End of the Year Recap and What to Expect for 2023
Executive Summary
In 2022, we witnessed eventful cybersecurity incidents that were destructive and overwhelming for many organizations. Russia and Ukraine attacked one another with malware wipers while hacktivists stole data from organizations within critical infrastructure. Last year’s vulnerabilities such as Log4Shell and PrintNightmare are still an issue for organizations, and supply chain attacks have not slowed down.
Over the past twelve months, cyber security researchers have witnessed threat actors become stealthier and more sophisticated with their attacks. Amateur groups such as Lapsus$ and Killnet proved that you don’t need to be a veteran cybercriminal with sophisticated tools to launch a successful cyber attack, and Google became a consistent target for threat actors. From Hermetic Wiper to Google’s zero days, let’s take a look at this year’s most talked about cyber threats and what organizations can expect for 2023.
privilege escALATION - ZERO DAYS
Although PrintNightmare (CVE-2021-34527) is a Microsoft Windows Print Spooler zero-day vulnerability that was exposed in 2021, it is still on the Cybersecurity and Infrastructure Security Agency’s (CISA) known exploited vulnerabilities catalogue this year. PrintNightmare allows local privilege escalation and remote code execution exploits. The vulnerability is located in the Windows print spooler service that Microsoft patched in July 2021.
In 2021, a Chinese security team named Sangfor presented a novel exploit at the cyber security conference, Black Hat. At the time, they produced a proof-of-concept (POC) exploit and published a teaser of the exploit on their Twitter feed. Unfortunately, the researchers not only published the teaser to their Twitter feed, they also published the full exploit to their public GitHub page – making room for cybercriminals to clone it and exploit it. PrintNightmare became a zero-day that haunted security professionals well into 2022.
In March 2022, CISA issued an advisory stating that Russian state-sponsored threat actors gained network access to a non-governmental organization by leveraging multi-factor authentication (MFA) defaults and exploiting PrintNightmare. The threat actors enrolled a new device for MFA and accessed the organization’s network before exploiting the vulnerability. As a result, they had access to email accounts, and they were able to move laterally to the organization’s cloud environment and steal sensitive documents.
PrintNightmare exploits continued into June 2022 when the ransomware group Black Basta was observed exploiting the print spooler flaw after gaining initial access in an attack to perform privileged file operations. The threat actors behind NightSky Ransomware also made swift moves to exploit Log4Shell.
CVE-2022-37969
CVE-2022-37969 is a privilege escalation zero-day vulnerability in Microsoft’s Windows Common Log File System Driver (CLFS). The vulnerability has a CVSS score of 7.8 and could allow attackers to gain system privileges and take over a machine.
To exploit it, an attacker would need to have access to their target’s system and the ability to run code on the system. It is not a complex vulnerability, but a crafty attacker could use it to exploit a different vulnerability or use a basic social engineering phishing attack to gain system privileges. Although Microsoft patched the vulnerability, CVE-2022-37969 became the second actively exploited zero-day in the CLFS component since the start of 2022.
CVE-2022-22047
CVE-2022-22047 is a Microsoft zero-day vulnerability found in the latest Windows 11 and Windows Server 2022 releases. CVE-2022-22047 is a local privilege escalation vulnerability found in the Windows Client and Windows Server Runtime Subsystem.
An attacker who successfully exploits the vulnerability could gain SYSTEM privileges and disable local services such as Endpoint Detection and Security tools. However, in order to gain those privileges, the attacker must first gain access to the system by exploiting a separate code execution flaw.
Microsoft patched the vulnerability in July 2022, but not before the threat actor, KnotWeed used it to gain system privileges and launch cyber attacks. The threat group is a private-sector offensive threat actor that has a history of exploiting Windows and Adobe zero-day vulnerabilities in targeted attacks.
SIMILARITIES
PrintNightmare, CVE-2022-37969, and CVE-2022-22047 were all zero-day vulnerabilities that allowed attackers to gain privilege escalation and possibly take over machines. However, in PrintNightmare’s case, threat actors were able to successfully continue to exploit the vulnerability due to organizations inconsistent patching. If organizations would have patched the vulnerability when the patch was initially released, they would have been less likely to be compromised.
initial access - phishing via social media
BUMBLEBEE
In April 2022, Proofpoint discovered a new malware loader called Bumblebee. The malware was linked to several threat actors and high-profile ransomware operations. Specializing in stealth, Bumblebee was responsible for multiple cyber attacks. At the time, Bumblebee was still in active development, but the malware was determined to be an upgraded replacement for BazarLoader.
