Russia vs. Ukraine Part Two
Executive Summary
As the world continues to watch the physical war between Russia and Ukraine, cyber security professionals are watching the cyber war between the two countries. Since our last Threat Intelligence Report regarding the wiper-like worm “WhisperGate”, we have seen Russia and Ukraine go back and forth with cyber attacks.
Since January 2022, the world has watched threat actors like Conti and Anonymous declare their allegiance to either Russia or Ukraine, as well as make consistent threats. Let’s take another look into the cyber war between Russia and Ukraine, and how it could potentially affect the U.S.
russia vs. ukraine - the wipers
WhisperGate
In January 2022, we published a flash notice detailing Microsoft’s discovery of a destructive malware (DEV-0586/WhisperGate) used to corrupt the systems of organizations in Ukraine. A few days prior to Microsoft’s discovery, 70 Ukrainian government websites were defaced by groups that were allegedly associated with the Russian secret service. The malware is a wiper and impacted the Ukrainian Foreign Ministry, the Ministry of Education and Science, and other state services.
At the time, the wiper was deployed just as Russia was threatening to invade Ukraine. However, Microsoft couldn’t find any notable links between WhisperGate and Russia despite the timely coincidence. Russia denied defacing the websites, but the Ukrainian Digital Transformation Ministry stated that all evidence pointed back to Russia. Microsoft’s discovery was just the beginning of a slew of cyber attacks that would affect both countries.
Cyclops Blink & HermeticWiper
In February 2022, Avertium published a flash notice regarding a new sandworm malware named Cyclops Blink. The malware was identified by the United Kingdom’s (UK) National Cyber Security Centre, the Cyber Security and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the Federal Bureau of Investigation (FBI). The threat actor Sandworm (also known as Voodoo Bear) is behind Cyclops Blink, as well as the 2017 malware, NotPetya. Sandworm was previously linked to the Russian General Staff Main Intelligence Directorate – Russia’s military intelligence division.
Cyclops Blink has been in the wild since 2019 and targets network devices - deploying malware that uses a modular structure, allowing operators to deploy second-stage payloads to infected devices. How the malware is deployed, or the details regarding the second-stage module capabilities, is still unknown. CISA described the malware as sophisticated, and deployment appears to be indiscriminate and widespread – affecting WatchGuard devices.
Not long after the deployment of Cyclops Blink, a data wiper named HermeticWiper was deployed on Ukraine’s computer networks. The wiper was discovered by ESET and Broadcom’s Symantec, who believed the attack may have been in the works for almost two months. HermeticWiper is also very similar to WhisperGate.
HermeticWiper abuses legitimate drivers from EaseUS Partition Master software to corrupt data before finally rebooting the computer. When ESET analyzed one of the victims, they observed that the wiper was dropped via the default (domain policy) GPO – indicating the threat actors took control of the Active Directory server. At the time, the Ukrainian government didn’t confirm or deny the cyber attack, but the attack came at a time when the tension between Russia and Ukraine was at an all-time high.
IsaacWiper, HermeticWizard, & HermeticRansom
By the end of February 2022, ESET discovered three new cyber attacks that were deployed against Ukraine which included three wipers: IsaacWiper, HermeticWizard, and HermeticRansom. HermeticWizard spreads HermeticWiper (aka DriveSlayer) across local networks via WMI and SMB. ESET observed that HermeticWizard is a worm that was deployed on a Ukrainian system on February 23, 2022. The malware starts by trying to find other machines on a local network before gathering known local IP addresses using these Windows functions:
- DNSGetCacheDataTable
- GetIpNetTable
- WNetOpenEnumW(RESOURCE_GLOBALNET, RESOURCETYPE_ANY)
- NetServerEnum
- GetTcpTable
- GetAdaptersAddresses
ESET stated that after HermeticWizard finds a reachable machine, it drops the WMI spreader onto a disk and creates a new process with the following command line: <current folder>\<6 random letters>.ocx #1 -s <path to HermeticWizard> – i <target IP>. According to ESET, like HermeticWiper, HermeticWizard was signed by a code-signing certificate assigned to Hermetica Digital Ltd, which was issued on April 13th, 2021. ESET requested the issuing CA (DigiCert) to revoke the certificate, which it did on February 24th, 2022.
Reuters issued a report stating the Hermetica Digital certificate was stolen by threat actors from Hermetica Digital, which is a Cypriot company. The Hermetica owner from Cyprus didn’t know that his certificate was being used in a malicious malware attack against Ukraine. The owner is a 24-year-old game designer who runs his business from a house next to a Cypriot church on the outskirts of Nicosia – never expecting to wind up in a global crisis. Reuters believes that the attackers impersonated the Cypriot company to get the certificate from DigiCert.
HermeticRansom (aka PartyTicket) was also discovered by ESET, which is ransomware written in Go. It’s currently being used at the same time as the HermeticWiper campaign but has a much smaller deployment. ESET believes that the ransomware was deployed at the same time to hide the HermeticWiper’s actions, as it doesn’t use obfuscation mechanisms.
In addition to HermeticWizard and HermeticRansom, ESET detected IsaacWiper on February 24, 2022, and it’s suspected that the threat actors used tools, like Impacket, to move laterally within networks and systems. ESET also observed a remote access tool called RemCom being deployed at the same time as IsaacWiper.
At this point during the conflict, Russia and Ukraine were clearly at odds but the three wipers were not attributed to Russia and the attackers remained unknown.
RURansom vs. CaddyWiper
By March 2022, Ukraine and Russia were not only in a physical war, but in a cyber war as well. CaddyWiper and RURansom took center stage and it became clear that this was the beginning of retaliation between the two countries.
CaddyWiper, a data wiping malware, targeted Ukraine’s networks, while RURansom, which is also a wiper despite its name, targeted Russian networks. RURansom is a .NET- based wiper which targeted entities in Russia. The malware encrypts files on their victim’s computers and spreads like a worm within the network or through USB devices. It then leaves a wiper note in the victim’s machine.
