An In-depth Look at Conti's Leaked Log Chats
Executive Summary
At the end of February 2022, internal chats from the ransomware gang, Conti, were leaked by a Ukrainian security researcher and published on Twitter. Cyber security researchers and analysts believe that Conti’s chats were leaked by the researcher due to the gang taking a strong stance with the Russia and Ukraine war – with Conti siding with Russia.
Also, one of the tweets from the account proclaimed, “Glory for Ukraine”. Prior to the leak, Conti vowed their support for Russia in two statements which were released on their data leak site. The statement came on the heels of Russia invading Ukraine. Initially, it was suspected that the leaker was a Ukrainian employee, but Alex Holden from Hold Security said that was not correct. The individual posting Conti’s conversations is a Ukrainian patriot who chose to stay in Ukraine and fight for his country.
The leak contained several years’ worth of internal chat logs linked to Conti and can be read here. With more than 100 salaried employees, Conti is a criminal enterprise that operates as if it’s an ethical business. Last year, the gang generated $180 million and routinely demands multimillion dollar ransom payments from their victims. Let’s take a look at what we learned from the internal chat leaks and why this incident may not be the end of Conti.
Who is conti?
In a previous Threat Intelligence Report we explained that Conti is a Russian-speaking RaaS organization, who uses RaaS to deploy disruptive ransomware attacks that target critical infrastructure, like hospitals and government organizations. Conti generally focuses on attacking companies with more than $100 million in annual revenue. They specialize in double extortion operations of simultaneous data encryption and data exfiltration for financial gain. If the ransom is not paid, Conti will blackmail their victims by threatening to publish stolen files.
In May 2021, the FBI notified the public stating that Conti tried to breach over a dozen healthcare and first responder organizations. By September 2021, the gang successfully stole the data of several healthcare organizations. According to our partner, Advanced Intelligence, Conti builds their negotiation strategies based on the premise that the majority of targets who pay the ransom, do so because they need to restore their data – making prevention of data leaks a secondary goal.
It is believed that Conti is controlled by a Russian-based cyber crime group, Wizard Spider. Wizard Spider is known for creating and operating TrickBot banking malware. The group began using TrickBot in 2016 for financial fraud and now has three ransomware families – Ryuk, Conti, and BazarLoader. However, Conti only uses TrickBot if they need additional resources. Once they deploy it, they may wait and stay in the network, beaconing out by using Cobalt Strike.
Conti uses several tactics to exploit their victim’s networks and systems. They have been known to utilize tools easily found within their victim’s networks as an aid in their attacks, adding tools as needed (Mimikatz and Sysinternals) to escalate privileges and move laterally through a network. This gives Conti the leverage to gain unauthorized access to networks by stealing RDP credentials and weaponizing malicious email links or attachments.
Conti also removes backups by selecting a team of people with experience related to backup identification, localization, and deactivation. The backup removal team then uses Veeam backup software to aid in this feat. Veeam is a backup, recovery, and data management solutions platform for cloud, virtual, and physical environments. After finding Veeam privileged users and services, Conti exfiltrates, removes, and encrypts backups to ensure that you have no chance of recovering your files. PrintNightmare, ProxyShell, TrickBot, and Cobalt Strike are some of the tools Conti uses to deploy their ransomware. Researchers believe that Conti is based in Saint Petersburg, Russia.
What Was Leaked?
Over 60,000 of Conti’s leaked chat messages and files were hacked and the internal logs were leaked in an email sent to multiple journalists on February 27, 2022. The conversations date back to January 29, 2021, to the day the chats were leaked. In the emails, the leaker stated that the logs were just the first portion of the Conti files that they plan to release at a later date.
Typically, Russian and Ukrainian hackers work together, but since Conti chose a side, that relationship is starting to change. Since the conflict between Russia and Ukraine, several cyber criminal gangs have chosen sides and have come forward regarding their plans to launch cyber attacks – Conti being one of those gangs.
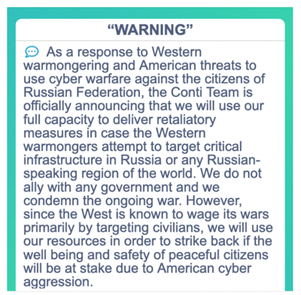
Image 1: Conti's Initial Statement
The initial pro-Russia statement was aggressive and clearly chose a side, however, Conti issued a second statement with a more neutral tone hours later. Unfortunately for Conti, the second statement came too late.
