How the Tables Have Turned - Russia vs. Ukraine Part Three
Executive Summary
In January 2022, Avertium’s Cyber Threat Intelligence Unit published an emergency Flash Notice detailing Microsoft’s discovery of a ransomware-like malware just days after 70 Ukrainian government websites were defaced by groups that were allegedly associated with the Russian secret service. The malware ended up being a wiper and impacted the Ukrainian Foreign Ministry, the Ministry of Education and Science, and other state services in Ukraine.
The defacement of the websites came at a time when the threat of invasion by Russia into Ukraine was growing daily. The security incident was just the beginning of a string of cyber attacks that would take place between Russia and Ukraine. Initially, it appeared as if Russia had the upper hand as they were constantly attacking Ukraine’s digital infrastructure.
However, over the past five months, things have changed, and it appears that Russia and Ukraine are now on equal footing regarding their cyber war. From WhisperGate to Anonymous, let’s take a look at initial attacks, retaliation, and what Russia and Ukraine’s current cyber war means for the future of cyberwarfare.
Russia vs. Ukraine - initial attacks
WhisperGate
In January 2022, Avertium addressed a wiper that defaced more than 70 Ukrainian government websites. The wiper was later attributed to Russia and was named WhisperGate. This wiper had two stages with the first stage being Whisper Gate’s tactical defense of disguising itself as ransomware. After the multi-stage malware executes via Impacket, it overwrites the MBR (Master Boot Record) on a system and includes a $10,000 Bitcoin ransom note. After the intended device powers down, the malware executes.
The second stage is described as a malicious file corrupter. After execution, stage2.exe downloads the next-stage malware hosted on a Discord channel, with the downloaded link hardcoded in the downloader. The malware then locates files in certain directories using dozens of the most common file extensions and overwrites the contents of the file with a fixed number of 0xCC bytes (total file size of 1MB). After over-writing, the destructor renames each file with a random four-byte extension.
Because WhisperGate happened at time of high tension between Russia and Ukraine, there was fear of a global impact – much like 2017’s NotPetya. NotPetya was a cyber attack against Ukraine that trickled down into other parts of the world and cost $10 billion global dollars. The attack left giant multinational corporations and government agencies unable to function. If an organization had any sort of business with Ukraine, they were affected by NotPetya.
Cyclops Blink & HermeticWiper
Cyclops Blink and HermeticWiper, began targeting the Ukraine in February 2022. Cyclops Blink is a sandworm malware and has been in the wild since 2019. The malware targets network devices - deploying malware that uses a modular structure, allowing operators to deploy second-stage payloads to infected devices. It has been described by CISA as sophisticated, affecting WatchGuard deices.
HermeticWiper was right on its heels as it deployed on Ukraine’s computer networks. Discovered by ESET, HermeticWiper was believed to be in the works for two months. Similar to WhisperGate, HermeticWiper abuses legitimate drivers from EaseUS Partition Master software to corrupt data before finally rebooting the computer. At the time, the Ukraine didn’t confirm or deny the cyber attack, but the attack happened just as things were heating up between Russia and Ukraine.
IsaacWiper, HermeticWizard, & HermeticRansom
After bombarding Ukraine with three wipers, Russia didn’t let up and continued their cyber attacks against the country with three more wipers – IsaacWiper, HermeticWizard, and HermeticRansom. HermeticWizard spreads HermeticWiper (aka DriveSlayer) across local networks via WMI and SMB. ESET observed that HermeticWizard is a worm that was deployed on a Ukrainian system on February 23, 2022. The malware starts by trying to find other machines on a local network before gathering known local IP addresses using certain Windows functions (i.e., GetTcpTable, GtAdapterAddresses, etc.).
HermeticRansom (aka PartyTicket) was also discovered by ESET, which is ransomware written in Go. It was used at the same time as the HermeticWiper campaign but has a much smaller deployment. ESET believes that the ransomware was deployed at the same time to hide the HermeticWiper’s actions, as it doesn’t use obfuscation mechanisms.
ESET discovered IsaacWiper at the end of February 2022, and it’s suspected that the threat actors used tools, like Impacket, to move laterally within networks and systems. ESET also observed a remote access tool called RemCom being deployed at the same time as IsaacWiper.
At this point during the conflict, Russia and Ukraine were clearly at odds but the three wipers were not attributed to Russia and the attackers remained unknown.
