New Ransomware Strains - CACTUS and 3AM
executive summary
In January 2023, there was a significant 41% decrease in ransomware victim posting rates across all groups compared to December 2022, signaling an overall decline in ransomware activities. Despite this downturn, LockBit continued to be a dominant force in ransomware incidents, maintaining their position at the forefront of the threat landscape.
Avertium's End of the Year Recap for 2022 already predicted a diminishing return on investment for ransomware gangs, yet anticipated ransomware to persist as a major issue for organizations in 2023. The report identified five major ransomware groups—LockBit, BlackCat (ALPHV), Royal, Vice Society, and Medusa—as responsible for the most disruptive attacks.
Corvus Insurance's Q3 2023 Global Ransomware Report further emphasized the severity of the ransomware landscape, revealing a resurgence in global incidents. The number of ransomware victims in 2023 has already exceeded the combined totals of 2021 and 2022, indicating an alarming trend. The report highlighted the CL0P ransomware group's pivotal role in the elevated Q3 ransomware numbers, attributing the spike to mass exploits targeting vulnerabilities in file transfer software. Industries such as law practices, government agencies (due to LockBit), manufacturing, oil and gas, and transportation, logistics, and storage experienced notable spikes in ransomware activity.
During Q4 of 2023, two new ransomware strains, CACTUS and 3AM, have emerged. CACTUS exploits known vulnerabilities in VPN appliances for initial access, while 3AM serves as a backup for a LockBit affiliate when the primary LockBit strain is blocked on a targeted network. These developments, alongside ongoing ransomware activity this year, highlight the importance of robust security controls across industries to counter the evolving threat of ransomware attacks. Let's dive into the specifics of CACTUS and 3AM ransomware strains, along with recommendations for organizations to safeguard against them.
tir snapshot
- In May 2023, Kroll Cyber Threat Intelligence Analysts published their discoveries of a new ransomware variant referred to as CACTUS, which has been actively targeting large commercial entities since March 2023.
- To maintain persistence, CACTUS deploys various remote access methods, including legitimate tools like Splashtop, AnyDesk, and SuperOps RMM, along with malicious tools like Cobalt Strike and Chisel.
- In November 2023, cybersecurity firm Qlik reported instances of attacks exploiting vulnerabilities, specifically CVE-2023-41266, CVE-2023-41265, and CVE-2023-48365, to gain initial access.
- The threat actors involved tried to deploy CACTUS ransomware on compromised systems.
- In December 2023, Microsoft issued a warning about CACTUS ransomware, revealing that attackers are leveraging malvertising through online ads to infect victims.
- In a recent incident involving a construction company, threat actors faced difficulty in deploying LockBit ransomware on the target network, leading them to resort to a newly identified ransomware variant known as 3AM.
- Despite initial attempts to deploy LockBit, the attackers pivot to 3AM, which only achieves partial success. During the incident, it was deployed on three machines in the organization's network, but was blocked on two out of the three computers.
- The cybersecurity landscape is witnessing a transformative phase as cybercriminals, particularly ransomware affiliates, adopt more sophisticated strategies.
- Organizations must remain vigilant, using multifaceted defense strategies to navigate these cyber risks.
CACTUS RANSOMWARE
In May 2023, Kroll Cyber Threat Intelligence analysts published their discoveries of a new ransomware variant referred to as CACTUS, which has been actively targeting large commercial entities since March 2023. The name "CACTUS" is derived from the filename found within the ransom note, cAcTuS.readme.txt, and is also self-declared within the note. Encrypted files carry the extension .cts1, although variations in the appended number have been observed across different incidents and victims.
CACTUS uses a unique tactic by requiring a key for decrypting the binary, likely implemented to evade antivirus detection. This key is embedded within a file named ntuser.dat, loaded through a scheduled task. Kroll’s research noted instances of data exfiltration and victim extortion over Tox, a peer-to-peer messaging service, but no known victim leak site was identified.
