Intelligence Team completed a demonstration of Evilginx vs. M365 with MFA. Watch this video of the full demonstration or take a look at the steps below:
Image 3: Evilginx vs. M365 with MFA
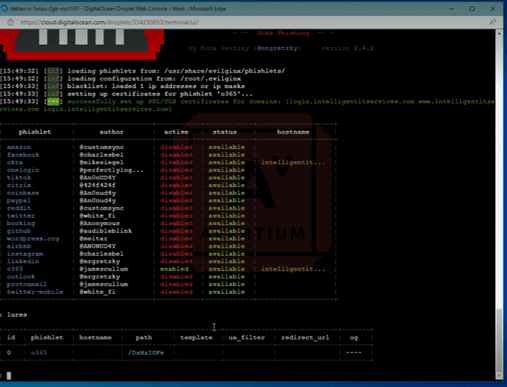
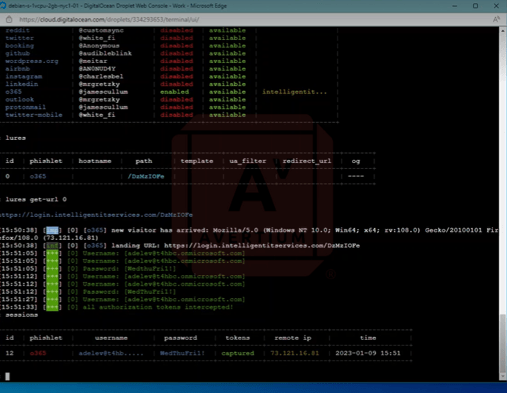
The image above shows a Debian digital ocean droplet with Evilginx 242 configured and running. As you can see, there is one phishlet O365 that is enabled.
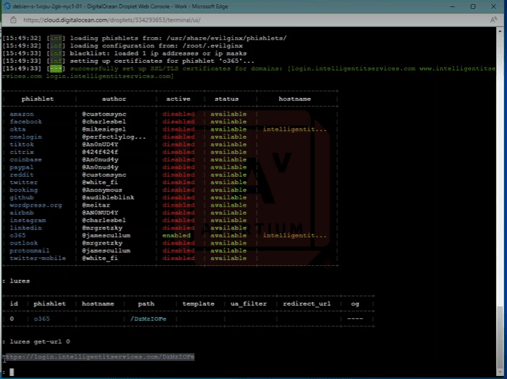
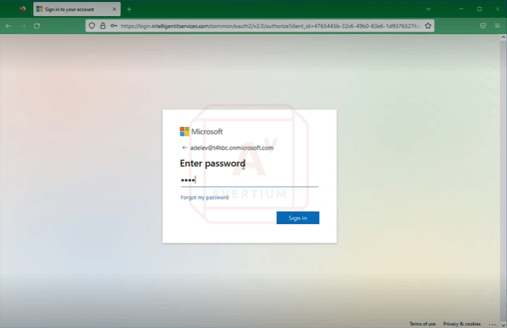
Image 4: Microsoft 365 Lure
Next, we configured a single Microsoft 365 lure and input the URL we want to deliver to the target. The victim authenticates once they click on the URL.
Image 5: Victim's System
Above, you can see the victim's system navigate to the URL. Evilginx then proxies disconnection before the victim logs into the web portal.
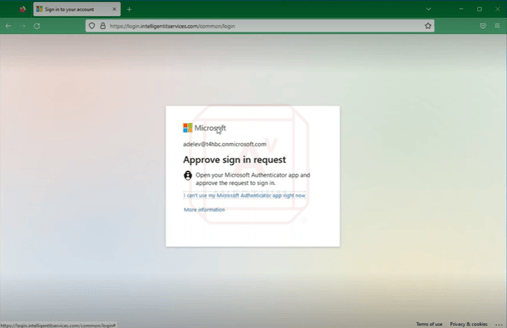
Image 6: Victim Logging into Web Portal
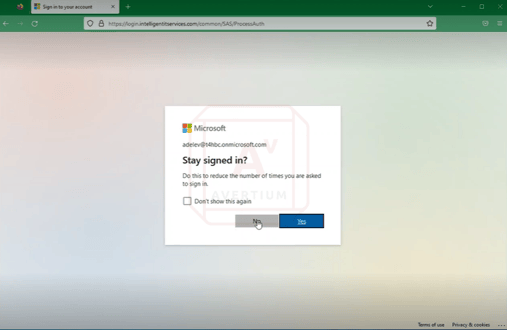
Below, you can see the MFA prompt appear to the victim who then clicks approve before authentication is complete. Next, there is a redirect to the actual Microsoft 365 portal.
Image 7: MFA Prompt
Image 8: The Redirect
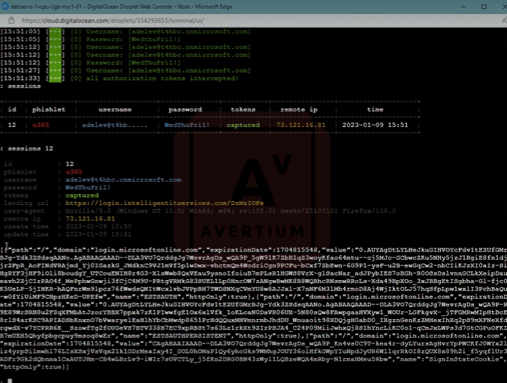
Below, we have successfully captured the victim's username, password, and session token.
