An In-Depth Look at the North Korean Threat Actor, ZINC
Executive Summary
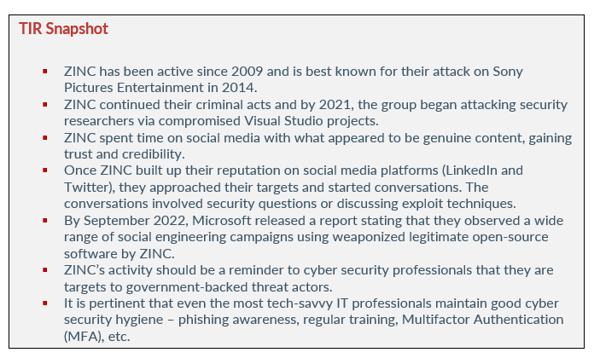
Since 2009, the North Korean threat actor ZINC (also known as Hidden Cobra by the U.S. government) has attacked organizations and individuals by way of highly sophisticated and evolving malware. The threat actor is a destructive, nation-state activity group that gained notoriety in 2014 when they attacked Sony Pictures Entertainment. The attack was in retaliation for the controversial film “The Interview”. The film was a satirical comedy about North Korean leader, Kim Jong Un.
ZINC is known for targeting security researchers, pen testers, and employees at security technology companies. In September 2022, Microsoft observed the threat actors targeting individuals from the Infosec community on social media platforms such as LinkedIn and Twitter. The threat actors spend months on social media platforms building their reputation before pulling the trigger on their targets. Let’s take a look at ZINC, their tactics and techniques, and how social engineering can fool those who were trained to recognize phishing attempts.
zinc
As we stated previously, ZINC has been active since 2009 and is best known for their attack on Sony Pictures Entertainment in 2014. The cyber attack led to the release of sensitive data about Sony employees, including financial records, salary information, Social Security numbers, and emails. The breach included four, non-released films and when the dust settled, the company lost millions of dollars. After the threat actors hacked Sony, they used the same aliases and accounts from the breach to send spear-phishing emails to several U.S. defense contractors.
ZINC continued their criminal acts and by 2021, the group began attacking security researchers via compromised Visual Studio projects. According to Microsoft, a Visual Studio project is a collection of code files and assets such as images, icons, etc. Those assets are built together using the “MSBuild” build system – a system for Visual Studio and is the best build system to use for Windows programs.
The Visual Studio project attack revealed that ZINC was associated with the Democratic People’s Republic of Korea (DPRK). Security researchers determined the association based on tradecraft, infrastructure, malware patters, and account affiliations. Microsoft, who has been tracking ZINC for quite some time, stated that the campaign was ongoing and that the threat actors used a variety of new techniques to target the security researchers.
ZINC spent time on social media with what appeared to be genuine content, gaining trust and credibility. They sent malicious Visual Studio projects and used a watering hole website embedded with browser exploits. ZINC’s objectives are geared towards espionage, data theft, financial gain, and network destruction
how did zinc build credibility AND TRUST?
Tactics & Techniques
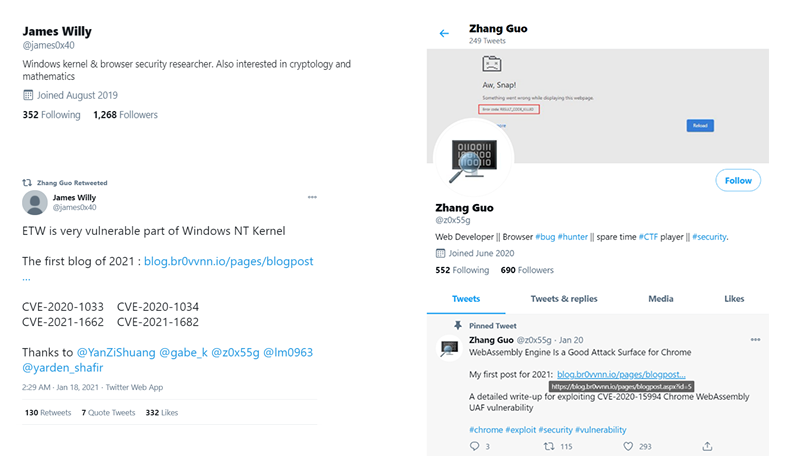
ZINC (a sub-group of Lazarus) spent a lot of time during 2020 establishing a research blog and several Twitter profiles to interact with their targets. They used the Twitter accounts to post links to their blog, which contained videos of their faux exploits. The Twitter account had a following of roughly 2,000 and included many prominent security researchers. The account also retweeted high quality security content and posted about exploit research from the blog controlled by the threat actor.
