How to Detect Ransomware: Best Practices for Avoiding Malware Attacks
RANSOMWARE – A GREATER THREAT THAN ONE MIGHT EXPECT
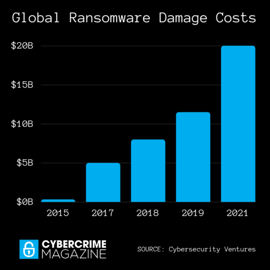
Over the past few years, ransomware attacks have skyrocketed, hitting 105% in 2021 while the ransomware payment demands have gone up 518%.
In 2021, JBS, the world’s largest meat processing company, fell victim to a ransomware attack. The company lost access to its servers after a malware attack forced them to choose between paying $11 million to regain access or indefinitely shutting down production in its plants across the nation. As a company responsible for processing about one-fifth of the nation’s meat supply, JBS ultimately chose to pay the ransom to the Russian ransomware gang known as REvil.
Successful ransomware attacks present large companies with harrowing financial and logistical choices. Because ransomware is designed to remain undetected, it often does not present itself until it has successfully gained the upper hand and can demand payment. However, by understanding how ransomware works and how to effectively use mechanisms that detect it early, well-equipped cybersecurity teams can outmaneuver these attacks.
In other words, companies often don’t know about ransomware until they've been hit by it... But does it have to be that way?
What is Ransomware?
Ransomware is a type of malware that targets data, devices, or infrastructure with the intent of extorting a ransom for restored use of the compromised data or machines. After infecting a device or network, a ransomware attack will use encryption techniques to lock out victims until they have paid the ransom demanded by the hacker.
Related Resource: RaaS Gangs, Drive-By-Downloads, and Botnets - Are You a Target?
Objectives of a Malware Attack
A malware attack could have several different objectives – here are some of the top reasons (note that a combination of the following could also be possible):
-
Data Exfiltration – The theft of personal credentials, financial information, or any sensitive data
-
Corporate Espionage – Rival businesses covertly use spyware or malware to monitor competitor activity, transmit trade secrets, or uncover future plans
-
Ransom – Attackers send a message indicating the price for your encrypted data, the payment method, and the timeframe (they can also transfer the encrypted data onto other devices, threatening data exposure if their demands go unmet)
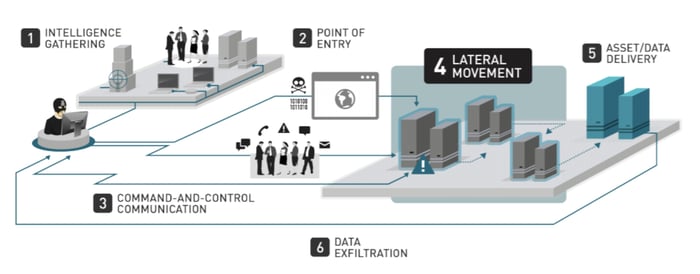
The Cyber Kill Chain
The term “cyber kill chain” refers to the sequential stages of a cyberattack and can be used for identifying, stopping, and preventing the attack. Unfortunately, as cybersecurity continues to advance, cybercriminal behavior adapts in step. While ransomware attacks can take many different forms, they tend to follow a pattern of:
- reconnaissance,
- malware delivery, and
- exploitation.
1. Precursors to a Ransomware Attack
Research and Reconnaissance
Before executing an attack, a cybercriminal will likely test the limits of their system access. Network, server, or workstation slowdowns may indicate that an attacker is preparing to interfere with your company. Any stoppage, regardless of cause or severity, must be classified as a cybersecurity incident. It's not always an attack or event, but it could be a sign of something bigger.
With this in mind, the most important question to ask your security personnel and systems is: Can your internal IT platform effectively recognize and monitor IT security incidents?
Weaponization
Attackers will use the information gathered through their reconnaissance to prepare their “game plan” for the attack. To help your organization prepare in advance for these specialized attacks, Avertium’s CTI Group produces timely, comprehensive Threat Reports and Flash Notices with the TTPs (tactics, techniques, and procedures) that many of today's active bad actors utilize.
Suspicious File Modifications
The unexpected appearance of or alterations to files or directories is another troubling sign. Frequently used files may suddenly appear to have different extensions or no extensions at all. If these alterations were not approved by someone in your company, this is a clear indicator of a cyberattack.
File Integrity Monitoring is a security service that immediately notifies your company if these unauthorized changes are made and can help stop attacks before they progress beyond this stage.
Data Extraction without Consent
A ransomware assault is likely underway if your team detects that many files have gone missing over a period of time. The attacker will want to wander undetected through your network for as long as possible in order to steal as much vital information as they can, but they will eventually begin exploring the boundaries of their access with fewer, less noticeable files before gradually moving onto larger targets.
