End of Year Recap for 2021
Executive Summary
In 2021, we saw some of the most deviant cyber attacks cause chaos for organizations and enterprises across the globe. At the end of 2020, researchers said that ransomware would become a permanent fixture within the cyber space and that third-party attacks would trend in a way they never have. Cyber terrorism was also a trending topic for cyber security professionals everywhere.
Over the past twelve months, we’ve seen threat actors become smarter, faster, and more sophisticated with their attacks. This year’s attacks had devastating real-world consequences and highlighted many of the predictions researchers projected for the year. From SolarWinds to PrintNightmare, let’s take a look at this year’s most talked about cyber attacks and why organizations need to remain vigilant during 2022.
supply chain CYBER attacks IN 2021
KASEYA
In July 2021, the IT management software company, Kaseya, became the victim of a massive supply-chain attack. The ransomware attack was carried out by the threat actor, REvil. Kaseya had a vulnerability within their VSA software and REvil leveraged that vulnerability against multiple managed service providers (MSP) and their customers.
REvil was able to attack Kaseya through an authentication bypass vulnerability in the Kaseya VSA web interface. As a result, this vulnerability allowed the threat actor to bypass authentication controls, gain access to an authenticated session, upload a malicious payload, and execute commands via SQL injection, while achieving code execution. REvil was able to hack a software update and deploy ransomware to hundreds of customers all at the same time. Because of the attack, supermarkets had to close, schools couldn’t function properly, a national railway system went down, and over 1,000 companies had servers and workstations encrypted.
Recently, there were two individuals who were arrested due to their participation in the attack on Kaseya. However, despite the recent arrests, analysts fear that other cyber gangs that maintain different ransomware strands will try to fill the void of REvil once the gang is completely dismantled.
SOLARWINDS
Although the SolarWinds attack took place at the end of 2020, the effects of the attack carried over into 2021. It all started in May 2020, when a vulnerability was discovered in the SolarWinds MSP Patch Management Engine (PME). When the attack initially happened, no one knew who was behind it. We now know that nation-state threat actor NOBELIUM was behind the breach. The cybercriminal gang was able to compromise SolarWinds by slipping a malicious code into Orion (a software program that monitors various components within the company’s network) while it was being updated.
NOBELIUM’s goal was to compromise SolarWinds’ infrastructure with the update, which contained a backdoor called Sunburst. After Orion customers downloaded the software update from their emails, Sunburst’s code was installed within their networks. Next, the group deployed other malware variants and targeted 100 prominent private firms as well as nine U.S. government agencies (Department of State, Department of Energy, Department of Homeland Security, Department of Commerce and Justice, etc.).
This supply-chain attack was significant because SolarWinds Orion is a widely-used IT management and monitoring platform used by IT organizations in various industries. After the breach, the Department of Homeland Security mandated that all Federal Agencies immediately disconnect their compromised Orion infrastructure from their network.
The attack was so severe that the Biden administration put cybersecurity at the top of their list of priorities. The administration also published an executive order that included new measures for how agencies buy and evaluate third-party software.
COLONIAL PIPELINE
In May 2021, the threat actor, DarkSide, launched a ransomware supply-chain attack that would end up becoming one of the largest in U.S. history. The threat actor gained access to Colonial Pipeline’s virtual private network (VPN) account due to a single compromised password. The account that was compromised allowed employees to remotely access the company’s computer network. At the time of the attack, the account wasn’t in use but could still be used to access the fuel company’s network.
After the ransomware attack, researchers discovered that the password for the account was inside a batch of leaked passwords on the dark web. It’s suspected that the Colonial Pipeline employee probably re-used that password on another previously hacked account. The VPN account that was compromised, did not use multifactor authentication and it isn’t known how DarkSide obtained the correct username and password. As a result of the attack, Colonial Pipeline had to shut down the fuel pipeline, leaving gas stations, businesses, and households without fuel. Additionally, the news of a cyber attack made its rounds and people started panic buying which resulted in gas shortages along the east coast. DarkSide stole about 100 gigabytes of data from the company and threatened to leak it if they refused to pay a ransom. Colonial Pipeline ended up paying DarkSide $4.4 million in ransom.
