Lapsus$: An In-Depth Look at Data Extortion Group
Executive Summary
In March 2022, Avertium published a flash notice warning organizations about a new threat actor named Lapsus$. The data extortion gang breached the United States based company Okta Inc., an authentication company used by millions, as well as other critical companies.
On March 21, 2022, the Lapsus$ hacking group posted screen shots of the group’s operators inside Okta’s internal systems via Telegram. The screen shots showed Okta’s Slack channels, as well as another internal system with a Cloudflare interface. The gang claimed that they had administrative access to Okta’s internal systems for two months. Okta Inc. initially denied the breach, but later confirmed it during an informational call shortly after.
Since that time, several members of Lapsus$ have been arrested. However, the group is likely to be larger than cyber security researchers originally speculated due to the group’s recent cyber attacks. In March 2022, Lapsus$ breached Globant and then breached T-Mobile in April 2022, stealing the company’s source code. Let’s take a look at Lapsus$, their techniques and tactics, as well as the consequences of companies taking too long to disclose cyber security breaches.
lapsus$ attacks
As we stated above, Avertium became aware of the data extortion gang Lapsus$ after they breached authentication company, Okta Inc. According to Okta’s public statement surrounding the alleged breach, they detected an attempt of an attacker trying to compromise the account of a third-party customer support engineer working for one of their sub-processors in late January 2022. Okta’s spokesperson, Chris Hollis, stated that the matter was investigated and contained.
During that time, Lapsus$ released a total of 8 photos on Telegram which showed sensitive information and Okta user identities. However, despite evidence, Okta was not convinced that the screen shots were connected to that particular incident. However, cyber security researcher, Bill Demikapi, believed that the published screen shots were credible. Other researchers believed that the breach was real as well and advised Okta customers to remain vigilant.
In addition to breaching Okta Inc., Lapsus$ breached Microsoft. The threat actor claimed that they gained access to Microsoft’s internal systems on March 20, 2022, when they posted a screen shot of what appeared to be a Microsoft Azure DevOps account in their Telegram channel. Azure DevOps is a Microsoft product that allows developers to collaborate on projects. The screen shots posted have since been deleted but they included images of internal projects including Bing and Cortana’s source code, as well as WebXT compliance engineering projects. Lapsus$ stated that they contained 90% of the source code for Bing and 45% of the code for Bing Maps and Cortana. Cyber security researcher, Kevin Beaumont, stated that Microsoft had multiple code signing certificates leaked as well.
Not only did Lapsus$ breach Okta and Microsoft, but they breached Nvidia, Ubisoft, Impresa, and Samsung as well. Nvidia’s breach took place in February 2022 and caused outages within their internal network. Lapsus$ ended up stealing 1TB of data of schematics, driver and firmware code, documentation, and SDKs. They also leaked a 19GB archive of those files online. Nvidia had their driver signing certificate stolen and Samsung had internal company data stolen.
Initially, Lapsus$ was believed to be based in Brazil due to their previous history with Brazil’s Ministry of Health. However, researchers discovered the ransomware group is actually based out of England, but a suspected member is based out of Brazil. The Brazilian member may be the reason why initial reports stated that the entire group was based out of Brazil.
lapsus$ Arrests
Not long after the initial company breaches, seven members of Lapsus$ were arrested. The London Police arrested seven teenagers between the ages of 16 and 21, with the alleged leader of the group being a 16-year-old Oxford-based teenager himself. The leader used the online alias “White” or “Breachbase” and it’s speculated that he made about $14 million Bitcoin from the Lapsus$ attacks.
When the teen leader’s parents were questioned, they stated that they had no idea that their child was a part of a cyber criminal operation and that the teen never talked about hacking, although he’s very good with computers and spends a lot of time on them.
