An Update on LockBit 3.0
Executive Summary
In July 2022, Avertium’s Cyber Threat Intelligence team published a detailed Threat Intelligence Report featuring LockBit 3.0 and their activity. The ransomware operation rebranded for the second time and acquired new tactics and techniques, as well as a new bug bounty program.
Originally targeting organizations within the U.S., the UK, Germany, China, India, France, the Ukraine, and Indonesia, LockBit researches targets with valuable data before encrypting files and demanding a hefty ransom payment. During the summer of 2022, the threat actors were very active and attacked multiple sectors and organizations across the globe. Their activity slowed for just a couple of months before starting up their attacks again this fall.
Recently, LockBit has made news for attacking several organizations including IT services providers and automotive giants. Let’s take a look at the recent activity of LockBit 3.0, their tactics and techniques, as well as the state of ransomware for 2022.
lockbit's evolution
Since 2019, LockBit (also known as LockBit Black) has operated as a ransomware-as-a-service (RaaS) gang, threatening to publish sensitive data on their leak site if targets didn’t pay their ransom demands. In the past, LockBit avoided attacking systems local to Russia or countries within the Commonwealth Independent States, likely to avoid prosecution from law enforcement.
LockBit’s earlier attacks include Accenture, one of the world’s largest tech consultancy firms. The attack on Accenture took place in August 2021 and the group stole 6 TB of data, demanding $50 million in ransom. LockBit is known to research organizations before they attack – Accenture’s revenue for 2020 was $44.33 billion.
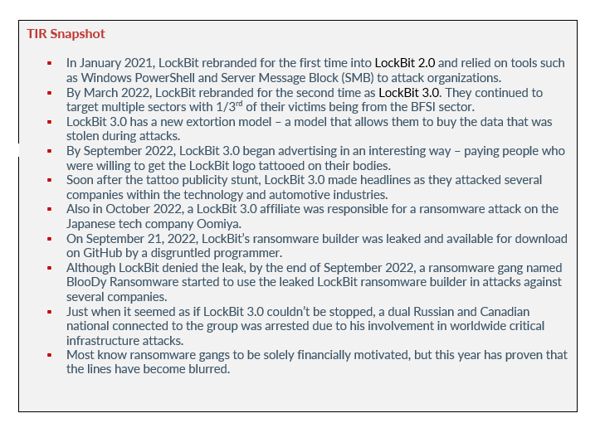
In January 2021, LockBit rebranded for the first time into LockBit 2.0 and relied on tools such as Windows PowerShell and Server Message Block (SMB) to attack organizations. They also started to become more public facing, giving multiple interviews. The ransomware group also encouraged organizations to use Bitdefender to defend against ransomware attacks. At this time, threat actors already figured out ways to bypass Bitdefender, including using the official Bitdefender Uninstall Tool to disable defenses.
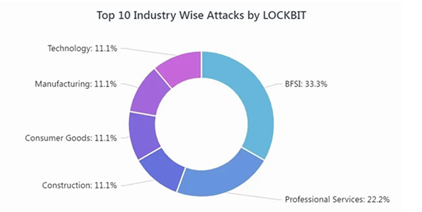
By March 2022, LockBit rebranded for the second time as LockBit 3.0. They continued to target multiple sectors with 1/3rd of their victims being from the BFSI sector. With the new rebrand, came new tactics and techniques. Their latest version of their ransomware encrypts files on victim’s machines and appends the extension of encrypted files as “HLjkNskOq”.
To encrypt files, LockBit 3.0 deletes a few services. However, before encryption, the ransomware uses the WMI query to enumerate Volume Shadow copies by using the command “select *from Win32_ShadwoCopy”. This is done before deleting the copies using “Win32_ShadowCopy.ID”, preventing attempts to restore a system after the files are encrypted.
Image 1: Industries Targeted by LockBit 3.0
Source: Cyble
The ransomware deletes the following services before it calls the OpenSCManagerA() API to get the service control manager database access, before changing their victim’s wallpaper to reflect that they’ve been hacked. Victims then are instructed on how to pay the demanded ransom via a ransom note that is dropped onto the victim’s computer. Also, victims are threatened and told their data will be leaked on LockBit 3.0’s data leak site if the ransom isn’t paid in Bitcoin.