SIMILARITIES
If you take a look at the attacks on Kaseya, Colonial Pipeline, and SolarWinds, you can clearly spot the similarities. All three supply-chain attacks involved critical infrastructure in some way and people were able to see just how vulnerable supply-chains can be. Both Kaseya and SolarWinds had unknown vulnerabilities within their software, specifically their updates.
In the case of Colonial Pipeline, we can see the lack of inventory control due to the company not knowing that they had a dormant VPN account. The company should have removed the account if it was no longer needed. They also didn’t use the cyber security best practice of multifactor authentication.
It’s clear that threat actors want to maximize their profits by going after industries who provide critical services. They know they have a better chance of receiving a reward if they attack industries that people depend on. Mismanagement of critical access points appears to be the common theme with the attacks on SolarWinds, Colonial Pipeline, and Kaseya – a theme we can expect to see in 2022 if organizations don’t implement good cyber security hygiene.
INITIAL ACCESS
PROXYSHELL
In August 2021, we learned that Microsoft Exchange Servers were being exploited by attackers through months-old vulnerabilities like ProxyLogon. However, a new series of attacks, named ProxyShell (CVE-202134473, CVE-2021-34523, and CVE-2021-31207), was worse than the original because LockFile, a ransomware gang, was suspected of being responsible for them.
LockFile used ProxyShell’s vulnerabilities to encrypt Windows domains after gaining access to Microsoft Exchange Servers. They then used a PetitPotam vulnerability to take command over Windows domain controllers. Also, ProxyShell allowed attackers to enable unauthenticated users to perform remote code execution (RCE) and steal plaintext passwords. There were about 300 servers that were compromised during the attacks.
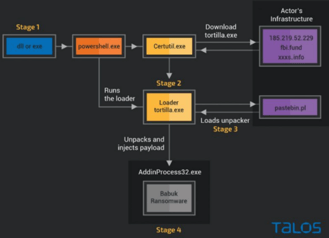
Naturally, after a few months of quiet, researchers assumed that ProxyShell was an exploit of the past, until the threat actor, Tortilla, proved otherwise. Tortilla is a new threat actor who uses Microsoft Exchange ProxyShell vulnerabilities to deploy a variant of Babuk ransomware. Babuk is famous for encrypting machines, interrupting the system backup process, and deleting volume shadow copies. By exploiting the vulnerabilities found within ProxyShell, Tortilla has been able to host malicious modules and conduct internet-wide scans to exploit machines. Tortilla wasn’t discovered until November 2021 and is exploiting a vulnerability that may continue to be exploited in 2022.
Chart 1: Infection Chain of Tortilla
Source: Talos/Cisco Labs
FORTINET
Although not new, CVE-2018-13379 has been exploited several times in 2021. The Fortinet vulnerability started off as a VPN credential exposure vulnerability. The VPN web portal allowed unauthenticated attackers to download system files via special crafted HTTP resource requests. In April 2021, CISA warned that cybercriminals were scanning ports and looking for Fortinet's flaws. Their goal was to carry out distributed denial of service attacks (DDoS), ransomware attacks, and structured query language (SQL) injection attacks. CVE-2018-13379 is just one of three Fortinet vulnerabilities that can be exploited, but it is often used to gain a foothold within networks before moving laterally and carrying out reconnaissance.
Of course, the year couldn’t end without Fortinet being exploited one last time. This time the vulnerability is being exploited by a state-backed Iranian threat actor. The Iranian APT has been exploiting the vulnerabilities within Fortinet since March 2021, as well as a ProxyShell vulnerability since October 2021. As a result, the threat actors were granted initial access to systems that lead to the deployment of ransomware, data exfiltration or encryption, and extortion. The Iranian threat actors don’t have a specific industry they’re targeting, but they have been seen attacking U.S. critical infrastructure sectors, including Transportation and Healthcare.