Google’s Threat Analysis Group (TAG) began tracking the threat actors behind Bumblebee in September 2021. They named the group EXOTIC LILY and observed them exploiting a zero-day in Microsoft MSHTML (CVE-2022-40444). The group acts as an initial Access Broker for Bumblebee and could be associated with the Russian cyber gang known as FIN12 or WIZARD SPIDER. EXOTIC LILY is a financially motivated group and was seen using domain spoofing as a way to gain additional credibility with the organizations they target.
The group has even gone as far as pretending to be employees of legitimate organizations on social media, sometimes creating fake profile pictures using a public service that generates A.I. human faces. In March 2022, Proofpoint observed Bumblebee ransomware being used in at least three separate waves of cyber attacks by three threat actors.
The main objective of Bumblebee is to download and execute additional payloads. Proofpoint observed the malware dropping shellcode, Cobalt Strike, Silver and Meterpreter. By March 2022, Bumblebee launched a DocuSign-branded email campaign with two alternate paths leading to victims downloading a malicious ISO file. There was also a campaign where victims were sent malicious emails after the threat actors submitted messages via the contact form on their target’s website.
Kroll reported that Bumblebee’s C2 servers correlate to previous Ryuk and Conti shared infrastructure, as well as IcedID, which is a trojan used by Quantum Locker. According to Kroll’s observations, Bumblebee was used as an initial infection vector to a Quantum Locker ransomware attack.
ZINC
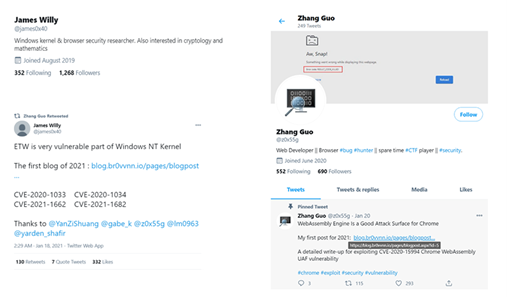
ZINC, also known as Hidden Cobra by the U.S. government, is a North Korean threat actor that is known for targeting security researchers, pen testers, and employees at security technology companies. Microsoft observed ZINC targeting the Infosec community on social media platforms such as LinkedIn and Twitter. ZINC is a sub-group of Lazarus and their objectives are geared toward espionage, data theft, financial gain, and network destruction.
The threat actors would spend months on social media platforms building their reputation before launching an attack on their target. They spent time on social media and created what looked like genuine content. They also created a bogus blog and once the target clicked on the blog link, malware was downloaded onto their devices. Although not confirmed by researchers, this chain of events indicates that a Chrome browser exploit chain was hosted on the blog. It was further suspected (but not proven) that because some of the victim’s browsers were not patched, the exploit chain used zero-days or patch gap exploits.
Once ZINC built up their credibility on social media platforms, they approached their targets and started conversations related to security or exploit techniques. When the target responded, they would lure them to another platform (Discord, email, etc.) or send files using encrypted PGP protected ZIPs. ZINC’s activity was a reminder to the Infosec community that they are targets to government-backed threat actors.
Image 1: Twitter Account Controlled by ZINC
Source: Microsoft
SIMILARITIES
The threat actors behind both Bumblebee and ZINC used phishing via social media as an initial access point. Both threat actors pretended to be something or someone that they were not to lure their targets. The threat actors behind Bumblebee pretended to be employees from legitimate organizations, while ZINC pretended to be a part of the Infosec community. In cases like these, it is the end-user who can help thwart a cyber attack by recognizing red flags.
Social engineering happens when threat actors like ZINC and those behind Bumblebee influence or manipulate victims so they can gain control over their computer system. One of the most obvious indications that you might be a target of a phishing campaign via social media include an individual or well-known company trying to persuade you to move off of social media and onto another platform. Also, if someone you have never met in person or offline is trying to persuade you to download an attachment, that is a red flag.