Because RURansom causes irreversible destruction to encrypted files, it can’t be called ransomware. The note that is left behind is more of a declaration than a ransomware note. Also, ransomware infections demand a ransom for decryption keys but RURansom’s keys are random and aren’t stored anywhere. How do we know that the malware’s primary target is Russia? According to researchers from Cyble, RURansom is hard coded to only affect computers with Russian IP addresses.
CaddyWiper, the third wiper discovered by ESET, was observed on March 14, 2022 – just a couple of weeks after RURansom was discovered. CaddyWiper was compiled just two hours before its deployment and has targeted a few dozen systems within the governmental and financial sectors in Ukraine. Although CaddyWiper’s code is not similar to HermeticWiper or IsaacWiper, the goal is still the same – erase user data and partition information from attached drives to render systems unusable.
WhisperKill & DoubleZero - Under the Radar
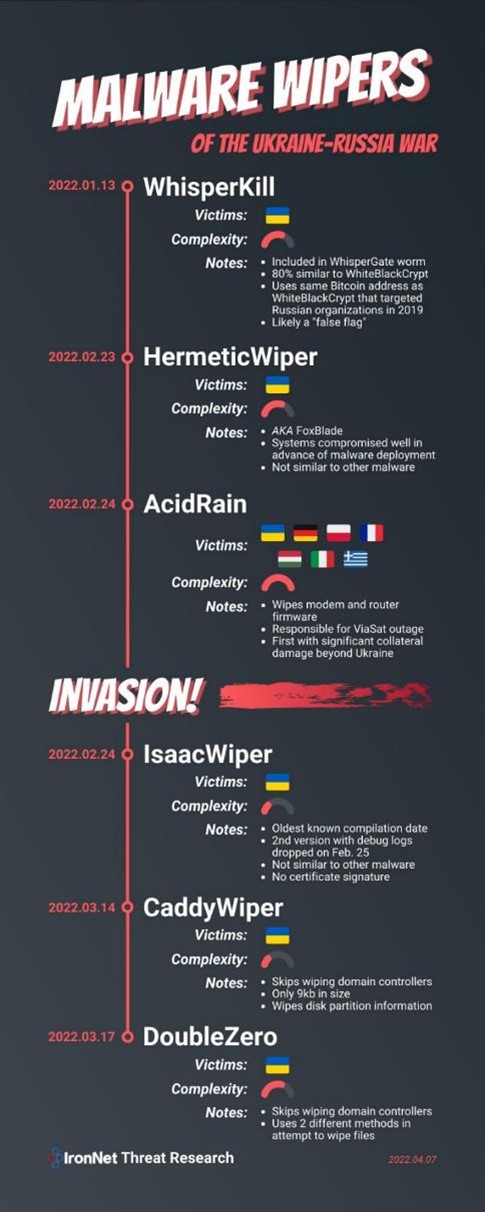
Unlike other cyber attacks, the goal for Russia and Ukraine is not financial gain, but destruction. Since January 2022, we have seen a total of seven wipers between the countries, including WhisperKill and DoubleZero which flew under the radar in January 2022.
According to the State Service of Special Communication and Information Protection of Ukraine (SSSCIP), WhisperKill is a malicious software designed to permanently erase files by overwriting their contents with 1MB of 0xCC character sequence. After further research, analysts discovered that WhisperKill is more than 80% similar to WhiteBlackCrypt ransomware – a ransomware which was active in March 2021.
Similar to WhisperGate, WhiteBlackCrypt masquerades as ransomware but is really a wiper designed to erase systems. Additionally, the wiper contains a bogus encryptor and the AES key is not saved, making it impossible for encrypted files to be recovered. Also, the ransom note WhisperKill leaves behind contains Ukraine’s coat of arms (a trident), but also contains the same Bitcoin addresses WhiteBlackCrypt used when it targeted Russian organizations in 2019. Two email addresses pointing back to WhiteBlackCrypt were left in the ransom note as well (Whiteblackgroup002@gmail[.com] and Wbgroup022@gmail[.com]).
Researchers believe that the threat actors put a trident on the ransom note in an attempt to imply that Ukraine is responsible for their own cyber attack. Cyber security researchers are calling the wiper a “false flag”.
“In addition, the author of the Telegram publication inexplicably (except for the trident and the anti-Russian activities of the extortioner) connects the hacker group Encrpt3d and the Special Operations Forces of the Armed Forces of Ukraine.
Thus, the deliberate use of the WhisperKill malware on January 13-14, 2022, which is morphologically similar to the WhiteBlackCrypt malware and manipulatively associated with the Special Operations Forces of the Armed Forces of Ukraine, is an attempt to provoke and distort reality to accuse Ukraine of the attacks in question.” - SSSCIPU
On March 17, 2022, another wiper named DoubleZero was seen targeting Ukrainian enterprises as Russia invaded the country. The wiper is a .Net-based implant that destroys files, as well as registry keys and trees on infected endpoints. According to Cisco Talos, DoubleZero begins by checking if the current endpoint is one of the domain’s controllers. Once the endpoint’s name is found, the wiper stops executing. The following privileges are obtained on the endpoint:
- SeTakeOwnershipPrivilege
- SeRestorePrivilege
- SeBackupPrivilege
- SeShutdownPrivilege
DoubleZero’s goal is to overwrite files in drives by destroying them – excluding a specific list of locations hardcoded in the wiper. It also seeks to destroy non-system files first before destroying system-related files. If system related files are destroyed while the overwriting of other files is pending, it will lead to instability and bricking the system. In these cases, it’s possible to recover the files from the disks that aren’t overwritten yet. After DoubleZero destroys, it then shuts down the system by using ExitWindowsEx API call. These actions render all machines inoperable.