SONICWALL
SonicWall has seen its fair share of vulnerabilities this year, with the most recent one being CVE-2021-20039. This flaw allows an unauthenticated attacker to inject arbitrary commands as the root user, leading to a remote takeover of unpatched devices. It has yet to be exploited in the wild, but it is the most dangerous flaw of them all. Other bugs that have been patched include a remote code execution (CVE-2021-20044) and an injection vulnerability (CVE-2021-20016) which allows a remote attacker to gain access to credentials like passwords and usernames. It’s an SSL VPN SMA100 SQL injection vulnerability.
In early December 2021, SonicWall encouraged customers to patch their devices as soon as possible. SonicWall SMA 100 appliances have been targeted by ransomware gangs multiple times since the start of 2021 and there are still threat actors exploiting CVE-2021-20016. In April 2021, the ransomware Fivehands was deployed by exploiting CVE-2021-20016. It was also said to target SonicWall’s internal systems. SonicWall warned of the increased risk of ransomware attacks targeting unpatched end-of-life SMA 100 series and Secure Remote Access products, but customers still left devices unpatched.
ATLASSIAN CONFLUENCE
Over Labor Day weekend, Atlassian Confluence (CVE-2021-26084) was attacked due to an OGNL (Object-Graph Navigation Language) injection vulnerability found in the remote code execution of the platform. The vulnerability was embedded in the Atlassian Confluence Server, as well as the Confluence Data Center products. It allowed unauthorized and authorized users to use arbitrary code, interpreted and rendered by OGNL, on both platforms. The company warned businesses about the vulnerability, but not before attackers performed mass scans and launched their attacks. One attack involved a threat actor gaining access to a company’s server and installing a Monero cryptocurrency miner.
ACCELLION
At the end of 2020, over 100 organizations and businesses were impacted by file-sharing company, Accellion’s (CVE-2021-27104 & CVE-2021-27101), data breach. Cl0p, a ransomware gang, was responsible for impacting the operations of a dozen healthcare organizations, one of those organizations being Kroger Health and Money Services. Cl0p was able to breach those organizations by gaining access to the Accellion FTA server of their third-party vendors. Morgan Stanley was also breached using the same attack method. Cl0p took advantage of both organization’s outdated third-party file transfer tool from Accellion. The data breach impacted 1,474,284 people and put clinic customer information at risk, including pharmacy records.
SIMILARITIES
The Fortinet and ProxyShell vulnerabilities could be classified as two of the most consistently exploited vulnerabilities of 2021. Both vulnerabilities allow for threat actors to deploy ransomware and encrypt machines. Because the flaws are easy to exploit, threat actors will more than likely continue to do so in 2022.
In the case of Accellion and SonicWall, you can see why the companies were compromised. Cyber security researchers and analysts have been pleading with organizations for years to switch to new products when vendors ask. Accellion FTA is a 20-year-old application that allows enterprises to transfer large files securely, but it’s reached the end of its life and is outdated. Last year, Accellion asked customers to switch over to a new product called Kiteworks, but a lot of their customers didn’t comply.
SonicWall was also compromised due to customers not being proactive with patching their end-of-life products. SonicWall patched the vulnerability in newer versions of their firmware for the affected devices, but threat actors exploited the vulnerability because organizations failed to take the appropriate actions to mitigate the vulnerabilities in the SRA and SMA 100 series products. Threat actors will seize any opportunity to victimize an organization and exploiting end-of-life products is an easy way to do that. Not upgrading these products when asked, is the equivalent of playing with fire.
LATERAL MOVEMENT
FATPIPE
In November 2021, the FBI issued a notice warning that an APT group had been exploiting a zero-day vulnerability in FatPipe’s (a computer networking hardware firm) router clustering and load balancer products. The vulnerability in the device software dated back to at least May 2021. The flaw, found in the device software’s WARP WAN redundancy product, its IPVPN load balancing and reliability device for VPNs, and in its MPVPN router clustering device; allowed attackers to gain access to a target’s systems, as well as access to an unrestricted file upload function. This vulnerability didn’t have a CVE identification, but can be tracked under the tag FPSA006.
