North Korea is the Threat
Executive Summary
Lately, North Korean threat actors have been extremely visible, attacking several industries and disrupting the operations of many organizations. While attacks from North Korea are not unusual, there has been an uptick in activity from the region. In April 2022, the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) released a joint advisory highlighting the activity of the North Korean state-sponsored APT group, Lazarus – also known as APT38.
As the rest of the world was focused on the cyber war between Russia and Ukraine, Lazarus was launching their own attacks. At the time, Lazarus was using social engineering to trick victims into downloading Trojanized cryptocurrency applications on Windows or macOS operating systems. According to CISA, Lazarus used the applications to gain access to their victims’ computer, propagate malware across their network, and steal private keys – activities that enabled follow-on activities that initiate fraudulent blockchain transactions.
CISA’s advisory would mark the beginning of a slew of attacks from North Korean threat actors in 2022. So far, we have seen steady activity from NOBELIUM, Kimsuky, H0ly Gh0st, and Lazarus. Let’s take a look at how active North Korea has been, links between threat groups, and why North Korea is a threat.

h0ly gh0st ransomware
A lesser-known, North Korean ransomware gang named H0ly Gh0st aka DEV-0530 (or Holy Ghost for this report) began attacking schools, manufacturing organizations, banks, and event management firms in June 2021. Interestingly, the group is not a state-sponsored threat actor, but they do cooperate with the government despite not being on the government’s payroll.
Microsoft analyzed Holy Ghost’s ransomware and found that the group has been in communication with Lazarus – a veteran North Korean threat actor. According to Microsoft,
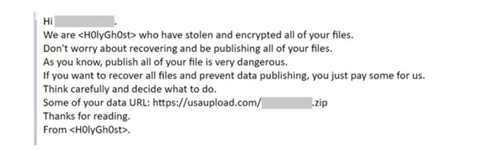
Holy Ghost has been developing and deploying ransomware since June 2021 and utilizes a ransomware payload with the same name for its campaigns. The ransomware gang also has a dot onion site where they interact with victims.
After encrypting their victim’s files, Holy Ghost uses the file extension .h0lyenc and sends the victim a sample of the encrypted files as proof. They then demand ransom payments in the form of Bitcoin. If the victim refuses to pay the demanded ransom the ransomware gang will threaten to publish sensitive data on social media or send the data to the victim’s customers. This tactic is known as double extortion.
Holy Ghost has been seen abusing flaws such as CVE-2022-26352 – a remote code execution vulnerability found in the ContentResource API in dotCMS 3.0 through 22.02.
According to Microsoft, Holy Ghost has connections with another North Korean-based group called PLUTONIUM. Although Holy Ghost’s ransomware is unique to the group, they have been observed communicating with PLUTONIUM. They’ve also been seen using tools created by PLUTONIUM.
While PLUTONIUM primarily targets the energy and defense industries in India, South Korea, and the United States, both HolyGhost and PLUTONIUM were seen operating from the same infrastructure set and using custom malware controllers with similar names. However, despite communicating with PLUTONIUM and the similarities, Microsoft believes that H0lyGh0st is its own distinct group.
Tactics & Techniques
Although Holy Ghost has some communication with North Korea’s government, their main goal is financial gain. Holy Ghost developed and used two new malware families: SiennaBlue and SiennaPurple. Those families have four variants under them: HolyLock.exe, BTLC_C.exe, HolyRS.exe, and BLTC.exe. The threat actors have clustered the variants based on code similarity, ransom note text, and C2 infrastructure (including C2 URL patterns). Because BTLC_C.exe is written in C++, it’s classified as SiennaPurple, while the rest are written in Go (also referred to as GoLang).
Microsoft observed a cluster of new Holy Ghost ransomware variants written in Go between October 2021 and May 2022. The variants were classified as SiennaBlue. SiennaBlue’s Go functions include features like string obfuscation, encryption options, public key management, and support for the internet and intranet.
In November 2021, Holy Ghost successfully compromised several targets in various countries by using HolyRS.ex. The victims were small to midsized businesses in the manufacturing, banking, education, and event and meeting planning industries. Holy Ghost was possibly able to compromise the organizations by exploiting vulnerabilities (such as CVE-2022-26352) on public-facing web applications and content management systems, gaining initial access into networks.