Image 1: Twitter Accounts Controlled by ZINC
Source: Microsoft
Once ZINC built up their reputation on social media platforms (LinkedIn and Twitter), they approached their targets and started conversations. The conversations involved security questions or discussing exploit techniques. If the target responded to the attacker positively, ZINC would try to lure them to another platform (Discord, email, etc.) or send files using encrypted or PGP protected ZIPs.
Because ZINC posted links to their bogus security blog within their Twitter posts, the links were retweeted and shared on other social media platforms by security professionals who followed them, as well as those who did not. In October 2020, a blog post titled DOS2RCE: A New Technique to Exploit V8 NULL Pointer Deference Bug, was shared by ZINC on Twitter.
Security researchers who weren’t contacted or sent files by the threat actor clicked on the links while using the Chrome browser. As a result, ZINC malware ended up on their machines. Although not confirmed by researchers, this chain of events indicates that a Chrome browser exploit chain was hosted on the blog. It was further suspected (but not proven) that because some of the victim’s browsers were not patched, the exploit chain used 0-day or patch gap exploits.
By September 2022, Microsoft released a report stating that they observed a wide range of social engineering campaigns using weaponized legitimate open-source software by ZINC. The threat actor was seen targeting employees within media, defense and aerospace, IT, and IT services. The countries of their targets are in the U.S., Russia, the UK, and India.
In June 2022, Microsoft observed ZINC using social engineering tactics to connect with individuals on LinkedIn – once again establishing trust and credibility. After successful communication and establishing trust, ZINC lured their targets off LinkedIn and onto the messaging app WhatsApp. The app acted as a vehicle to deliver malicious payloads. In addition to weaponizing WhatsApp, ZINC also weaponized a wide range of open-source software including KiTTY, PuTTY, TightVNC, Sumatatra PDF Reader, and muPDF/Subliminal Recording software installer for their attacks.
Since June 2022, ZINC has compromised numerous organizations and has attempted to move laterally and exfiltrate data from victim networks. Microsoft stated that because of the wide use of platforms and software ZINC utilizes in their LinkedIn campaign, they could be a serious threat to organizations and individuals across various sectors and regions.
ZINC has been tracked by other security companies (Black Artemis, and Labyrinth Chollima) and uses a variety of custom remote access tools or RATs, including FoggyBrass and PhantomStar. Although the group has launched attacks for various reasons, their attacks are similar to state-sponsored activities such as evolving and sophisticated malware, heightened operational security, and politically motivated targeting.
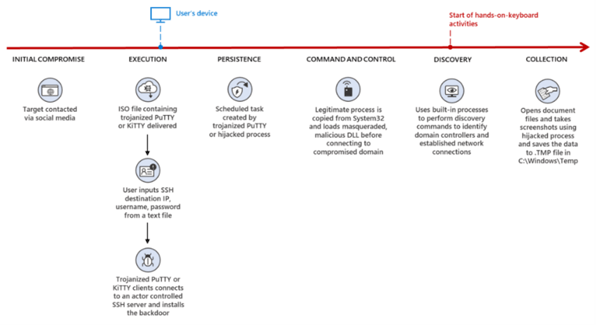
Image 2: ZINC's Attack Flow
Source: Microsoft
Additionally, Microsoft stated that they observed at least five methods of Trojanized open-source applications containing the ZetaNile malware family. Implant DLLs in the ZetaNile malware are either encrypted using custom algorithms or packed with commercial software protectors such as VMProtect and Themida. Once ZINC establishes a connection with their target, they operationalize malicious versions of two SSH clients – PuTTY and KiTTY. The SSH clients act as the entry point for the ZetaNile implant. It is important to note that the malicious versions of PuTTY and KiTTY are not official and are from disreputable sources. Therefore, they would not match the signatures of the real thing. This is why one should ALWAYS verify files.
PuTTY was Trojanized by ZINC and used as a part of their attack chain for years before they started using KiTTY. According to Microsoft, the most recent variant of ZINC’s Trojanized PuTTY establishes persistence on compromised devices by utilizing scheduled tasks.
“Both utilities provide terminal emulator support for different networking protocols, making them attractive programs for individuals commonly targeted by ZINC. The weaponized versions were often delivered as compressed ZIP archives or ISO files. Within that archive, the recipient is provided a ReadMe.txt and an executable file to run.” – Microsoft
Microsoft explained that in order for ZetaNile to be deployed, the SSH utility requires the IP provided in the ReadMe.txt file – this helps ZINC evade traditional security defenses. Once ZINC is able to persuade victims to move from LinkedIn to WhatsApp, they deliver the ZetaNile malware to their victims. As we stated above, ZINC used PuTTY in the past, but they have recently started using KiTTY as well. ZINC has expanded their capabilities and they have started to weaponize KiTTY, which is a fork of PuTTY.