Things to avoid on social media:
- Sharing your work email address
- Sharing phone numbers
- Sharing addresses of any kind
- Sharing your financial status
- Sharing your job role (may be impossible with career related social media platforms like LinkedIn)
- Sharing your location
- Sharing screenshots of conversations
LATERAL MOVEMENT
CVE-2022-22954
In 2022, Avertium’s Cyber Threat Intelligence Team issued four Flash Notices regarding VMware vulnerabilities. The most notable VMware vulnerability is CVE-2022-22954 - a critical remote code execution (RCE) vulnerability, due to a server-side template injection, in VMware Workspace ONE Access and Identity Manager.
The vulnerability was addressed on April 6, 2022, and a patch was issued, however, by April 13, 2022, a proof of concept (PoC) exploit code was published – allowing attackers to target vulnerable systems. The vulnerability was given a CVSSv3 score of 9.8.
What made the vulnerability noteworthy was the fact that it could be chained together with another vulnerability, CVE-2022-22960 – another remote code execution vulnerability found in VMware Workspace ONE Access (Access), VMware Identity Manager (vIDM), VMware vRealize Automation (vRA), VMware Cloud Foundation, and vRealize Suite Lifecycle Manager.
After gaining root access, APTs were able to wipe logs, elevate permissions, and apply lateral movement to gain control over compromised systems. According to MITRE, a common goal for post compromise exploitation of remote services is for lateral movement to enable access to a remote system.
YANLUOWANG
Yanluowang is a ransomware operation and is highly experienced with ransomware-as-a-service (RaaS). The group could be linked to veteran RaaS groups, Fivehands and Thieflock. Although the group is primarily focused on attacking organizations within the financial sector, they have also targeted companies in manufacturing, IT services, consultancy, and engineering.
According to Symantec, their Threat Hunter Team initially discovered the use of AdFind, a legitimate command-line Active Directory query tool, on the undisclosed target’s network. Ransomware attackers often use AdFind as a reconnaissance tool. The tool also equips Yanluowang operators with resources that they need for lateral movement by way of Active Directory. Days after discovering the suspicious use of AdFind, the attackers attempted to deploy Yanluowang ransomware.
VICE SOCIETY
At the beginning of September 2022, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) warned that a ransomware gang named Vice Society was targeting the education sector. The advisory stated that they expected an increase in attacks after the start of the 2022/2023 school year due to cyber criminal groups seeing opportunity.
Vice Society obtains initial network access through compromised credentials by exploiting internet facing applications. Before deploying their ransomware, Vice Society explores their victim’s network to identify opportunities to increase access and to exfiltrate data for double extortion. The group has also been seen using several tools, including PowerShell Empire, SytemBC, and Cobalt Strike for lateral movement.
SIMILARITIES
The APTs that exploited CVE-2022-22954, and the threat actors Yanluowang and Vice Society, all used lateral movement to gain control over their victim’s machines. Although Yanluowang and Vice Society focus on different sectors, they both used legitimate tools to help aid with lateral movement. As a result, they were able to breach organizations and steal sensitive data.
Organizations could have prevented the lateral movement by implementing network hierarchy protocols with network segregation and decentralization. Endpoint detection tools (EDR) would have also been useful for detecting lateral connections. It is also important to note that lateral movement often depends on software utilities running from the command line. Threat actors will have great difficulty moving laterally if they are not able to run these tools.
NOTEWORTHY SECURITY EVENTS OF 2022
RUSSIA VS. UKRAINE
In January 2022, Microsoft warned that there was a destructive malware being used to corrupt the systems of several organizations in Ukraine. At the time, Microsoft stated it was a ransomware-like malware that was made on January 13, 2022. The malware was designed to look like ransomware but lacked a ransom recovery mechanism. The malware turned out to be a wiper-like worm and it was later named WhisperGate.
A few days prior to Microsoft’s discovery, over 70 Ukrainian government websites were defaced by groups that are allegedly associated with the Russian secret service. WhisperGate had two stages:
- Stage 1 - WhisperGate’s tactical defense is its ability to disguise itself as ransomware. After the multi-stage malware executes via Impacket, it overwrites the MBR (Master Boot Record) on a system and includes a $10,000 Bitcoin ransom note. After the intended device powers down, the malware executes.
- Stage 2 - Stage 2 (stage2.exe) of the malware is being described as a malicious file corrupter. After execution, stage2.exe downloads the next-stage malware hosted on a Discord channel, with the downloaded link hardcoded in the downloader. The downloader fetches the third stage, which is a dynamic link library (DLL) file. The DLL is coded in C# and drops a fourth-stage wiper payload, which deletes all data on the endpoint.