According to KrebsOnSecurity, the members were exposed due to disgruntled Doxbin members. Doxbin is a text-based website where members post personal information of a victim or find personal data on thousands of people who have already been doxed. Last year, Doxbin was purchased by the leader of Lapsus$ and because he failed to keep the site running smoothly, the Doxbin community started targeting and harassing him.
As a result, Lapsus$’ leader ended up handing over control of Doxbin to the original owner, but not before leaking Doxbin’s entire data set – which included private doxes that were not published on the site. Naturally, the Doxbin community was upset, and they responded by doxing the Lapsus$ leader, posting videos shot at night outside of his home in the United Kingdom.
Despite accusations, the teen who was arrested and named as being the leader of Lapsus$ has not been officially accused of the cyber crimes. According to CNET, all the arrested members of Lapsus$ were released under investigation and law enforcement has not been able to tie the leader to every attack Lapsus$ claimed.
recent attacks - globant and t-mobile
Despite several arrests, Lapsus$ remained busy and active. At the end of March 2022, Lapsus$ breached the software services firm, Globant, and dumped a 73GB archive of stolen data. Globant provides software services for brands such as Google, Disney, and Electronic Arts. The dumped files allegedly contained information about Facebook, DHL, C-Span, and Abbott Laboratories. After the breach, Lapsus$ started circulating the archive online and claimed to have stolen customer information, as well as customers’ source code.
The threat actor also published the logins and passwords for Globant.com web portals, while mentioning Globant’s “poor security practices”. Globant responded to the breach with a statement admitting that they were the victims of a cyber attack and that a limited section of the company’s code repository was accessed by an unauthorized user.
By April 2022, Lapsus$ was at the center of another breach – this time involving T-Mobile. The group stole T-Mobile’s source code for a range of company projects and, according to private chat messages, accessed T-Mobile’s systems several times in March 2022.
Source: KrebsOnSecurity
As mentioned in Lapsus$ conversations, the group obtains initial access to targeted organizations by buying it from websites such as Russian Market. According to KrebsOnSecurity, the site sells access to remotely compromised systems, as well as credentials that may be stored on the systems. The messages also showed that the threat actor targeted T-Mobile employees who would be able to give them access to company tools, eventually giving them what they need to conduct a SIM swap. SIM swapping gives attackers the ability to reassign a target’s mobile phone number to a device the attacker controls – intercepting text messages (which may have links sent via SMS for password resets) and phone calls.
Lapsus$ was also observed finding or buying another set of T-Mobile VPN credentials each time they were cut off from a T-Mobile employee’s account. On March 19, 2022, Lapsus$ had access to Atlas, T-Mobile’s internal tool used for managed customer accounts. Once Lapsus$ gained access to Atlas, the group tried to get into accounts connected to the FBI and the Department of Defense, however, those accounts required additional verification procedures before Lapsus$ could change anything.
Some Lapsus$ members wanted to SIM swap wealthy targets for financial gain, but others pleaded not to burn their access to Atlas and other tools by attempting to SIM swap government accounts. The Lapsus$ breach also led to the termination of VPN connection to T-Mobile’s network and focused on stealing source code instead. Lapsus$ gained access to T-Mobile’s Slack and Bitbucket accounts and downloaded more than 30,000 source code repositories from T-Mobile.
Cyber security researchers are still not clear on why Lapsus$ was adamant about stealing source code. Some assume that the threat actors thought they might find security weaknesses that could be used later to further their attacks. In an emailed statement to The Verge, T-Mobile stated the following:
“Several weeks ago, our monitoring tools detected a bad actor using stolen credentials to access internal systems that house operational tools software. Our systems and processes worked as designed, the intrusion was rapidly shut down and closed off, and the compromised credentials used were rendered obsolete.” – T-Mobile
This is not the first time T-Mobile has had to deal with unauthorized SIM swaps. In December 2021, T-Mobile observed unauthorized activity on some of its customer accounts. The company stated that SIM swapping is a common industry-wide occurrence, and they would be providing information on preventing account takeover. They didn’t go into detail regarding how the attackers were able to perform the SIM swaps in the first place.