After the executable collects the hostname and username of the victim’s system, it sends the information to a hardcoded IP address over TCP/22. Once there is a successful TCP connection to the server, the KiTTY executable deploys the malware as %AppData%\mscoree.dll followed by several rounds of decoding.
In addition to KiTTY, ZINC was observed using a Trojanized version of TightVNC Viewer remote administration application, along with two PDF readers, Sumatra PDF and muPDF/Subliminal Recording installer.
Image 3: Malicious VNC Remote Access Tool
Image 4: Malicious KiTTY.exe Remote Access Tool
Image 5: Malicious Secure PDF Reader
security researchers are targets
ZINC’s activity should be a reminder to cyber security professionals that they are targets to government-backed threat actors. Security professionals should always remember to remain vigilant when engaging with individuals they have not previously communicated with on social media platforms.
LinkedIn Threat Prevention and Defense observed ZINC creating profiles and pretending to be technology, defense, and media entertainment recruiters with the goal of moving their targets off LinkedIn and on to WhatsApp for delivery of malware. Technical support professionals and engineers working at information technology and media companies were the primary targets for ZINC.
The threat actors sent outreach to each target and tailored it to the individual’s profession or background. They then were encouraged to apply for an open position at legitimate companies. When LinkedIn learned of the fraudulent activity, they terminated accounts associated with the threat actor.
However, LinkedIn could not terminate those accounts before unknowing victims were compromised. Security professionals are trained to spot phishing attempts, hacking attempts, and other malicious threats. However, even the most educated security professional can fall victim to a highly sophisticated threat actor like ZINC. When social engineering is combined with highly targeted spear phishing, it can be difficult to spot.
It's pertinent that even the most tech-savvy security professionals maintain good cyber security hygiene – phishing awareness, regular training, Multifactor Authentication (MFA), etc. Engineers that communicate with individuals for the first time on social media platforms need to be especially careful due to their positions often being associated with privileged access.
If you are recruited by a tech company that asks you to download archives from WhatsApp (or another encrypted messaging app) and run custom executables, this should be seen as alarming. Keep in mind that a large company or startup has other ways to assess job candidates.
Social engineering happens when threat actors like ZINC influence or manipulate victims so they can gain control over their computer system. The threat actors who use social engineering don’t discriminate and anyone can fall victim to their tricks, including cyber security professionals. The same best practices that cyber security professions stress to those outside of the industry, are the same best practices they should adhere to. Some of the most obvious indications that you might be a target of social engineering include:
- Addressing you in a generic way by using Sir/Madam
- Asking you to click on a misleading URL hyperlink
- The “From” email address looks suspicious
- Trying to persuade you to move your communication from one platform to another
- Trying to persuade you to download attachments
- Someone you have never met online or offline, tries to start a random connection/relationship with you on a social media platform
Things to avoid on social media:
- Sharing your work email address
- Sharing phone numbers
- Sharing addresses of any kind
- Sharing your financial status
- Sharing your job role (may be impossible with career related social media platforms like LinkedIn)
- Sharing your location
- Sharing screenshots of conversations
How Avertium is Protecting Our CUSTOMERS
It’s important to get ahead of the curve by being proactive with protecting yourself and your organization, instead of waiting to put out a massive fire. Avertium offers the following services to keep you and your organization safe:
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium’s offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills.
- Fusion MXDR is the first MDR offering that fuses together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is great than the sum of its parts.
- Avertium offers Vulnerability Management to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Avertium offers user awareness training through KnowBe4. The service also Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
avertium's recommendations
ZINC’s techniques can be mitigated by adopting the security considerations provided by Microsoft:
- Block in-bound traffic from IPs specified in the “Indicators of compromise” table.
- Review all authentication activity for remote access infrastructure, with a particular focus on accounts configured with single factor authentication, to confirm authenticity and investigate any anomalous activity.
- Enable multifactor authentication (MFA) to mitigate potentially compromised credentials and ensure that MFA is enforced for all remote connectivity. NOTE: Microsoft strongly encourages all customers download and use password-less solutions like Microsoft Authenticator to secure your accounts.
