An In-Depth Look at Quantum Ransomware
Executive Summary
As long as there is money to be made, ransomware will continue to be a global issue for organizations. Recently, Sophos published a report regarding the state of ransomware for 2022. The company conducted an independent, vendor-agnostic survey of 5,600 IT professionals in mid-sized organizations (including 381 healthcare respondents) across 31 countries. The report revealed that 66% of the healthcare organizations surveyed were compromised by ransomware in the last year – 34% more than 2020. This data means that there was a 94% increase in healthcare ransomware attacks over the course of one year.
Threat actors are becoming more strategic and more capable of executing ransomware attacks at scale. The uptick in ransomware attacks is more than likely due to the continued success of the RaaS model. Quantum ransomware is a newer, lesser-known ransomware that operates with the RaaS model and has been very successful with compromising healthcare organizations.
In the past, threat actors tried to steer clear of attacking the healthcare sector but lately, attackers have dismissed all ethics and morals and are going full force with attacks. Now that threat actors like those behind Quantum ransomware know how vulnerable healthcare organizations are, we can expect many more ransomware attacks for the sector. Let’s take a look at Quantum ransomware, their recent attacks, and why social engineering and phishing are a major threat for healthcare organizations.

quantum ransomware
Discovered in August 2021, Quantum ransomware is linked to the Quantum Locker operation. Quantum Locker has had a few rebrands (AstroLocker, MountLocker, and XingLocker). Our technology partner, AdvIntel, confirmed that Quantum is a splinter group from Conti and that the ransomware operation was taken over by Conti Team Two in April 2022 – keeping Quantum’s original name.
In June 2022, Quantum was observed employing their version of BazarCall, called Jormungandr, and hiring people who specialized in OSINT, spamming, design, and call center operations. BazarCall is a method that is also known as call-back phishing. This tactic emerged in early 2021 as an attack vector used by Ryuk ransomware (later evolving into Conti).
BazarCall is used to gain initial access into a victim’s network and involves emailing victims. The emails allege that a paid subscription is up for automatic renewal, but the renewal can be cancelled if the victim calls a specific number. Once the victim calls the number, the threat actor on the other end of the line convinces the victim via social engineering to start a remote access session by the use of legitimate software controlled by a network intruder.
While the victim is distracted on the call, the intruder tries to figure out how to compromise the victim’s network without triggering alarms. These kinds of attacks are highly targeted and make it difficult for cyber security professionals to detect due to the social engineering aspect of the attack. AdvIntel believes that the switch to social engineering is more than likely due to the predictability of ransomware attacks, causing profits to decline for adversaries. If threat actors like Quantum are able to trick people, they can have a more flexible approach to their attacks – making them difficult to defend.
Quantum’s BazarCall campaigns have grown more sophisticated in just two months’ time. They’ve impersonated a large number of brands, including:
- Gobble
- Luchechko Mortgage Team
- CrowdStrike
- HelloFresh
- Oracle
- Ginyard International
- US Equal Opportunity Employment Commission
When Quantum initially emerged, they experimented with BazarCall emails and impersonated Oracle. They delivered phishing emails to more than 200,000 people with the below email language.
Image 1: Fake CrowdStrike Email
Source: AdvIntel
Using the same method, Quantum was observed in another phishing operation where they impersonated the Luchechko brand. The threat actors sent a message regarding the company discriminating against an individual based on their ethnicity. Quantum chose Luchechko due to the company being Eastern European, therefore, the victim wouldn’t be suspicious of the threat actor’s accent.
In July 2022, Quantum successfully locked up the network of a New Jersey healthcare system. They exfiltrated data from the organization and demanded $500,000 in ransom in exchange for the data’s return. The healthcare organization is a private, statewide, non-profit behavioral healthcare organization that specializes in treating developmental disabilities and other health conditions.
