New Ransomware Strains - CryptNet, Mallox, and Xollam
executive summary
Although ransomware appeared to decline towards the end of 2022, there seemed to be an uptick in ransomware attacks during the second quarter of 2023. Research from SonicWall showed a 74% increase in ransomware attacks compared to the first three months of the year. According to findings by SonicWall Capture Labs Threat Researchers, the first quarter of 2023 witnessed a relatively low number of ransomware attacks, totaling 51.2 million incidents. This marked the lowest figure recorded since the fourth quarter of 2019.
In contrast, the second quarter of 2023 experienced a resurgence in ransomware activity, with a substantial increase of 74%, totaling 88.9 million attacks. Nonetheless, the upswing in ransomware attacks observed throughout April, May, and June of 2023 suggests a potential resurgence in attacker activity. The report highlighted this concern, stating, "When considering the monthly patterns, it becomes apparent that ransomware may resurge as we progress through 2023."
In July 2023, Chainalysis found that in the first half of 2023, ransomware attackers made $176 million more than they did during the same period in 2022. This is a reversal of the trend we saw in 2022 when ransomware attacks were decreasing. Now, there are new ransomware strains contributing to the rise of ransomware attacks. CryptNet, Mallox, and Xollam are new strains with operators that have intensified the way they attack, posing new challengers for cybersecurity professionals. Let’s dive into the details of these ransomware strains and explore measures organizations can take to protect themselves.
tir snapshot
- CryptNet emerged in April 2023 and claims to exfiltrate data prior to performing file encryption.
- CryptNet's attack region is worldwide, and their targeted industries include trading companies and distributers, as well as internet software and services.
- The ransomware operation uses code that is written in .NET and obfuscated using .NET Reactor.
- Mallox ransomware specifically targets computers running Microsoft Windows. This ransomware was first observed in June 2021 and is known for exploiting unsecured MS-SQL servers as a penetration vector to compromise victims' networks.
- Recently, researchers from Unit 42 have noticed a significant increase in Mallox ransomware activity, with a surge of almost 174% compared to 2022.
- Researchers have also reported that the group has attempted to distribute Mallox via phishing emails - suggesting affiliates may be involved.
- Mallox ransomware operators claim to have breached hundreds of organizations worldwide and Unit 42 stated that their telemetry indicates at least dozens of potential Mallox victims.
- Researchers believe the Xollam is also a variant of the TargetCompany ransomware strain due to the operators using similar techniques.
- Xollam employs a pseudo-fileless technique using PowerShell. This involves the execution of reflective loading to download its payload. Xollam is also a variant of the TargetCompany
cryptnet
In May 2023, the threat researchers at ZScaler published technical details about the ransomware strain, CryptNet. The strain emerged in April 2023 and the operators claim to exfiltrate data prior to performing file encryption. According to ZScaler, CryptNet has a data leak site that lists two victims from April 2023. CryptNet appears to be a ransomware-as-a-service (RaaS) operation – recruiting affiliates via criminal forums. [1]Surprisingly, affiliates have the chance of a 90% cut, which is a big jump from the 60-80% share most groups offer.
CryptNet’s attack region is worldwide, and targeted industries include trading companies and distributors, as well as internet software and services. CryptNet promotes itself as high-speed, completely undetectable ransomware, claiming to have the ability to delete shadow copies, perform offline encryption, and disable backup services. The ransomware operators also have a chat panel for ransom negotiations.
TACTICS AND TECHNIQUES
ZScaler’s research states that CryptNet uses code that is written in .NET and obfuscated using .Net Reactor. Upon removing the obfuscation layer, it becomes clear that CryptNet bears striking similarities to the Chaos ransomware family, particularly its latest variant, Yashma. These similarities include encryption techniques, the ability to disable backup services, and the deletion of shadow copies, as mentioned above. CryptNet seems to have enhanced the Yashma code, resulting in better file encryption performance.
