An In-depth Look at the Kraken Botnet
Executive Summary of the kraken botnet
A recently discovered botnet named Kraken is under active development and is stealing data from Windows hosts. Kraken has been active since October 2021 and was discovered by ZeroFox Intelligence. The botnet is known for its simple functionality but has already started turning a $3k monthly profit for its owners. According to ZeroFox, Kraken is trying to rebrand and find its place within the threat landscape. Between January 4, 2022, and January 7, 2022, the operators behind Kraken began using names “Anubis” and “Pepega” internally. However, the name Kraken is still being used by cyber security professionals and by media outlets.
Ever-shifting, botnets have proven just how dangerous they can be within the last few months. From Meris to Qakbot, botnets can spread through machines quickly and easily take down an entire organization before the attack is noticed. Let’s take a look at Kraken and how you can keep your organization from becoming a victim of this newly developed botnet.
what is a botnet?
A botnet, which is short for robot network, is a group of computers that have been infected with malware. The botnets are under the control of threat actors that can command every computer on their botnet to carry out coordinated attacks. Sometimes botnets are massive, comprised of millions of bots. The scale of a botnet can allow attackers to perform large scale attacks that were impossible with malware alone.
How Do They Work?
The purpose of a botnet is to speed up a threat actor’s ability to carry out large attacks. At little cost to them, threat actors can acquire thousands of machines to use in their attacks. Bot herders (threat actors) are at the head of the operation and compile bots, while using command programming to drive their next actions. Bots operate under remote commands designed by their bot herder. Here are the basic stages of building a botnet:
- Prep and Expose — attacker exploits a vulnerability to expose users to malware.
- Infect — user devices are infected with malware that can take control of their device.
- Activate — attackers mobilize infected devices to carry out attacks.
Under the control of the threat actors, targeted machines can change their behavior at any moment and can receive updates. Because of the botnet’s ability to change quickly, threat actors will often rent access to segments of their botnet to other cyber criminals on the black market.
Bot herders send bots from their command and control severs to unknowing recipients via malicious file sharing, email, or social media application protocols. When an unknowing victim opens the malicious file, the bot sends a message back to command and control (C2). Next, the threat actor dictates commands to infected computers.
Botnets are one of the most sophisticated types of modern malware and are a significant concern for organizations. Leveraging networks to gain power and resilience, botnets expose organizations to breaches, DDoS attacks, email spam, and targeted intrusions.
the kraken botnet
As previously stated, Kraken was unknown until ZeroFox discovered it in October 2021. Keep in mind, this new botnet is not to be confused with the Kraken botnet from 2008, as they don’t have much in common. Kraken uses SmokeLoader, a multi-use hacking tool, to install malicious software on targeted machines and picks up hundreds of new bots every time a new C2 server is deployed. The botnet is still under development but already has the ability to exfiltrate sensitive data from Windows hosts. According to ZeroFox, current iterations of Kraken feature the following abilities:
- Maintain persistence
- Collect information about the host for registration (varies per version)
- Download and execute files
- Run shell commands
- Steal various cryptocurrency wallets
- Take screenshots
In October 2021, Kraken’s code, which is written in Go, was uploaded to GitHub, but the project only had two commits and the source code pre-dated any binaries ZeroFox observed in the wild. The GitHub profile’s owner is unknown, so it isn’t clear if the profile belongs to Kraken’s operators or if the operator used the code to kickstart their development.
How Kraken Spreads and Infects
Originally, Kraken spread in self-extracting RAR SFX files via SmokeLoader downloads. The SFX included a UPX-packed version of Kraken called RedLine Stealer, as well as another binary used to delete Kraken. Today, Kraken is downloaded by SmokeLoader directly and the botnet’s binaries are UPX-packed but are protected by the Themida packer as well.
According to the Department of Justice, the data was given to China to aid in securing contracts for state-owned enterprises within targeted countries, resulting in better contract bids for Chinese companies and gaining an edge on competitors. Hainan Xiandun was used in collaboration with Bronze Mohawk (APT40) and university staff to recruit hackers and linguists from the universities’ ranks to assist in potential intrusions.