tactics & techniques
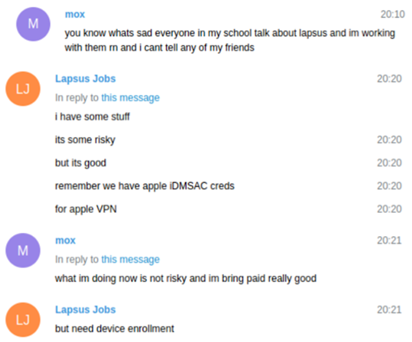
Unlike other cyber criminal operations, Lapsus$ does not have a darknet leak site or social media accounts. The group operates solely via Telegram and email, and they started their attacks using phishing emails, before moving on to attacking companies via insider threats. Their Telegram channel has several posts asking insiders at companies to reach out to them if they are willing to give up their credentials for a fee.
Lapsus$ has been seen recruiting employees who work for the following companies: AT&T, Microsoft, Apple, EA, IBM, Claro, Telefonica, Atento, Telperformance, OVH, and Locaweb. Not only did they want insiders from the mentioned companies, but they wanted insiders from any company providing telecommunications, software and gaming, and other services – it’s possible this is how Lapsus$ was able to breach and conduct the T-Mobile attack.
“DEV-0537 advertised that they wanted to buy credentials for their targets to entice employees or contractors to take part in its operation. For a fee, the willing accomplice must provide their credentials and approve the MFA prompt or have the user install AnyDesk or other remote management software on a corporate workstation allowing the actor to take control of an authenticated system. Such a tactic was just one of the ways DEV-0537 took advantage of the security access and business relationships their target organizations have with their service providers and supply chains.” – Microsoft
Lapsus$’ Telegram recruitment post stated that they are looking for an employee who can provide them with “a VPN or CITRIX to the network” for the listed companies. The threat actor is also interested in non-employees who happen to have access to a VPN or VDI at any of those companies.
In addition to recruiting insider threats and phishing emails, Lapsus$ has used SIM swapping to gain access to accounts at their targeted organizations. The SIM swapping involves the threat actor bribing or tricking mobile company employees into transferring a mobile phone number to their device. After the transfer, Lapsus$ intercepts one-time passwords sent to their victim via SMS or phone call. The password can also be reset for any online account that allows resets through SMS links. This technique is phone-based social engineering and allows for account takeover.
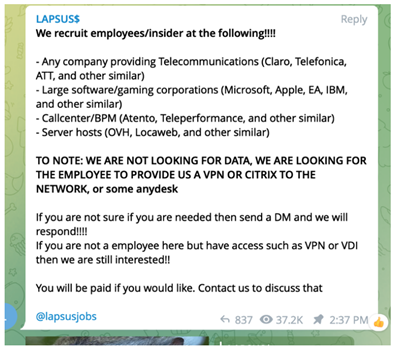 Image 2: Lapsus$ Recruitment on Telegram
Image 2: Lapsus$ Recruitment on Telegram
Redline password-stealing malware is also used to gain access to organizations. Once deployed, Redline searches public code repositories for passwords, as well as purchasing credentials and session tokens from dark web criminal forums. Lapsus$ uses a pure extortion and destruction model but doesn’t deploy ransomware payloads.
Initially targeting organizations in the United Kingdom and South America, Lapsus$ has now expanded to include global targets within the government, technology, telecom, media, retail, and healthcare sectors. Most cyber criminals try to fly under the radar, but Lapsus$ does not cover their tracks. They announce their attacks on Telegram where they buy credentials from their target’s employees.
Source: Microsoft
In addition to recruiting employees, Lapsus$ also gains initial access to networks by compromising personal or private (not work related) accounts, which gives them access to look for additional credentials – ultimately giving them access to corporate systems. Employees often use personal accounts or mobile numbers as their second-factor authentication. Lapsus$ will then use those accounts and mobile numbers to reset passwords and complete account recovery procedures.