Image 1: H0ly Gh0st Ransomware Analysis
Source: Avertium's Cyber Threat Intelligence Team
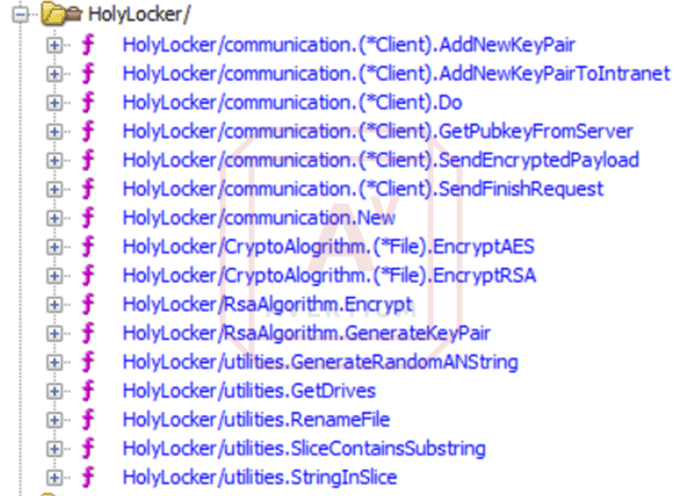
Avertium’s Cyber Threat Intelligence team (CTI) analyzed two samples of Holy Ghost ransomware: oih12ek4k[.]dll and ufggul58a[.]dll. As you can see, both samples can be found on vx-underground, and both are ransomware encryptors that are written in Go. One advantage that Go has over other programming languages is that Go function calls are easier to see in Ghidra. Other languages, such as C++, don’t always decompile cleanly in IDAPro or Ghidra – losing function names and other information.
The samples pulled from vx-underground appear to be from a more recent campaign, based on the inclusion of functions that did not exist in the 2021 ransomware samples - including self-delete, encrypt string, and decrypt string functions. Like other North Korean ransomware Avertium’s Cyber Threat Intelligence Team has analyzed, obfuscation does not appear to be the highest priority. While the following function calls do not show up in the strings, it was easily parsed by the decompiler. The name of the function is called HolyLocker.
Image 2: H0ly Gh0st Ransomware

Source: Avertium's Cyber Threat Intelligence Team
There are two possible reasons why the CTI team was not able to find the static strings for where it stores remote IP address or other IOCs:
- The strings are not stored in this file. We do not think the is the case, when these samples were uploaded to VirusTotal, they reached out to the C2 server.
- The strings are encoded or otherwise obfuscated. In the list of functions found in Ghidra, there are several that are geared toward simple encoding and decoding.
Also, there is a pair of functions for left and right rotate, which can be used for ROT cyphers. After testing, the CTI team concluded that the only functions we can safely assume are used by the malware are the ones with “HolyLocker”.
Once Holy Ghost gains access to their target’s network, they drop and execute the SiennaBlue malware variants. Once the network is compromised, the threat actor exfiltrates a copy of the victims’ files. After encryption, Holy Ghost replaces all the file names with Base64-encoded versions of the file names and renames the extension .h0lyenc.
Image 3: H0ly Gh0st Ransom Note
Source: Microsoft.com
kimsuky
At the end of July 2022, researchers observed Kimsuky (also known as Black Banshee and Thallium), a North Korean threat actor, deploying a malicious browser extension for Google Chrome and Microsoft Edge. Using SHARPEXT, Kimsuky was able to steal content from actively logged in email accounts, as well as replace browser preference files. The threat actor targeted workers in Europe, the U.S., and South Korea.
Because the malware script is short and targeted email sessions were logged into by a legitimate user, browser providers had a hard time detecting SHARPEXT. Kimsuky has been active since 2012 and previously attacked South Korean bureaucracies and businesses. Kimsuky is a part of several hacker groups that act on behalf of North Korea, including Lazarus.
Tactics & Techniques
In August 2022, Kaspersky published a report detailing how Kimsuky ensures their malicious payloads are solely downloaded by their intended targets and not on the systems of security researchers who can find them. The group’s new techniques filter out invalid download requests, evidenced with their attack against targets in the Korean peninsula.
According to Kaspersky, the new techniques are so effective that researchers couldn’t obtain the final payloads despite being connected to the threat actor’s command and control server.