WhisperGate was just the beginning of the wipers that Russia and Ukraine would deploy in retaliation. After WhisperGate, Cyclops Blink and HermeticWiper were involved in attacks against Ukraine. Cyclops Blink has been in the wild since 2019 and was linked to the threat actor Sandworm. The threat actor was linked to Russia’s military intelligence division – Russian General Staff Main Intelligence Directorate.
Not long after the deployment of Cyclops Blink, Russia deployed another data wiper called HermeticWiper. The wiper was very similar to WhisperGate and was deployed on Ukraine’s computer networks.
By the end of February 2022, ESET discovered three new cyber attacks that were deployed against Ukraine which included three wipers: IsaacWiper, HermeticWizard, and HermeticRansom. HermeticWizard spreads HermeticWiper (aka DriveSlayer) across local networks via WMI and SMB. ESET observed that HermeticWizard is a worm that was deployed on a Ukrainian system on February 23, 2022. At this point during the conflict, Russia and Ukraine were clearly at odds but the three wipers were not attributed to Russia and the attackers remained unknown.
By March 2022, Russia and Ukraine were in an intense cyber war. The malware CaddyWiper and RURansom were deployed against Ukraine – wiping data from Ukraine’s networks. Although CaddyWiper’s code was not similar to HermeticWiper or IsaacWiper, the goal was still the same – erase user data and partition information from attached drives to render systems unusable.
There were two wipers that Russia deployed which flew under the radar – WhisperKill and DoubleZero. The wipers were active in January 2022 and went after Ukraine’s systems. WhisperKill is a malicious software designed to permanently erase files by overwriting their contents with 1MB of 0xCC character sequence. DoubleZero was seen targeting Ukrainian enterprises as Russia invaded the country.
HACKTIVISTS - CONTI & NB65
When Russia declared war on Ukraine, hacktivists began to declare their allegiance to either country. Conti was one of the first threat actors to choose a side by siding with Russia. Conti was a Russian-speaking RaaS gang that used RaaS to deploy destructive ransomware attacks, targeting critical infrastructure. Researchers believe that their stance on the war is what led to their chat logs and source code being leaked by a Ukrainian patriot and researcher in February 2022.
Despite Russia’s constant attacks on Ukraine, the tables turned in April 2022 when the threat actor NB65 (linked to Anonymous) took sides with Ukraine and stole files from the Russian space agency, Roscosmos. The threat actor also used Conti’s leaked source code against them by using the code in their Roscosmos attack. Anonymous, NB65, DoomSec, AgainstTheWest, and other hacktivist groups continued to bombard Russia with cyber attacks.
By June 2022, Conti had shut down and splintered into smaller, lesser-known ransomware groups. According to our partners, AdvIntel, Conti was in the process of rebranding into multiple ransomware groups and the brand (not the organization) was shutting down.
AdvIntel also confirmed that the ransomware group Quantum (discovered in August 2021) is a splinter group from Conti and that the ransomware operation was taken over by Conti Team Two in April 2022 – keeping Quantum’s original name.
ATTACKS ON HEALTHCARE
MAUI & MEDUSA LOCKER
In 2022, ransomware gangs attacked healthcare organizations at an unprecedented rate. Threat actors became aware of the vulnerabilities within the sector and they took every opportunity to attack. In July 2022, Medusa Locker and Maui ransomware infected and encrypted systems across multiple sectors, with specific attention to the healthcare sector.
During 2019, MedusaLocker took advantage of the chaos surrounding the COVID-19 pandemic and launched phishing and spam email campaigns to gain initial access. The threat actors behind the ransomware rely on vulnerabilities in Remote Desktop Protocol (RDP) to gain access to their victim’s networks. To gain access to victim’s networks, MedusaLocker uses phishing and spam email campaigns, attaching the ransomware directly to the email. To avoid security tools, MedusaLocker restarts the targeted machine in safe mode before execution – avoiding encrypting executable files.
Maui ransomware is believed to be an operation by North Korean-state sponsored threat actors. In 2021, threat actors infected he servers of a medical center in the District of Kansas, receiving $100,000 in Bitcoin to decrypt and recovery encrypted files. The FBI was able to trace the payments back to China-based money launders. In 2022, Maui continued to be a threat to the healthcare sector. However, in April 2022, the FBI was able to seize a cryptocurrency account that received a $120,000 payment. The account was confirmed to be related to a medical center based in Colorado.
