The Top 5 Cyber Threats Within the Education Sector
Executive Summary
During recent years, the InfoSec community has seen an onslaught of cyber threats and attacks within the education sector, particularly higher education. These attacks happen for several reasons, but the primary reason is lack of resources and lack of budget for legitimate security insurance.
Even though education institutions have had to face major challenges such as the ramifications of the pandemic, lack of funding, and lack of staff, cyber threats and attacks won’t exclude them. Recently, ransomware in particular has become an issue in the education sector and some schools have had to shut down and rebuild systems due to ransomware attacks – attacks that compromise student safety.
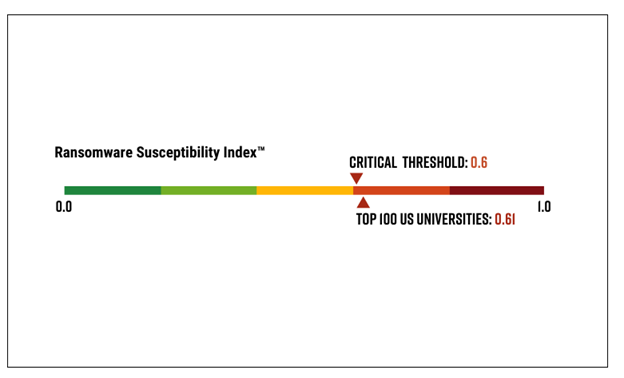
This year, Avertium’s technology partner, Black Kite conducted research on the top 100 universities in the U.S., using a technical rating system from A to F. None of the schools had an A rating and all of the schools were extremely vulnerable to cyber attacks. Let’s take a look at the top five cyber threats within higher education, how ransomware is taking center stage, and what the education sector can do to prevent devastating cyber attacks from happening.

ransomware
Ransomware is the number one threat and attack vector for colleges and universities. Once ransomware is deployed on a network or system, it prevents victims from accessing the network or files, causing disruption. Attackers will also keep the files in exchange for a ransom payment, leaking the files on a data leak site if the ransom is not paid.
During the first few months of the COVID-19 pandemic in 2020, the creation of new ransomware samples increased by 72% - coming in the form of infected file downloads and malicious emails. Although unprepared, colleges were not excluded from the surge in ransomware attacks, especially as most colleges and universities put a stop to in-person learning at the beginning of the pandemic.
With universities and colleges having to rely on virtual learning, technical resources were burdened. In 2020, the National Cyber Security Centre in the United Kingdom warned that the education sector was being targeted with ransomware attacks. Colleges, universities, as well as K-12 school districts were being bombarded with ransomware attacks.
In September 2020, the Clark County school district in Las Vegas, Nevada, fell victim to a ransomware attack that locked up their files. The school serves 320,000 students and the attack involved current and former employee information. The district had to hire third-party forensic investigators to look into the attack and figure out how to restore their systems. Once the attackers realized that the school officials were not going to pay the demanded ransom, they published documents containing student grades, Social Security numbers, and other private information.
BLACK KITE RESEARCH - TOP 100 COLLEGES AND UNIVERSITIES
Colleges and Universities have suffered their fair share of ransomware attacks. On May 13, 2022, Lincoln College in Illinois, had to close their doors after serving students for 157 years, partly due to a ransomware attack. The attack took place in December 2021 after the college was already battling financial issues due to the COVID-19 pandemic.
According to Lincoln College, the ransomware attack hindered the school’s access to institutional data and prevented admissions activities, making it impossible to see a clear picture of Fall 2022’s enrollment projections. Although no personal identifiable information was exposed, the systems required for retention, fundraising, and recruitment were inoperable. Once the systems were restored in March 2022, it was too late. The projections for Fall 2022 showed significant enrollment shortfalls. If the college wanted to remain open, it would require an enormous donation or a transformational partnership.
“Lincoln College has been serving students from across the globe for more than 157 years. The loss of history, careers, and a community of students and alumni is immense.” - David Gerlach, president of Lincoln College.
Quacquarelli Symonds’ research for Black Kite showed that since January 4, 2022, 15 colleges and universities fell victim to ransomware attacks. Those colleges include:
- Butler Community College
- Summit College – alleged ransomware attack on 1/4/2022
- Lewis-Clark State College
- University of Detroit Mercy - alleged ransomware attack by LockBit, on 2/4/2022
- Centralia College – alleged ransomware attack on 2/15/2022
- North Carolina A&T - alleged ransomware attack by AlphaVM, on 4/6/2022
- Austin Peay State University – alleged ransomware attack on 4/27/2022
- College of Coastal Georgia
LockBit ransomware group was mentioned more than once on Black Kite’s list (some schools were not mentioned intentionally). Their attack on the University of Detroit Mercy affected the school’s servers and the group stole sensitive information (the kind of information was not disclosed). LockBit’s ransomware note stated that if the university didn’t comply with their ransom demands by February 1, 2022, the school’s information would be leaked on the dark web. There were no details released regarding how much LockBit was asking for or if the University of Detroit Mercy was in negotiations with the group.