In its operations, CACTUS demonstrates a consistent set of tactics, techniques, and procedures (TTPs). The initial exploit involves the exploitation of vulnerable VPN appliances, a prevalent method observed across multiple CACTUS incidents. Once inside the network, the threat actor conducts internal scouting using tools like SoftPerfect Network Scanner and PowerShell commands to enumerate endpoints, identify user accounts, and ping remote endpoints.
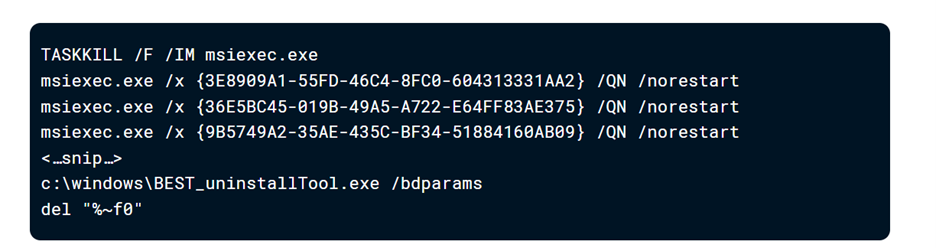
To maintain persistence, CACTUS deploys various remote access methods, including legitimate tools like Splashtop, AnyDesk, and SuperOps RMM, along with malicious tools like Cobalt Strike and Chisel. The threat actor attempts to disable security software using custom scripts, such as TotalExec, and uninstall common antivirus software.
Image 1: A Piece of Bath Script to Disable Anti-Virus
Source: Kroll
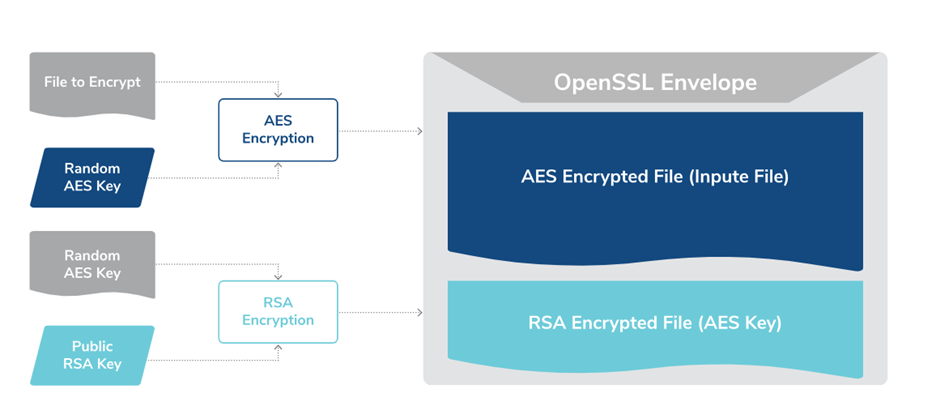
Lateral movement is achieved through valid or created accounts, the Remote Desktop Protocol (RDP), and remote management tools like Super Ops. For mission execution, CACTUS employs exfiltration tools like Rclone and deploys a script (TotalExec.ps1) to automate the deployment of the ransomware encryptor. The ransomware binary, named after the victim ID, follows an execution flow controlled by command-line switches, including setup mode, read configuration mode, and encryption mode.
Image 2: File Encryption Process
Source: Kroll
CACTUS encrypts files using the AES algorithm and OpenSSL's envelope implementation, appending them with the extension "cts\d." A ransom note named "cAcTuS.readme.txt" is created, providing details on negotiation over Tox chat. The ransom amount and the effectiveness of any provided decryptor in case of non-payment remain uncertain.
NOVEMBER 2023
In November 2023, cybersecurity firm Qlik reported instances of attacks exploiting vulnerabilities, specifically CVE-2023-41266, CVE-2023-41265, and CVE-2023-48365, to gain initial access. The threat actors involved tried to deploy CACTUS ransomware on compromised systems. Praetorian discovered these vulnerabilities and disclosed details in August and September.