Windows
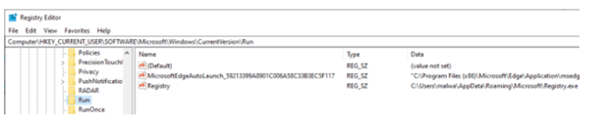
Kraken runs two commands to stay hidden: 1. Powershell -Command Add-MpPreference -ExclusionPath %APPDATA%Microsoft and 2. Attrib +S +H %APPDATA%\Microsoft\<EXE_NAME>. Microsoft Defender receives a message from the PowerShell command which tells it not to scan Kraken’s installation directly. The attributed command hides the copied EXE file from a Windows Explorer window that hasn’t enabled the option, “Show hidden files, folders, and drives.” Also, every time a victim logs in, Kraken ensures the Windows Run registry key starts.
Image 1: Run Key Persistence
Source: ZeroFox.com
Although Kraken’s features are simple, they are mighty. Kraken can collect information about their infected host and send it back to the C2 sever during registration. Although the information Kraken collects varies from build to build, here is some of information ZeroFox observed the botnet collecting:
- Hostname
- Username
- Build ID (TEST_Build_ + the timestamp of the first run)
- CPU details
- GPU details
- Operating system and version
Unlike earlier versions, Kraken now has the ability to download and execute files. From the dashboard, Kraken’s operators are able to run shell commands and return the results back to the C2 server. After execution, the botnet takes a screenshot and sends it to the command and control. Additionally, Kraken has the ability to steal various cryptocurrency wallets from different locations. Those locations include:
- %AppData%\Zcash
- %AppData%\Armory
- %AppData%\bytecoin
- %AppData%\Electrum\wallets
- %AppData%\Ethereum\keystore
- %AppData%\Exodus\exodus.wallet
- %AppData%\Guarda\Local Storage\leveldb
- %AppData%\atomic\Local Storage\leveldb
- %AppData%\com.liberty.jaxx\IndexedDB\file__0.indexeddb.leveldb
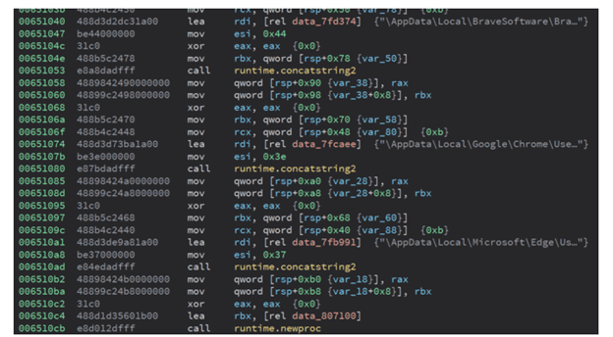
In February 2022, Kraken’s C2 panel was redesigned and was named Anubis. The panel provides the threat actors with more information than the original Kraken panel. It’s now possible for Kraken’s operators to view command history and information about their victim. Additionally, the Anubis panel targets specific Chromium-based browsers (Brave, Google Chrome, and Microsoft Edge). Kraken deploys generic information stealers and cryptocurrency miners.
Image 2: Cryptomining Statistics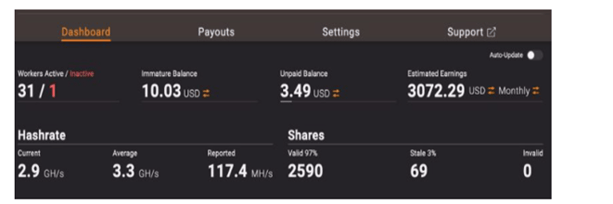
Source: ZeroFox Intelligence
Image 3: Chromium Based Web Browser Paths
As we stated earlier, Kraken is still in development and its C2s disappear often. There has been dwindling activity for severs on several occasions, but another appears later using either a new port or a new IP address. Spread by SmokeLoader, Kraken is able to gain hundreds of new bots each time the C2 changes. The operator behind Kraken has pushed information stealers (particularly RedLine Stealer via Anubis) from October 2021 to December 2021. Kraken used to rely solely on secondary payloads like RedLine Stealer to steal data from victims, but researchers expect for Kraken to end its reliance on third-party information stealers if it continues to add new features. Researchers are not sure what the ultimate goal is for creating Kraken or what the operators plan to do with the stolen information. If Kraken currently pulls in USD $3,000 per month for its operators, then some might say the operators’ goal is financial.