Phone based social engineering, SIM swapping to facilitate account takeover, paying employees or business partners at target organizations for credential access and MFA approval, and intruding on crisis-communication calls of targets are tactics that are less frequently used by threat actors. However, Lapsus$ has made it a point to use those tactics interchangeably and they have been quite successful.
Reconnaissance and Privilege Escalation
According to Microsoft, after obtaining access to their targeted network, Lapsus$ exploits unpatched vulnerabilities on internally accessible servers including JIRA, Gitlab, and Confluence. The threat actor also finds exposed credentials and secrets by searching code repositories and collaboration platforms. Lapsus$ also consistently uses AD Explore to enumerate users and groups in a network – allowing them to see which accounts have higher privileges.
In some instances, Lapsus$ will call an organization’s help desk and try to convince the support staff to reset a privileged account’s credentials. The threat actor will have an English-speaking person speak with the help desk to enhance the social engineering. They will also use previously gathered information such as profile pictures and answer common recovery prompts such as “mother’s maiden name” or “first street you lived on”.
After gaining privileged access, Lapsus$ exfiltrates data from their target for future attacks and deletes the target’s resources both on premises and in the cloud. This action triggers the organization’s incident and crisis response process. Why does an organization’s incident and response process matter? Because Lapsus$ joins the organization’s crisis communication calls and internal discussion boards (Teams, Slack, etc.) to understand how the organization responds to attacks, as well as understand their workflow. This gives Lapsus$ insight into their targets knowledge of the intrusion and is a venue to initiate extortion demands. Lapsus$’ goal is to target cryptocurrency accounts, stealing wallets and funds.
slow response to cybersecurity breaches
As previously stated, Okta Inc. was not convinced that they were breached in March 2022 and were adamant that the incident was related to a separate incident that took place in January 2022. However, it didn’t take the company long to realize that they in fact had been recently breached by Lapsus$, prompting them to quickly spring into action to address the issue.
During a Zoom call on March 23, 2022, Okta stated that the security incident was related to a partner breach and concluded that 2.5% of their customers may have been impacted and their data may have been viewed. Lapsus$ was able to access the data via a third-party engineer working for Sitel, a sub process contractor.
Fortunately, support engineers have limited access to the Okta environment and “SuperUser” is the internal application that engineers use to access clients. Okta was built with least privilege in mind, therefore there is limited access for support engineers like those from Sitel. This means that Okta’s source code, active servers, and customer databases cannot be accessed by support engineers. The threat actors would only be able to access what the third-party support engineer was already logged into.
Initially, Okta stated that 366 customers had their Okta Inc. site accessed, but that number was recently changed to two customers after a forensic investigation. The company also stated that the threat actors only had unauthorized access for 25 minutes and they were not able to authenticate directly to customer accounts or make configuration changes.
SEC Rules and Fines
Avertium has published previous reports on slow to respond companies. Okta Inc. responded to the cyber security incident in decent time, but they didn’t believe that it was happening. Okta maintained in an initial official statement that the company was not breached, remained fully operational, and that there were “no corrective actions that need to be taken by our customers.”
In March 2022, the Securities and Exchange Commission (SEC) proposed amendments to its rules regarding disclosure and incident reporting by public companies. According to the SEC, the amendments would require the following:
- Periodic reporting to provide updates about previously reported cyber security incidents.
- Periodic reporting about a registrant’s policies and procedures to identify and manage cyber security risks.
- The registrant’s board of directors’ oversight of cyber security risk.
- Annual reporting or certain proxy disclosure about the board of directors’ cyber security expertise.