Image 1: String Decryption Algorithm
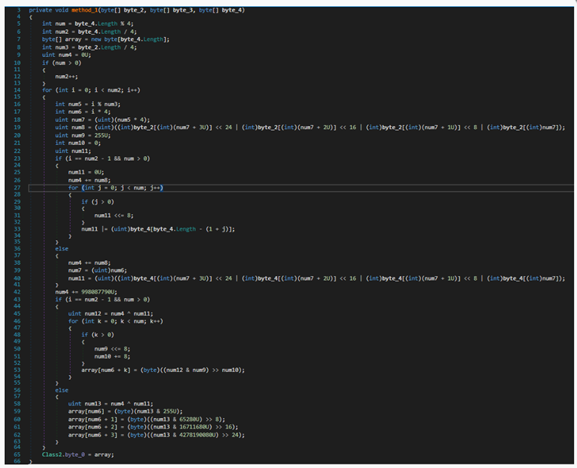
Source: ZScaler
[1] CryptNet: Russian ransom gang makes its debut | Cybernews
Despite the researchers successfully removing the obfuscation layer, they encountered a situation where the vital information within the ransomware code remained concealed within a resource section. This section was further protected through encryption using a customized algorithm. Once decrypted, the strings appear to be stored in sequence, with each string preceded by a DWORD value indicating its size.
One of the initial steps carried out by the ransomware involves creating a decryption ID, which is later included in the ransom note. Once CryptNet creates the victim ID, it begins the main encryption process. The ransomware excludes the following directories from encryption:
- windows.old
- windows.old.old
- amd
- nvidia
- program files
- program files (x86)
- windows
- $recycle.bin
- documents and settings
- intel
- perflogs
- programdata
- boot
- games
- msocach
The following file names are also excluded from encryption:
- iconcache.db
- autorun.inf
- thumbs.db
- boot.ini
- bootfont.bin
- ntuser.ini
- bootmgr
- bootmgr.efi
- bootmgfw.efi
- desktop.ini
- ntuser.dat
Here is a sample of file extensions (that have a matching file) CryptNet will encrypt:
- .myd
- .ndf
- .qry
- .sdb
- .sdf
- .tmd
- .tgz
- .lzo
- .txt
- .jar
- .dat
- .xlsx
- .ppt
- .pptx
- .odt
- .jpg
- .csv
- .dif
The ransom note that CryptNet drops during the encryption process is named RESTORE-FILES-[9 random chars] . txt. See the note below.
Image 2: CryptNet Ransom Note
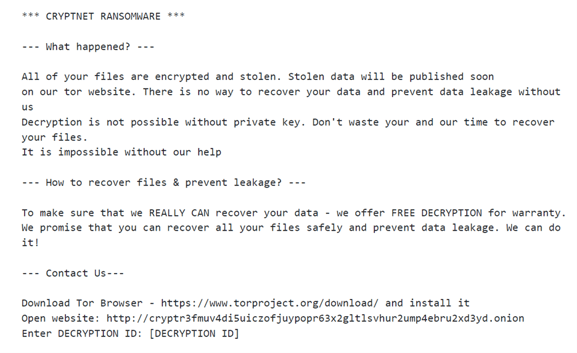
Source: ZScaler
Furthermore, when the ransomware is executed with administrator privileges, CryptNet will stop a list of services. It also removes Window shadow copies before deleting the backup catalog if the ransomware has administrator privileges. Once a victim enters the Tor site mentioned in the ransom note, a login screen asks them to enter a decryption ID and solve a captcha. Next, a timer is displayed with the option to test file decryption. There is also a chat feature to negotiate ransom payments. The chat feature also provides a link to CryptNet’s data leak site.
Although CryptNet does use the same codebase as the Yashma and Chaos ransomware families, CryptNet lacks some of Yashma’s features which include lack of persistence and language/country restrictions. It’s clear that CryptNet has taken the codebase of Yashma and Chaos and increased the file encryption efficiency.
mallox and xollam
MALLOX
Mallox ransomware specifically targets computers running Microsoft Windows. This ransomware was first observed in June 2021 and is known for exploiting unsecured MS-SQL servers as a penetration vector to compromise victims’ networks. The ransomware’s targeted industries are manufacturing, professional and legal services, and wholesale and retail. The ransomware operators claim that their victims include worldwide organizations.