AcidRain
On February 4, 2022, Viasat, a global communications company, suffered a cyber attack which rendered their KA-SAT modems inoperable in Ukraine. As a result, there was spillover from the attack which affected 5,800 Enercon wind turbines in Germany. The turbines were unable to communicate for remote monitoring control. According to Sentinel Labs, the turbines themselves were not rendered inoperable, but the remote monitoring and control of the wind turbines was inoperable due to satellite communications issues.
The timing of the attack happened when Russia invaded Ukraine and there was suspicion that Russia was attempting to take out Ukrainian military command-and-control capabilities by impeding satellite connectivity. On March 30, 2022, Viasat released a statement alluding to a cyber attack, but didn’t officially confirm it until March 31, 2022, during an interview with journalists at BleepingComputer.com. Viasat stated the attack happened in two phases:
- Phase 1: DDoS attack from “several SufBeam2 and SurfBeam2+ modems” located in Ukraine – temporarily knocked KA-SAT modems offline.
- Phase 2: Gradual disappearance of modems from Viasat service. Eutalsat provides the service, but the service is administered by Skylogic (an Italian company) as part of a transition plan.
Also, the attackers exploited a misconfigured VPN appliance to gain access to the trust management segment of the KA-SAT network. They then moved laterally and executed targeted management commands on a number of residential modems at the time. Sentinel Labs was not sure how legitimate commands could disrupt modems or how the commands could enable a DoS attack and render the devices unusable but not permanently bricked.
 Image 1: Tweet Regarding Viasat's Cyber Attack
Image 1: Tweet Regarding Viasat's Cyber Attack
Sentinel Labs believes that the threat actors behind the Viasat attack used the KA-SAT management mechanism in a supply-chain attack to push a wiper that would wipe modems and routers. The wiper would overwrite key data in the modem’s flash memory, making the modem inoperable and ultimately in need of being replaced.
Source: Twitter.com
On March 15, 2022, Sentinel Labs noticed that a MIPS ELF binary was uploaded to VirusTotal from Italy with the name “urop”. It’s suspected that the name is shorthand for “ukr”aine “op”eration, which is the acronym for the Ukrainian Association of Patriots, or a Russian slur for Ukrainians “ykpon”. However, only Viasat would be able to confirm if the malware was used in this particular case. The malware is now known as AcidRain.
According to Sentinel Labs, AcidRain is a straightforward wiper that performs an initial recursive overwrite and deletes non-standard files in the filesystem. After deleting the files, AcidRain attempts to destroy the data in several storage device files:
|
Targeted Device(s) |
Description |
|
/dev/sd* |
A generic block device |
|
/dev/mtdblock* |
Flash memory (common in routers and IoT devices) |
|
/dev/block/mtdblock* |
Another potential way of accessing flash memory |
|
/dev/mtd* |
The device file for flash memory that supports fileops |
|
/dev/mmcblk* |
For SD/MMC cards |
|
/dev/block/mmcblk* |
Another potential way of accessing SD/MMC cards |
|
/dev/loop* |
Virtual block devices |
According to Sentinel Lab’s case study, AcidRain iterates device file identifiers, opens the device file, and overwrites it with up to 0x40000 bytes of data or uses the following to erase: MEMGETINFO MEMUNLOCK, MEMERASE, and MEMWRITEOOB. To ensure the writes have been committed, AcidRain runs fsync syscall. After the wiping processes are complete, the device is rebooted.
Image 2: Attempt to Reboot Device
Although Sentinel Labs has not attributed the Viasat attacks to a threat actor, they did notice that AcidRain had developmental and code overlaps with a VPNFilter plugin that has been attributed to the Russian APT, Sandworm. As we stated earlier, Sandworm was responsible for 2017’s NotPetya and Cyclops Blink. Sentinel Labs noticed that both the VPNFilter and AcidRain shared binaries using the MEMGETINFO, MEMUNLOCK, and MEMERASE IOCTLS to erase device files.
In a statement to SearchSecurity, Viasat said it didn’t view the cyber incident as a supply chain attack or vulnerability, but the company is still investigating and will share more details when the investigation is complete.
Image 3: Malware Wipers
Source: IronNet Threat Research
Conti's Leaked Ransomware Source code & NB65
Just when we thought things couldn’t get any more interesting, they did. In April 2022, files were leaked by threat actors linked to Anonymous – NB65. The threat actor stole files from the Russian space agency, Roscosmos and stated that Russian President, Vladimir Putin, “no longer had control over spy satellites”. NB65 shared Roscosmos’ server information on Twitter to prove they had the space agency’s files.
The curve ball is that 66% of the source code for one of the files matched Conti’s leaked ransomware source code – turning out to be a modified version. The group stated that their encryptor is based on the first Conti source code leak and is modified for each victim, making existing decryptors unusable. In a previous Threat Intelligence Report, we discussed Conti’s chat logs that were leaked by a Ukrainian researcher and patriot who chose to stay in Ukraine and fight for his country. This took place just after Conti took a strong stance and sided with Russia regarding the war against Ukraine.
Source: RedPacketSecurity
Conti is the threat actor behind some of the most devastating cyber attacks in history. They are a Russian-speaking RaaS organization that uses RaaS to deploy disruptive ransomware attacks that target critical infrastructure, like hospitals and government organizations. They specialize in double extortion operations of simultaneous data encryption and data exfiltration for financial gain.
Now, we see that the threat actor’s source code is being used against them by NB65, who is associated with Anonymous. According to the NB65’s Twitter account, they are only attacking Russian organizations and they won’t stop until Russia stops attacking Ukraine. They also stated that payments received from their ransomware attacks will be donated to humanitarian efforts in Ukraine.