- Educate end users about preventing malware infections, including by ignoring or deleting unsolicited and unexpected emails with ISO attachments. Encourage end users to practice good credential hygiene—limit the use of accounts with local or domain admin privileges and turn on Microsoft Defender Firewall to prevent malware infection and stifle propagation.
- Educate end users about protecting personal and business information in social media, filtering unsolicited communication, identifying lures in spear-phishing email and watering holes, and reporting of reconnaissance attempts and other suspicious activity.
Mitigation
Unfortunately, there is a chance that ZINC is successful in their social engineering attack. However, there are things you can do to thwart the attack from getting any further:
- Behavioral analysis will spot anomalous activity.
- Monitoring outgoing traffic will reveal suspicious activity.
- Keep in mind that most cyber criminals don’t always use IP addresses associated with the hidden web but opt for genuine platforms and C2-like servers. This makes it very difficult to catch sophisticated threat actors, particularly since victims may use the same platforms consistently.
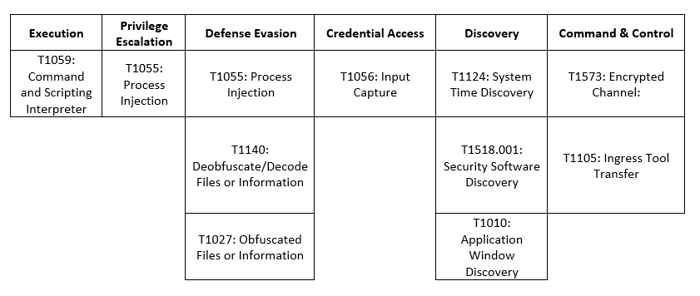
MITRE Map
Indicators of Compromise (IoCs)
File Names
|
§ amazon_assessment_test[.]iso |
|
§ SecurePDF[.]exe |
|
§ amazon_assessment_test[.]iso § Amazon-KiTTY[.]exe § Amazon_IT_Assessment[.]iso § IT_Assessment[.]iso |
File Paths
- C:\ProgramData\Comms\colorui[.]dll
- %APPDATA%\KiTTY\mscoree[.]dll
IP Addresses
- 172[.]93[.]201[.]253
- 137[.]184[.]15[.]189
- 44[.]238[.]74[.]84
Hashes
- 63cddab76e9d63e3cbea421b607342735d924e462c40f3917b1b5fbdf8d4a20d
- 1492fa04475b89484b5b0a02e6ba3e52544c264c294b57210404b96b65e63266
- aaad412aeb0f98c2c27bb817682f08673902a48b65213091534f96fe6f5494d9
- e1ecf0f7bd90553baaa83dcdc177e1d2b20d6ee5520f5d9b44cdf59389432b10
- c5a470cdf6f57125a8671f6b8843149cc78ccbc1a7bc615f34b23d9f241312bf
- 71beb4252e93291c7b14dfcb4cbb5d58144a76181fbe4aab3592121a3dbd9c55
Domains
- olidhealth[.]com/wp-includes/php-compat/compat[.]php
- hurricanepub[.]com/include/include[.]php
- turnscor[.]com/wp-includes/contacts[.]php
- elite4print[.]com/support/support[.]asp
- cats[.]runtimerec[.]com/db/dbconn[.]php
- recruitment[.]raystechserv[.]com/lib/artichow/BarPlotDashboard[.]object[.]php
Supporting Documentation
Sony Drops ‘The Interview’ Following Terrorist Threats - The New York Times (nytimes.com)
North Korean programmer charged in Sony hack, WannaCry attack | PBS NewsHour
Visual Studio Projects - C++ | Microsoft Learn
DPRK Job Opportunity Phishing via WhatsApp | PuTTY Utility (mandiant.com)
North Korean threat actors spread poisoned open source wares • The Register
North Korea-Sponsored Hackers Attack with Bad-Code Visual Studio Projects -- Visual Studio Magazine
New campaign targeting security researchers (blog.google)
ZINC attacks against security researchers - Microsoft Security Blog
Lazarus Group Affiliate Uses Trojanized Open Source Apps in New Campaigns | Decipher (duo.com)
ZINC weaponizing open-source software - Microsoft Security Blog
ZINC Hackers Leverage Open-source Software to Lure IT Pros | eSecurityPlanet
Lazarus Affiliate ‘ZINC’ Blamed for Campaign Against Security Researcher | Threatpost
New campaign targeting security researchers (blog.google)
Numerous orgs hacked after installing weaponized open source apps | Ars Technica
7 Best Practices to prevent Cyberattacks, Downtime and Data Breaches (teamviewer.com)
How Hacker's Use Social Media For Social Engineering Attacks (usecure.io)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.