The security vulnerabilities, classified as 'critical' and 'high severity,' impact Qlik Sense Enterprise for Windows, a data analytics solution. CVE-2023-41266 is identified as a path traversal issue allowing a remote, unauthenticated attacker to generate anonymous sessions and send unauthorized HTTP requests. Meanwhile, CVE-2023-41265 is a HTTP tunneling flaw that can allow an attacker to elevate privileges and execute HTTP requests on backend servers hosting repository applications.
When combined, these vulnerabilities allow a remote, unauthenticated threat actor to execute arbitrary code and introduce new admin users to the Qlik Sense application. Praetorian researchers assigned CVE-2023-48365 after successfully circumventing the patch for CVE-2023-41265.
Upon gaining initial access to the targeted organization's systems, the threat actors were seen altering admin account passwords, uninstalling security software, installing remote access software, engaging in data exfiltration, and employing RDP for lateral movement.
While Qlik's initial advisories stated that there was no exploitation of the vulnerabilities in the wild, Arctic Wolf maintained that attacks exploiting the vulnerabilities for remote code execution were observed. Qlik has since released a statement to Security Week acknowledging that they are conducting an investigation into the reports of exploitation.
DECEMBER 2023
In December 2023, Microsoft issued a warning about CACTUS ransomware, revealing that attackers are leveraging malvertising through online ads to infect victims. The threat actor behind the campaign, Storm-0216, (also known as Twisted Spider or UNC2198), shifted to using Danabot malware for initial access after receiving handoffs from Qakbot operators, whose infrastructure was dismantled by law enforcement in August 2023. Danabot, observed since November, operates with a private version of info-stealing malware, collecting user credentials and information sent to command and control. CACTUS has become increasingly prevalent in attacks on industrial organizations, impacting manufacturing and ICS equipment.
3am ransomware
In a recent incident involving a construction company, threat actors faced difficulty in deploying LockBit ransomware on the target network, leading them to resort to a newly identified ransomware variant known as 3AM. Symantec's Threat Hunter Team uncovered the incident, where a LockBit affiliate attempted to initiate a LockBit attack on the network but shifted to 3AM when LockBit deployment was thwarted.
3AM, written in Rust, represents an entirely new malware family. Before file encryption, it attempts to halt various services on the infected system and then proceeds to eliminate Volume Shadow (VSS) copies. The ransomware's authors and potential ties to known cybercrime organizations remain uncertain.
The attack preparation phase involves suspicious activities such as using the gpresult command to extract enforced policy settings and executing Cobalt Strike components for privilege escalation. Reconnaissance commands like whoami, netstat, quser, and net share are deployed, with the goal of lateral movement and adding a new user for persistence. The attackers also utilize the Wput tool to exfiltrate victim files to their FTP server.
Despite initial attempts to deploy LockBit, the attackers pivot to 3AM, which only achieves partial success. During the incident, it was deployed on three machines in the organization's network but was blocked on two out of three computers.
Named after its file extension, .threeamtime, and referencing the time in its ransom note, 3AM encrypts files, adding a marker string "0x666" to the encrypted data. The ransom note, emphasizing mysticism at 3 am, outlines the encryption and data theft, proposing negotiation via a Tor browser link.
The malware's execution involves various command-line parameters, with specific commands attempting to stop security and backup-related software before initiating file encryption. 3AM attempts to delete Volume Shadow backup copies and exhibits signs of being used as a backup when the primary ransomware attack fails.