Additionally, prior to attacking the healthcare organization in New Jersey, Quantum was responsible for attacking Interim Healthcare in July 2022, as well as a research-based biopharmaceutical company in June 2022. Quantum also attacked an IVF clinic based in Delhi, India. The clinic provides IVF and fertility treatments by using cutting edge technology.
tactics and techniques
As previously stated, Quantum is a merger between Quantum Locker and several members of Conti’s former pentesting group called Conti Team Two. According to AdvIntel, when Conti dissolved, members of the group decided to distance themselves from the toxic Conti brand. The two largest divisions of Conti created their own collectives – Team Two created the current version of Quantum, while Team One created Royal Zeon.
Quantum’s Jormungandr campaign is a major development that Quantum has been preparing for since June 2022. The phishing campaign is a derivative of BazarCall, and initial access is achieved by utilizing IcedID for reconnaissance tasks, as well as persistence. The DFIR Report published a case summary in April 2022 that showed the threat actors entering a victim’s network when a user endpoint was compromised by an IcedID payload contained within an ISO image, likely delivered via email.
According to the DFIR Report, the ISO contained IcedID malware and a LNK shortcut to execute it. After the initial IcedID payload was executed, it only took 2 hours after initial infection for Quantum to begin hands-on-keyboard activity. They then quickly deployed Cobalt Strike and RDP to move across the network before using WMI and PsExec to deploy the Quantum ransomware.
Image 2: IcedID and Cobalt Strike
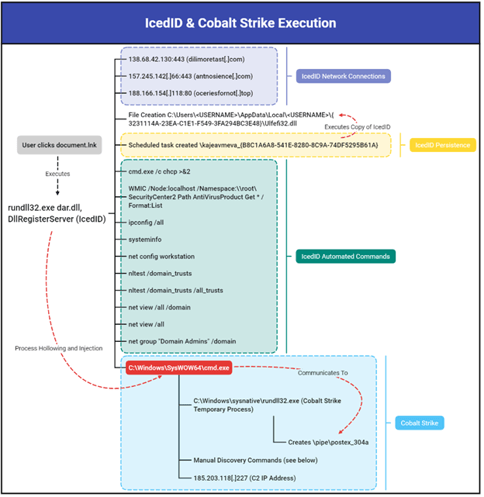
Source: The DFIR Report
According to Avertium’s Cyber Threat Intelligence Team, ISO file types are a common way of grouping files together, but unlike zipped files, ISO files are mountable, allowing the user to attach the file like a virtual CD and access the files. This also lends itself to malware delivery quite well. In this case docs_invoice_173.iso contained two files, a hidden DLL file, and a LNK file made to look like a document.
Image 3: LINK File Masquerading as a Document
Source: Avertium's Cyber Threat Intelligence Team
Image 4: LINK File
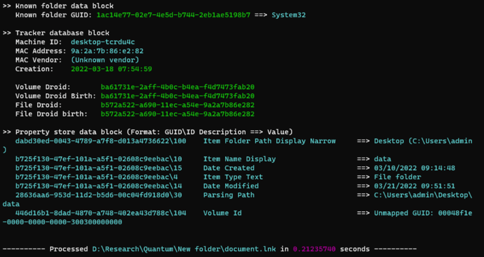
Source: Avertium's Cyber Threat Intelligence Team
Once Quantum gains initial access, Cobalt Strike is injected into the cmd.exe process. AdFind is abused by the threat actors and helps them map out the active directory structure and abuse nslookup to gather network information from hosts. Credentials are then extracted from LSASS memory and tested using WMI discovery.
Next, Quantum copies the ransomware payload, ttsel.exe, followed by the dropping of the ransom note into each infected host with the file name “README_TO_DECRYPT.html”. The ransom note contains a portal to reach out and contact the threat actors for negotiation purposes. Quantum achieves persistence by encrypting files and folders on their victim’s machine. The threat actor’s demanded ransom ranges between $150k and $200k but have been higher for some organizations. The whole process takes less than 4 hours – a very short time-to-ransom.