botnet trends 2022
In October 2021, Avertium published a report featuring the Meris botnet. The botnet was responsible for attacking Cloudfare, Yandex, and KrebsOnSecurity via DDoS attacks. It also targeted customers in the financial industry and exploited an unpatched vulnerability (CVE-2018-14847) within MikroTik routers from 2018. The attackers behind Meris had the ability to execute a much larger attack, but they chose not to at that time. In March 2022, the Meris botnet played a key role in a massive DDoS attack on an undisclosed website. The threat actors behind the attack included a ransom note as part of the attack itself. Researchers believe it was a reminder to send their bitcoin payment.
Also, the Qakbot botnet has been seen spreading through email thread hijacking. Email thread hijacking happens when malware operators malspam replies to ongoing email threads – with victims not realizing the replies are not from the human who owns the email box where the replies originated. In March 2022, our partner, Sophos, published a detailed report about the botnet and its capabilities. Qakbot’s main goal is to steal logins and passwords for malicious reasons. It’s also capable of spying on financial operations and installing ransomware, making the botnet multipurpose.
Botnets, like TrickBot can be used as initial access points for ransomware. TrickBot was initially a banking trojan designed to steal financial data but has since evolved into a modular stealer – targeting a wide range of information. It has been used often by the ransomware gang, Conti, and is one of the reasons why Conti was able to rise so quickly. At one point, Conti became the only end-user of TrickBot’s botnet product, ultimately leading TrickBot to be acquired by Conti at the end of 2021. TrickBot is still operational, but the malware has reached its maximum value.
Most of the IoCs associated with TrickBot are not used by Conti because of how easy they are to detect. However, the developers and managers behind TrickBot are still valuable to Conti.
Because botnets have become a fixture within the threat landscape and are starting to shift their focus from DDoS attacks, it’s important to recognize that they evolve quickly and use newer attack techniques. Unlike Meris, Kraken has steered clear of using a DDoS attack and has other means of attacking its victims – choosing to steal information via RedLine Stealer from infected machines. In September 2021 and October 2021, Security Week saw an increase in RedLine Stealer malware, particularly in the Middle East and in Europe. RedLine Stealer isn’t a new tool and the developers behind it regularly change the malware to find new victims, with its latest variant named “Omicron Stats.exe.”
The above is a testament to how botnets are growing in sophistication and how threat actors leverage several attack techniques to accomplish their malicious goals. Law enforcement and security professionals have been successful in taking down botnets, but the success is often short lived. In April 2021, Emotet was taken down by law enforcement and was a major win for the cyber security world, but the victory was short lived when the botnet returned in November 2021.
If you think your organization can wait to protect itself from botnets like Kraken, you’re mistaken. We have already seen some of the most vicious cyber attacks this year and a holistic, yet integrated security approach is the best protection against botnets. Additionally, ensuring that your organization takes a security-first approach when adopting new technologies, will help keep networks safe. Don’t put off securing your environment, it takes one threat to cripple an organization.
How Avertium is Protecting Our CUSTOMERS
- MDR provides an in-depth investigation into potential threats on an organization’s network. Avertium’s risk-based approach to managed security delivers the right combination of technology, field-validated threat intelligence, and resource empowerment to reduce complexity, streamline operations, and enhance cybersecurity resilience. If you need a more advanced security solution, MDR is the next step.
- Penetration testing will help your employees understand malware and will help prevent attacks. It’s easier for an organization to avoid malware if employees understand the “what” and “why” behind it.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium offers Zero Trust Network as a Service (ZTNaaS) for any organization that wants to control their attack surface. The zero-trust security model delivers exactly what the name promises: it's an IT security concept that specifies no access is allowed until the successful completion of authentication and authorization processes.