ZEPPELIN RANSOMWARE
In August 2022, Zeppelin ransomware targeted the healthcare sector with a new campaign that involved multi-encryption tactics. The threat actors also targeted charities, non-profit organizations, and homeless shelters. Attackers gained access to victims’ networks via RDP exploitation, SonicWall firewall vulnerabilities, and phishing campaigns. However, all hope was not lost for the organizations hit by the ransomware. For two years, law enforcement and security experts have been secretly decrypting systems for victims.
The cyber security firm Unit 221B has been helping Zeppelin ransomware victims for two years. The researchers found a vulnerability in Zeppelin’s encryption flow that temporarily left a key in the registry. As a result, Unit 221B was able to exploit the vulnerability and crack the keys on victims’ computers.
NOTEWORTHY THREAT ACTORS
BLACKCAT
BlackCat or ALPHV is a ransomware group that uses triple extortion in their attacks - a new technique that we did not see with previous ransomware gangs. Discovered by researchers in November 2021, the threat actors recruit affiliates to perform corporate breaches and encrypt devices. They have recruited affiliates from several ransomware gangs, including BlackMatter, REvil, and DarkSide.
BlackCat’s ransom demands range from $400,000 to $3 million. Their ransomware is highly customizable and allows for attacks on a wide range of corporate environments, targeting both Linux and Windows systems. What makes BlackCat unique is that they add a third layer to their extortion process.
Generally, ransomware gangs use the double extortion technique, a technique that involves ransomware gangs stealing sensitive data before infecting networks and systems with ransomware. The stolen data is then used to extort the victims into paying the demanded ransom. If the ransom is not paid, the threat actor will leak the stolen data on a data leak site. BlackCat takes things a step further by adding a third layer to their extortion model – a DDoS attack if the demanded ransom isn’t paid by their deadline. Cyber security researchers call the third layer triple extortion.
In December 2022, BlackCat was called out by the HHS Health Sector Cybersecurity Coordination Center (HC3) for targeting the healthcare sector. HC3 describes the group’s ransomware variant as “one of the more adaptable ransomware operations in the world.”
LOCKBIT 3.0
This year, Avertium’s Cyber Threat Intelligence team published two Threat Intelligence Reports featuring LockBit and the group’s evolution. In July 2022, the ransomware operation rebranded for the second time and acquired new tactics and techniques, as well as a new bug bounty program.
During that time, LockBit rebranded as LockBit 3.0 and attacked several organizations including IT service providers and automotive giants. LockBit is known for researching their targets before they attack, with an earlier 2021 attack being on Accenture – one of the world’s largest tech consultancy firms. The group stole 6 TB of data and demanded $50 million in ransom. Accenture’s revenue for 2020 was $44.33 billion.
In 2022, LockBit 3.0 announced the world’s first bug bounty program ran by cyber criminals. The program is specifically for security researchers, unethical, and ethical hackers to find flaws in LockBit’s ransomware. By December 2022, LockBit 3.0 was named by HC3 (along with BlackCat) as one of the threat groups actively targeting the healthcare sector and that the sector should consider the group a threat.
MFA BREACHES
This year, multi-factor authentication (MFA) breaches were a trending attack method amongst cyber criminals. Uber suffered a security breach by a threat actor bypassing MFA. In September 2022, Uber was allegedly breached by an 18-year-old hacker who goes by the name “Tea Pot”. The hacker tricked an Uber employee (social engineering) into giving him account access and accepting an MFA prompt, allowing the hacker to register their own device. Dropbox, GitHub, and Rockstar Games were also victims of MFA attacks.
LAPSUS & KILLNET
Lapsus$ and Killnet proved that you don’t need to be an advanced hacker to pull off a cyber attack, you just need to attack organizations with weak security posture and be consistent. In March 2022, the authentication company Okta Inc. was breached by Lapsus$, a new threat act actor. During the same month, Globant suffered also suffered a breach via MFA Fatigue, followed by T-Mobile in April 2022.
MFA fatigue is a growing attack trend amongst threat actors. It involves an attacker running a script, attempting to log in with stolen credentials repeatedly – causing a nonstop stream of MFA push requests. The goal is to keep sending these push notifications day and night until the victim on the receiving end of the requests breaks down and accepts the request or accidentally hits the “approve” button.