Source: KrebsOnSecurity
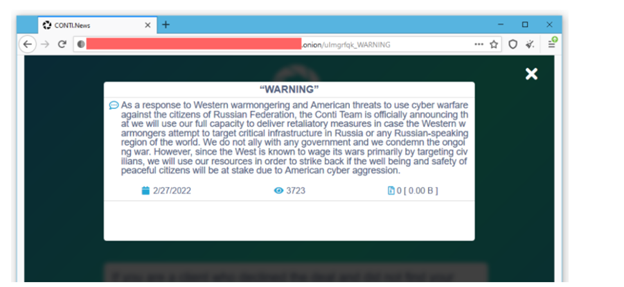
Image 2: Conti's Second Statement
Holding true to their word, the twitter account that posted the first set of Conti’s leaks, posted additional leaks from June 22, 2020, to Nov. 16, 2020.
Source: TheRecord
relationship with trickbot, emotet, & internal breaches
According to KrebsOnSecurity, there are several gaps in the chat logs that correspond with the times Conti’s IT infrastructure was either dismantled or infiltrated by private security firms or law enforcement. Those holes also match up with time periods when the group was trying to re-establish
According to KrebsOnSecurity, there are several gaps in the chat logs that correspond with the times Conti’s IT infrastructure was either dismantled or infiltrated by private security firms or law enforcement. Those holes also match up with time periods when the group was trying to re-establish their network of infected systems and fire bottom-tier staff for security reasons.
The TrickBot botnet (malware that infected computers and spread ransomware) was seized by the U.S National Security Agency (NSA) in September 2022, giving them control over the botnet. Conti has used TrickBot regularly to deploy malware. However, after NSA gained control, the NSA hackers sent all infected systems a command telling them to disconnect themselves from the internet servers that TrickBot operators were using to control compromised Microsoft Windows computers.
In addition, NSA loaded millions of fake records regarding new victims into TrickBot’s database. Just a few hours after TrickBot was compromised, Conti’s leaked chat logs showed that the gang’s leadership noticed something was wrong, stating that whoever was responsible “did it very well” and that the culprit knew how the bot worked. One leader, who went by the name of “Hof” in the chat log, stated that the intruder “somehow encrypted the config, i.e. he had an encoder and a private key, plus uploaded it all to the admin panel. It’s just some kind of sabotage.”
After the compromise, it took Conti months to rebuild their malware infrastructure and continue to infect thousands of new Microsoft Windows systems. During that time, Conti chose 428 healthcare organizations with their ransomware. In October 2020, the FBI and the U.S. Department of Homeland Security had a conference with healthcare industry executives warning them about a cyber crime threat to U.S. hospitals and healthcare organizations/providers. The chat logs also revealed that the TrickBot botnet shut down in early March 2022.
In January 2021, the chat logs corresponded with the international law enforcement’s operation to seize control over Emotet, a malware strain and cyber crime platform used by Conti. According to Conti’s chat logs, after Emotet was taken down by law enforcement, Conti had to reorganize. The takedown was named “Operation Ladybird” and involved authorities from the Netherlands, Germany, the U.S. the United Kingdom, France, Lithuania, Canada, and Ukraine. Emotet was a pay-per-install botnet that deployed the ransomware Ryuk and TrickBot.
Conti’s leaked chat logs showed that they kept tabs on victim bots infected with malware through crimeware platforms, TrickBot and Emotet. During that time, Conti employed people to constantly test, maintain, and expand this infrastructure 7 days a week.
their network of infected systems and fire bottom-tier staff for security reasons.
The TrickBot botnet (malware that infected computers and spread ransomware) was seized by the U.S National Security Agency (NSA) in September 2022, giving them control over the botnet. Conti has used TrickBot regularly to deploy malware. However, after NSA gained control, the NSA hackers sent all infected systems a command telling them to disconnect themselves from the internet servers that TrickBot operators were using to control compromised Microsoft Windows computers.
In addition, NSA loaded millions of fake records regarding new victims into TrickBot’s database. Just a few hours after TrickBot was compromised, Conti’s leaked chat logs showed that the gang’s leadership noticed something was wrong, stating that whoever was responsible “did it very well” and that the culprit knew how the bot worked. One leader, who went by the name of “Hof” in the chat log, stated that the intruder “somehow encrypted the config, i.e. he had an encoder and a private key, plus uploaded it all to the admin panel. It’s just some kind of sabotage.”