Image 5: Ransom Note

Source: The DFIR Report
social engineering and phishing
In October 2021, Avertium’s Cyber Threat Intelligence Team published a Threat Intelligence Report regarding the healthcare industry and why the industry is constantly at risk for security incidents. The industry is two to three times more likely to be a target for cybercrime than any other industry. Some ransomware gangs try not to focus on attacking healthcare facilities, but Quantum is not one of those groups.
Quantum’s use of social engineering is quite disturbing because it’s difficult to track. By using social engineering and pretending to be legitimate organizations, Quantum has been able to breach and ransom several high-profile organizations. Social engineering is a major threat to the healthcare sector because healthcare organizations house sensitive information for patients (dates of birth, social security numbers, addresses, etc.).
According to Avertium’s blog on phishing, phishing attacks are often a vessel to deliver malware that masquerades as a communication from a trusted or reputable source. Although Quantum now uses call-back phishing, they have also used email phishing in their social engineering attacks.
Phishing attacks can come in the form of an email, a phone call, or a text message (smishing) – with the most common vehicle being through email. A phishing attack email typically looks or sounds like it’s from a company or someone within your organization. The threat actor behind the attack will ask for privileged information’s or provide a link to an attachment which results in you downloading something malicious.
Social engineering is included in all kinds of phishing attacks and involves threat actors researching companies or individuals prior to the attack. The goal is to get the victim to trust the threat actor by providing a lot of convincing information about the victim – something Quantum seems to have mastered. Quantum takes advantage of core human psychology to manipulate people into doing exactly what they want.
If threat actors like Quantum are able to successfully breach healthcare organizations via social engineering, they will be able to gain access to data that could cripple an organization. Clinics, hospitals, and healthcare systems possess a high volume of patient and employee information. The information could be used for a verity of illicit activities including financial fraud and for other activities within Quantum’s social engineering campaigns.
How Avertium is Protecting Our CUSTOMERS
It’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. Avertium offers the following services to keep your organization safe:
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium’s offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills.
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Avertium offers user awareness training through KnowBe4. The service also Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
Avertium’s Recommendations
Avertium and AdvIntel recommend the following to mitigate Quantum ransomware:
- Quantum utilizes data encryption as a part of its ransomware locker. Organizations should implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and severs in a separate, segmented, and secure location.
- Organizations should implement network segmentation and have offline backups of data.
- Back up data regularly and password protect backup copies offline. Copies of critical data should not be accessible for modification or deletion from the system where data resides.
- Organizations should emphasize network investigation tools that are used for exfiltration-centric groups (Cobalt Strike, Metasploit, and customized PowerShell Commands.
- Track abnormal signaling to assist in identifying beacons.
- The BazarCall attack vector relies on the execution of a beacon or malicious payload into the network system, which is liable to spread to other devices on the network. Separating the device while mitigating the BazarCall breach minimizes the chance that the infection will be able to affect other devices.
- To identify Cobalt Strike, examine the network traffic using TLS inspection, then isolate bot traffic and identify the suspicious traffic by examining data within HTTPS requests.
- Network Based Security Practices
- Use and maintain anti-virus software and a firewall.
- Regularly scan for spyware.
- Keep software up to date.
- Evaluate your software settings.
- Avoid unused software programs.
- Establish guidelines for computer use.
- Encrypt sensitive files.
- Dispose of sensitive information properly.
- Physical Security Practices
- Password-protect all computers.
- Consider using physical locks on devices with sensitive information.
- Consider an alarm or lock.
- Implement physical access control plans.