AlphaVM, aka BlackCat, is another ransomware gang that was mentioned more than once on Black Kite’s list. The gang took responsibility for a ransomware attack on Florida International University in April 2022. The attacker stole personal information from students, staff, and teachers (about 1.2 TB of data). The data stolen included accounting documents, Social Security numbers, and email databases.
Image 1: Black Kite's Ransomware Susceptibility Index - Higher Education
Source: Black Kite
Like ransomware, security attacks are a serious concern in the IoT (Internet of Things) space. The more network devices you have, the more your endpoints need to be secured. An IoT attack takes place when an IoT system is compromised. This kind of attack involves networks, data, devices, and users. Threat actors launch this kind of attack to steal information and take over an automated or IoT system, thus shutting it down.
In February 2017, an unnamed university was attacked by its own vending machines, lightbulbs, and lamp posts. Over 5,000 connected IoT devices were compromised by threat actors. The devices made hundreds of Domain Name Service (DNS) lookups every 15 minutes and caused the university’s network connectivity to become painfully slow. Almost all systems were living on the segment of the network dedicated to the university’s IoT structure. Students reported the issues they were having with slow network connectivity, but the complaints were allegedly brushed off by the school’s help desk.
According to Verizon’s Data Breach Digest 2017, the IoT systems were supposed to be isolated from the rest of the network, but instead, they were all configured to use DNS servers in a different subnet. Lightbulbs and vending machines were connected to the network for easier management and for efficiency. The attackers behind the ordeal instructed the IoT devices to make DNS lookups regarding seafood (red flag #1) every 15 minutes. However, according to the firewall and DNS logs, out of the thousands of domains requested, only 15 IP addresses were returned (red flag #2). Four of those addresses and about 100 domains appeared in an indicator list for an emergent IoT botnet.
The above is great example of poorly secured IoT devices. While every soda machine and lamp post didn’t have to be replaced because of the attack, the botnet did spread from device to device by using brute force on default and weak passwords.
phishing attacks & social engineering
Phishing via social engineering is a tried-and-true cyber attack that often gets the best of schools and universities. According to Avertium’s blog on phishing, phishing attacks are often a vessel to deliver malware that masquerades as a communication from a trusted or reputable source. Phishing attacks can come in the form of an email, a phone call (fishing), or a text message (smishing) – with the most common vehicle being through email.
A phishing attack email typically looks or sounds like it’s from a company or someone within your organization. The threat actor behind the attack will ask for privileged information’s or provide a link to an attachment which results in you downloading something malicious.
Social engineering is included in phishing attacks and involves threat actors researching companies or individuals prior to the attack. The goal is to get the victim to trust the threat actor by providing a lot of convincing information about the victim. Threat actors take advantage of core human psychology to manipulate people into doing exactly what they want. Given the lack of consistent security training, schools and universities are especially susceptible to a phishing/social engineering attack.
In 2017, MacEwan University in Edmonton, Canada was defrauded of $11.8 million due to a staff member falling victim to a phishing attack. The attacker sent the victim an email, impersonating a vendor requesting a change in banking information. The first mistake the victim made was not verifying the email and the request. As a result, MacEwan University lost millions of dollars.
data breaches
Data breaches can have a devastating impact on the education sector. The information that is stored by educational institutions is sensitive and if that data is leaked, students, teachers, and staff could be exposed to the masses. A data breach happens when an unauthorized person gets access to protected information such as dates of birth, Social Security numbers, banking information, and medical records.
According to Comparitech’s report on data breaches and the education sector, they found that from 2005 to the end of 2021, K-12 school districts, as well as colleges and universities around the world, experienced 1,850 data breaches. More than 28.6 million records were affected by the data breaches and over 200 hundred of those attacks were the result of Blackbaud ransomware.
Millions of individuals were impacted in early 2020 after Blackbaud Inc., a cloud computing company, was targeted by a ransomware gang. The attacker was able to remove a copy of a subset of data from Blackbaud’s private cloud environment, holding the data ransom in exchange for destruction of the stolen data. The data stolen included usernames and passwords, bank account information, and Social Security numbers. The breach impacted students at Boston University, Santa Clara University, the University of Illinois Foundation, George Washington University, and the University of Dallas. As a result of the attack, Blackbaud faced several lawsuits stating claims of violations of data breach statutes and breach of contract.