Additionally, in March 2022, Microsoft was attacked by Lapsus$ and had their internal projects leaked. Cyber security researcher, Kevin Beaumont, stated that Microsoft had multiple code signing certificates leaked as well.
Not long after the initial company breaches, seven members of Lapsus$ were arrested. The London Police arrested seven teenagers between the ages of 16 and 21, with the alleged leader of the group being a 16-year-old Oxford-based teenager himself. It was speculated that the teen made around $14 million Bitcoin from the attacks.
Lapsus$ was able to breach the organizations by purchasing initial access from websites such as Russian Market. The site sells access to remotely compromised systems, as well as credentials that may be stored on the systems. Lapsus$ also gained access to organizations via employees with access to systems and networks. They advertised on their Telegram Channel that they were looking for insiders that were willing to give up their credentials for a fee.
In June 2022, Killnet claimed responsibility for a DDoS attack on the European country, Lithuania. The attack was in response to the country’s decision to block transit goods sanctioned by the European Union to the Russian exclave of Kaliningrad. As a result, Killnet disrupted 1652 of Lithuania’s web resources.
Killnet’s attack vector of choice is DDoS attacks. They don’t use or develop custom tools and the tools they use are not very sophisticated. The group has a preference for brute-forcing credentials and in May 2022, Forescout observed 81 attacks coming from 58 unique IP addresses – 56 of which were dictionary attacks using well-known default credentials in hopes that their target wouldn’t change them.
Killnet appears to work based off emotion and revenge and they only attack via DDoS. The group has often been described as a nuisance due to their lack of sophistication and their sometimes-empty threats. AdvIntel’s believes that the group is simply a DDoS group despite their constant threats. Killnet’s tactics are primitive and even though they can take a server down for a period of time, they seem to be more focused on publicity than anything else. Neither Lapsus$ or Killnet has the skillset of advanced threat actors such as Conti or Ryuk.
google zero days
Google has had several zero-days this year (nine to be exact), but they have been quick to fix them by providing users with patches. The zero-days are a testament that attackers are becoming more familiar and capable of finding flaws in Google products - this was not the case in the past. In previous years, people assumed that Google’s products were safe and were not likely to be hacked. However, the security world knows that anything with an endpoint can be hacked, and Google products are no exception. Take a look at Google’s zero-days:
- CVE-2022-2856 - August 17
- CVE-2022-2294 - July 4
- CVE-2022-1364 - April 14
- CVE-2022-1096 - March 25
- CVE-2022-0609 - February 14
- CVE-2022-3723 - October 28
- CVE-2022-4135 - November 25
- CVE-2022-4262 – December 2
what to expect for 2023
The security incidents of 2022 were eventful and eye opening. In 2021, we ended the year with Log4Shell and began 2022 with the spirit of Log4Shell quietly lurking. We also watched Russia’s cyber attacks against Ukraine escalate, and unskilled threat actors like Lapsus$ take down large enterprises. While it’s important to take a look back at what we have endured, it is also important to look toward the future and be prepared for what may be ahead. Here are Avertium’s predictions for 2023.
RANSOMWARE
The return on investment is still dropping. Over the past few months, we have seen a slight uptick in ransomware activity. Ransomware next year will be worse than it was this year, although it will not be as awful as it was in 2020 or 2021. Ransomware affiliates are going to be more skilled and that will cause organizations a lot of issues.
The ransomware operations will be the entry way into cybercrime and script kiddies will end up doing a lot of damage in the process of deploying ransomware because they are not experienced. Ransomware operations will be the entry way into cyber crime in 2023.
BUSINESS EMAIL COMPROMISE (BEC)
Business Email Compromise will increase in 2023. Threat actors will spend more time inside email chains and they will come up with more material for the emails they create. The emails will become more convincing, more creative, and harder to detect.
THREAT ACTOR'S IN OTHER COUNTRIES
As the war between Russia and Ukraine slows down, Russian cyber threat activity will start to increase, but Ukrainian threat activity won’t increase as much. China will continue to be a threat, as Japan and Australia start taking proactive action against cyber crime operators. We can expect to see this from the U.S. government as well.
LOG4J
We will see at least one application that still has Log4j vulnerabilities embedded in it and gets picked up by threat for exploitation. Expect to see some sort of library that is used by different tools, opening up a vulnerability.