LockBit 3.0 has a new extortion model – a model that allows them to buy the data that was stolen during attacks. Found in one of the JavaScript files used by the threat actor’s new leak site, a new HTML modal dialog allows people to buy stolen data from the site. People will be able to buy the data and download it through a Torrent or directly on the site. The options will more than likely be based on the size of the stolen data. Torrents will be used for larger data dumps, while direct downloads will be used for smaller data dumps.
As LockBit was introducing new tactics and techniques, the group also introduced a bug bounty program. Once victims click on a Tor link mentioned in LockBit’s ransom note, they are redirected to the group’s leak site. The site contains a link that redirect users to a page where LockBit announces their bug bounty program – a program specifically for security researchers, unethical, and ethical hackers to find flaws in LockBit’s ransomware.
recent lockbit 3.0 activty
By September 2022, LockBit 3.0 began advertising in an interesting way – paying people who were willing to get the LockBit logo tattooed on their bodies. The group posted a message on their site stating that due to the amount of people wanting to tattoo the logo, the “promotion” would be limited until September 11, 2022.
The group also stated that the tattoo had to be permanent and that all participants needed to take a photo of it along with a photo of their bitcoin wallet. LockBit ended up paying more than 10 people, $1k for the tattoos. Why would a ransomware gang choose this kind of advertisement? A security expert and researcher with the Twitter handle 3xp0rtblog stated that it is inexpensive advertisement.
Pendragon
Soon after the tattoo publicity stunt, LockBit 3.0 made headlines as they attacked several companies within the technology and automotive industries. In October 2022, the group posted Pendragon, a UK car dealership, on their blog. LockBit claimed that they stole more than two million files from the company and threatened to publish the data if they did not pay the $60 million ransom demand.
With more than 200 car dealerships in the UK, Pendragon’s dealerships include retailers such as Evans Halshaw, Stratone, and CarStore. The retailers carry brands such as Jaguar, Porsche, and Mercedes. Pendragon refused to negotiate with LockBit 3.0 and stated that they would not be held hostage by the group nor would they be paying the ransom demand. Instead, the company decided to launch an investigation into the attack. Although Pendragon’s servers were indeed hacked, LockBit only stole 5% of its database.
Oomiya
Also in October 2022, a LockBit 3.0 affiliate was responsible for a ransomware attack on the Japanese tech company Oomiya. Oomiya designs and manufacturers microelectronics and facility system equipment. The attackers used LockBit’s ransomware to steal data before threatening to leak the data by October 20, 2022, if the company refused to pay the undisclosed ransom.
Because Oomiya is in the supply chain of major organizations worldwide in several industries (healthcare, communications, manufacturing, automotive, and semiconductors), the security incident could have a major impact on third party organizations. The company is broken up into four major areas: manufacturing and designing chemical and industrial products, pharmaceutical development, designing electronic materials, and factory manufacturing. There are currently no reports on the status of Oomiya’s negotiations with LockBit 3.0 or with the affiliate that used the ransomware.
Kingfisher Insurance
In Addition to Oomiya, LockBit 3.0 also attacked Kingfisher insurance – a UK insurance company that operates eight brands across specialist insurance areas including home and car insurance. The group claimed to have stolen 1.4 TB of personal data of employees and customers. The ransomware gang infiltrated Kingfisher’s servers and retrieved that data before demanding that the company pay an undisclosed ransom by November 28, 2022.
Thales
By early November 2022, LockBit 3.0 attacked yet another major technology organization – Thales. Thales is a defense and technology group operating out of France. LockBit stole some of the company’s data and threatened to publish the data on their data leak site by November 7, 2022.
At that time, Thales acknowledged LockBit’s attempt to extort them and stated that they had not received a direct ransom notification from the ransomware group. Thales opened an internal investigation and informed the ANSSI national cyber security agency about the security incident.
By November 10, 2022, LockBit published Thales’ data on their data leak site and Thales confirmed the leak.