“We’ve seen that the Kimsuky group continuously evolves its malware infection schemes and adopts novel techniques to hinder analysis. The main difficulty in tracking this group is that it’s tough to acquire a full-infection chain. As we can see from this research, threat actors have recently adopted victim verification methodology in their command-and-control servers.” – Kaspersky Researchers – SecureList.com
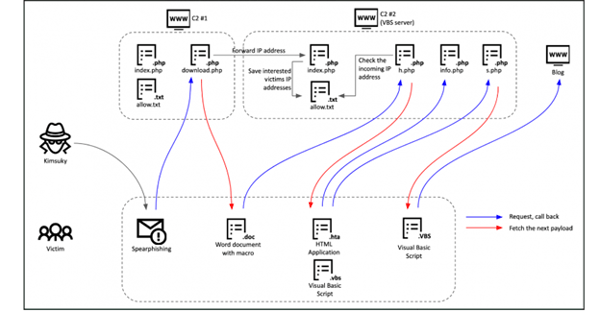
Kimsuky begins their attacks by sending phishing emails to diplomats, politicians, journalists, and professors in North and South Korea. Once the email is opened, the victim clicks on a link that takes them to a first stage C2 server. Next, the server checks and verifies a few parameters (visitors email address, OS, and the file [who].txt] before delivering a malicious document.
Dropped by the first-stage C2, a document containing a malicious macro connects the victim to the second-stage C2, fetches the next-stage payload, and runs it via the following process: mshta.exe. Next an .HTA file creates a scheduled task for auto-execution and profiles the victim – checking ProgramFiles folder paths, AV name, MS Office version, OS version, and more. There is also a payload that takes the victim to a legitimate blog to the next payload-download phase if the victim is a valid target.
Image 4: Kimsuky Infection Process
Source: Secure List
In January 2022, Kimsuky was behind the KONNI Remote Access Trojan (RAT). KONNI is a remote access tool that has been around since 2014 and has been attributed to North Korean threat groups. This malware is known to allow threat actors to steal files, grab screen shots, record key strokes, and execute arbitrary code. KONNI’s initial vector is social engineering and phishing email campaigns.
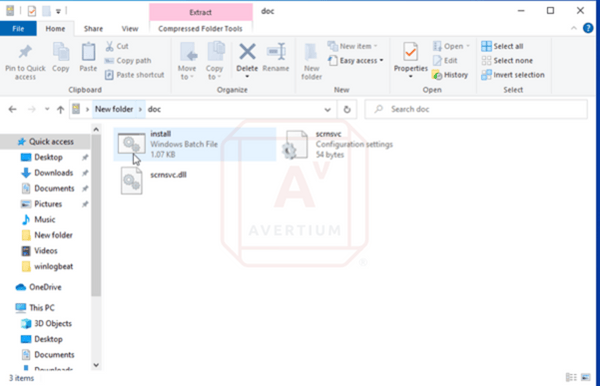
Kimsuky likely uses KONNI due to its stealth and flexibility. Avertium’s CTI team believes the stealthiness is achieved through string obfuscation and through adding additional processes into the malware to confuse advanced static analysis. The most recent KONNI variant revolves around the download of a malicious cabinet file. The file contains a malicious command script, a .dll file, and an encrypted ini file.
Image 5: KONNI Cabinet Files
Source: Avertium's Cyber Threat Intelligence Team
lazarus
Active since 2009, the North-Korean threat actor, Lazarus, is one of the most known APTs in cyber space. They are behind large-scale cyber espionage and ransomware campaigns, and they have been seen attacking the cryptocurrency market and the defense industry. With a variety of advanced tools, Lazarus has recently attempted to steal cryptocurrency from deBridge Finance – a cross-chain protocol that enables the decentralized transfer of assets between blockchains.
Tactics & Techniques
In August 2022, Lazarus used a phishing email to trick deBridge Finance employees into launching malware that collects information from Windows systems and allows the delivery of additional malicious code. The email is disguised as being from the company’s founder, Alex Smirnov, with information regarding salary changes.
The email included an HTML file that looks like a plain text PDF file containing a password. After clicking on the malicious and fake PDF file, a cloud storage location is opened which claims to provide a password-protected archive containing the PDF. Clicking on the archive launches a fake txt file to obtain the password.
The LNK file then executes the Command Prompt with a command that retrieves a payload from a remote location. If processes for ESET, Tencent, or Bitdefender are not present on their victim’s system, the malicious file is saved in the startup folder for persistence. Once persistence is achieved, the attacker is able to send out requests to their command-and-control server for further instructions. During this stage, Lazarus was able to collect details regarding the system’s operating system, CPU, running processes, and network adapters.