Image 5: A Tweet from NB65
Source: Twitter.com
Image 6: A Tweet from NB65
Source: Twitter.com
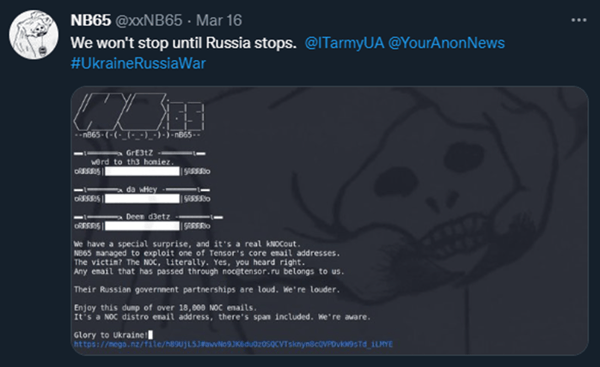
It’s not unusual for ransomware gangs to target companies and encrypt their data, but it is unusual for Russian organizations to be attacked in the same manner. The reason why Russian hackers steer clear of attacking Russia is because they believe that if they don’t attack Russian interests, then Russia will overlook their cyber attacks on other countries. NB65 has now changed that narrative, as they have breached Russian organizations for the past month – including document management operator, Tensor, and VGTRK, a state-owned Russian Television and Radio broadcaster. NB65 successfully stole 786.2 GB of data (9,000 emails and 4,000 files) from VGTRK, Russia’s largest state-owned media corporation. The only way Russian organizations will be able to decrypt is to contact NB65. So far, the threat actors have not received any communications from their Russian victims and the group does not expect them to reach out.
anonymous
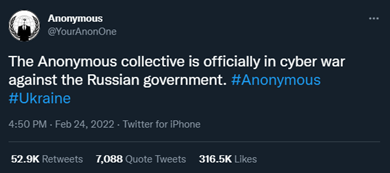
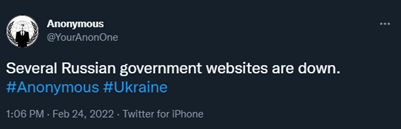
When the war started, Anonymous sided with Ukraine and made various threats against Russia and companies who do business with Russia. So far, they have followed through on several of those threats. In February 2022, Anonymous took down several Russian government websites and hacked Russian state television channels in order to broadcast what they stated are “the true events” of the war. By March 1, 2022, Anonymous leaked the database of the Ministry of Economic Development of Russia.
Image 7: Tweet from Anonymous
Source: Twitter.com
Image 8: Tweet from Anonymous
Source: Twitter.com
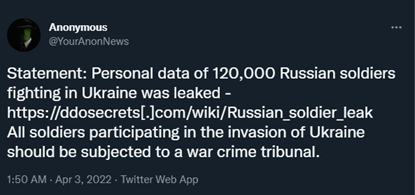
Lisa Forte, a partner at the security firm Red Goat, stated that although Anonymous’ attacks have been basic, they are creative and difficult to execute. She believes that most of the attacks have been DDoS attacks – a simple but effective way to flood networks and take websites offline. In addition to attacking Russian companies, Anonymous has also stolen the personal information of 120,000 Russian soldiers – the information stolen includes addresses, passport numbers, dates of birth, and unit affiliations. The group has also hacked hundreds of surveillance cameras in Russia, releasing messages against the invasion of Ukraine.
Image 9: Tweet from Anonymous
Source: Twitter.com
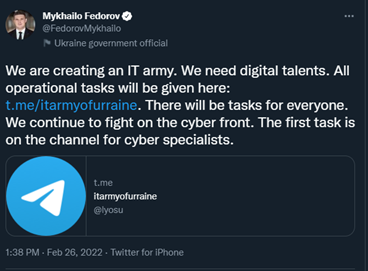
The group has no plans on slowing down and they have continued to threaten Russia on an almost daily basis via Twitter. Additionally, Ukraine’s Secretary of Digital Affairs, Mykhailo Fedorov, declared on Twitter that the country is creating an IT army and they would need digital talents – anyone is welcome to join via Telegram. The group has reached more than 300,000 members.
Image 10: Tweet from Anonymous
Source: Twitter.com
Because Anonymous isn’t a structured organization, anyone interested in joining can do so if they simply claim to be a part of the group. When an Anonymous associated Twitter account with thousands of followers was asked if it was the official Twitter account for the group, the account stated that they are all a team and there isn’t an official Anonymous Twitter account. As long as you are willing to take on the values of Anonymous, you can join.
government funded Apts
Hacktivists like Anonymous have been known as cyberspace “justice warriors” and thus earn the respect of the hacker community, as well as the general public. Anonymous’ signature Guy Fawkes mask, which was used in the movie V for Vendetta, is dramatic and appealing to the current generation looking to carry out cyber attacks without revealing themselves. Because the members of Anonymous are unknown, their members are interchangeable. No one knows if a country’s secret services have been involved in hacktivism in order to cover up an attack, but government funded hacker groups do exist – they’re known as APTs.
We’ve seen it happen in 2017 when the Russian group Voodoo Bear attacked Ukraine with NotPetya. What was supposed to be a targeted attack, ended up spreading across the globe. Voodoo Bear also attacked telecommunications networks under the name “F Society” – a fictional cyber activist group from a TV series called Mr. Robot.
Adam Meyers from CrowdStrike stated that was the first time Voodoo Bear executed a false-flag attack. In 2007, Estonia’s digital infrastructure was under attack when authorities moved a Soviet monument to a less-visible part of the city of Tallinn. The attacks came from hundreds of personal computers located in dozens of countries, but NATO believed that Moscow was behind the attack. The Kremlin denies responsibility.
The APT MuddyWater is also a government sponsored APT that has targeted several government and private sector organizations in the defense, oil and natural gas, local government, and telecommunications industries.
how does this affect the u.s.?
At the end of March 2022, President Biden warned the U.S. that Russian cyberattacks may very well be a possibility and that the country will use every tool to prevent and respond to those attacks. Because the U.S. has imposed sanctions on Russia, it’s possible that Moscow could act in retaliation. According to President Biden, the U.S. believes that the Russian government is exploring their options and U.S. companies should accelerate their efforts to protect they cyber environments.