RURansom
Not long after WhisperGate, Cyclops Blink, HermeticWiper, IsaacWiper, HermeticWizard, and HermeticRansom, Ukraine launched their own attack called RURansom. In early March 2022, a malware variant dubbed RURansom started targeting entities in Russia. The malware is a .NET-based wiper that encrypts files on victim’s computers and spreads like a worm within their network or through USB devices. Because RURansom causes irreversible destruction of encrypted files, it can’t be called ransomware. The note that is left behind is more of a declaration than a ransomware note. Also, ransomware infections demand a ransom for decryption keys but RURansom’s keys are random and aren’t stored anywhere.
CaddyWiper
Soon after Ukraine’s attack with RURansom, ESET discovered another wiper – CaddyWiper. This wiper was seen on March 14, 2022, just a couple of weeks after RURansom was discovered. According to a series of tweets published by ESET Research, CaddyWiper’s operators had control of their target’s network before they deployed the malware via Microsoft Group Policy Objects (GPO).
ESET Research also observed that one organization’s default GPO was abused to spread the malware. They further reported that CaddyWiper avoids erasing data on domain controllers – a tactic they more than likely use to keep access inside the organization while continuing to disturb operations. Again, Russia’s goal was to destroy everything it could.
WhisperKill & DoubleZero
There were two wipers that Russia deployed which flew under the radar – WhisperKill and DoubleZero. The wipers were active in January 2022 and went after Ukraine’s systems. WhisperKill is a malicious software designed to permanently erase files by overwriting their contents with 1MB of 0xCC character sequence. After further research, analysts discovered that WhisperKill is more than 80% similar to WhiteBlackCrypt ransomware – a ransomware which was active in March 2021.
On March 17, 2022, another wiper named DoubleZero was seen targeting Ukrainian enterprises as Russia invaded the country. This is another wiper that wasn’t heavily covered by the media. The wiper is a .Net-based implant that destroys files, as well as registry keys and trees on infected endpoints. According to Cisco Talos, DoubleZero begins by checking if the current endpoint is one of the domain’s controllers. Once the endpoint’s name is found, the wiper stops executing.
DoubleZero’s goal is to overwrite files in drives by destroying them – excluding a specific list of locations hardcoded in the wiper. It also seeks to destroy non-system files first before destroying system-related files. If system related files are destroyed while the overwriting of other files is pending, it will lead to instability and bricking the system. In these cases, it’s possible to recover the files from the disks that aren’t overwritten yet. After DoubleZero destroys, it then shuts down the system by using ExitWindowsEx API call. These actions render all machines inoperable.
Conti takes a stance
Since the conflict between Russia and Ukraine, several cyber criminal gangs have chosen sides and have come forward regarding their plans to launch cyber attacks – Conti being one of those gangs. Conti is a Russian-speaking RaaS (ransomware-as-a-service) organization, who uses RaaS to deploy disruptive ransomware attacks that target critical infrastructure, like hospitals and government organizations.
While Russia attacked Ukraine, Conti took a pro-Russia stance - a stance which led to their chat logs being leaked weeks later by a Ukrainian patriot. What Conti didn’t expect was for their source code to be leaked along with the chat logs. The same Ukrainian patriot who leaked Conti’s old source code, leaked their newer one as well.
hacktivists for ukraine
After the back and forth with deploying wipers, hacktivists started to take matters into their own hands. One hacktivist group that comes to mind is Anonymous. In April 2022, NB65 (linked to Anonymous) stole files from the Russian space agency, Roscosmos, and stated that Putin no longer had control over spy satellites. They shared the server information on Twitter. Conti’s leaked source code was used against them by NB65, as the hacktivists stole sensitive files from Roscosmos.
According to the NB65’s Twitter account, they are only attacking Russian organizations and they won’t stop until Russia stops attacking Ukraine. They also stated that payments received from their ransomware attacks will be donated to humanitarian efforts in Ukraine.
This is where we start to see the tables turn as it pertains to the cyber war between Russia and Ukraine. While it once appeared as though Russia had the upper hand, pro-Ukraine hacktivists made it clear that they wouldn’t let Ukraine go down without a good fight.
Anonymous, NB65, DoomSec, AgainstTheWest, and other hacktivist groups continued to bombard Russia with cyber attacks. In May 2022, Anonymous released 184 GB of emails from Metprom Group, a Russian metallurgic engineering and investment group. During the same month, it was reported that Anonymous, and its affiliate groups, compromised 90% of databases owned by different Russian organizations and government in support of Ukraine. Russian IT infrastructure was being targeted every other day – including State-run TV channels and online video streaming platforms.