Sometimes, companies try to keep vulnerabilities private to keep attackers in the dark about the company’s next steps, but they also keep quiet to keep backlash and financial loss at a minimum. Public embarrassment or shame may be another reason why incidents are hushed. However, not reporting data breaches or vulnerabilities within a certain time frame may end up costing companies much more than embarrassment. Although Okta Inc. initially addressed the chatter surrounding their breach, they didn’t exactly say “we were breached” until a bit later. Hopefully, the proposed SEC amendments will encourage organizations to not only respond to attacks in an appropriate amount of time, but to also conduct thorough investigations before denying an attack.
insider threats
Cyber security threats from untrustworthy employees who work for an organization are known as insider threats. One of the central ways Lapsus$ was able to gain initial access into the organizations they breached was through insider threats. Although it may be tempting to solely focus on threats from the outside, internal threats pose a great risk and are the source of many losses in critical infrastructure industries. Sometimes employees or contractors ignorantly use their authorized access to do harm to the security of a company, but most of the time an insider is well aware of what they’re doing and why.
The question is, how can organizations stop insider threats from compromising security? First you have to know how to spot them and there are few ways of achieving that feat, which include:
- The Ignorant – These insiders don’t act with harmful intent and are ignorant to the security risks they expose their organization to. They need training on security policies, and it may need to be done every quarter to make things clear. This employee may be surfing non-secure websites via the company computer, or they may click on a malicious link in a phishing email.
- The Manipulated – This insider is a pawn and was more than likely manipulated into carrying out a task that could cause destruction. This employee may accidentally download malware onto their work computer via social engineering (think spoofed emails).
- The Cooperator – This insider will collaborate with a third-party (competitors or nation-states) and use their access to intentionally cause harm to a company. They will steal customer information or disrupt business operations.
- The Independent – This insider acts maliciously solely on their own and has not been manipulated. They may even intentionally seek employment at an organization for the sole purpose of obtaining elevated levels of privilege (think system administrators).
Now that you know the kinds of insider threats you may be dealing with, let’s dig into how your organization may be able to stop insider threats before they start:
- Fully vet employees before you hire them. This includes doing full background checks, calling previous employers and references, and doing multiple interviews.
- Adopt a privileged access management monitoring stance. Abnormal login attempts, out of hours logins or several failed login attempts should generate an alert for an analyst to investigate.
- Use SIEM to monitor sensitive data areas to see who accessed the data.
- Harden your systems and use branded checklists such as CIS Benchmarks. Applying hardening measures for your cyber environment is crucial to keeping insider threats at a minimum.
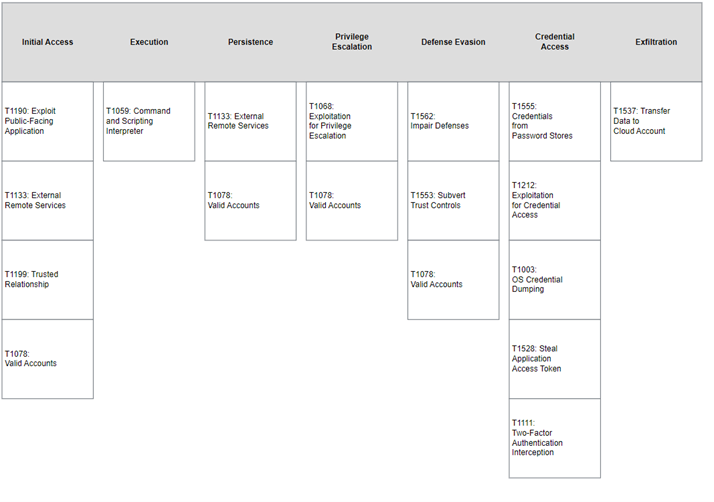
MITRE Mapping
Indicators of Compromise
- zip
- 2no[.co]
- https://cdn.discordapp.com/attachments/879433223103459409/879433370159968306/Setup2[.exe]