“If you have not already done so, I urge our private sector partners to harden your cyber defenses immediately by implementing the best practices we have developed together over the last year. You have the power, the capacity, and the responsibility to strengthen the cybersecurity and resilience of the critical services and technologies on which Americans rely. We need everyone to do their part to meet one of the defining threats of our time — your vigilance and urgency today can prevent or mitigate attacks tomorrow.” – President Biden – Whitehouse.gov
Since tensions started rising between Russia and Ukraine, the cyber security world has been on edge, bracing themselves for either an attack on the U.S. or spill over from an attack on Ukraine. NotPetya was a Russian cyber attack that cyber security analysts suspected was to primarily affect Ukraine. However, the attack ended up having a global impact (spill over) and cost $10 billion global dollars. The attack left giant multinational corporations and government agencies unable to function. If an organization had any sort of business with Ukraine, they were affected by NotPetya.
How Avertium is Protecting Our CUSTOMERS
As we continue to watch the war between Russia and Ukraine, it’s important to remain vigilant and secure our cyber environments. As mentioned above, there is no telling how this will affect the U.S. and cyber warfare can easily spiral out of control. In times of crisis, it is tempting to seek a “silver bullet” that will protect against a new threat. It is important to remember the basics of cyber hygiene. Avertium offers the following services to help keep your organization safe:
- Endpoint Detection and Response (EDR): Avertium's EDR is a platform of automated tools and capabilities that continuously monitor a system for suspicious activity within the security perimeter. These tools will recognize malicious activity from malware like WhisperGate and will immediately alert the security team, which allows for rapid investigation and containment of attacks on endpoints. We offer EDR endpoint protection through SentinelOne, Sophos, and Microsoft Defender.
- SentinelOne prevents threats and extends protection from the endpoint to beyond. Find threats and eliminate blind spots with autonomous, real-time, index-free threat ingestion and analysis that supports structured, unstructured, and semi-structured data.
- Security Information and Event Management (SIEM): Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A SIEM system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
- Digital Forensics and Incident Response (DFIR): To identify the source of your breach and the scope that it reached; you’ll want to include Avertium’s DFIR services in your protection plan. We offer DFIR to mitigate damage from a successful breach. This service is provided as an on-demand crisis response service, as well as a retainer-based program.
- Extended Detection and Response (XDR): Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- Attack Surface Management (ASM): Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium offers ASM, so you’ll have no more blind spots.
- Third-Party Risk: Avertium also offers Vendor Risk Management.
Avertium’s Recommendations
The wipers we mentioned in our report have the potential to cause significant and widespread damage to critical infrastructure if deployed. Avertium urges you to implement the following recommendations per CISA:
Regularly Review Your Cyber Hygiene
- Validate that all remote access to the organization’s network and privileged or administrative access requires multi-factor authentication.
- Ensure that software is up to date, prioritizing updates that address known exploited vulnerabilities identified by CISA.
- Confirm that the organization’s IT personnel have disabled all ports and protocols that are not essential for business purposes.
- If the organization is using cloud services, ensure that IT personnel have reviewed and implemented strong controls outlined in CISA's guidance.
- Sign up for CISA's free cyber hygiene services, including vulnerability scanning, to help reduce exposure to threats.
Quickly Detect a Potential Intrusion
- Ensure that cybersecurity/IT personnel are focused on identifying and quickly assessing any unexpected or unusual network behavior.
- Enable logging in order to better investigate issues or events.
- Confirm that the organization's entire network is protected by antivirus/antimalware software and that signatures in these tools are updated.
- If working with Ukrainian organizations, take extra care to monitor, inspect, and isolate traffic from those organizations; closely review access controls for that traffic.
Prepare to Respond if an Intrusion Occurs
- Designate a crisis-response team with main points of contact for a suspected cybersecurity incident and roles/ responsibilities within the organization, including technology, communications, legal, and business continuity.
- Assure availability of key personnel; identify means to provide surge support for responding to an incident.
- Conduct a tabletop exercise to ensure that all participants understand their roles during an incident.
Maximize Your Organization’s Resilience to a Destructive Cyber Incident
- Test backup procedures to ensure that critical data can be rapidly restored if the organization is impacted by ransomware or a destructive cyberattack; ensure that backups are isolated from network connections.
- If using industrial control systems or operational technology, conduct a test of manual controls to ensure that critical functions remain operable if the organization’s network is unavailable or untrusted.