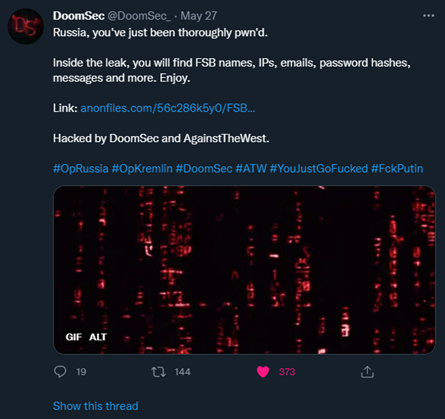
Also in May 2022, DoomSec and AgainstTheWest announced via Twitter that they pwn’d Russia and leaked FSB names, IP addresses, emails, password hashes, and other confidential messages. They even shared a link where you can find the files.
Image 1: Tweet from DoomSec
Source: Twitter.com
now what?
At this point, Russia appeared to be having a hard time keeping up with the attacks and didn’t retaliate as much as researchers thought. As Anonymous and other hacktivist groups constantly attacked Russia’s networks and systems, Russia devised another attack plan – a disinformation campaign.
In May 2022, Russian backed hackers launched a disinformation campaign to cause discord, panic, and division amongst Ukrainians. The campaign falsely claimed that Ukrainian President Volodymyr Zelensky committed suicide in a military bunker in Kyiv. The message was that because the president couldn’t keep his country safe, he had no other choice but to end his life. This turned out to be false.
Also, in April 2022, there was a rumor circulating that Ukraine’s Azov regiment, a Ukrainian special operations unit within the country’s National Guard, sought revenge against Zelensky for abandoning his troops in Mariupol. Telegram was also used to spread disinformation regarding the Ukrainian government and its corruption and ineptitude. The campaigns weren’t launched by Russia’s government but were launched by Russian backed hackers who wanted to cause internal unrest amongst Ukrainians.
current attacks
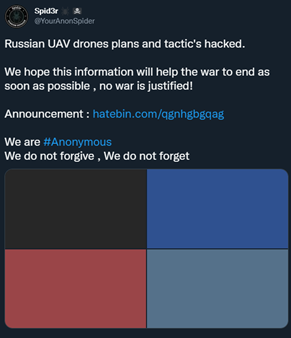
As of June 2022, Pro-Ukraine hacktivists are still consistently assailing Russia with cyber attacks. This month, Anonymous hacked Russia’s Public Chamber of the Krasnoyarsk and leaked 69k emails. The group also hacked into a weapons company that handles Russian Unmanned Aerial Vehicles, obtaining tactics and plans.
Image 2: Tweet from Spid3r
Source: Twitter.com
Also in June, Anonymous breached the website of the Russian Presidential Academy of National Economy as well as the Public Administration of Russian Federation, stating that they stand with Ukraine and won’t stop their attacks until Russian President Putin ends the war. Anonymous also took down the website of the National Intelligence Agency of Belarus.
Russia and the U.S.
Anonymous wasn’t the only one keeping busy. In mid-June 2022, the U.S. Department of Justice disrupted the Russian RSocks malware botnet used to hijack millions of computers and other IoT devices. The operation involved the FBI, as well as law enforcement from Germany, the Netherlands, and the United Kingdom.
According to Bill Toulas from BleepingComputer, the RSocks botnet was used to change residential computers into proxy servers, which would then allow the botnet’s customers to use them maliciously or appear as coming from a residential IP address. This kind of exploit could have been used for phishing operations, credential stuffing, or account takeover.
FBI agents began investigating the RSocks infrastructure in 2017 and during that time, 25,000 compromised devices were identified – many of them in the U.S. The devices were compromised via brute-forcing their passwords and installing software on breached computers. There were several large and private entities that were victims of the RSocks botnet, including universities, hotels, and an electronics manufacturer.
Now, there are reports of Russian intelligence agencies increasing their hacking and espionage operations and going after governments outside Ukraine, the U.S being the #1 target, according to Microsoft. The second target on Microsoft’s list was Poland with other popular targets being foreign ministries of NATO countries, think tanks, and critical infrastructure. Russia appears to be preparing to go after allied governments.