After the compromise, it took Conti months to rebuild their malware infrastructure and continue to infect thousands of new Microsoft Windows systems. During that time, Conti chose 428 healthcare organizations with their ransomware. In October 2020, the FBI and the U.S. Department of Homeland Security had a conference with healthcare industry executives warning them about a cyber crime threat to U.S. hospitals and healthcare organizations/providers. The chat logs also revealed that the TrickBot botnet shut down in early March 2022.
In January 2021, the chat logs corresponded with the international law enforcement’s operation to seize control over Emotet, a malware strain and cyber crime platform used by Conti. According to Conti’s chat logs, after Emotet was taken down by law enforcement, Conti had to reorganize. The takedown was named “Operation Ladybird” and involved authorities from the Netherlands, Germany, the U.S. the United Kingdom, France, Lithuania, Canada, and Ukraine. Emotet was a pay-per-install botnet that deployed the ransomware Ryuk and TrickBot.
Conti’s leaked chat logs showed that they kept tabs on victim bots infected with malware through crimeware platforms, TrickBot and Emotet. During that time, Conti employed people to constantly test, maintain, and expand this infrastructure 7 days a week.
Using commercial security services
As counter intuitive as this sounds, Conti actually purchased security and antivirus tools to see how many products detected their malware, as well as for their own security. It was not unusual for upper management to direct a Conti “employee” to quietly check on the activity of network administrators on a weekly basis. This was done to ensure the administrators weren’t doing anything that would jeopardize the integrity or security of their operation. Conti also installed endpoint detection and response (EDR) tools on the administrators’ computers.
“Install EDR on every computer (for example, Sentinel, Cylance, CrowdStrike); set up more complex storage system; protect LSAS dump on all computers; have only 1 active accounts; install latest security updates; install firewall on all networks.” – Reshaev (Conti Upper Manager)
Additionally, Conti budgeted for open-source intelligence tools. They subscribed to various services which help verify who is behind an IP address or if an IP address is tied to a virtual private network (VPN) service. The open-source intelligence tools allowed Conti to abuse commercial services that could help them in ransom negotiations with victims. Conti is known for setting ransom demands based on a percentage of their victim’s annual revenue (hence why they go after organizations with $100 million in revenue or more) and for harassing board members/investors of companies refusing to negotiate or even engage in conversations with Conti.
Also, Conti purchased subscriptions to Zoominfo and Crunchbase Pro because those companies provided detailed information on millions of companies (earning and statements, contact information, etc.). The gang also spent $60,000 on a valid license for Cobalt Strike (a legitimate commercial network penetration testing and reconnaissance tool that’s only given to vetted partners). Unfortunately, it’s common for cyber criminal gangs to purchase a stolen license to help with the installation of their ransomware on a victim’s network. Because a company discreetly purchased the tool on Conti’s behalf, the company was paid $30,000 of the $60,000 Conti invested trying to get the tool.
In addition to using open-source tools, the leaked chats revealed that Conti has an organizational unit called the “Reversers” The unit’s role was to find and exploit new security vulnerabilities in software and cloud-based services, as well as widely used hardware. In July 2021, the unit was ordered to focus on Windows 11, which is Microsoft’s latest operating system.
non-disclosure of breaches + help from third parties
When an organization is breached, it’s in their best interest, and in the best interest of their customers, to inform the masses about the breach. Full disclosure helps to maintain trust between the organization and the public. However, according to Conti’s chat logs, not only was there a journalist being paid by Conti to intimidate their ransomware targets for a cut of the profits (5%), but the targets, also known as businesses, didn’t disclose a breach despite negotiating ransom payments.
In September 2021, Avertium published a Threat Intelligence Report featuring T-Mobile and a data breach that exposed sensitive information of more than 50 million current, past, prospective customers. The breach, which exposed the names, addresses, driver’s licenses, social security numbers, IMEI numbers, and ID information, came to light on August 15, 2021, when hackers claimed to have accessed the data of over 100 million people.
Additionally, Conti had relationships with people who worked at ransomware recovery firms, companies that helped victims navigate how they would pay demanded ransoms in virtual currency. Also, Conti was consistent with targeting companies that had cyber insurance since they were more likely to pay. Companies with cyber insurance are more likely to pay because their insurance covers their losses associated with a ransomware attack. Conti also tried to set up demos with legitimate cyber security companies such as Carbon Black and Sophos to test their tools and discover evasion methods in an attempt to avoid being detected in networks/systems.