Essentially, the vulnerability allowed for the APT threat actor to drop a webshell with root access. FatPipe stated that the vulnerability was caused by a lack of input and validation checking mechanisms for certain HTTP requests on devices. This means that an attacker could send a modified HTTP request to an affected device. The attackers exploiting the vulnerability used the compromised VPNs to move laterally within their targets’ networks.
ZOHO MANAGEENGINE
Zoho ManageEngine products have been exploited several times this year. In December 2021, CISA reported that an APT group was exploiting two vulnerabilities, CVE-2021-44515 and CVE-2021-44077. The first vulnerability, CVE-2021-44515, allowed for attackers to bypass authentication, which affected MangeEngine’s Desktop Central MSP. The vulnerability allowed attackers to gain unauthorized access by sending a crafted request that leads to remote code execution.
The second vulnerability, CVE-2021-44077, was also an authentication bypass issue and allowed attackers to upload executable files and place webshells which allowed for lateral movement and stealing administrator credentials. These vulnerabilities affected at least 13 organizations across the energy, healthcare, education, and technology industries.
SIMILARITIES
In both cases, you can see that webshells were dropped to help the threat actors move laterally within the systems. The FatPipe and ManageEngine vulnerabilities also had issues with attackers modifying HTTP requests and escalating their privileges. These kinds of issues can allow malicious threat actors to steal credentials, weaken encrypted traffic’s cryptography, read sensitive data from devices, and remotely execute code.
In regard to FatPipe, the vulnerability is a good example of how unsecure VPNs can be a major problem, just ask Colonial Pipeline who was attacked due to an old VPN password. Even Fortinet’s 85,000 customers would have a story to tell about how unpatched SSL-VPNs led to their credentials being exposed online.
PRIVILEGE ESCALATION
WINDOWS PRINT SPOOLER AKA PRINTNIGHTMARE
In 2021, a Chinese security team (Sangfor) presented a novel exploit at the cyber security conference, Black Hat. The team discovered a security flaw in Microsoft’s Print Spooler service (runs by default on Windows) which allows local privilege escalation and remote code execution exploits. This allows attackers to run arbitrary code with administrative privileges. The flaw ultimately gives threat actors the ability to install programs, modify data, and create new accounts with full administrator rights.
Sangfor didn’t just discover the vulnerability, but they produced a proof-of-concept exploit script and published a teaser of the exploit on their Twitter feed. While the teaser didn’t explain how to execute the exploit, it did solidify an invitation for Sangfor to present for a second time at the Black Hat 2021 conference.
Unfortunately, the excitement was short-lived once Sangfor discovered that they inadvertently published the full exploit details to their public GitHub page before making a responsible disclosure to Microsoft. Before the page could be taken down, it had already been cloned and made permanently available to everyone who uses the internet. Instead of receiving a bug-bounty payment, they had to deal with the consequences of accidentally unleashing a zero-day vulnerability, which we know as PrintNightmare (CVE-2021-36958) The vulnerability continues to be used by threat actors like Conti.
MICROSOFT AZURE
In September 2021, researchers at a Cloud Security company named Wiz disclosed several vulnerabilities that affected Microsoft Azure. The exploit dubbed, OMIGOD came about due to an issue with a software agent called Open Management Infrastructure (OMI). Because the software was automatically deployed without customers’ knowledge, they enabled certain Azure services after setting up a Linux virtual machine in their cloud. As a result, four vulnerabilities were easily exploited by attackers (CVE-2021-38647 , CVE-2021-38648, CVE-2021-38645, CVE-2021-38649). Three out of the four vulnerabilities involved privilege escalation with one involving unauthenticated RCE as root – thus turning victim machines into botnets, where large-scale exploitation could take place.
Senior security researcher from Wiz, Nir Ohfeld, stated that OMIGOD is a textbook RCE vulnerability from the 90s because an attacker could use a single packet to become root on a remote machine, just by removing the authentication header. Before customers could patch their devices, threat actors successfully scanned the web for vulnerable Azure Linux virtual machines.