The Russian threat actor, Killnet, recently claimed responsibility for a DDoS attack on Lithuania (a European country). The group claimed the attack was in response to Vilnius’s decision to block transit of goods sanctioned by the European Union to the Russian exclave of Kaliningrad. Killnet stated that they’ll stop the DDoS attack when Lithuania lifts the blockade. So far, Killnet has disrupted 1652 of Lithuania’s web resources and Anonymous has officially launched a campaign to “take down” the Russian threat actor as a result.
Microsoft also stated that, by using artificial intelligence tools, they assessed Russia’s disinformation and propaganda campaign and found that their cyber influence operations increased the spread of Russian propaganda after the physical war began. It increased by 216% in Ukraine and by 82% in the United States.
In a rare public acknowledgement, the U.S. military confirmed that their hacking unit has conducted offensive cyber operations in support of Ukraine. The idea is to counter Russia in cyber space without escalating things to a physical war. President Biden pledged to leave Russia be as long as the U.S. and its allies aren’t attacked. However, after the U.S. and its allies imposed sanctions on the Kremlin, there is a serious chance of Russian cyber retaliation against U.S. infrastructure.
The Future of Cyber Warfare
The physical war between Russia and Ukraine has been the topic of discussion for months, but what does the cyber war between the two countries mean for the future of cyber warfare? Researchers are saying that Russia’s strategically timed cyber attacks before the physical war, will likely be present in future conflicts across the globe.
The future of modern warfare could be much more complex, more sophisticated, and more destructive moving forward. Such as weaponizing the internet and social media to influence the public. However, cyber warfare is still secondary to actual war. Matt Marsden, Vice President of Tanium, stated that Cyber warfare won’t replace conventional war. He sees it as “a force multiplier and as a way to increase or decrease the effectiveness of conventional or kinetic military operations.”
Since the war began, Russian backed threat actors have launched cyber attacks against Ukraine consistently – some were successful and some failed. Ukraine successfully stopped a Russian cyber attack in April 2022, before it hit computers that controlled an energy firm’s high voltage substations. The threat actor was affiliated with Russia’s military intelligence agency, GRU. This feat implies that Russia has underestimated Ukraine’s military and cyber capabilities.
“I think the Russians expected a walk in the park. Ukrainians have learned from past Russian cyberattacks.” – Paul Capasso (Vice President of Strategic Programs at Telos.
Because of previous history, Ukraine has invested in improving their cyber defenses. In 2015 Ukraine suffered a destructive Russian cyber attack that affected their power grid. The attack left more than 200k people without power for several hours.
The second devastating attack they suffered at the hands of Russia was 2017’s Petya attack. The attack disrupted Ukrainian banks, government ministries, and key companies. Researchers state that as cyber warfare evolves, threat actors will continue to use wipers and DDoS attacks during war.
How Avertium is Protecting Our CUSTOMERS
As we continue to watch the war between Russia and Ukraine, it’s important to remain vigilant and secure our cyber environments. The war could take a turn at any moment, so it’s important to remember the basics of cyber hygiene. Avertium offers the following services to help keep you organization safe:
- Fusion MXDR: Avertium now offers Fusion MXDR as the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
- Endpoint Detection and Response (EDR): Avertium's EDR is a platform of automated tools and capabilities that continuously monitor a system for suspicious activity within the security perimeter. These tools will recognize malicious activity from malware like WhisperGate and will immediately alert the security team, which allows for rapid investigation and containment of attacks on endpoints. We offer EDR endpoint protection through SentinelOne, Sophos, and Microsoft Defender.
- SentinelOne prevents threats and extends protection from the endpoint to beyond. Find threats and eliminate blind spots with autonomous, real-time, index-free threat ingestion and analysis that supports structured, unstructured, and semi-structured data.
- SentinelOne prevents threats and extends protection from the endpoint to beyond. Find threats and eliminate blind spots with autonomous, real-time, index-free threat ingestion and analysis that supports structured, unstructured, and semi-structured data.
- Security Information and Event Management (SIEM): Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A SIEM system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
- Digital Forensics and Incident Response (DFIR): To identify the source of your breach and the scope that it reached; you’ll want to include Avertium’s DFIR services in your protection plan. We offer DFIR to mitigate damage from a successful breach. This service is provided as an on-demand crisis response service, as well as a retainer-based program.
- Attack Surface Management (ASM): Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium offers ASM, so you’ll have no more blind spots.
- Third-Party Risk: Avertium also offers Vendor Risk Management.