“At this stage, on November 10, 2022, at 3 pm (CET time) Thales is able to confirm the following information:
- On November 10, 2022, an extortion and ransomware group (LockBit 3.0) released on its publication platform data pertaining to Thales Group.
- At this stage, Thales is able to confirm that there has been no intrusion of its IT systems.
- Thales security experts have identified one of the two likely sources of the theft, which has been confirmed through the user account of a partner on a dedicated collaboration portal. This has led to the disclosure of a limited amount of information.
- Thales continues to investigate the other source of theft.
- Thales reiterates that, as of now, there is no impact on the Groups operations.
- Thales is working closely with its partner and is providing all of the necessary technical support and resources to minimize any potential impact to concerned customers and stakeholders.
- The Group remains vigilant towards any data theft, systematically mobilizing our teams of security experts, as data security of any of our stakeholders is our utmost priority.” – Thales
a downturn for lockbit?
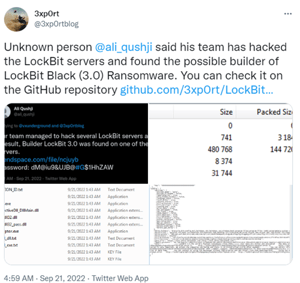
On September 21, 2022, LockBit’s ransomware builder was leaked and available for download on GitHub by a disgruntled programmer. LockBit denied that they were hacked and stated that they fired the programmer who leaked their builder. The leak contained a screen shot of a default config file where you can clearly see a password “123QWEqwe?”.
Image 2: LockBit Builder Leaked
Source: Twitter
Image 3: LockBit Builder Leaked
Source: Twitter
Although LockBit denied the leak, by the end of September 2022, a ransomware gang named BlooDy Ransomware started to use the leaked LockBit ransomware builder in attacks against several companies. According to Bleeping Computer, the builder allows anyone to build a fully functional encryptor and decryptor that threat actors can use for attacks.
Researchers predict that the builder will be used by other threat actors to create their own ransomware, as the builder is easily customizable. BlooDy Ransomware has been operating since May 2022 and they have targeted medical and dental practices in New York. Their tactics and techniques include breaching networks, stealing data, and encrypting deices. However, unlike other ransomware gangs, BlooDy Ransomware does not use a Tor data leak site to extort their victims. Like Lapsus$, BlooDy Ransomware has opted to use a Telegram channel to publish stolen data and extort their victims.
Avertium’s Cyber Threat Intelligence team was able to analyze LockBit’s most recent malware and we didn’t find significant changes in their tactics and techniques since their last rebrand. The availability of the ransomware build greatly improves our ability to analyze this type of malware. While the builder program leak will force LockBit 3.0 to retool, it will also result in copycat attacks using this ransomware.
Being able to detect and identify LockBit’s malware will continue to be important for the foreseeable future. Fortunately, Windows Defender will stop this ransomware if Windows computers are consistently updated. With Defender enabled, LockBit’s ransomware will be blocked, forcing copycats to jump through additional hoops to disable it.
The LockBit 3.0 builder was leaked in September 2022 and the builder package contains a bat file, a json config file, a key generator and the actual ransomware builder. The json config file contains options for different settings for the encryptor. The screen shots below show all the possible configurable options available.
Image 4: Configurable Options
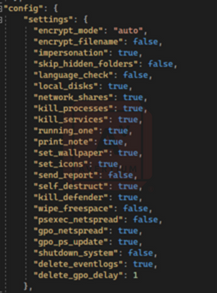
The below screen shot shows the options for whitelisting file extensions, files, and folders, as well as the different processes or services to kill and accounts to impersonate.
Image 5: Options for Whitelisting File Extensions
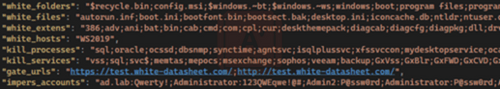
Image 6: Json Config File
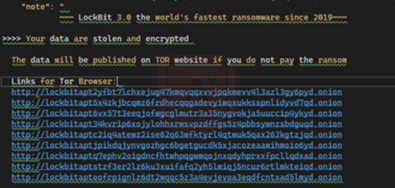
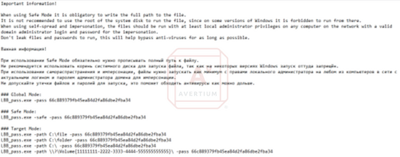
This text file is created during the building of the ransomware. The note includes a warning and instructions about using “Safe Mode”. The note is written in both English and Russian, indicating a link to Eastern Europe, but also that this group operates as a “Ransomware-as-a-service” model.