Image 3: Ransom Note
|
Hello. "3 am" The time of mysticism, isn't it? All your files are mysteriously encrypted, and the systems "show no signs of life", the backups disappeared. But we can correct this very quickly and return all your files and operation of the systems to original state. All your attempts to restore data by himself will definitely lead to their damage and the impossibility of recovery. We are not recommended to you to do it on our own!!! (or do at your own peril and risk). There is another important point: we stole a fairly large amount of sensitive data from your local network: financial documents; personal information of your employees, customers, partners; work documentation, postal correspondence and much more. We prefer to keep it secret, we have no goal to destroy your business. Therefore can be no leakage on our part. We propose to reach an agreement and conclude a deal. Otherwise, your data will be sold to DarkNet/DarkWeb. One can only guess how they will be used. Please contact us as soon as possible, using Tor-browser: http://threeam7[REDACTED].onion/recovery Access key: [32 CHARS SPECIFIED BY -k COMMAND LINE PARAMETER] |
DEFENSE
The cybersecurity landscape is witnessing a transformative phase as cybercriminals, particularly ransomware affiliates, adopt more sophisticated strategies. The spotlight on Qlik, with vulnerabilities affecting over 40,000 customers, emphasizes the severity of the situation. ZoomEye's data, revealing 17,000 exposed instances of Qlik Sense, magnifies the need for robust cybersecurity measures.
CACTUS ransomware's targeted operations since March 2023, exploiting VPN appliance vulnerabilities, highlight the evolving tactics of cybercriminals. The introduction of 3AM as a backup plan in LockBit cyber attacks adds a layer of complexity, indicating a strategic approach among threat actors. While 3AM's current deployment is limited, its utilization as a fallback suggests a potential interest from attackers and the ransomware could be used again in the near future. Organizations must remain vigilant, using multifaceted defense strategies to keep their information safe. Please see the following recommendations on how to keep your organization safe from Cactus and 3AM:
CACTUS
- Patch and Update VPN Devices
- Given that VPN appliances are a likely avenue for initial access, it is wise to regularly patch and update these devices to mitigate vulnerabilities.
- Implement Password Managers
- The threat actor successfully extracted credentials from browsers. Implementing password managers enhances security by safeguarding sensitive credentials.
- Monitor PowerShell Execution
- Actively monitor and log PowerShell execution, creating detections for encoded script execution to detect and respond to any malicious activities involving PowerShell.
- Audit User, Administrator, and Service Accounts
- Regularly audit and verify the access and privileges of user, administrator, and service accounts. Adhering to the principle of least privilege ensures appropriate access levels and reduces the risk of unauthorized actions.
- Implement Multi-Factor Authentication
- To restrict access to sensitive areas and prevent lateral movement, incorporate multi-factor authentication. This additional layer of security is essential, especially in light of the threat actor's ability to traverse the network freely.
- Review Backup Strategies
- Establish robust backup strategies by ensuring regular backups and maintaining at least one isolated from the network. This proactive approach allows for quick restoration in the event of an impact, enhancing overall resilience against ransomware attacks.
3AM
- User Education and Training
- Conduct regular cybersecurity awareness training for employees to recognize and avoid phishing attempts. Given that the threat actors initially gained access through user interactions, educated and vigilant users are a critical defense.
- Endpoint Security Solutions
- Deploy and maintain robust endpoint security solutions, including antivirus and anti-malware software. This can help detect and block malicious activities, providing an additional layer of defense against ransomware.
- Access Control and Least Privilege
- Enforce the principle of least privilege by restricting user access to the minimum level necessary for their roles. This limits the impact of a potential breach and reduces the likelihood of lateral movement within the network.
- Multi-Factor Authentication
- Implement MFA to add an extra layer of authentication, preventing unauthorized access even if credentials are compromised. This is particularly important in mitigating the risk of lateral movement observed in the 3AM ransomware attack.