Avertium’s Recommendations
The wipers we mentioned in our report have the potential to cause significant and widespread damage to critical infrastructure if deployed. Avertium urges you to implement the following recommendations per CISA:
- Regularly Review Your Cyber Hygiene
- Validate that all remote access to the organization’s network and privileged or administrative access requires multi-factor authentication.
- Ensure that software is up to date, prioritizing updates that address known exploited vulnerabilities identified by CISA.
- Confirm that the organization’s IT personnel have disabled all ports and protocols that are not essential for business purposes.
- If the organization is using cloud services, ensure that IT personnel have reviewed and implemented strong controls outlined in CISA's guidance.
- Sign up for CISA's free cyber hygiene services, including vulnerability scanning, to help reduce exposure to threats.
- Quickly Detect a Potential Intrusion
- Ensure that cybersecurity/IT personnel are focused on identifying and quickly assessing any unexpected or unusual network behavior.
- Enable logging in order to better investigate issues or events.
- Confirm that the organization's entire network is protected by antivirus/antimalware software and that signatures in these tools are updated.
- If working with Ukrainian organizations, take extra care to monitor, inspect, and isolate traffic from those organizations; closely review access controls for that traffic.
- Prepare to Respond if an Intrusion Occurs
- Designate a crisis-response team with main points of contact for a suspected cybersecurity incident and roles/ responsibilities within the organization, including technology, communications, legal, and business continuity.
- Assure availability of key personnel; identify means to provide surge support for responding to an incident.
- Conduct a tabletop exercise to ensure that all participants understand their roles during an incident.
- Maximize Your Organization’s Resilience to a Destructive Cyber Incident
- Test backup procedures to ensure that critical data can be rapidly restored if the organization is impacted by ransomware or a destructive cyberattack; ensure that backups are isolated from network connections.
- If using industrial control systems or operational technology, conduct a test of manual controls to ensure that critical functions remain operable if the organization’s network is unavailable or untrusted.
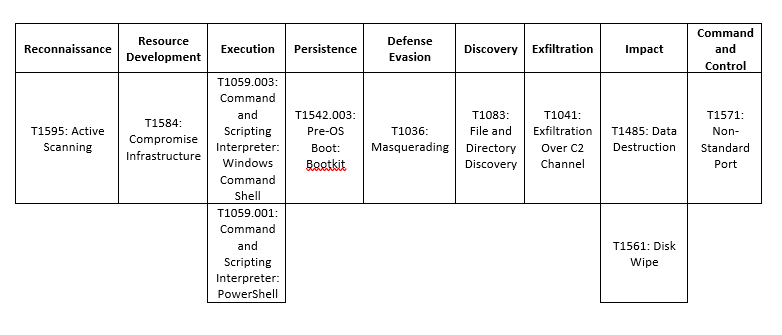
MITRE Map
Indicators of Compromise (IoCs)
Please click on the link for IoCs related to WhisperGate, HermeticWiper, RURansom, Cyclops Blink, Double Zero, WhisperKill, HermeticWizard, IsaacWiper, AcidRain, CaddyWiper, and NB65.
Supporting Documentation
Anonymous & its affiliates hacked 90% of Russian misconfigured databases (hackread.com)
Anonymous Hits Russia With Devastating Drone Hack That Could Speed Up End Of War (ibtimes.com)
Russian RSocks botnet disrupted after hacking millions of devices (bleepingcomputer.com)
Anonymous Declares Cyber War Against Pro-Russia Hacker Group Killnet (hackread.com)
Russian RSocks botnet disrupted after hacking millions of devices (bleepingcomputer.com)
https://fortune.com/2022/04/25/anonymous-hacks-into-russian-energy-publishes-emails/
Microsoft: Russian cyber spying targets 42 Ukraine allies | AP News
Russia's Killnet hacker group says it attacked Lithuania | Reuters
Anonymous claims hack on Russian drones (computing.co.uk)
Anonymous: the hacker collective that has declared cyberwar on Russia | Ukraine | The Guardian
US confirms military hackers have conducted cyber operations in support of Ukraine | CNN Politics
What the Russia-Ukraine war means for the future of cyber warfare | The Hill
Meet the Administrators of the RSOCKS Proxy Botnet – Krebs on Security
Hacktivists and cybercriminals wreak havoc in Russia - The Washington Post
Russian disinformation finds fertile ground in the West | Nature Human Behaviour
Feds Take Down Russian 'RSOCKS' Botnet (darkreading.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: Russia vs. Ukraine Part Two