Everything You Need to Know About Bumblebee Malware
Executive Summary
In April 2022, Proofpoint discovered that Bumblebee, a new malware loader, was linked to several threat actors and high-profile ransomware operations. Specializing in stealth, Bumblebee was responsible for multiple cyber attacks. At the time, Bumblebee was still in active development, but the malware was determined to be an upgraded replacement for BazarLoader.
Additionally, the malware was observed to have elaborate evasion techniques, including complex anti-virtualization. After analysis, Proofpoint found that the threat actors behind Bumblebee are associated with Quantum, Conti, and MountLocker. Bumblebee has been solidified as a highly sophisticated malware that is distributed via phishing email campaigns. Let’s take a look at Bumblebee, its links to threat actors, as well as tactics and techniques.
bumblebee malware
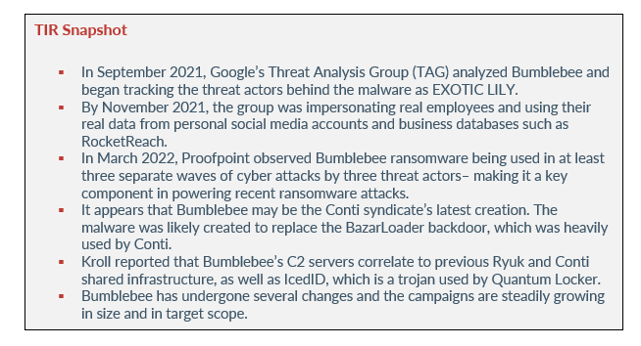
In September 2021, Google’s Threat Analysis Group (TAG) analyzed Bumblebee and began tracking the threat actors behind the malware as EXOTIC LILY. The group was seen exploiting a zero-day in Microsoft MSHTML (CVE-2021-40444). TAG believes that because several threat actors have been observed using Bumblebee malware, EXOTIC LILY is acting as an Initial Access Broker. TAG also believes that the group may be working with the Russian cyber gang known as FIN12 or WIZARD SPIDER.
According to TAG, EXOTIC LILY is a financially motivated group and their activities have been closely linked with data exfiltration and deployment of human-operated ransomware such as Diavol and Conti. It has been estimated that at the peak of EXOTIC LILY’s activity, they were sending more than 5,000 emails a day to about 650 global organizations. Initially, it appeared as if the group was only targeting specific industries such as IT and healthcare. Now, the group appears to be attacking a variety of industries with no specific focus.
In September 2021, EXOTIC LILY was seen using domain and identity spoofing as a way to gain additional credibility with organizations they were targeting. EXOTIC LILY posed as employees of real organizations on social media, sometimes creating a fake profile picture using a public service that generates A.I. human faces. By November 2021, the group was impersonating real employees and using their real data from personal social media accounts and business databases such as RocketReach. From there, EXOTIC LILY sent spearphishing emails via spoofed email accounts. The email subjects were geared toward business proposals or project development.
TAG further discovered that EXOTIC LILY used public-file sharing services such as WeTransfer, TransferXL, and OneDrive to upload their payload. They then used a built-in email notification feature to share the file with their target. This action allowed the final email to originate from the email address of a legitimate file sharing service instead of the threat actors email – presenting challenges for detection.
tactics & techniques
In March 2022, Proofpoint observed Bumblebee ransomware being used in at least three separate waves of cyber attacks by three threat actors– making it a key component in powering recent ransomware attacks. The threat actors used multiple techniques to deliver the malware, but researchers observed several similarities across the campaigns.
In an attack involving Quantum, Bumblebee was used to deliver ransomware to targets. The attack started with a phishing email that contained an ISO file. The ISO file hid the Bumblebee loader and ran it on the target’s machine once the email attachment was opened. Additionally, Proofpoint observed the malware using an APC (asynchronous procedure call) injection to start the shellcode from the commands received from the command and control (C2).
The main objective of Bumblebee is to download and execute additional payloads. So far, Proofpoint has observed the malware dropping shellcode, Cobalt Strike, Silver and Meterpreter. Bumblebee’s use amongst cyber criminal gangs coincides with BazarLoader, which is a popular payload that facilitates follow-on compromises.
In March 2022, Bumblebee was observed being used by three threat groups. A DocuSign-branded email campaign with two alternate paths lead to victim’s downloading a malicious ISO file. The first path included the victim opening an email and clicking on a hyperlink titled “REVIEW THE DOCUMENT”. After clicking, the victim unknowingly downloaded a zipped ISO file, hosted on OneDrive.
Additionally, the email also contained a HTML attachment, which masqueraded as an email containing a link for an unpaid invoice. The URL within the HTML attachment used a redirect service that is referred to as Cookie Reloaded. The redirect service uses Prometheus TDS to filter downloads based on the cookies and time zone of a target.