- https://cdn.discordapp.com/attachments/879422002287493133/879685414934417479/R24[.bmp]
- https://cdn.discordapp.com/attachments/879422002287493133/879653243217670164/app24[.bmp]
- https://cdn.discordapp.com/attachments/879422002287493133/879653242093600808/sfx_123_201[.bmp]
- https://cdn.discordapp.com/attachments/879422002287493133/879653239560228884/help24[.bmp]
- https://cdn.discordapp.com/attachments/879422002287493133/879653236993318933/Falioca24[.bmp]
- https://cdn.discordapp.com/attachments/879422002287493133/879423887002206228/Passat[.bmp]
- https://cdn.discordapp.com/attachments/879422002287493133/879423620030550088/Real231[.bmp]
- https://cdn.discordapp.com/attachments/879422002287493133/879423245999276102/VerminateMechanize_2021-08-18_15-57[.bmp]
- https://cdn.discordapp.com/attachments/873056123240972371/875681686568992788/E_PL_Client[.bmp]
- https://cdn.discordapp.com/attachments/870454586861846551/870548989903274054/jooyu[.exe]
- https://cdn.discordapp.com/attachments/928009932928856097/936319550855716884/Windows11InstallationAssistant[.zip]
- https://t.me/[minsaudebr]
- ip[.sb]
- lapsusgroup@protonmail[.com]
- 0a7921d68d31d9d6cb23d0060daf018ead026c31069f8147c2127bd7a062578d
- 0c409e9c2ba44bc27e9d26e07deba2ba7372fa7ce4ca67da0696d4322c7e19d0
- 28d71a579fb75cb672af489ce602392b4504f895c3881691a12c51cea7719f4d
- 2c5d8cf9d86b78fdf3eb085e48b5e13989331ae2be1b9793204717f2da76f253
- 39772550650d897f50e3353a601d611e38bc65670e8883a60e0f9ac0a40b774c
- 41dba5cf17e66001306398b1117761d3bfdbf823807282edfa898d21ee08065a
- 42a888e2cf677ed57ea3e072c5ccdbe15492745c4cb14bb3f2d72f4db81a4756
- 57d417306e6d1d2f4943736a43e33818f87666b962107939395d56a500f26968
- 62d9bab3db42901422cbf4ffa5c2f6bd01f3e04f988ae54401216d294b1d5798
- 661913595df0ab71310fb9c3ab56af07c47a4fe9b5f25fb1da7ee0c83b199bca
- 666d848a4ecb284b4b6f70f0e6c8126fff9facb5427dabd0fe7b45502d70f0b2
- 67923efca1ac97b09b579dfd774399eb0327ffe25bf60ecb42a6d3d833639455
- 7b76caa7c924e3271e67f576f4f73b9338b93c579298d76375af493749d6cdbc
- 91922830b0dadc450c785a55789ecdbc801801eb76e029e1c35673ac0ba60f86
- 927965d51c202140e974ea473ed143e701e1ed3b6b34583200d5a8935457a36f
- 9a305e8a3616def77c4c7f18c0c91a7b67544fd4473c209d95b8b614c31a5790
- ae9e7613eb86358cf0c50eb2753c82c605f170fcae1ada510506d037d2987e66
- c33defdd2c60f2d74ebaabbe82805a7a36fa2428cda8c42fd202396b4eda28f6
- d2e03bb72a530d14de71be2c7d4aa2275887113aa2ff6d57f53c57f4a8516365
- f088dac66ed4630d674073125c7562aa3eb283a30bc4bcc162abf0d47458ce8f
- http://81.4.105.174/Dlmfs[.jpg]
- http://81.4.105.174/FileOne[.png]
- http://81.4.105.174/InjectPersistenceF2[.log]
- http://81.4.105.174/Ipqtn[.jpg]
- http://81.4.105.174/Koqomwipj[.jpg]
- http://81.4.105.174/Lavgimu[.jpg]
- http://81.4.105.174/Liafandgotica[.png]
- http://81.4.105.174/Mstst[.log]
- http://81.4.105.174/Prwcwm[.jpg]
- http://81.4.105.174/Qraqpk[.png]
- http://81.4.105.174/Ribtcqqqb[.log]
- http://81.4.105.174/SentinelInstaller[.png]
- http://81.4.105.174/SentinelWiskonsinDam[.jpg]
- http://81.4.105.174/Sifican[.log]
- http://81.4.105.174/Vcdrpuc[.log]
- http://81.4.105.174/VideoPublicAllocation[.log]
- http://81.4.105.174/VirtualAlloc2[.log]
How Avertium is Protecting Our CUSTOMERS
A breach by Lapsus$ could have devastating consequences for organizations. It’s important to remember to protect your cyber environment against insider threats and relentless threat actors like Lapsus$. Avertium offers the following services to help keep your organization safe:
- Avertium offers security consulting services to develop robust internal security policies.