How Avertium is Protecting Our Customers
How Avertium is Protecting Our Customers
It’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. Avertium can provide the following services to help keep your organization safe from ransomware strains such as CACTUS and 3 AM:
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills. See every threat in your attack surface, every device, every entry point, and every vulnerability. Our Attack Surface Management services include:
- Risk Assessments
- Pen Testing and Social Engineering
- Infrastructure Architecture and Integration
- Zero Trust Network Architecture
- Vulnerability Management
- Avertium offers Vulnerability Management (VM) to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability
MITRE MAP
CACTUS
- Initial Access
- T1190: Exploit Public-Facing Application
- Execution
- T1059: Command and Scripting Interpreter
- T1053.005: Scheduled Task
- T1072: Software Deployment Tools
- Persistence
- T1136: Create Account
- Defense Evasion
- T1562.001: Disable or Modify Tools
- T1027.002: Software Packaging
- T1027: Obfuscated Files or Information
- Credential Access
- T1555.003: Credentials from Web Browsers
- T1003: OS Credential Dumping
- Discovery
- T1049: System Network Connections Discovery
- T1087.002: Domain Account
- T1087: Account Discovery
- T1018: Remote System Discovery
3AM
- Initial Access
- T1193: Spearphishing Attachment
- Execution
- T1059: Command and Scripting Interpreter
- Defense Evasion
- T1027: Obfuscated Files or Information
- Impact
- T1486: Data Encryption for Impact
- T1490: Inhibit System Recovery
- T1529: System Shutdown/Reboot
- T1096: Account Manipulation
- T1048: Exfiltration Over Alternative Protocol
INDICATORS OF COMPROMISE (IOCS)
CACTUS
- IP Address
- 163[.]123[.]142[.]213
- MD5
- d9f15227fefb98ba69d98542fbe7e568
- 3adc612b769a2b1d08b50b1fb5783bcf
- be7b13aee7b510b052d023dd936dc32f
- 26f3a62d205004fbc9c76330c1c71536
- d5e5980feb1906d85fbd2a5f2165baf7
- 78aea93137be5f10e9281dd578a3ba73
- SHA256
- 78c16de9fc07f1d0375a093903f86583a4e32037a7da8aa2f90ecb15c4862c17
- Files Created
- C:\ProgramData\ntuser.dat
- C:\ProgramData\b4kr-xr7h-qcps-omu3.exe
- C:\ProgramData\update.log
3AM
- SHA256
- 079b99f6601f0f6258f4220438de4e175eb4853649c2d34ada72cce6b1702e22
- 307a1217aac33c4b7a9cd923162439c19483e952c2ceb15aa82a98b46ff8942e
- 680677e14e50f526cced739890ed02fc01da275f9db59482d96b96fbc092d2f4
- 991ee9548b55e5c815cc877af970542312cff79b3ba01a04a469b645c5d880af
- ecbdb9cb442a2c712c6fb8aee0ae68758bc79fa064251bab53b62f9e7156febc
- Network Indicators
- 185.202.0[.]111
- 212.18.104[.]6
- 85.159.229[.]62
Supporting Documentation
A Deep Dive Into Cactus Ransomware Whitepaper | SecurityScorecard
Cactus ransomware exploiting Qlik Sense flaws to breach networks (bleepingcomputer.com)
Protection Bulletins (broadcom.com)
CACTUS ransomware | Cyber Threat Intelligence | Kroll
Cactus Ransomware Report - Quorum Cyber
Q3 Ransomware Report: Global Ransomware Attacks Up More Than 95% Over 2022 (corvusinsurance.com)
Qlik Sense Vulnerabilities Exploited in Ransomware Attacks - SecurityWeek
DoubleQlik: Bypassing Original Fix for CVE-2023-41265 - (praetorian.com)
Qlik Sense Remote Code Execution Technical Exploitation - (praetorian.com)
When LockBit Ransomware Fails, Attackers Deploy Brand-New '3AM' (darkreading.com)
Malvertising leveraged to distribute Cactus ransomware | SC Media (scmagazine.com)
Qlik Sense flaws exploited in Cactus ransomware campaign - Help Net Security
Microsoft warns of Cactus ransomware actors using malvertising to infect victims (therecord.media)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.