During the same month, there was a campaign sending emails to victims after the threat actors submitted messages via the contact form on their target’s website. Depending on how the contact portion of the site was configured, the submission left public comments. Furthermore, the emails sent claimed that stolen images existed on the website.
By April 2022, Proofpoint observed a thread-hijacking campaign that appeared to be replies to existing benign email conversations with malicious zipped ISO attachments. The attachment names were in the following pattern: “doc_invoice_[number]zip.” The ISO was password protected but the password was shared in the body of the email. If ran, the shortcut file “DOCUMENT.LNK” executed “tar.dll” with the correct parameters to start the Bumblebee downloader.
Avertium’s Cyber Threat Intelligence team (CTI) was able to analyze a sample of Bumblebee malware. The sample closely follows other indicators for Bumblebee’s TTPs. The first sample is a .vhd file, which can be mounted on a Windows machine as a virtual drive (and the files accessed). The second sample is a PowerShell file, which has a large portion of its data base64 encoded.
Image 1: Bumblebee - Base64 Encoded

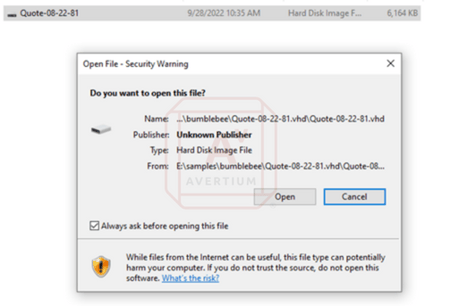
The hard disk image must be mounted to access the file stored on it.
Image 2: Hard Disk Image
Users will be warned about trusting these kinds of files; however, Windows will allow it to be mounted.
Image 3: Security Warning
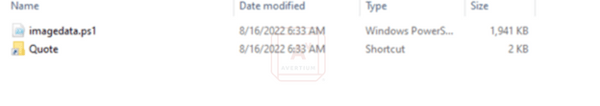
Once mounted, the only file that is visible is a shortcut file that attempts to trick users into double clicking it. After double clicking the shortcut, a hidden PowerShell file is executed.
Image 4: Bumblebee - Shortcut
The executed PowerShell script has multiple layers and types of obfuscation. The CTI team believes this was done to not only avoid detection by antivirus software, but to also confuse malware researchers. Many of the command strings are broken up into chunks and assigned variables, while the majority of the code is encoded and compressed.
Image 5: Bumblebee - ShowWindow and GetCurrentProcess
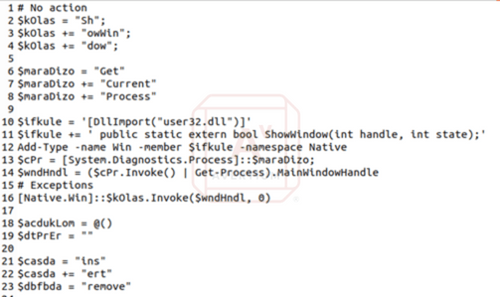
As you can see above, “ShowWindow” and “GetCurrentProcess” are broken into pieces and assigned to a variable. This makes the code hard to read without taking additional time. These are just two examples of using this method of obfuscation.
While EXOTIC LILY continued delivering ISO files in March 2022, they did so with a DLL containing their custom loader – a more advanced variant of a first-stage payload previously seen when the group was exploiting CVE-2021-40444. The loader is recognized by its use of a unique-user agent called “bumblebee” – thus the malware now being called Bumblebee. Bumblebee is likely being used to facilitate access for cyber criminals who wish to deploy ransomware.
links to other groups
As previously stated, it appears that Bumblebee may be the Conti syndicate’s latest creation. The malware was likely created to replace the BazarLoader backdoor, which was heavily used by Conti. According to Kroll, Bumblebee operates in a similar way to Emotet or IcedID – deploying payloads such as Cobalt Strike. The operators of Bumblebee have been named EXOTIC LILY by TAG and have been officially linked to Conti.
Kroll reported that Bumblebee’s C2 servers correlate to previous Ryuk and Conti shared infrastructure, as well as IcedID, which is a trojan used by Quantum Locker. According to Kroll’s observations, Bumblebee was used as an initial infection vector to a Quantum Locker ransomware attack. Kroll also observed a Bumblebee payload delivered via an ISO file downloaded from a Google storage service.
The phishing attack included the previously mentioned website contact lure where the threat actor sends an email via the contact form , claiming an organization has stolen images on its website. In this particular case, the following methods were used to deliver the malware:
- Phishing email with a link to a file sharing service offering a download of .zip of .iso container
- Phishing emails with attached .iso containers
- Email thread hijacking
- Excel .xlsb downloaded from Microsoft One
It’s also important to note that when a malware has been used for only two months by threat groups, it has undergone several changes in that time. The Bumblebee campaigns are steadily growing in size and in target scope.