The breach was one of the most significant because of the number of records exposed and the regulatory repercussions that could possibly take place. The attacker who was selling the information on a forum asked for 6 bitcoin (about $270,000) for a portion of the data containing 30 million social security numbers and driver’s licenses.
T-Mobile’s breach was significant because they waited until August 16, 2021, before confirming that the breach happened. Customers went an entire 24 hours reading headline after headline from media outlets, without ever hearing a word directly from T-Mobile regarding their compromised information. The only statement T-Mobile gave when the news broke, was to Motherboard, Vice.com’s technology website. They also repeatedly turned down follow-up questions regarding the scale of the attack.
Because of T-Mobile and other companies who wait to inform, Congress began examining a House of Representative bill that included how quickly companies need to report attacks (between 24 or 72 hours), what kind of compromises need to be reported to CISA, and should a fine be implemented if there is non-compliance. Now, there is a law called the Strengthening American Cybersecurity Act, requiring key businesses to report to the government when they’ve been breached. On March 9, 2022, a new rule was proposed by the Securities Exchange Commission that would force publicly traded companies to disclose data breaches and other serious cyber security events within four days.
cryptocurrency payments
Because Conti received ransom payments in bitcoin, the emails addresses associated with those bitcoin payments will help law enforcement track down the threat actor’s profits. Making $180 million last year, Conti is one of the most successful ransomware gangs in the world and are at the top of law enforcement’s list.
A lot of Conti’s money was made via Bitcoin and because they made such a large sum of money, they were able to do things that the typical investor wouldn’t be able to do. The group was able to move the price of cryptocurrency in one direction or the other and built a cryptocurrency platform. Conti’s upper management also discussed creating a crypto currency scheme for cross-platform blockchain applications.
“I’m addicted right now, I’m interested in trading, defi, blockchain, new projects. Big companies have too many secrets that they hold on to, thinking that this is their main value, these patents and data. Like Netherium, Polkadot and Binance smart chain, etc. Does anyone know more about this? Study the above systems, code, principles of work. To build our own, where it will already be possible to plug in NFT, DEFI, DEX and all the new trends that are and will be. For others to create their own coins, exchanges and projects on our system.” – Stern (one of Conti’s top managers)
In December 2021, we published a Threat Intelligence Report discussing how difficult it can be for law enforcement to crack down on cyber criminals due to the different laws surrounding cyber criminal activity in different countries. Typically, ransomware investigations are one and done, then on to the next. However, in the case of ransomware group Cl0p, the 30-month long law enforcement investigation introduces a different era of cyber-criminal investigations – sending the message that cyber criminals are being carefully watched and arrests will happen. In Conti’s case, the bitcoin email addresses are like a bread crumb trail for law enforcement to recoup money.
In October 2021, Conti was involved in SQUID, which is a new cryptocurrency that’s actually a giant social media scam. The scam netted millions of dollars and was a crypto-based pump-and-dump scam. The goal was to use misleading information to inflate the price of currency and sell it for a profit. Conti’s members were quite excited about this and one member stated:
“The big day has arrived,” Ghost wrote. “24 hours remaining until the biggest pump signal of all time! The target this time will be around 400% gains possibly even more. We will be targeting 100 million $ volume. With the bull market being in full effect and volumes being high, the odds of reaching 400% profit will be very high once again. We will do everything in our power to make sure we reach this target, if you have missed our previous big successful pumps, this is also the one you will not want to miss. A massive pump is about to begin in only 24 hours, be prepared.” – Ghost (a Conti member)
Although the above message doesn’t indicate which platform would be targeted, the message does line up with a pump-and-dump executed against the SQUID cryptocurrency. SQUID was initially presented to investors in October 2021.
Image 3: The SQUID Scam
is this the end for conti?
The simple answer is, no. As you can see above, Conti has had to deal with breaches before. Cyber security analysts and researchers have said that Conti is resourceful and will probably rebound from this, despite the leak. However, the chat log leaks will probably cost them a lot of money and it will take them some time to rebuild their reputation.
 Image 4: Conti's Newer Source Code
Image 4: Conti's Newer Source Code
What Conti may not have expected was for their source code to be leaked over the weekend. The same Ukrainian (named Conti Leaks on Twitter) who was responsible for the original leak containing Conti’s old source code, is also responsible for leaking Conti’s newer malware source code.
This version of Conti’s source code was last modified in January 2021 – a year older than the previous source code which dated back to September 2020. The current source code is a Visual Studio solution and allows anyone with access to compile the ransomware locker and decryptor. It can also be easily modified by attackers to use their own public keys. This latest development could have a disastrous impact on organizations because other threat actors could use it to create their own ransomware operations.