MITRE Mapping
|
[T1059.003] Command and Scripting Interpreter: Windows Command Shell |
[T1059.001] Command and Scripting Interpreter: PowerShell
|
[T1542.003] Pre-OS Boot: Bootkit
|
[T1485] Data Destruction
|
[T1561] Disk Wipe
|
[T1041] Exfiltration Over C2 Channel
|
|
WhisperGate |
WhisperGate |
WhisperGate |
IsaacWiper |
WhisperKill |
CaddyWiper |
|
HermeticWiper |
HermeticWiper |
HermeticWiper |
HermeticWizard |
DoubleZero |
Cyclops Blink |
|
|
RURansom |
Cyclops Blink |
WhisperGate |
WhisperGate |
AcidRain |
|
|
|
|
HermeticWiper |
AcidRain |
|
|
|
|
|
Cyclops Blink |
IsaacWiper |
|
|
|
|
|
RURansom |
|
|
|
|
|
|
AcidRain |
|
|
|
[T1571] Non-Standard Port
|
[T1036] Masquerading
|
[T1584] Compromise Infrastructure |
[T1083] File and Directory Discovery
|
[T1595] Active Scanning |
|
Cyclops Blink |
Cyclops Blink |
RURansom |
WhisperGate |
RURansom |
|
|
WhisperGate |
WhisperGate |
|
|
|
|
HermeticWiper |
HermeticWiper |
|
|
|
|
WhisperKill |
CaddyWiper |
|
|
|
|
|
Cyclops Blink |
|
|
Indicators of Compromise (IoCs)
WhisperGate
- 159.135[.233]
- 1AVNM68gj6PGPFcJuftKATa4WLnzg8fpfv
- 14c8482f302b5e81e3fa1b18a509289d
- 5481d3c166d06f7a29e429880a558c87
- 5d5c99a08a7d927346ca2dafa7973fc1
- 78c855a088924e92a7f60d661c3d1845
- 7c8cb5598e724d34384cce7402b11f0e
- b3370eb3c5ef6c536195b3bea0120929
- e0f11b2047ecc48343d427e8955bc8c7
- e61518ae9454a563b8f842286bbdb87b
- 16525cb2fd86dce842107eb1ba6174b23f188537
- 189166d382c73c242ba45889d57980548d4ba37e
- 82d29b52e35e7938e7ee610c04ea9daaf5e08e90
- b2d863fc444b99c479859ad7f012b840f896172e
- 34ca75a8c190f20b8a7596afeb255f2228cb2467bd210b2637965b61ac7ea907
- 35feefe6bd2b982cb1a5d4c1d094e8665c51752d0a6f7e3cae546d770c280f3a
- 923eb77b3c9e11d6c56052318c119c1a22d11ab71675e6b95d05eeb73d1accd6
- 9ef7dbd3da51332a78eff19146d21c82957821e464e8133e9594a07d716d892d
- a196c6b8ffcb97ffb276d04f354696e2391311db3841ae16c8c9f56f36a38e92
- dcbbae5a1c61dbbbb7dcd6dc5dd1eb1169f5329958d38b58c3fd9384081c9b78
- 111.111[.111]
- 3031417f8bd82b8a4204ae8f114fa41d45467028
- 7e7d9ed69af1faa628884f409065b34e078716ae
- f831fff298ca8205ced4ae6a00cf4ad8de0fb8a7
RURansom
- 01ae141dd0fb97e69e6ea7d6bf22ab32
- 191e51cd0ca14edb8f06c32dcba242f0
- 6cb4e946c2271d28a4dee167f274bb80
- 8fe6f25fc7e8c0caab2fdca8b9a3be89
- 9c3316a9ff084ed4d0d072df5935f52d
- fe43de9ab92ac5f6f7016ba105c1cb4e
- 0bea48fcf825a50f6bf05976ecbb66ac1c3daa6b
- 27a16e1367fd3e943a56d564add967ad4da879d8
- a30bf5d046b6255fa2c4b029abbcf734824a7f15
- c35ab665f631c483e6ec315fda0c01ba4558c8f2
- c6ef59aa3f0cd1bb727e2464bb728ab79342ad32
- fbeb9eb14a68943551b0bf95f20de207d2c761f6
- 107da216ad99b7c0171745fe7f826e51b27b1812d435b55c3ddb801e23137d8f
- 1f36898228197ee30c7b0ec0e48e804caa6edec33e3a91eeaf7aa2c5bbb9c6e0
- 610ec163e7b34abd5587616db8dac7e34b1aef68d0260510854d6b3912fb0008
- 696b6b9f43e53387f7cef14c5da9b6c02b6bf4095849885d36479f8996e7e473
- 8f2ea18ed82085574888a03547a020b7009e05ae0ecbf4e9e0b8fe8502059aae
- 979f9d1e019d9172af73428a1b3cbdff8aec8fdbe0f67cba48971a36f5001da9
- 013addcf6e3f3a2e7ff441ccdc0433ce
- 318d857c4b4c12b1b5d67f37fad616e9
- 4ecd4debe942f6a5e45732d8d073b5ec
- 5028a73d50a0a2bd0abe6a24c660cb65
- 84e5cf74ecbed6caa3e88b1e00e1dc0d
- 94a65c7f033faf7efb1348df4a79f498
- 9d298f3eaff0db4fb1f5b3160911e3ee
- a6988a9060278741c0ba3e9028de1f97
- a938dbd999f4a1ba7d537c9181c8d902
- e09183041930f37a38d0a776a63aa673
- e5e98aa9efcd4bd83245524ff430b28e
- 05c63ce49129f768d31c4bdb62ef5fb53eb41b54
- 06c6dc34a9728f67038a7d41bcbe2372a9c4e6e4
- 085b697d49b103c4a42b20aa8b2f5c4730212653
- 34b9694fe6f5adb63f58217f80b4abb53c48e320
- 5104c127b4d56ffe93016582401c250630f6d274
- 8746ab9039ad88ebf8aa822473fa2f9947131d19
- 97dae0c8fc302b6cbbc2e31c756909a16630d9c5
- b1261722dd055dc6a5e2d2f3839a91390eac24e8
- dd2a120b485cbf9ff7dd7435ee1d1a3fc4596862
- df4a28bdd8b743c16d2c9917c6d39030c07f2c09
- ed2b4ef1c2f1814c40326a094f8874c683dec68b
- 009ce5fcce062d699db46559badcf259eb925fcfcf374c0bdea8eb13d5750edf
- 2548ad9263dd94109ab22393a08f77364d96c48b0b96640cb530818adb9c08f0