How Avertium is Protecting Our CUSTOMERS
Malware like Bumblebee can be difficult to detect and difficult to stop by anti-virus tools. Because Bumblebee has increased its stealth-ness, it is alluring to ransomware and malware operators looking to deploy their payloads. Avertium offers the following services to keep your organization safe:
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts
- Avertium offers Vulnerability Management to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Avertium offers user awareness training through KnowBe4. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior
Avertium’s Recommendations
- Require multifactor authentication to protect employees’ accounts from being used by attackers to obtain account credentials and use them to escalate privileges and move laterally within the network.
- Perform daily backups and keep them offline to avoid losing data.
- Disrupt network movements/investigation by way of creating separated segments of network, clear access hierarchy, and additional security for active directory, domain admin, and local domains – thus complicating LockBit 3.0’s operations.
- Relying on outdated tools and point solutions will compromise your network or system. Better technology exists to detect complex attacks like LockBit 3.0 ransomware.
- Use anti-ransomware technology as a prevention method. Deploy prevention that works like next-generation antivirus and explicit anti-ransomware technology.
- Reduce the target by including these technical practices: close vulnerabilities, augment security hygiene, create and enforce strong general policies, and sustain backup and recovery practices.
- Prevent lateral movement by implementing network hierarchy protocols with network segregation and decentralization.
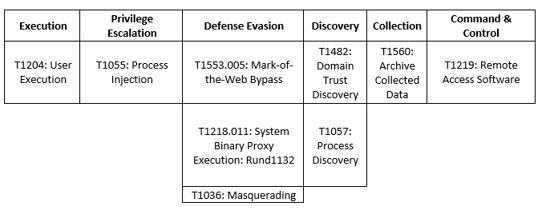
MITRE Map
Indicators of Compromise (IoCs)
MD5 Hashes
- 254d757d0f176afa59ecea28822b3a71
- 59fc 33d8 49f9 ad2a b4e4 b7fe 4b44 3a33
SHA-1 Hashes
- 3e59fff860826055423dde5bbd8830cceae17cf3
- e4ed0f94e8ad9aeeb019e6d253e2eefa83b51b5a
SHA-256 Hashes
- 0ff8988d76fc6bd764a70a7a4f07a15b2b2c604138d9aadc784c9aeb6b77e275
- 2102214c6a288819112b69005737bcfdf256730ac859e8c53c9697e3f87839f2
SSDEEP Hashes
- 24576:CjrA94pj6XmVW1MN90pbRYYeDADfI06nGjjO2:6KXENeVL776/2
- 24576:kjrA94pj6XmVW1MN9
Domains
- conlfex[.]com
- avrobio[.]co
- elemblo[.]com
- phxmfg[.]co
- modernmeadow[.]co
- lsoplexis[.]com
- craneveyor[.]us
- faustel[.]us
- lagauge[.]us
- missionbio[.]us
- richllndmetals[.]com
- kvnational[.]us
- prmflltration[.]com
- brightlnsight[.]co
- belcolnd[.]com
- awsblopharma[.]com
- amevida[.]us
- revergy[.]us
- al-ghurair[.]us
- opontia[.]us
Bumblebee ISO samples
- 9eacade8174f008c48ea57d43068dbce3d91093603db0511467c18252f60de32
- 6214e19836c0c3c4bc94e23d6391c45ad87fdd890f6cbd3ab078650455c31dc8
- 201c4d0070552d9dc06b76ee55479fc0a9dfacb6dbec6bbec5265e04644eebc9
- 1fd5326034792c0f0fb00be77629a10ac9162b2f473f96072397a5d639da45dd
- 01cc151149b5bf974449b00de08ce7dbf5eca77f55edd00982a959e48d017225
Supporting Documentation
BumbleBee: Round Two – The DFIR Report
The chronicles of Bumblebee: The Hook, the Bee, and the Trickbot connection | by Eli Salem | Medium
New Bumblebee malware loader increasingly adopted by cyber threat groups | TechRepublic
This isn't Optimus Prime's Bumblebee but it's Still Transforming | Proofpoint US
This new malware is at the heart of the ransomware ecosystem | ZDNET
Exposing initial access broker with ties to Conti (blog.google)
Bumblebee malware adds post-exploitation tool for stealthy infections (bleepingcomputer.com)
Bumblebee Loader Linked to Conti and Used In Quantum Locker Attacks | Kroll
New Bumblebee malware replaces Conti's BazarLoader in cyberattacks (bleepingcomputer.com)
Remote Access Software, Technique T1219 - Enterprise | MITRE ATT&CK®
The New Bumblebee Malware Replaces Now Conti’s BazarLoader (heimdalsecurity.com)
Bumblebee Malware Buzzes Into Cyberattack Fray (darkreading.com)
Google Details New 'Exotic Lily' Initial Access Group | Decipher (duo.com)
Bumblebee Malware: Deep Instinct Prevents Attack Pre-Execution | Deep Instinct
Exposing initial access broker with ties to Conti (blog.google)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.