EMOTET
A vulnerability that was previously seen in January 2021, Emotet surprised everyone when it came back into cyber space during November 2021. Emotet malware came back with a vengeance and used TrickBot to install malware on infected Windows systems. Attackers were able to install the malware via reply-chain emails. The reply-chain emails persuaded victims to open malicious attachments disguised as Word or Excel documents. This kind of social engineering is dangerous because most of the emails look legitimate and discuss things that wouldn’t be unusual to the victim (missing wallet, canceled meeting, political donations, etc.).
After the malicious attachments were opened, victims enabled malicious macros that launched a PowerShell command that then downloads the Emotet loader DLL from a compromised WordPress site. Emotet then runs silently in the background, waiting for commands to execute from its C2. The commands steal email account information, spread malware to other computers, and install additional payloads like TrickBot. Recently, Emotet has been seen installing Cobalt Strike beacons directly, which gives threat actors immediate network access and makes ransomware attacks inevitable.
Cobalt Strike is a penetration testing toolkit that is used often by non-malicious professionals, but Emotet is using the toolkit to deploy beacons on compromised devices to perform remote network surveillance and execute additional commands – skipping their primary malware payload of TrickBot altogether. This now makes it much easier for Emotet to spread laterally, steal data, and quickly deploy ransomware.
SIMILARITIES
Both PrintNightmare and OMIGOD allowed attackers to exploit privilege escalation. In Print Nightmare’s case, privilege escalation allowed attackers to use remote code execution to install programs, modify data, and create new accounts with full admin rights – OMIGOD’s privilege escalation allowed the same.
In both cases, analysts blame insecure management software running on customers’ machines, unknown to the customers. OMI and Windows Print Spooler both run automatically unbeknownst to customers. Analysts don’t believe that this issue rests solely with Microsoft. Other cloud providers may have vulnerable components within their systems as well.
SOFTWARE DEPENDENCY COMPROMISE
THE CURVEBALL
On December 10, 2021, the internet was set ablaze when a zero-day exploit vulnerability (CVE-2021-44228) named Log4Shell was found in Apache’s Java-based Log4j logging library. The vulnerability allows for remote code execution (RCE) on vulnerable servers, which gives an attacker the ability to import malware that could compromise machines.
Almost every network security system runs on some kind of logging process, which means a popular library like log4j has a vast reach. Logging is a process in which applications keep a running list of activities they have performed that can later be reviewed in case of an error. Millions of applications use Log4j for logging and if an attacker has the app, he can compromise it by logging a special string of characters. The vulnerability was initially seen on sites hosting Minecraft servers where people could trigger the vulnerability by hosting chat messages.
This exploit is still active and any company that uses the affected products (ApacheStruts2, Apache Druid, Apache Flink, etc.) is at its mercy – including Apple iCloud, Amazon, Twitter, Steam, etc.
Apache immediately developed a patch and mitigations for the vulnerability, but it was quickly discovered that the mitigations were not effective. A researcher discovered that the vulnerability could also allow attackers with control over Thread Context Map (MDC) to input data when the logging configuration uses a non-default Pattern Layout with a Context Lookup or a Thread Context Map pattern. This allows the attacker to craft malicious input data using a JNDI Lookup pattern resulting in a denial of service (DOS) attack. The exploit was given a new CVE identification number (CVE-2021-45046) and a set of new mitigations.
A Chinese threat actor has already started to exploit Log4Shell. This means that they, and other threat actors, could take control of servers and steal data (photos, medical records, etc.), and extort organizations via ransomware attacks along the way. The good? Data will only be vulnerable if it’s been stored on a server that uses an application programming interface (API), which incorporates Log4j. The bad? General users wouldn’t even be able to tell if their data was stolen and they wouldn’t be able to stop it from happening.
Some of the world’s largest companies and government agencies have found some of their servers to be vulnerable to Log4Shell (IBM, Google, CISA, etc.). Log4Shell is an exploit that cyber security specialists are saying is unprecedented and will linger for months if not years. This is definitely not how most cyber security professionals expected 2021 to end.
WHAT TO EXPECT IN 2022 & STAYING VIGILANT IN THE NEW YEAR
Most of what we’ve witnessed in 2021 is likely to show up again in 2022 in some form or fashion. When thinking about protection for 2022, we should be focusing on Critical Access Management. Critical Access Management is the key to protecting organizations from cybercriminals and that appears to be something that is lacking amongst organizations.