While some employees at deBridge Finance reported the emails as suspicious, others opened the document. Researchers were able to attribute the attack to Lazarus by thorough analysis. As a result, researchers found an overlap in file names and infrastructure used in a previous attack that was attributed to the group.
Lazarus’ current cryptocurrency campaign also targeted cryptocurrency firms in March 2022. During that time, Lazarus targeted Woo Network by sending a malicious document masquerading as a job offer from Coinbase. The file names are different than that of deBridge, but the same fake PDF was used to trick victims.
Lazarus has focused on using social engineering to establish a foothold on their victims’ computer before stealing cryptocurrency funds and assets. The group’s largest cryptocurrency heist was the April 2022 attack on Axie Infinity’s Ronin bridge network, where they stole almost $620 million in Ethereum.
north korea is the threat
North Korea has been linked to several attack campaigns. In July 2022, CISA and the FBI warned that North Korean state-sponsored attackers were targeting healthcare and public health sector organizations within the U.S.
In March 2022, Avertium issued an emergency Flash Notice regarding CVE-2022-1096 – a Google Chrome Zero-Day leveraged by North Korean attackers. The bug was a type confusion vulnerability and was being exploited by threat actors in the wild – making all Chromium based browsers vulnerable to attacks. Affecting 2 billion users, flaw allowed threat actors to execute arbitrary code on victim devices and allowed the threat actor to trick Chrome into running malicious code.
In July 2022, Avertium published a Threat Intelligence Report regarding North-Korean threat actors deploying Maui ransomware against healthcare organizations. According to CISA, the FBI observed and responded to several cyber security incidents within the healthcare sector due to Maui. The incidents included the encryption of servers responsible for providing healthcare services (diagnostic services, imaging services, intranet services, etc.). Maui has been infecting servers since May 2021 and the attacks have been attributed to Andariel. The group is known for using their attacks to cause discord in South Korea, as well as to generate revenue.
Andariel has been attributed to other ransomware attacks targeting media, construction, network services, and manufacturing in South Korea. Although the group seeks financial gain, they use their revenue for the North Korean government. Andarial has also been linked to cyberespionage attacks that involve data wiping and data theft. In July 2022, the U.S. State
Department announced rewards up to $10 million for information regarding Andarial.
In 2014, North Korea’s cyber attacks drew attention when Pyongyang’s threat actors attacked Sony Pictures in retaliation for a movie about North Korean leader, Kim Jong Un. Since then, threat actors from the country have attacked Bangladesh’s central bank, the U.K. National Health Service, and several cryptocurrency exchanges. Between 2011 and 2020, North Korean threat actors such as Lazarus have stolen more than $1 billion in cryptocurrency. In 2021, North Korean threat actors stole about $400 million in crypto coins. Researchers state that the money stolen is likely spend on North Korea’s weapons and other government priorities.
However, not only is North Korea intent on big pay days, but they also engage in conventional cyber espionage. In January 2022, Lazarus was spotted using two Microsoft Word documents that contained false Lockheed Martin employment information, which delivered payloads to the victims. Lazarus appears to be targeting job seekers in the aerospace and U.S. defense industries via spear-phishing attacks.
Although policymakers and foreign-policy experts have ignored North Korea’s increasingly sophisticated cyberoperations in the past, they are starting to see that North Korea is not a country one should doubt. While the country may be impoverished with a crumbling healthcare system, they have prioritized developing their cyber sector into a sophisticated operation. North Korea’s threat actors have been trained to steal billions of dollars across the globe.
When it comes to cyber attacks, most think of threat actors as their own group. However, North Korea has proven that we can’t analyze Lazarus without analyzing Kimsuky, H0ly Gh0st, and other North Korean threat actors because they have connections to one another in some way.
North Korean threat actors are working under the umbrella of North Korea, and very rarely will you see a threat actor from that county who is not cooperating with the government in some fashion. It’s time for cyber security professionals across the globe to start thinking about North Korea in a more strategic way and to accept that North Korea is a serious threat in cyberspace.
How Avertium is Protecting Our CUSTOMERS
It’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. Avertium offers the following services to keep your organization safe:
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
- Avertium offers Vulnerability Management to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium uses whitelisting tools like AppLocker to audit or block command-line interpreters.