- 26e75390015ba36c2723d35ed7a227064892979ad331e0a728e39673feaa24c2
- 70e8a9b39aa7dd91c461c32ddfeb090b3699e5984beb610787c92afd24ad546b
- 7c935dcd672c4854495f41008120288e8e1c144089f1f06a23bd0a0f52a544b1
- a932b37f6ebadfca08beb990cf784ac247317abbc42c72a9961f8d4a1fe7e1fb
- ae00bb69f06936ac9afb0475d4b3ddf592e4c61e68327be2051211533a57d919
- ceebcd4472623db39026ae89dc0737d0cdec631cd763d9717d0f4a822a3a2085
- d02ede8735c319012923efc6d4befa78f39fcb6c4ce40cb37a45b419a2efc923
- e0c4021b38f4d2f1e13d0a8374c8ef081be458fc3031e7ad49795a65a013cb43
- fb4f3d9421cf8d35de950ad52ff4dca3a0c3e84c3c770c09c3cf6bbcc540e9d4
CaddyWiper
- 98b3fb74b3e8b3f9b05a82473551c5a77b576d54
- a294620543334a721a2ae8eaaf9680a0786f4b9a216d75b55cfd28f39e9430ea
- 98b3fb74b3e8b3f9b05a82473551c5a77b576d54
AcidRain
- 20ea405d79b4de1b90de54a442952a45
- ecbe1b1e30a1f4bffaf1d374014c877f
- 261d012caa96d3e3b059a98388f743fb8d39fbd5
- 86906b140b019fdedaaba73948d0c8f96a6b1b42
- 47f521bd6be19f823bfd3a72d851d6f3440a6c4cc3d940190bdc9b6dd53a83d6
- 9b4dfaca873961174ba935fddaf696145afe7bbf5734509f95feb54f3584fd9a
Cyclops Blink
- bf24ade7-1a90-54a5-8664-fa993256e66f
- 50e5c6d8-f1ee-593a-bf2c-b99c8c2d6a10
- 512e379a-2b3b-5f97-8dd2-03519971c66f
- 9d16715a-9e88-5305-8e67-110b4dde6848
- d87d5a66-05df-56c4-9311-6e2af3fde2e8
- a8174e4e-7b98-5c0a-9dff-7e6485ed9adc
- a8174e4e-7b98-5c0a-9dff-7e6485ed9adc
- /usr/bin/cpd
- /var/tmp/a.tmp
- rootfs_cfg
- 43.220[.]234
- 80.68[.]193
- 152.254[.]170
- 81.37[.]50
- 62.153[.]174
- 230.110[.]137
- 63.245[.]175
- 103.208[.]182
- 255.126[.]65
- 134.89[.]167
- 4.177[.]118
- 199.247[.]222
- 99.163[.]162
- 71.147[.]186
- 159.248[.]137
- 155.38[.]210
- 57.80[.]18
- 0.169[.]250
- 202.147[.]10
- 234.179[.]113
- 82.169[.]99
- 51.177[.]66
- 15.113[.]188
- 153.75[.]103
- 192.30[.]125
HermeticWiper
- 912342F1C840A42F6B74132F8A7C4FFE7D40FB77
- 61B25D11392172E587D8DA3045812A66C3385451
- Win32/KillDisk[.NCV] trojan 6/n
HermeticRansom (also known as PartyTicket)
- 4dc13bb83a16d4ff9865a51b3e4d24112327c526c1392e14d56f20d6f4eaf382
HermeticWizard and IsaacWiper
- 6983f7001de10f4d19fc2d794c3eb534
- bdf30adb4e19aff249e7da26b7f33ead
- d57f1811d8258d8d277cd9f53657eef9
- 0e84aff18d42fc691cb1104018f44403c325ad21
- 23873bf2670cf64c2440058130548d4e4da412dd
- 379ff9236f0f72963920232f4a0782911a6bd7f7
- 3c54c9a49a8ddca02189fe15fea52fe24f41a86f
- 61b25d11392172e587d8da3045812a66c3385451
- 6b5958bfabfe7c731193adb96880b225c8505b73
- 736a4cfad1ed83a6a0b75b0474d5e01a3a36f950
- 87bd9404a68035f8d70804a5159a37d1eb0a3568
- 912342f1c840a42f6b74132f8a7c4ffe7d40fb77
- ac5b6f16fc5115f0e2327a589246ba00b41439c2
- ad602039c6f0237d4a997d5640e92ce5e2b3bba3
- b33dd3ee12f9e6c150c964ea21147bf6b7f7afa9
- e9b96e9b86fad28d950ca428879168e0894d854f
- f32d791ec9e6385a91b45942c230f52aff1626df
- 23ef301ddba39bb00f0819d2061c9c14d17dc30f780a945920a51bc3ba0198a4
- 2c7732da3dcfc82f60f063f2ec9fa09f9d38d5cfbe80c850ded44de43bdb666d
- 3c2fe308c0a563e06263bbacf793bbe9b2259d795fcc36b953793a7e499e7f71
DoubleZero
- d897f07ae6f42de8f35e2b05f5ef5733d7ec599d5e786d3225e66ca605a48f53
- 8dd8b9bd94de1e72f0c400c5f32dcefc114cc0a5bf14b74ba6edc19fd4aeb2a5
- 3b2e708eaa4744c76a633391cf2c983f4a098b46436525619e5ea44e105355fe
- 30b3cbe8817ed75d8221059e4be35d5624bd6b5dc921d4991a7adc4c3eb5de4a
WhisperKill
- b4a5e03e11767a026227c40b316112b9
- acb50d48ca3fa765fe254f80a6075ab08ee724f1
- 420960a10e3f3730ab124bfefceedc032ef06c7b38fa014b2b59462365a5f08d
- 14c8482f302b5e81e3fa1b18a509289d
- 178b0739ac2668910277cbf13f6386e8
- 20bb6aec6889f9135d29ad40f4a25c23
- 3907c7fbd4148395284d8e6e3c1dba5d
- 3d00076c999de471d8e966e6465d9474
- 5d5c99a08a7d927346ca2dafa7973fc1
- 78e941e780adc1a159fdc7090194c96d
- 833cd8302870af5a50b3a09af0420297
- 8842acb150e1625ff20a84190073ece6
- 9fe8203b06c899d15cb20d2497103dbb
- b3370eb3c5ef6c536195b3bea0120929
- e4aca1b6ea6ec906ad40e63a5d309f96
- e61518ae9454a563b8f842286bbdb87b
- eecaecd170ef3d7a5976d435f6d03ef8
- fd4de6bb19fac13487ea72d938999fbd
- 11eeade0c1a40abece43f6c1381d80584fdb3ed1
- 16525cb2fd86dce842107eb1ba6174b23f188537