Access control, access monitoring, and access governance are three solutions that could mean the difference between having to shut down an entire industry and keeping your environment free from intruders. With these three solutions, you will be able to gain visibility into who has access to devices, systems, and software. You will also be able to implement access controls like Zero Trust Network Access, as well as be able to monitor access for insight and prevention.
Log4Shell gave organizations the wake-up call they needed. A simple vulnerability turned the internet upside down and most will spend many months trying to mitigate attacks. We can expect threat actors to use Log4Shell to deploy ransomware and execute double extortion next year. Is your organization prepared for that?
After the new year, expect to see more coordinated activity from RaaS gangs that include improvement in the collaboration between the private and public sectors. We can also expect to see more involvement from law enforcement when it comes to cracking down on RaaS gangs and cybercriminals in general, just as we did with Cl0p and REvil. Software Dependency Compromises are also likely to take the lead in 2022, like Log4Shell.
how avertium is protecting our clients
In 2022, some of the largest ransomware gangs may try to fly under the radar and re-group with smaller, lesser-known ransomware gangs. Instead of letting your guard down during that time, focus on being proactive with security instead of reactive. Avertium strives to keep your organization free from intruders with our managed services. Please take a look at some of the services we can offer you in 2022 and beyond.
- Increasing visibility within your environment is crucial when trying to prevent or mitigate a potential attack from botnets. Avertium offers EDR protection through SentinelOne, Sophos, and Microsoft Defender.
- SentinelOne prevents threats and extends protection from the endpoint and beyond. Find threats and eliminate blind spots with autonomous, real-time, index-free threat ingestion and analysis that supports structured, unstructured, and semi-structured data.
- Our Partners, Microsoft and Sophos, also offer endpoint protection. Sophos can help secure your environment by protecting and prioritizing potential threats. Microsoft Defender provides real-time threat detection, as well as firewall and network protection. The program comes standard with Windows.
- Avertium also offers user awareness training and phishing simulation campaigns using KnowBe4.
- Today’s attack surface extends beyond your physical IT assets, now encompassing your entire digital footprint. This expansion has fundamentally changed the surface area that security teams must protect. Gone are the days of vulnerability management serving as an adequate defense for your attack surface… today’s cybersecurity professionals have to think bigger: they have to think about attack surface management (ASM). Avertium offers Attack Surface Management and 3rd Party Vendor Risk services to keep your organization ahead of the curve.
- Avertium also offers continuous monitoring of the threat landscape with automatic synchronization of IoCs into our MDR/XDR
- Avertium offers web application pen testing for software dependency compromise.
recommendations
Supply Chain Attacks – Kaseya, SolarWinds, & Colonial Pipeline
- Assess your third party’s risk before you begin work with them by gathering intelligence on their attack surface and considering how it affects yours.
- Define security standards your vendors must comply with, especially those with persistent connections to your environment
- Continuously monitor your vendors’ attack surfaces and work with them to help optimize their cybersecurity.
- Require multi-factor authentication log-ins.
- Have contractual rules and regulations limiting the use and knowledge of your data.
Initial Access – ProxyShell, SonicWall, Fortinet, Atlassian Confluence, & Accellion
- Patch your devices. Using end-of-life software makes your device vulnerable to attacks.
- If disabling NTLM is not possible, use an unofficial 0patch to block NTLM relay attack vector or apply filters to block access to vulnerable functions.
- Enable multifactor authentication (MFA) as a safety measure.
- MFA has an invaluable safeguard against credential theft and is a key measure of good security posture.
- Reset the passwords for any users who may have logged into the device via the web interface.
Lateral Movement – FatPipe & Zoho ManageEngine
- Avertium recommends that you patch your device as soon as possible.
- We also recommend a Zero Trust Architecture, like AppGate, to stop malware lateral movement.
Privilege Escalation – PrintNightmare, Microsoft Azure, & Emotet
- Apply security patches to your devices when they are released.
- Provide awareness training for employees regarding the dangers of phishing emails.