- Avertium offers user awareness training through KnowBe4. The service also Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
Avertium’s Recommendations
Ransomware
- Require multifactor authentication to protect employees’ accounts from being used by attackers to obtain account credentials and use them to escalate privileges and move laterally within the network.
- Perform daily backups and keep them offline to avoid losing data.
- Disrupt network movements/investigation by way of creating separated segments of network, clear access hierarchy, and additional security for active directory, domain admin, and local domains – thus complicating a ransomware gang’s operations.
- Relying on outdated tools and point solutions will compromise your network or system. Better technology exists to detect complex attacks.
- Use anti-ransomware technology as a prevention method. Deploy prevention that works like next-generation antivirus and explicit anti-ransomware technology.
- Reduce the target by including these technical practices: close vulnerabilities, augment security hygiene, create and enforce strong general policies, and sustain backup and recovery practices.
APTs
- Tabletop Exercises: Have a good cyber incident response plan in place that has been tested with tabletop exercises.
- Security Review: Be sure to review the plan and improve it every time it’s tested on real cyber threats.
- Risk Analysis: Prevent an attack by ensuring your organization has a detailed defense strategy based on a risk analysis approach.
- Cybersecurity Education: Educate your employees on cyber security preparedness and the dangers of opening potentially malicious documents. Annual or quarterly training modules can help prevent threat actors from tricking employees into opening malicious email attachments.
MITRE Map
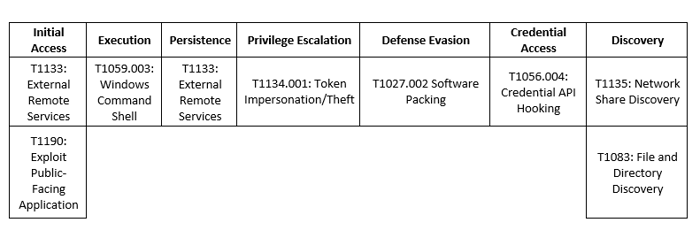
H0ly Gh0st
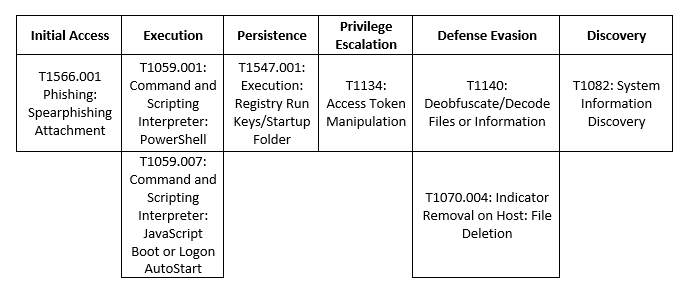
Kimsuky
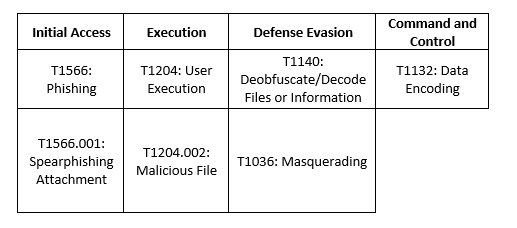
Lazarus
Indicators of Compromise (IoCs)
Kimsuky
- onedriver.epizy[.com]
- rf[.gd]
- 07b2457f6e71d0b75693b6fecf9c88e7
- 157e31eb70e2f28059f100f85317fcce
- 238e6952a990fd3f6b75569feceb26a2
- 23b5811baa6cc9e562185571579ce5bc
- 2c73cf2356a9005850fb2d07d024b2f2
- 3265b2d5e61971c43a076347fb405c4b
- 32dda97cab8876215d771e398dd10f84
- 3361fa242eb7e6162fd4682471f4e952
- 3fa45dcacf2193759086319c0d264341
- 40de99fb06e52e3364f2cd70f100ff71
- 4433edb19f368e56d903a4ed0aa25a2e
- 490b2496434e6a20dae758d0b6fc6e00
- 56b5fec59e118ba324ccee8a336f7f12
- 56df55ef50e9b9c891437c7148a0764a
- 596251e844abdaa77eeca905f0cb7677
- 5b5247ee7b43f51092ab07a1d1a31936
- 62b0fa29bcc317c59c5f5e7fd3a867bc
- 71def16f01ce0f57afe7b19c104a24e5
- 75ae786fe89491dc57509801c212fa8b
- 7953f5b1ed7b0b0ac778a2d47f44195c
- 7a3e966d30fe5d52cfe97d998e8c49cb
- 7fb868e6baf93a86d7a6a17ac00f4827