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Implement XDR as a prevention method. Our XDR is a combination of monitoring software like LogRhythm, Microsoft Azure Sentinel, or AlienVault, combined with endpoint protection such as SentinelOne. XDR platforms enable cybersecurity through a technology focus by collecting, correlating, and analyzing event data from any source on the network. This includes endpoints, applications, network devices, and user interactions.
- Avertium offers user awareness training through KnowBe4. The service also includes Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
Avertium’s Recommendations
- MFA should be required for all users, including those in trusted environments.
- Don’t use weak MFA factors like text messages or simple push. Use number matching instead.
- Don’t use easily guessed passwords – all passwords should be hard.
- Employees should be reminded that workplace credentials shouldn’t be stored in browsers or password vaults secured with personal credentials.
- Implement User and Entity Behavior Analytics (UEBA Principles)
- UEBA can detect complex threats across multiple users and IP addresses.
- UEBA solutions can track data regarding normal behavior to build a profile and can detect unusual behavior and alert admins.
- UEBA systems can compare data from several sources such as packet capture data and logs.
- UEBA systems can communicate what they find by issuing a request for a cyber security analyst to investigate strange behavior.
- System Hardening – securing your servers or computers helps to minimize the attack surface or potential attack vectors.
- Increase auditing of employee activities.
Supporting Documentation
Flash Notice: Authentication Company, Okta, Breached by Lapsus$ (avertium.com)
Okta says Lapsus$ breach lasted 25 minutes, impacted two customers | VentureBeat
Lapsus$ Ransomware Gang - A Malware in Disguise - Check Point Software
Updated Okta Statement on LAPSUS$ | Okta
Cybersecurity Insider Threat | Homeland Security (dhs.gov)
Threat Brief: Lapsus$ Group (paloaltonetworks.com)
How To Defend Against And Spot Malicious Insider Threats (newnettechnologies.com)
Despite Arrests, LAPSUS$ Hacking Group Strikes Again, Hitting IT Supplier | PCMag
What is UEBA? Complete Guide to User and Entity Behavior Analytics (varonis.com)
Leaked Chats Show LAPSUS$ Stole T-Mobile Source Code – Krebs on Security
A teen is reportedly the mastermind behind the Lapsus$ hacking group - The Verge
A Closer Look at the LAPSUS$ Data Extortion Group – Krebs on Security
System Hardening: An Easy-to-Understand Overview (trentonsystems.com)
Police Arrest Suspected Hackers in Wake of Lapsus$ Attack on Okta, Report Says - CNET
T-Mobile says new data breach caused by SIM swap attacks (bleepingcomputer.com)
Okta ends Lapsus$ hack investigation, says breach lasted just 25 minutes - The Verge
Lapsus$ hackers breached T-Mobile’s systems and stole its source code - The Verge
7 Suspected Members of LAPSUS$ Hacker Gang, Aged 16 to 21, Arrested in U.K. (thehackernews.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
Related Resource: [Threat Report] Russia vs. Ukraine Part Two