Unrecognized File Encryption
Encrypting files is a good approach to keeping sensitive data safe whether it is in transit or at rest. However, misuse of encryption can jeopardize data availability, and that is a red flag for ransomware. Encryption should only be applied to data according to regulations or necessity, and it should always be performed by an authorized person. If your security team detects encrypted data on your network with an unknown origin or responsible party, it is evident that a cyberattack is likely underway.
Additional Precursors of an Impending Attack
Sometimes, multiple precursors appear. While they might seem to be separate attacks, they could also be different symptoms of the same attack or a long-term brute force attack against a publicly facing Remote Desktop Protocol (RDP) port.
Related Resource: Not all Penetration Tests are Created Equal: Tools for Effective Pen Testing
2. Delivery and Deployment of Malware
In this phase, instead of quickly executing their entire attack plan, the threat actor often uses their initial network access to strengthen their position. By installing back doors or creating new users with admin privileges, they ensure that they’re able to regain access to the network in the event that you detect and attempt to stop them.
There are a number of effective techniques for delivering the tool or medium attackers could use for their plan:
-
Phishing
Phishing is one of the most common methods for malware delivery today. Delivered most often via email, a payload can take many different formats including a PDF, ZIP file, Word documents, etc. One of the best defenses against phishing is cybersecurity awareness training. Users across an organization should understand the danger of blindly clicking on an unknown email link or attachment. Contacting the originator to verify a questionable email’s contents can save extended downtime and cost to your organization.
-
Remote Desktop Protocol (RDP)
RDP is designed to allow IT managers to remotely access a user's computer to troubleshoot or customize it. While there are obvious advantages to the friendly use of RDP, it can easily be weaponized for nefarious purposes. It is advised that RDP is disabled unless it is absolutely required.
-
Suspicious File Modifications
Drive-by downloads are malicious downloads that happen without a user’s knowledge while visiting a compromised website. Attackers often launch drive-by downloads by exploiting flaws in the software of reputable websites. Then, they exploit these flaws to either insert malicious code onto a website or lead the victim to a site that contains exploit kit software.
Exploit kits allow bad actors to secretly scan a visitor's device for vulnerabilities and (if any are discovered) execute code in the background without user action or approval. The victim will then be confronted with a ransom notice informing them of the infection and demanding payment for the return of their data.
-
Ransomware as a Service (RaaS) Gangs and Botnet Operators
Both RaaS Gangs and Botnet Operations have occasionally joined forces to propagate malware for more efficient delivery. This is accomplished through the spread of malicious emails.
In one instance, spam emails used subject lines that included Copy_, Document_, Scan_, File_ or PDF_ followed by random numbers. The infection vector is an attached PDF file containing an embedded Microsoft Word DOCM document. This document contained a malicious macro, which downloads and immediately executes the ransomware strain if permitted to run by the user.
However, if the infected system used Russian as the default language, that particular strain would delete itself prior to performing any encryption, giving quite a home-field advantage to the Russian RaaS Gangs behind the attacks.
Related Resource: Flash Notice: The Cyber War Continues - CaddyWiper vs RURansom
3. Exploitation: How Attackers Gain Control of Multiple Systems
After performing careful reconnaissance and successfully delivering their malware, the cybercriminals will accelerate the attack. With a compromised network, they can take advantage of the identified vulnerabilities and run exploits.
When installing the ransomware, attackers may use a variety of techniques to manipulate your network to their advantage.
-
Command + Control
Often called C2 or C&C, command and control servers are mechanisms for infecting a network of computers by deploying software beacons to establish communications with a Command and Control server controlled by the attacker. An attacker can use a single infected device as an in-road to then infect other devices on the same network by spreading the malware and establishing a botnet.
-
Botnet
A botnet is a network of computers that communicate with one another to deploy a ransomware attack. Most botnets consist of four elements:
-
The botmaster is the person in control of the ransomware attack.
-
The command and control server is the computer that the botmaster uses to communicate with compromised devices.
-
The malware is the code itself that, once installed onto a device, allows communication between the computer and the command and control server.
-
The bots are devices infected with malware that can be controlled by the botmaster.
-
-
-
Lateral Network Movement
Lateral network movement is the process of broadening access to a system by navigating the network environment and utilizing various tools to gain additional privileges. After obtaining access to the network, an attacker uses lateral movement tactics to advance deeper in pursuit of sensitive data and other high-value assets by impersonating a genuine user.
Even if an infection is identified on a workstation, lateral network movement allows a threat actor to evade containment and maintain network access. Because of the long-stay period of many attackers, data theft might occur weeks or even months after the initial breach.
Related Resource: Building an XDR Solution: Factors You Ought to Consider for ZTNA, EDR, Vulnerability Scanning, and SIEM
Common Types of Ransomware
As malware attack rates increase every year, ransomware continues to be the largest category of attacks. While the list of ransomware variants is constantly growing, they can generally be understood through a few frameworks:
-
Locker Ransomware
Locker ransomware involves locking users out of their devices until the ransom is paid. For example, locker ransomware may block access to device functionality (excluding the mouse and keyboard), rendering it unusable for anything but paying the ransom.