CISA recommends organizations take the following actions to strengthen their defenses:
- Increase organizational vigilance by ensuring there are no gaps in Information Technology (IT)/Operational Technology (OT) security personnel coverage and that staff provides continual monitoring for all types of anomalous behavior.
- Prepare your organization for rapid response by adopting a state of heightened awareness. Create, update, or review your cyber incident response procedures and ensure your personnel are familiar with the key steps they need to take during and following an incident.
- Ensure your network defenders implement cybersecurity best practices. Enforce multi-factor authentication and strong passwords, install software updates (prioritizing known exploited vulnerabilities), and secure accounts and credentials.
- Stay informed about current cybersecurity threats and malicious techniques. Encourage your IT/OT security staff to subscribe to CISA’s mailing list and feeds to receive notifications when CISA releases information about a security topic or threat.
- Lower the threshold for threat and information sharing. Immediately report cybersecurity incidents and anomalous activity to CISA and/or the FBI.
MITRE TTPs:
Please click on the links below to see the MITRE TTPs for the following vulnerabilities:
- ProxyShell
- SonicWall
- Accellion
- FatPipe
- Zoho ManageEngine
- PrintNightmare
- Microsoft Azure
- Emotet
- Log4Shell
Indicators of Compromise (IoCs):
Please click on the links below to see the IoCs for the following vulnerabilities:
- ProxyShell
- SonicWall
- Accellion
- FatPipe
- Zoho ManageEngine
- PrintNightmare
- Microsoft Azure
- Emotet
- Log4Shell – here and here
Supporting Documentation
July 4th Post Mortem on PrintNightmare and REvil (avertium.com)
Flash Notice - Microsoft Azure OMIGOD Vulnerability (avertium.com)
Azure Zero-Day Bugs Show Lurking Supply-Chain Risk | Threatpost
Preparing For and Mitigating Potential Cyber Threats | CISA
Microsoft warns of critical Windows ‘PrintNightmare’ vulnerability - The Verge
OMIGOD Vulnerability Exposes Virtual Machines Running Inside Azure (datacenterknowledge.com)
Flash Notice - Emotet Botnet is Back with New Spam Campaigns (avertium.com)
Emotet now drops Cobalt Strike, fast forwards ransomware attacks (bleepingcomputer.com)
‘Tortilla’ Wraps Exchange Servers in ProxyShell Attacks | Threatpost
Security Advisory (sonicwall.com)
SonicWall VPN vulnerability is pretty much as serious as it gets | TechRadar
New ransomware group uses SonicWall zero-day to breach networks (bleepingcomputer.com)
Exchange, Fortinet Flaws Being Exploited by Iranian APT, CISA Warns | Threatpost
Updated Kaseya ransomware attack FAQ: What we know now | ZDNet
Updated Kaseya ransomware attack FAQ: What we know now | ZDNet
SolarWinds Attack: One Year Later, Cybersecurity Lessons For Pros (dice.com)
Colonial Pipeline Cyber Attack: Hackers Used Compromised Password - Bloomberg
The Different Types of Access Control | SecureLink
The biggest healthcare data breaches of 2021 | Healthcare IT News
President Biden’s Executive Order on Cybersecurity: What it does & What it doesn’t do (avertium.com)
This Year’s Largest Healthcare Data Breaches (healthitsecurity.com)
FBI: FatPipe VPN Zero-Day Exploited by APT for 6 Months | Threatpost
SonicWall customers urged to patch up immediately amid new ransomware attacks | TechRadar
U.S. and Europe Target Top Ransomware Cartel | Burr & Forman - JDSupra
The Internet’s biggest players are all affected by critical Log4Shell 0-day | Ars Technica
‘Extremely bad’ vulnerability found in widely used logging system - The Verge
Log4j – Apache Log4j Security Vulnerabilities
New zero-day exploit for Log4j Java library is an enterprise nightmare (bleepingcomputer.com)
Emerging threat details on CVE-2021-44228 in Apache Log4j · GitHub
APPENDIX II: Disclaimer
This document and its contents do not constitute and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of the Client's compliance with any law, regulation, or standard.