Image 7: Ransomware Note
arrests
Just when it seemed as if LockBit 3.0 couldn’t be stopped, a dual Russian and Canadian national connected to the group was arrest due to his involvement in worldwide critical infrastructure attacks. Mikhail Vasiliev was arrested in Ontario, Canada at the end of October 2022. The investigation was led by the French National Gendarmerie with the help of the FBI, the Canadian Royal Canadian Mounted Police, and Europol’s European Cybercrime Centre.
During Vasiliev’s arrest, law enforcement allegedly seized eight computers, 32 external hard drives, and 400,000 euro in cryptocurrency. Vasiliev’s arrest followed the arrest of two of his accomplices. He is currently awaiting extradition to the U.S. where he faces a maximum of five years in prison if convicted of conspiracy to intentionally damage protected computers and to transmit ransom demands.
Ransomware 2022
LockBit 3.0 has been the most active ransomware gang during the third quarter of 2022. The group has been responsible for 37% of the ransomware attacks deployed this quarter and that number will likely rise. So far, LockBit has claimed at least 1,000 victims in the U.S., and they have stolen tens of millions of dollars in ransom payments from victims.
According to Digital Shadows, ransomware activity in general decreased in the third quarter of 2022, as threat actors regrouped and refocused after a busy start to the year. However, the attacks on high profile targets and on political entities didn’t stop. As new tools and techniques emerged, RaaS gangs rushed to fill the void left by Conti.
During the third quarter of 2022, researchers observed the emergence of 12 new ransomware data leak sites and LockBit 3.0 topped off the quarter in the lead with their attacks. BianLian, Medusa Locker, and BlackByte kept busy as they attacked critical infrastructure. Previously, ransomware ware cut and dry regarding motivation. Most know ransomware gangs to be solely financially motivated, but this year has proven that the lines have become blurred.
Ransomware like H0ly Gh0st and the Iranian attacks on Albania muddy the waters when it comes to differentiating between a political agenda and a financial one. While we know that H0ly Gh0st is ransomware, those behind it were North Korean state backed attackers. This makes ransomware not just a tool for cybercriminals looking for financial gain, but an impactful political tool as well.
As the lines continue to blur, it’s important for organizations to maintain excellent cyber security posture against ransomware gangs like LockBit and ransomware gangs that are willing to do anything to obtain what they want.
How Avertium is Protecting Our CUSTOMERS
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium’s offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills.
- Avertium recommends utilizing our service for DFIR (Digital Forensics and Incident Response) to help you rapidly assess, contain, eradicate, and recover from a security incident like a malware attack.
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
- Avertium offers VMaaS to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium uses whitelisting tools like AppLocker to audit or block command-line interpreters.
- Avertium offers user awareness training through KnowBe4. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
avertium's recommendations
- Require multifactor authentication to protect employees’ accounts from being used by attackers to obtain account credentials and use them to escalate privileges and move laterally within the network.
- Perform daily backups and keep them offline to avoid losing data.
- Disrupt network movements/investigation by way of creating separated segments of network, clear access hierarchy, and additional security for active directory, domain admin, and local domains – thus complicating LockBit 3.0’s operations.
- Relying on outdated tools and point solutions will compromise your network or system. Better technology exists to detect complex attacks like LockBit 3.0 ransomware.
- Use anti-ransomware technology as a prevention method. Deploy prevention that works like next-generation antivirus and explicit anti-ransomware technology.
- Reduce the target by including these technical practices: close vulnerabilities, augment security hygiene, create and enforce strong general policies, and sustain backup and recovery practices.