Additionally, Black Kite’s research showed two confirmed data breaches in their top 100 list of colleges and universities. Syracuse University faced a data breach on March 28, 2022, when two email addresses belonging to employees fell victim to a cyber attack involving personal information. An unauthorized party was able to access the email accounts due to a phishing attack. Washington University School of medicine was also the victim of a data breach in March 2022. An attacker was able to gain access to employee email accounts which contained patient health information.
unpatched & outdated software
According to Black Kite, patch management is an issue amongst higher education institutions, so it’s no surprise that unpatched and outdated software made it to this list. Installing patched software and updating software in general is a cyber security best practice that the education sector lets fall the wayside. Patching is paramount if you want to avoid a breach, yet every year threat actors successfully exploit devices due to lack of patching.
In September 2021, the University of Colorado Boulder suffered a cyber attack when their software was compromised – exposing the personal information of 30,000 current and former students and employees. The attack was the result of a vulnerability in Atlassian software the school used to share information and access files. The information compromised included student ID numbers, dates of birth, and phone numbers.
Atlassian released a patch for the vulnerability in August 2021, but the university did not patch their software in time. Had they patched the vulnerability sooner, they could have avoided the public shame that comes with a data breach. The campus stated they needed to make investments to improve their threat analysis, as well as automation for system patches to create less of a lag between a software patch releases and implementation.
cyber threats & higher education - black kite
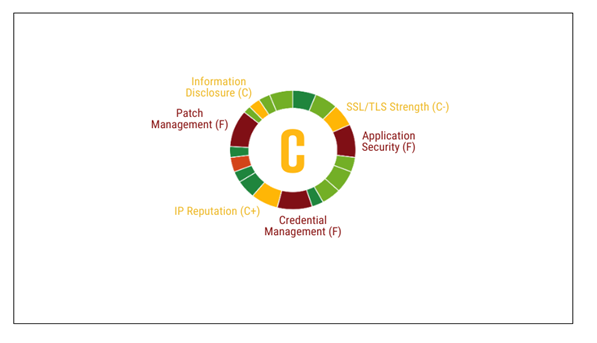
Image 2: Black Kite's Security Rating for Top 100 College and Universities
Source: Black Kite
As previously stated, Black Kite conducted research on the top 100 colleges and universities within the U.S., using a technical rating system from A to F. Ninety-three colleges and universities had a rating of C, while two colleges and universities had a rating of D when it came to overall cyber security.
- Patch Management – 93 schools had an F rating.
- Application of Security – 97 schools had an F rating.
- Attack Surface – all schools had a D- rating.
- Credential Management – every single school had an F rating and the top 100 list had at least one credential available on the dark web in the last 90 days.
- The list’s average technical rating has a rating of 73, which is a C.
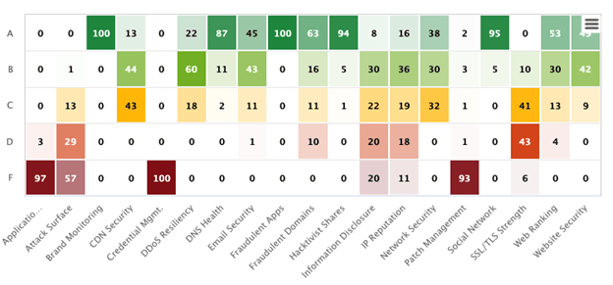
Image 3: Black Kite's Higher Education Ecosystem
Source: Black Kite
Black Kite’s research shows that colleges and universities are doing a poor job of securing their cyber environments. Lack of resources and budget, the absence of security policies, and lack of security training are all reasons why higher education institutions don’t have the best cyber security in place. However, despite these challenges, every institution should lay the foundation for a secure IT network.
All of the mentioned examples of cyber attacks on colleges and universities could have been avoided had the institution has their security priorities in order. Avertium recommends the following to help keep your institution safe:
- Ransomware Attacks – Ransomware threat actors are simply looking for a way to make money. Avoid becoming a ransomware statistic by doing tabletop exercises with your staff. These kinds of exercises will help test your people, as well as your systems. Encrypting your data can also prevent ransomware attacks – attackers can’t access encrypted data and therefore, cannot ransom you.