- 809f60589ee8be7daf075446c2180eaa
- 8289771e7eeffd28fb8a9e1bdeb3e86c
- 85f24b0f10b77b033e6e66ae8b7d55fc
- 86b523d2f19e1628e8c74602a51ebff9
- 8735788b2422c7ab910953178af57376
- 8b6d472fa9ec0023d7a35bdd7b8b2d4f
- 8bb7c8e8b723b02ffdcf6ff52444a810
- 8d28e28c1ee6f133441b6d71f7f8bcba
- 96f5ef3d58a750a6db60f2e0566dc6e6
- a871511ef8abae9f103a3dfe77b12b6d
- a87614a2c7c66c7f13f0b170e4837ede
- b18d2d4e77fc567306d406c75b75dc53
- b237b484c5c0fb020952e99b1134a527
- b6ba7e07b4867e4bd36dc9713744aedc
- b80d15cbb729e6ca86e3b41924407c30
- bb6662ed3f058a737674be6749c7e6f2
- bd0f789ace4def9196ce26588c3f41f8
- beb6601397e208d2793aaa7be297b0f4
- c0097cfa2e05ab1d18cf3dad93d98050
- c4a69dab3f8369d2f823c538590de345
- c5ad15506ab05f054d547587111d6393
- c791d7fc5216d4035825f4efb714ba0e
- d9f2acfed7ede76f110334e2c572b74e
- ddf966990bc4bdb40b67b8eda0ae1fd7
- dfb8d00ce89172bfc7ee7b73b37129a9
- e36cee3e23f3ab5557e547ce02b5bf3d
- e4df8b86d669e1eb36add172972bcb27
- edde6a385c86f60342831f24c3651925
- 364801240ed176e73a257ee86f573a2264027ecd
- 4b77fa3e1fe5a5d880467418f13ae6cb84366cca
- 8e6d7d7385eb2867bda605e5e3ac4e59dc7ae9c2
- de87429f36935c6610b3e338211dc388cbb290cf
- 2450961c630bc9a047a8b529323c55898c4a29ad5697154ac75d6828e85cfccd
- 5498c3eb2fb335aadcaf6c5d60560c5d2525997ba6af39b191f6092cb70a3aa6
H0ly Gh0st
- 99fc54786a72f32fd44c7391c2171ca31e72ca52725c68e2dde94d04c286fccd
- f8fc2445a9814ca8cf48a979bff7f182d6538f4d1ff438cf259268e8b4b76f86
- bea866b327a2dc2aa104b7ad7307008919c06620771ec3715a059e675d9f40af
- Command line: Example of new ScheduledTask to BTLC.exe
- exe /Q /c schtasks /create /tn lockertask /tr [File] /sc minute /mo 1 /F /ru system 1> \\127.0.0.1\ADMIN$\__[randomnumber] 2>&1
- 193[.]56[.]29[.]123
- H0lyGh0st@mail2tor[.]com
- http://DJVU[.SH]
- http://matmq3z3hiovia3voe2tix2x54sghc3tszj74xgdy4tqtypoycszqzqd[.onion]
- cloud-ex42.usaupload[.com]
Lazarus
- 147.231[.213]
- 0c2dde41d508941cf215fe8f1f7e03a7
- 114f22f3dd6928bed5c779fa918a8f11
- 1a536709554860fcc2c147374556205d
- 1fd8fef169bf48cfdcf506151264128c
- 210db61d1b11c1d233fd8a0645946074
- 2677f9871cb340750e582cb677d40e81
- 37505b6ff02a679e70885ccd60c13f3b
- 4382384feb5ad6b574f68e431006905e
- 44be20c67a80af8066f9401c5bee43cb
- 4548c7f157d300ec39b1821db4daa970
- 556abc167348fe96abfbf5079c3ad488
- 6df608342938f0d30a058c48bb9d8d4d
- 728b908e90930c73edeb1bf58b6a3a64
- 7b07cd6bb6b5d4ed6a2892a738fe892b
- 90f2b7845c203035f0d7096aa28dda83
- 96d86472ff283f6959b7a779f004dfba
- a225b7aff737dea737cd969fb307df23
- bb9ee3a6504fbf6a5486af04dbbb5da5
- bd416ea51f94d815b5b5b66861cbdcc5
- bdfb5071f5374f5c0a3714464b1fa5e6
- c32f40f304777df7cfab428a54bb818b
- d19dd02cf375d0d03f557556d5207061
- d7f6b09775b8d90d79404eda715461b7
- db0483aced77a7db130a6100aef67967
- e2e5644e77e75e422bde075f409d882e
- e732bc87033a935bd2d3d56c7772641b
- 0b97f9e91e374aa7d27823f9648b253b7c851b22