- It’s likely that LockBit 3.0 monitors the latest CVEs. Monitor exposed endpoints and application of CVE-addressing patches.
MITRE Map
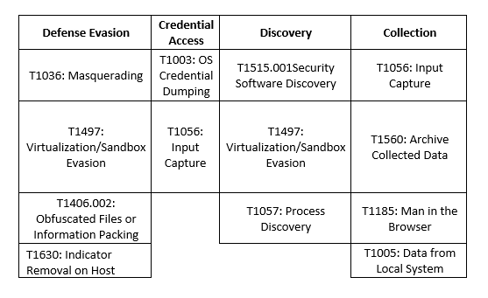
Indicators of Compromise (IoCs)
Hashes
|
f9ab1c6ad6e788686509d5abedfd1001 |
|
bf331800dbb46bb32a8ac89e4543cafa |
|
bf4d4f36c34461c6605b42c456fa4492 |
|
1690f558aa93267b8bcd14c1d5b9ce34 |
|
cb480fb6281f2c42ac214822416c24e01942cfea |
|
12eb4ca3ec5b7c650123c9053ea513260d802aa52486b7512b53fb7e86ec876b |
|
5e54923e6dc9508ae25fb6148d5b2e55 |
|
97bef2aed306a8f6bde427fd22e0f20095f14af7 |
|
87b76f35740262abb8da224b94779ff56eb6346318b4f9fb1988a59a72a4e6c9 |
|
ad444dcdadfe5ba7901ec58be714cf57 |
|
61fed673833726bd8261c1c94963ff23c412735a |
|
5aff860634fadee66a6e8220e67f7ebc88bfcde7a905a2753655706c0252afd1 |
|
56c9c8f181803ece490087ebe053ef72 |
|
424dc482b786bf20dca62e890675bd4c21f45c39 |
|
8fb3b241a2578c6fbaf43a7c4d1481dc5083d62601edece49d1ce68b0b600197 |
|
13b12238e3a44bcdf89a7686e7179e16 |
|
b0fee72899c445da6b93777969ec58eabbafb709 |
|
142cbad8b9d400380c78935e60db104ec080812b1a298f9753a41b2811c856be |
|
ae59e82ddd8d9840b79bfddbe4034462 |
|
cf1f380d736c035793581d87868952efe789520a |
|
1d8596310e2ea54b1bf5df1f82573c0a8af68ed4da1baf305bcfdeaf7cbf0061 77c5fb080bf77f099c5b5f268dcf4435 f019495a1d4feecc07769dc1fbecccb871634cc707c43befe1ea7aa2c629e337 |
URLs
hxxp://ppaauuaa11232[.]cc/aaa[.]exe
ppaauuaa11232[.]cc
hxxp://ppaauuaa11232[.]cc/dlx5rc[.]dotm
Supporting Documentation
10 people gets a LockBit ransomware logo tattooed for $10,000 (thetechoutlook.com)
An In-Depth Look at Ransomware Gang, LockBit 3.0 (avertium.com)
Pendragon posted on LockBit 3.0 blog for $60m (techmonitor.ai)
LockBit 2.0 Ransomware: An In-Depth Look At LockFile & LockBit (avertium.com)
Japanese tech firm Oomiya hit by LockBit 3.0Security Affairs
Kingfisher Insurance suffers ransomware attack from LockBit 3.0 (techmonitor.ai)
France's Thales says hackers claim to have stolen data | Europe – Gulf News
France's Thales says hackers claim to have stolen data | Reuters
Thales position on LockBit 3.0 | Thales Group
Police arrest suspected LockBit operator as the ransomware gang spills new data | TechCrunch
LockBit 3.0 Ransomware Unlocked - VMware Security Blog - VMware
Leaked LockBit 3.0 builder used by ‘Bl00dy’ ransomware gang in attacks (bleepingcomputer.com)
LockBit repeats 'PR stunt' as Thales ransomware investigation reveals no breach | IT PRO
Police arrest suspected LockBit operator as the ransomware gang spills new data | TechCrunch
Ransomware In Q3 2022 | Digital Shadows
An In-Depth Look at Ransomware Gang, LockBit 3.0 (avertium.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.