MITRE Map
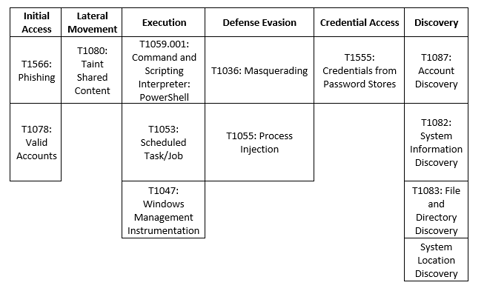
Indicators of Compromise (IoCs)
Files
- docs_invoice_173[.iso]
- e051009b12b37c7ee16e810c135f1fef
- 415b27cd03d3d701a202924c26d25410ea0974d7
- 5bc00ad792d4ddac7d8568f98a717caff9d5ef389ed355a15b892cc10ab2887b
- Dar[.dll]
- 4a6ceabb2ce1b486398c254a5503b792
- 08a1c43bd1c63bbea864133d2923755aa2f74440
- 4a76a28498b7f391cdc2be73124b4225497232540247ca3662abd9ab2210be36
- Document[.lnk]
- adf0907a6114c2b55349c08251efdf50
- aa25ae2f9dbe514169f4526ef4a61c1feeb1386a
- 3bb2f8c2d2d1c8da2a2051bd9621099689c5cd0a6b12aa8cb5739759e843e5e6
- Adf[.bat ]
- ebf6f4683d8392add3ef32de1edf29c4
- 444c704afe4ee33d335bbdfae79b58aba077d10d
- 2c2513e17a23676495f793584d7165900130ed4e8cccf72d9d20078e27770e04
- Ulfefi32[.dll ]
- 49513b3b8809312d34bb09bd9ea3eb46
- 445294080bf3f58e9aaa3c9bcf1f346bc9b1eccb
- 6f6f71fa3a83da86d2aba79c92664d335acb9d581646fa6e30c35e76cf61cbb7
- License[.dat]
- e9ad8fae2dd8f9d12e709af20d9aefad
- db7d1545c3c7e60235700af672c1d20175b380cd
- 84f016ece77ddd7d611ffc0cbb2ce24184aeee3a2fdbb9d44d0837bc533ba238
- Ttsel[.exe]
- b1eff4fffe66753e5f4265bc5332f72e
- da2caf36b52d81a0d983407ab143bef8df119b8d
- b6c11d4a4af4ad4919b1063184ee4fe86a5b4b2b50b53b4e9b9cc282a185afda
- p227[.dll ]
- 350f82de99b8696fea6e189fcd4ca454
- deea45010006c8bde12a800d73475a5824ca2e6f
- c140ae0ae0d71c2ebaf956c92595560e8883a99a3f347dfab2a886a8fb00d4d3
IcedID
- dilimoretast[.]com
- antnosience[.]com
- oceriesfornot[.]top
- 138[.]68.42.130:443
- 157[.]245.142.66:443
- 188[.]166.154.118:8
Cobalt Strike
- C2/IP: 185.203.118[.]227:443
- Watermark: 305419776
Network Detections
- ET MALWARE Observed Malicious SSL Cert (Fake Gmail Self Signed - Possible Cobalt Stirke)
- ET POLICY SMB2 NT Create AndX Request For an Executable File In a Temp Directory
- ET MALWARE Win32/IcedID Request Cookie
- ET POLICY PE EXE or DLL Windows file download HTTP
- ET POLICY PsExec service created
- ET RPC DCERPC SVCCTL - Remote Service Control Manager Access
- ET POLICY SMB2 NT Create AndX Request For an Executable File
- ET DNS Query to a *.top domain - Likely Hostile
- ET INFO HTTP Request to a *.top domain
Supporting Documentation
The State of Ransomware in 2022 | BlackFog
Quantum Ransomware | Cyborg Security
Hackers impersonate cybersecurity firms in callback phishing attacks (bleepingcomputer.com)
sophos-state-of-ransomware-healthcare-2022-wp.pdf
Ransomware gangs move to 'callback' social engineering attacks (bleepingcomputer.com)
Quantum Ransomware – The DFIR Report
Social Engineering Attacks - Check Point Software
The Top 5 Cyber Threats Within the Education Sector (avertium.com)
Quantum ransomware gang: fast and furious | Cybernews
Cybereason vs. Quantum Locker Ransomware
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