- IoT Attacks – Please change your default passwords and settings when setting up a new IoT device – make it difficult for threat actors to guess your passwords. Also, using multi-factor authentication when logging into IoT devices will give you extra protection. However, when basic security measures are still not enough, managing the network access to IoT devices will help minimize the risk of unauthorized network access – even if your lightbulbs and vending machines are compromised.
- Phishing & Social Engineering – Prevent phishing and social engineering attacks by providing security training for your staff. Again, tabletop exercises that try to trick your employees into becoming a victim of this kind of attack will help your institution figure out where you are with security knowledge. Suspicious email addresses, spelling and layout errors in documents, and spoofed hyperlinks are all ways employees and students can become phishing victims.
- Data Breaches – Make the school staff aware of data security and the importance of safeguarding information. The main reason data breaches happen is due to human error. If you do fall victim to a data breach, at least make sure you have secure backups that are tested regularly.
- Unpatched & Outdated Software – Preventing an attack via a vulnerability is as simple as patching (updating) your software. Patching immediately can save an educational institution a lot of time and money, as well as prevent a cyber attack.
How Avertium is Protecting Our CUSTOMERS
- We offer EDR endpoint protection through SentinelOne, Sophos, and Microsoft Defender.
- SentinelOne prevents threats and extends protection from the endpoint to beyond. Find threats and eliminate blind spots with autonomous, real time, index-free threat ingestion and analysis that supports structured, unstructured, and semi-structured data.
- SentinelOne prevents threats and extends protection from the endpoint to beyond. Find threats and eliminate blind spots with autonomous, real time, index-free threat ingestion and analysis that supports structured, unstructured, and semi-structured data.
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
- Avertium offers Zero Trust Network as a Service (ZTNaaS) for any organization that wants to control their attack surface. The zero-trust security model delivers exactly what the name promises: it's an IT security concept that specifies no access is allowed until the successful completion of authentication and authorization processes.
- Avertium offers user awareness training through KnowBe4. The service also Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
Avertium’s Recommendations
To prevent ransomware attacks, data breaches, IoT attacks, phishing and social engineering attacks, and attacks via unpatched software, Avertium and the FBI recommend that you do the following:
- Use strong credentials and multi-factor authentication.
- Patch and update your software.
- Educate your employees on cyber security best practices.
- Upgrade your devices when software is obsolete.
- Use hard passwords and enforce this amongst your institution.
- Encrypt your data and always have backups (test your backups often).
- Disable unused remote access/RDP ports and monitor remote access/RDP logs.
- Require administrator credentials to install software.
- Audit user accounts with administrative or elevated privileges and configures access controls with the least privilege in mind.
- Implement network segmentation.
- Monitor IoT devices at all times.
- Gain visibility into how many IoT devices are connected to your network.
- If you don’t have one already, develop a cyber security policy that employees must follow.
- Advise employees not to click on suspicious links or open email attachments from suspicious senders.
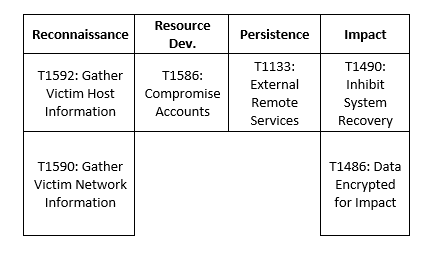