-
Crypto-Ransomware
Crypto-ransomware involves the encryption of valuable data. Victims can still use their computers but are met with a ransom message when they try to access their files.
-
Double Extortion
Double extortion is when attackers steal data and then threaten to leak it unless their demands are met.
-
Triple Extortion
Unlike double extortion, triple extortion incidents usually add the threat of distributed denial-of-service (DDoS) attacks. If the ransom is not paid, the attackers will launch a separate DDoS attack which disrupts the corporate network by overwhelming it with a flood of internet traffic.
-
Ransomware as a Service (RaaS)
RaaS is a business model where ransomware developers sell their ransomware variants to criminals lacking the technical expertise to engineer their own malware. It has fueled the spike in ransomware attacks by making ransomware attacks easier for non-experts to perform.
Rising Ransomware Variants
According to a ransomware incident report, the most prevalent ransomware strains in the fourth quarter of 2021 were...
-
LockBit 2.0 at 29.7%
-
Conti at 19%
-
PYSA at 10.5%
-
Hive at 10.1%
Related Resource: Why Pen Tests are Key to a Robust Incident Response Plan
Implement Best Practices for Ransomware Detection Before a Ransomware Attack Deploys
Ransomware attacks can be extremely creative and adaptive, and there is no single solution that can counter all malicious activity. However, a robust combination of practices can give your security team the edge to detect and respond to these threats.
Security Information and Event Management (SIEM)
A modern SIEM is a platform where security analysts use forensic tools and threat intelligence to hunt, investigate and respond to cyber threats in real-time. A modern SIEM must have four capabilities:
-
Detection Engineering
-
Monitoring
-
Incident Response
-
Threat Intelligence
Effective use of a SIEM can dramatically decrease an organization’s risk of attack.
Pen Testing
Similar to a bad actor performing reconnaissance before an attack, cybersecurity professionals conduct penetration tests by acting as “ethical hackers.” In a pen test, cybersecurity specialists attempt to discover a company’s security vulnerabilities. They allow security teams to identify and address potential vulnerabilities, ensuring that their company is not the low-hanging fruit that would attract an attacker’s attention.
Zero Trust Network Architecture
The philosophy of Zero Trust security is to take the default view that nobody, inside or outside the network, can be trusted and that anyone attempting to access the network must first verify their identity. Network Segmentation, one of the main pillars of ZTN, prevents lateral network movement if one part of the network is compromised. Data breaches have been prevented by adding this extra layer of security.
Related Resource: Flash Notice: Authentication Company, Okta, Breached by Lapsus$
Threat Hunting
Threat hunting is a strategy that involves searching through networks to detect and isolate threats before they actively present themselves. While threat hunters have a variety of strategies at their disposal, the best strategy is often determined by the type of threat they are hunting. Threat hunters do not only search for active threats; they are attuned to hacker tactics, techniques, and procedures (TTPs), indicators of compromise (IoCs), indicators of attack (IoAs), and threats such as Advanced Persistent Threats (APTs) that may be evading the existing security system.
Risk Assessments
A risk assessment can help you satisfy regulatory requirements with standards such as HIPAA / HITECH, HITRUST, FFIEC, PCI-DSS, and use guides and tools such as ACET and NIST-CSF.
Clients receive a gap analysis, a ranked list of action items, and a roadmap in accordance with a security maturity model to help put a timeline on fixing present issues. The assessment can be used as the baseline for improvement by integrating into a security strategy with Managed Detection and Response, Incident Response Preparedness, or Scanning & Technical Testing. These improvements can put you in a better posture to be prepared for ransomware or other advanced malware.
Everyday Tips for Ransomware Protection
-
Consider implementing Zero Trust Networking. The perimeter has collapsed and by trusting no one each user must be thoroughly authenticated before being granted access to sensitive corporate data.
-
Use Multi-Factor Authentication. Organization-wide use of MFA creates an added layer of identification to access a user’s credentials that can create a significant buffer between the network and a hacker.
-
Back up your data regularly and make sure it’s off-site. Maintaining regular backups of your company’s data eliminates the leverage of many ransomware threats.
-
Use a next-generation endpoint protection platform. Antivirus is not enough and is, in most cases, easily bypassed by modern ransomware attacks.
-
Never trust public Wi-Fi. The WPA2 protocol allows for the interception of all kinds of data points, including information that is supposedly encrypted.
-
Keep software up-to-date. Oftentimes, ransomware takes advantage of older vulnerabilities that have been fixed through software updates.
-
Create an organization-wide culture of cybersecurity. Equip your employees with the necessary skills and mindset to avoid security compromises.
Take a look at one of our latest eBooks:
"2022 Cybersecurity Predictions"