Image 9: Evilginx Captures Credentials
Image 10: Authentication Token
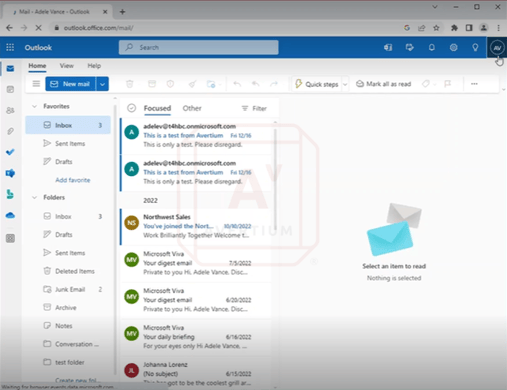
Above is the authentication token that the threat actor copies before navigating to Microsoft Office. Next, they pull up cookie editor and copy, paste, and import the cookie before hitting enter. We have now successfully logged into the victim's Microsoft 365 account without credentials and without MFA.
Image 11: Successfully Logged into Victim's Microsoft 365 Account
defense
There is no silver bullet for organizations to protect themselves against MITM attacks. It’s up to organizations to compliment traditional MFA with other security measures. However, there are some ways organizations can defend themselves against MITM attacks.
EvilProxy & Evilginx
- Force browser connections through a proxy service that protects users from accessing known bad and malicious websites.
- Use an email filtering service that detects malicious emails.
- Using password-less authentication methods will help organizations defend themselves against EvilProxy/Evilginx attacks. Please note that your organization must have end-user devices to have biometric support (facial, iris, and fingerprint recognition).
- Use hardware token MFA methods (FIDO2 security keys).
- Organizations should block legacy authentication and implement Zero Trust principles and move towards modern authentication. This adds more security layers and could protect your from EvilProxy and Evilginx actors.
Microsoft 365
- Organizations should implement conditional access through their Microsoft Office License. This will limit access to specific devices, locations, etc.
- Deny access to untrusted devices by configuring Microsoft Intune compliance to deny access to untrusted devices.
- Turn on user risk/sign-in risk policy
Financial Fraud
- Implement verification process for requested changes to payment processes. For example, calling to verify when requests to change banking details are made.
User/BEC/Phishing Awareness
- Train employees on how to verify the source of your emails.
- Train employees to check the grammar in received emails. A legitimate email will rarely have glaring grammatical errors.
- Train employees on how to double check domain names for errors. The FBI mentioned that a target noticed that the domain name in an email had an extra letter.
- Train employees on the importance of being suspicious of unexpected emails.
- Train employees on the importance of keeping all personal electronic device software current.
How Avertium is Protecting Our CUSTOMERS
It’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. Avertium can provide the following services to help keep your organization safe from MITM attacks:
- Avertium offers user awareness training through KnowBe4. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Avertium offers Zero Trust Network as a Service (ZTNaaS) for any organization that wants to control their attack surface. The zero-trust security model delivers exactly what the name promises: it is an IT security concept that specifies no access is allowed until the successful completion of authentication and authorization processes.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.
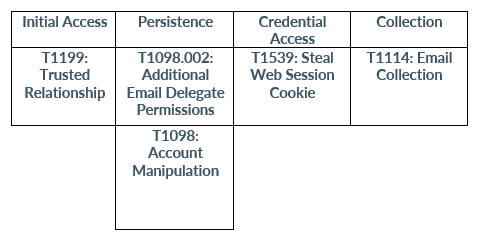
MITRE Map
Indicators of Compromise (IoCs)
EvilProxy
- The IoCs for EvilProxy change as they are detected, therefore, we have included a direct link to the IoCs that can be referenced as they change.
Evilginx
- The IoCs for Evilginx change as they are detected, therefore, we have included a direct link to the IoCs that can be referenced as they change.
Supporting Documentation
Lilac Wolverine, a Nigerian Cybercrime Syndicate, Uses Covid-19 to Lure Victims (fij.ng)
What Is a Man-in-the-Middle (MITM) Attack? Definition and Prevention - Panda Security Mediacenter
The Top 5 Cyber Threats in the Healthcare Industry (avertium.com)
California Hospital Sued Over Data Breach - Infosecurity Magazine (infosecurity-magazine.com)
Evilginx - Advanced Phishing with Two-factor Authentication Bypass (breakdev.org)
Resecurity - EvilProxy Phishing-as-a-Service with MFA Bypass Emerged in Dark Web
Resecurity - EvilProxy Phishing-as-a-Service with MFA Bypass Emerged in Dark Web
Protect against AiTM/ MFA phishing attacks using Microsoft technology (jeffreyappel.nl)
EvilProxy: What is it and Why is it Dangerous? - Radius Technologies
MFA Breaches & MFA Fatigue (avertium.com)
EvilProxy phishing campaign - AlienVault - Open Threat Exchange
GitHub - hash3liZer/phishlets: Phishlets for Evilginx2 (MITM proxy Framework)
10 tips to secure your identities in Microsoft 365 - JanBakker.tech
EvilProxy - AlienVault - Open Threat Exchange
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.