MITRE Map
LockBit
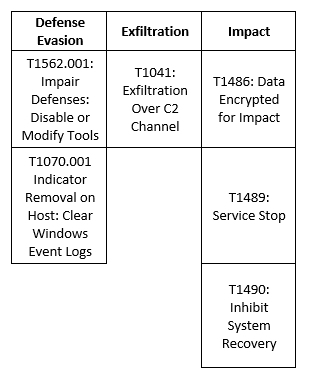
BlackCat
Indicators of Compromise (IoCs)
LockBit
- Sha256 -0545f842ca2eb77bcac0fd17d6d0a8c607d7dbc8669709f3096e5c1828e1c049
- hxxp://lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd[.]onion
- hxxp://lockbitsap2oaqhcun3syvbqt6n5nzt7fqosc6jdlmsfleu3ka4k2did[.]onion
- hxxp://lockbitsup4yezcd5enk5unncx3zcy7kw6wllyqmiyhvanjj352jayid[.]onion
- hxxp://209.14.0[.]234:46613/VcEtrKighyIFS5foGNXH
BlackCat
- id7seexjn4bojn5rvo4lwcjgufjz7gkisaidckaux3uvjc7l7xrsiqad[.onion]
- sty5r4hhb5oihbq2mwevrofdiqbgesi66rvxr5sr573xgvtuvr4cs5yd[.onion]
- htnpafzbvddr2llstwbjouupddflqm7y7cr7tcchbeo6rmxpqoxcbqqd[.onion]
- aoczppoxmfqqthtwlwi4fmzlrv6aor3isn6ffaiic55wrfumxslx3vyd[.onion]
- alphvmmm27o3abo3r2mlmjrpdmzle3rykajqc5xsj7j7ejksbpsa36ad[.onion]
- 2cuqgeerjdba2rhdiviezodpu3lc4qz2sjf4qin6f7std2evleqlzjid[.onion]
- zujgzbu5y64xbmvc42addp4lxkoosb4tslf5mehnh7pvqjpwxn5gokyd[.onion]
- mu75ltv3lxd24dbyu6gtvmnwybecigs5auki7fces437xvvflzva2nqd[.onion]
- f815f5d6c85bcbc1ec071dd39532a20f5ce910989552d980d1d4346f57b75f89
- c3e5d4e62ae4eca2bfca22f8f3c8cbec12757f78107e91e85404611548e06e40
- 74464797c5d2df81db2e06f86497b2127fda6766956f1b67b0dcea9570d8b683
- 4e18f9293a6a72d5d42dad179b532407f45663098f959ea552ae43dbb9725cbf
- 1af1ca666e48afc933e2eda0ae1d6e88ebd23d27c54fd1d882161fd8c70b678e
- 15b57c1b68cd6ce3c161042e0f3be9f32d78151fe95461eedc59a79fc222c7ed
- 13828b390d5f58b002e808c2c4f02fdd920e236cc8015480fa33b6c1a9300e31
- c8b3b67ea4d7625f8b37ba59eed5c9406b3ef04b7a19b97e5dd5dab1bd59f283
- bd337d4e83ab1c2cacb43e4569f977d188f1bb7c7a077026304bf186d49d4117
- 7b2449bb8be1b37a9d580c2592a67a759a3116fe640041d0f36dc93ca3db4487
- 38834b796ed025563774167716a477e9217d45e47def20facb027325f2a790d1
- 2cf54942e8cf0ef6296deaa7975618dadff0c32535295d3f0d5f577552229ffc
- 28d7e6fe31dc00f82cb032ba29aad6429837ba5efb83c2ce4d31d565896e1169
- 0c6f444c6940a3688ffc6f8b9d5774c032e3551ebbccb64e4280ae7fc1fac479
- f8c08d00ff6e8c6adb1a93cd133b19302d0b651afd73ccb54e3b6ac6c60d99c6
- 731adcf2d7fb61a8335e23dbee2436249e5d5753977ec465754c6b699e9bf161
- 59868f4b346bd401e067380cac69080709c86e06fae219bfb5bc17605a71ab3f
- 3d7cf20ca6476e14e0a026f9bdd8ff1f26995cdc5854c3adb41a6135ef11ba83
- 7e363b5f1ba373782261713fa99e8bbc35ddda97e48799c4eb28f17989da8d8e
- cefea76dfdbb48cfe1a3db2c8df34e898e29bec9b2c13e79ef40655c637833ae
Supporting Documentation
Rise of Ransomware Attacks on the Education Sector During the COVID-19 Pandemic (isaca.org)
2 emails in SU department victim to data breach involving personal information - The Daily Orange
How to Secure IoT Devices in the Enterprise - Palo Alto Networks
What are the Best Ways to Protect IoT Devices from Attack? - Revolutionized
Protecting Sensitive and Personal Information from Ransomware-Caused Data Breaches (cisa.gov)
Colo. University Hacked Due to Lack of Updated Software (govtech.com)
The State of Cybersecurity in Education - Security Boulevard
Avoiding Social Engineering and Phishing Attacks | CISA
Ransomware risk: 6 steps colleges can take to help prevent cyberattacks | (universitybusiness.com)
What is a Data Breach & How to Prevent One (kaspersky.com)
A university was attacked by its lightbulbs, vending machines and lamp posts | Mashable
Blackbaud ransomware attack may have impacted millions of Individuals | BenefitsPRO
Ransomware group hacks UofD mercy threatens to release info (audacy.com)
Hacking Humans: The social engineering threat (avertium.com)
BlackCat Ransomware & Triple Extortion (Analysis & Tactics) (avertium.com)
Preventing Security Hacks in the Education IoT Space | Kajeet Education Solutions
Ransomware Vs. Phishing Vs. Malware (What's The Difference) (avertium.com)
Related Resource: [Threat Report] The Top 5 Cyber Threats in the Manufacturing Industry
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.