- 189166d382c73c242ba45889d57980548d4ba37e
- 374c9059fce14f0d61945ecb7d9a96d6ef0ea31b
- 4d303e08764073ff13b6f439ff861d22ee387a39
- 55048b1d190cd90d16329d3a40daefe09dc282f6
- 56f526a838ae6dc1b8c7daf5a844aaf4115a3fd5
- 7509dac85f4d2e984b949e5bb92d66778f9c0fb9
- 82d29b52e35e7938e7ee610c04ea9daaf5e08e90
- 833d60a91f1726411898ecb4af0352cf47d24712
- 9cd8a786572a7ee8713492302555fe4ce3432911
- a67205dc84ec29eb71bb259b19c1a1783865c0fc
- b2d863fc444b99c479859ad7f012b840f896172e
- b8857f5a1c26d2573bd04d0d8e87df37bae59318
- e6494106d23212dfd1708a856d46abc02e95634b
- 081b548f9e06488d367497b02de972394b0da10b473a245bdf0c026e6406b86b
- 276ac9b9fe682d76382ec6e5bc3d1d045ce937438f92949c23453468eb62a143
- 320d091b3f8de8688ce3b45cdda64a451ea6c22da1fcea60fe31101eb6f0f6c2
- 34ca75a8c190f20b8a7596afeb255f2228cb2467bd210b2637965b61ac7ea907
- 3590dd881d094b020fe4b93bb6894e768b878ebcda7f03589da6671db2c652e5
- 35feefe6bd2b982cb1a5d4c1d094e8665c51752d0a6f7e3cae546d770c280f3a
- 6f21dde5cf5394eebf779451d45494dfeb22c2eebbb4af1aa3f779724dadf8af
- 75f728fa692347e096386acd19a5da9b02dca372b66918be7171c522d9c6b42d
- 7ee8cfde9e4c718af6783ddd8341d63c4919851ba6418b599b2f3c2ac8d70a32
- 839170c51d75bd1dc77f17b957846ace0caa19a83de837277d7294a47e5023b3
- 8831eb86996d4778be526a6fd281c98d624b155940aae463b45dda1c5f979f1c
- 923eb77b3c9e11d6c56052318c119c1a22d11ab71675e6b95d05eeb73d1accd6
- 9ef7dbd3da51332a78eff19146d21c82957821e464e8133e9594a07d716d892d
- a196c6b8ffcb97ffb276d04f354696e2391311db3841ae16c8c9f56f36a38e92
- a82cb2076b7274179d5f7246f8db274eda47a89392875b3c700f2fa15d70ab2e
- aa07ab7dba1aeb41c57bcdcbca54cefb85afb6f8927d33bf88aef5c19878ba92
- bdb4f98bf2bed83b09278bcf7b85771688fb1292612d6c82ad0eb8d7e3256fa1
- cbc7f2afe334bc160b741dde2e857ff26e01925744b9f0668a826aa4a1437ab8
- db5a204a34969f60fe4a653f51d64eee024dbf018edea334e8b3df780eda846f
- dcbbae5a1c61dbbbb7dcd6dc5dd1eb1169f5329958d38b58c3fd9384081c9b78
- e8207e8c31a8613112223d126d4f12e7a5f8caf4acaaf40834302ce49f37cc9c
- edecec2c413770fa929937c04ecf889e5c58d562c6e08ef0bfcd65ce482d397c
- 8003659902[.site]
- 8003659902[.space]
- Allowance[.stc]
- smm2021[.net]
- perfection.zanulor[.ru]
- perfection.zanulor[.ru]
- bicyclelist.telefar[.ru]
- energy.lortova[.ru]
- allows.telefar[.ru]
- salary.nemoiti[.ru]
- deserts.coagula[.online]
- sundabokun[.ru]
- temp.swtest[.ru]
NB65
|
· f5346a7d2508fd5976d3449f3afc971d |
|
· f746ea39c0c5ff9d0a1f2d250170ad80 |
|
· dac28369f5a4436b2556f9b4f875e78d5c233edb |
|
· 7f6dbd9fa0cb7ba2487464c824b6d7e16ace9d4cd15e4452df4c9a9fd6bd1907 |
|
· f173674f89069f2d9f7378b16f9cc1f5bfcd829b6bd43f6a3a0cae8158092832 |
Supporting Documentation
AcidRain | A Modem Wiper Rains Down on Europe - SentinelOne
TIR-20211004 An In-Depth Look at Ransomware Gang, Conti (avertium.com)
Anonymous vows to continue cyber war against Russia | Fortune
Conti ransomware offshoot targets Russian organizations - RedPacket Security
What You Need to Know About Russian Cyber Escalation in Ukraine (socradar.io)
CISA Insights Implement Cybersecurity Measures Now to Protect Against Potential Critical Threats
Statement by President Biden on our Nation’s Cybersecurity | The White House
Russia Gets Hit With A Cyberattack Using Its Own Ransomware (ladbible.com)
Biden: Russia 'exploring' US cyber-attacks - BBC News
Information on the possible provocation (cip.gov.ua)
Hacktivist group Anonymous launches series of cyberattacks against Russia - News WWC
Hackers use Conti's leaked ransomware to attack Russian companies (bleepingcomputer.com)
Cisco Talos Intelligence Group - Comprehensive Threat Intelligence: Threat Advisory: DoubleZero
New 'AcidRain' malware may be connected to Viasat attack (techtarget.com)
An In-Depth Look at Iranian APT "MuddyWater" (avertium.com)
Ukrainian enterprises hit with the DoubleZero wiper - AlienVault - Open Threat Exchange
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: [Flash Notice] New Malware - CISA Warns of Renewed Russian Threat as New Activity is Seen in Ukraine