Avertium’s Recommendations
- Don’t open attachments or click on links from senders you don’t recognize.
- Regularly check schedule backup routines – this includes integrity checks and/or offsite storage.
- Antivirus and intrusion detection software should be up to date and patched.
- Two-factor authentication should be enabled for all organizational accounts to help mitigate phishing and credential stuffing attacks.
- Log all admin actions and alt on place an alert of any suspicious activity.
- Ensure that your employees are aware of what botnets could look like and how to avoid any links that may be hazardous.
- Check that your partners and supply chain are equipped with cybersecurity so that you are not a victim of a breach within their networks.
- Work with the right Managed Security Service Provider (MSSP) that is able to consistently monitor and combat vulnerabilities in your attack surface.
MITRE TTPS
- [T1033] System Owner/User Discovery
- [T1047] Windows Management Instrumentation
- [002] Obfuscated Files or Information: Software Packaging
- [T1113] Screen Capture
- [T1571] Non-Standard Port
- [001] Command and Scripting Interpreter: PowerShell
Indicators of Compromise (IoCs)
- 21.105[.85]
- 206.14.[151]
- 181.152[.184]
- 112.83[.22]
- 112.83[.96]
- 206.212[.165]
- 226.71[.125]
- 5d99125b0d97ba0abfcf9916c1a05081c1cc117eb2afaaab39a6f95a60e42ab3
- 1d772f707ce74473996c377477ad718bba495fe7cd022d5b802aaf32c853f115
- d742a33692a77f5caef5ea175957c98b56c2dc255144784ad3bade0a0d50d088
- ddf039c3d6395139fd7f31b0a796a444f385c582ca978779aae7314b19940812
- dcaaef3509bc75155789058d79f025f14166386cec833c2c154ca34cfea26c52
- 54d36e5dce2e546070dc0571c8b3e166d6df62296fa0609a325ace23b7105335
- 095c223b94656622c81cb9386aefa59e168756c3e200457e98c00b609e0bb170
- 0f0cabb24d8cc93e5aed340cfc492c4008509f1e84311d61721a4375260a0911
- 2ced68e4425d31cca494557c29a76dfc3081f594ff01549e41d2f8a08923ef61
- 3215decffc40b3257ebeb9b6e5c81c45e298a020f33ef90c9418c153c6071b36
- ef3e0845b289f1d3b5b234b0507c554dfdd23a5b77f36d433489129ea722c6bb
- 7c76ca5eb757df4362fabb8cff1deaa92ebc31a17786c89bde55bc53ada43864
- 48c2f53f1eeb669fadb3eec46f7f3d4572e819c7bb2d39f22d22713a30cc1846
- 43f46a66c821e143d77f9311b24314b5c5eeccfedbb3fbf1cd484c9e4f537a5d
- 8c4294e3154675cd926ab6b772dbbe0e7a49cae16f4a37d908e1ca6748251c43
Supporting Documentation
Baby Golang-Based Botnet Already Pulling in $3K/Month for Operators | Threatpost
What is a Botnet? - Palo Alto Networks
Move over Storm - there's a bigger, stealthier botnet in town • The Register
TIR-20211011 DDoS Attacks & The Meris Botnet (avertium.com)
RaaS gangs, Drive-By Downloads, and Botnets - Are You a Target? (avertium.com)
Quick Update: Kraken Completes Its Rebrand to Anubis | ZeroFox
All About the Bots: What Botnet Trends Portend for Security Pros | SecurityWeek.Com
What is a Botnet? (kaspersky.com)
Conti Ransomware 'Acquires' TrickBot as It Thrives Amid Crackdowns | SecurityWeek.Com
Qakbot injects itself into the middle of your conversations – Sophos News
Dayslong DDoS Attack With Embedded Ransom Note Mitigated (bankinfosecurity.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.

CHECK OUT OUR LATEST EBOOK >>>
In this eBook, you will learn...
- The newest and growing trends in cybersecurity tools, processes, and data storage
- Expectations for what cybersecurity will look like in 2022, based on data collections & observations from Avertium security experts, plus commentary from Avertium's partners