How Avertium is Protecting Our CUSTOMERS
Successful threat actors like Conti never go disappear without a fight. As we stated earlier, Conti has been known to suffer breaches and bounce back. If they are raking in millions of dollars from their ransomware operation, it is not likely that they will easily cease all activity and wave the white flag. It’s important for organizations to remain vigilant despite Conti’s recent breach. Avertium offers the following services to help keep your organization safe from Conti and safe from other threat actors attempting to use Conti’s leaked source code for their own ransomware operations:
- Avertium offers vulnerability management as a service (VMaaS) to remove any unnecessary applications and implementing XDR tools to prevent ransomware and phishing attacks.
- It’s also recommended by Avertium and the FBI that your business require multi-factor authentication to remotely access networks. Implementing network segmentation and filtering network traffic to stop phishing emails from reaching victims is also helpful. Recommendations from Avertium and our partner, Advanced Intelligence:
- Conti uses developed social engineering techniques to lure victims. Avertium offers user awareness training with KnowBe4.
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. Use whitelisting tools to audit or block command-line interpreters (AppLocker).
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a cryptomining malware attack. This service is provided as an on-demand crisis response service, as well as retainer-based program.
Avertium’s Recommendations
- Rclone and other data exfiltration command-line interface activities can be captured through correct logging of process execution with command-line arguments.
- Have security protocol in place for Veeam to avoid account takeover. Enabled backups decrease Conti’s ransom demands and can lead to data recovery without you having to pay them.
- Prevent lateral movement by implementing network hierarchy protocols with network segregation and decentralization.
Indicators of Compromise (IoCs)
- 0737ebb6ede108d90216bc06ccfce57defa2179bfda93a34edd868a6f9172a78 (associated with newer leaked sourced code)
- fb49dce92f9a028a1da3045f705a574f3c1997fe947e2c69699b17f07e5a552b
- 3d3308249c9678add3a18400dee765e1
- 6237d6565ebde559310120a80567e016
- ed475bccfcbe008930aa837a8effd7a9
- 0aebd55ec0cb8ff6e7f5a853c68f9948f4ed824e
- ac2785ef856f0a6a93a68d4c6f45fc87ff7bb530
- bf8a4f936ea526547304941b071a893c26c4fc8b
- 5f3ae6e0d2e118ed31e7c38b652f4e59f5d5745398596c8b31248eda059778af
- e1b147aa2efa6849743f570a3aca8390faf4b90aed490a5682816dd9ef10e473
- fb737da1b74e8c84e6d8bd7f2d879603c27790e290c04a21e00fbde5ed86eee3
- 106.160[.]77
- 106.215[.]61
- 82.19[.]173
- Gojihu[.com]
- Sazoya[.com]
- Yawero[.com]
- Suhuwow[.com]
- Mihojip[.com]
- Hewecas[.com]
- Balacif[.com]
- Wuvehus[.com]
- Codasal[com]
- Xekezix[.com]
- Conti uses remote access tools that beacon to domestic and international VPS infrastructure over ports 80, 443, 8080, and 8443.
- Conti may use port 53 for persistence.
- New accounts and tools (especially Sysinternals) that were not installed by your organization.
- Disabled endpoint detection and constant HTTP and DNS beacons.
Supporting Documentation
TIR-20211004 An In-Depth Look at Ransomware Gang, Conti (avertium.com)
Conti ransomware gang chats leaked by pro-Ukraine member - The Record by Recorded Future
International Action Targets Emotet Crimeware – Krebs on Security
Clop Ransomware (TIR-20210419) (avertium.com)
More Conti ransomware source code leaked on Twitter out of revenge (bleepingcomputer.com)
To strengthen American cybersecurity, we need clear incident reporting rules | Fortune
Conti Ransomware Group Diaries, Part IV: Cryptocrime - Security Boulevard
Conti Ransomware Group Diaries, Part IV: Cryptocrime – Krebs on Security
TIR – 20210920 T-Mobile and BlackBerry - Why Waiting to Inform May Cost You (avertium.com)
Conti Ransomware Group Diaries, Part II: The Office – Krebs on Security
Attacks Aimed at Disrupting the Trickbot Botnet – Krebs on Security
Conti Ransomware Group Diaries, Part III: Weaponry – Krebs on Security
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: [Threat Report] An In-Depth Look at the Kraken Botnet