PARTNERS AND SERVICE PROVIDERS
Partners and service providers are going to continue to be an issue. Less skilled operators will target healthcare and education cyber environments because those sectors don’t usually have the best security in place. The more skilled operators will conduct more targeted attacks against service providers, particularly big game – organizations that can provide them with the maximum value. There will be a transition where ransomware returns are dropping, but we may also see the crypto return dropping.
Towards the end of the year, we may start to see a new variant of cyber crime. Threat actors will likely figure out a new way to start making money. It’s too early to tell exactly what that will be.
How Avertium is Protecting Our CUSTOMERS
As we look back at 2022, let’s remember that while there is no silver bullet for cyber security, adhering to cyber security best practices will always help keep your cyber environment safe. Some of the stealthiest cyber criminal gangs fly under the radar because organizations do not have the best cyber security posture. Avertium can help get you up to speed for 2023 by providing you with services that won’t leave your organization vulnerable:
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
- Avertium offers Vulnerability Management to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Avertium offers user awareness training through KnowBe4. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior
- Today’s attack surface extends beyond your physical IT assets, now encompassing your entire digital footprint. This expansion has fundamentally changed the surface area that security teams must protect. Gone are the days of vulnerability management serving as an adequate defense for your attack surface… today’s cybersecurity professionals have to think bigger: they have to think about attack surface management (ASM). Avertium offers Attack Surface Management and 3rd Party Vendor Risk services to keep your organization ahead of the curve.
- Avertium offers web application pen testing for software dependency compromise.
avertium's recommendations
CISA recommends organizations take the following actions to strengthen their defenses:
- Increase organizational vigilance by ensuring there are no gaps in Information Technology (IT)/Operational Technology (OT) security personnel coverage and that staff provides continual monitoring for all types of anomalous behavior.
- Prepare your organization for rapid response by adopting a state of heightened awareness. Create, update, or review your cyber incident response procedures and ensure your personnel are familiar with the key steps they need to take during and following an incident.
- Ensure your network defenders implement cybersecurity best practices. Enforce multi-factor authentication and strong passwords, install software updates (prioritizing known exploited vulnerabilities), and secure accounts and credentials.
- Stay informed about current cybersecurity threats and malicious techniques. Encourage your IT/OT security staff to subscribe to CISA’s mailing list and feeds to receive notifications when CISA releases information about a security topic or threat.
- Lower the threshold for threat and information sharing. Immediately report cybersecurity incidents and anomalous activity to CISA and/or the FBI.
MITRE Map
Please see the following links for information regarding TTPs:
Indicators of Compromise (IoCs)
Please see the following links for information regarding IoCs:
Supporting Documentation
Black Basta Ransomware Actors Take Aim at PrintNightmare Flaw | Decipher (duo.com)
Lapsus$: An In-Depth Look at Data Extortion Group (avertium.com)
Attackers breach NGO by exploiting MFA, PrintNightmare flaw • The Register
End of Year Recap for 2021 (avertium.com)
Microsoft's Latest Security Update Fixes 64 New Flaws, Including a Zero-Day (thehackernews.com)
Flash Notice: Windows Privilege Escalation Zero-Day (avertium.com)
Known Exploited Vulnerabilities Catalog | CISA
An Update on LockBit 3.0 (avertium.com)
0XDEAD ZEPPELIN (unit221b.com)
Google Chrome emergency update fixes 9th zero-day of the year (bleepingcomputer.com)
Chrome Releases: Stable Channel Update for Desktop (googleblog.com)
Microsoft's rough 2022 security year in review | CSO Online
An In-Depth Look at Yanluowang Ransomware (avertium.com)
Everything You Need to Know About Bumblebee Malware (avertium.com)
An In-Depth Look at the North Korean Threat Actor, ZINC (avertium.com)
HHS Warns Healthcare Sector of LockBit 3.0, BlackCat Ransomware (healthitsecurity.com)
Healthcare Ransomware Threats - MedusaLocker & Maui (avertium.com)
Threat Actors Chaining Unpatched VMware Vulnerabilities for Full System Control | CISA
Exploitation of Remote Services, Technique T1210 - Enterprise | MITRE ATT&CK®
An In-Depth Look at Vice Society Ransomware (avertium.com)
How WhisperGate Affects the U.S. and Ukraine (avertium.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.