- 33e00fcd263ee84688c6aab238373efeeb536616
- 51c9d5a26c0924a74bdc6879335878eb60a9dcc2
- 5f593020255279aa5eb654a695e88cf53942f461
- 6402fafa0864460fea18a83ec4885bfe179734b2
- a132b3f3a88565cde7435dfe921bca17e5026ffd
- a2f513d27c18a885490e0e824c48d6cdb162af28
- b4d1a0a6aaa52d30ca7082a070cd33ef81a60962
- bb3a0dc01309162971ad6a11c5cb159fe93fedee
- c5ae757463b2015ef2d472fa26aec0f6aac1fa3f
- cf4ad12ef7de85a4a2d468082c510665d41abc12
- e206db4ddad984fe67bb44748f3ea6c38665ae8a
- e220659c6eee4c051d670bde48a4aa1d79eb4c65
- feab39a0e08849ef1c748931943dfb6de0ca922b
- 06d29b5f1611303a792bb335ecafdd228cf0a1ffd55629f8cc1b9ce25d7fb378
- 0ec2cfae9709b12236052e43356e37df2bf8601d76b48937cb14cc4c237c4ca7
- 2fc71184be22ed1b504b75d7bde6e46caac0bf63a913e7a74c3b65157f9bf1df
- 352d1850f2f6030fa4481728df2575448e88f28169b2f3702465d32b0e61476b
- 4e9ba92b357dcfa79f64f2ca829d31935b5a93059022414ca894a070b625da66
- 76a87057cb72139ed2a2c6776949aabd15134ba887b05bf1e56d46f3e97cda87
- 94fb3a34ecbde3435934f4cb44d86ff8ea37fda32b2b2ee17881c65654d91e8d
- a7c17e5fa55bcc60d4cff64dd37d0a1f0cc93f4f44b3cebd5633ca5af413e5cc
- ae7275988753fffb29bdb254babdf46773daf935b2721006fe66a1747af3d1d4
- b2a3d4261b0a6845d9ee4f395261946842964591804dfa474355b8e8bd1ad00f
- b63335a46a5096de1783da08b8709ce7b77c13073a2c6f87f7b392e95ae0d616
- c17234de3a14deadf84c7acc614345484d10c43a72cccb748de6357b0066c48a
- c4b29c58d2b2173a184c857d494f72a96ef5b7950261dc93a755d435e818a941
- For more IoCs, please click here.
Supporting Documentation
TraderTraitor: North Korean State-Sponsored APT Targets Blockchain Companies | CISA
Microsoft links Holy Ghost ransomware operation to North Korean hackers | TechRadar
CVE - CVE-2022-26352 (mitre.org)
Konni remote access Trojan receives 'significant' upgrades | ZDNET
North Korean hackers launch attack using Windows Update and GitHub | TechSpot
North Korean Attackers Use Malicious Browser Extension to Steal Email | Decipher (duo.com)
Maui ransomware operation linked to North Korean 'Andariel' hackers (bleepingcomputer.com)
Healthcare Ransomware Threats - MedusaLocker & Maui (avertium.com)
Flash Notice: [CVE-2022-1096] Zero-Day Google Chrome Type Confusion Vulnerability (avertium.com)
Underestimating North Korean Cyberattacks Leaves the West Vulnerable (foreignpolicy.com)
How 'Kimsuky' hackers ensure their malware only reach valid targets (bleepingcomputer.com)
Kimsuky’s GoldDragon cluster and its C2 operations | Securelist
deBridge Finance crypto platform targeted by Lazarus hackers (bleepingcomputer.com)
https://blog.talosintelligence.com/2017/05/konni-malware-under-radar-for-years.html
https://www.malwarebytes.com/blog/threat-intelligence/2022/01/konni-evolves-into-stealthier-rat
H0lyGh0st - North Korean Threat Group Strikes Back With New Ransomware (picussecurity.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.