According to Lior Rochberger, a senior security researcher at Palo Alto Networks, Mallox’s sudden increase in activity is attributed to the deliberate actions taken by the group's leaders to expand Mallox's operations. Rochberger stated that group appeared to focus more on recruiting affiliates at the beginning of 2023. This shift in strategy explains the significant increase observed this year.
Recently, researchers from Unit 42 have noticed a significant increase in Mallox ransomware activity, with a surge of almost 174% compared to 2022. This increase is primarily due to Mallox using vulnerable MS-SQL (CVE-2020-0618 and CVE-2019-1068) servers to spread the ransomware. Unit 42 also observed Mallox using tactics such as brute force, data exfiltration, and the use of network scanning tools.
Researchers have also reported that the group has attempted to distribute Mallox via phishing emails – suggesting affiliates may be involved. Once the threat actors gain access, they use the command line and PowerShell to download the Mallox ransomware payload from a remote server. Like other ransomware groups, the initial payload tries to deactivate any services that might hinder data encryption on the targeted system. Also, it tries to erase shadow copies, making data recovery more challenging after encryption. The malware also attempts to eliminate all event logs, utilizing a commonly used Microsoft command utility to try and complicate forensic analysis.
Like CryptNet, the threat actors behind Mallox use the double extortion method – stealing data before encrypting it. They also have a data leak site where they leak the data of victims that refuse to pay or negotiate its ransom demands. Victims negotiate with the threat actors by using a private key to authenticate themselves.
As previously stated, the ransomware operators claim to have breached hundreds of organizations worldwide. Unit 42 stated that their telemetry indicates at least dozens of potential Mallox victims. In 2022, Mallox ransomware was discovered to be a variant of the TargetCompany ransomware strain.
XOLLAM
Researchers believe that Xollam is also a variant of the TargetCompany ransomware strain due to the operators using similar techniques. According to TrendMicro, in 2023, Xollam was seen using phishing campaigns and Microsoft OneNote files to access and distribute malware - a departure from the TargetCompany and Mallox’s previous focus on exploiting vulnerable MS SQL databases.
According to Trend Micro’s investigation, Xollam employs a pseudo-fileless technique using PowerShell. This involves the execution of reflective loading to download its payload. Trend Micro also observed the technique in earlier variants of the TargetCompany ransomware.
The latest version of the ransomware, Xollam, was found in February of this year. In that same month, the older version of Mallox was also active and was responsible for an attack on the Federation of Indian Chambers of Commerce and Industry (FICCI).
The TargetCompany is known to be a small and closed group. It’s clear that the operation is now exploring new methods and expanding its reach by participating in OneNote phishing campaigns. This shift allows the TargetCompany to target a broader range of potential victims, leading to higher profits.
In just two years of operation, the cybercriminals behind the ransomware have extended their operations by introducing a RaaS affiliate program and maintaining multiple channels to publicize victims and publish stolen data.
conclusion
Ransomware operations are constantly evolving and adapting their tactics. CryptNet, for instance, evolved from Yashma and streamlined its code for better performance. Mallox shifted from primarily targeting MS SQL databases to using phishing campaigns with OneNote files, showing the desire to diversify their victim base. The evolving tactics, increased modification, and persistence of ransomware groups/strains underscore the ongoing need for robust cybersecurity measures, timely patching, and user education to protect against ransomware threats.
avertium's recommendations
Best practices when that can help protect organizations from ransomware operations like Mallox, Xollam, The TargetCompany, and CryptNet.
- Administrator Accounts - Minimize the use of administrator accounts (at both the local and domain level). All domain administrators should have standard accounts for day-to-day use and additional administrator accounts that are only used when required.
- DLP Software - Use Data Loss Prevention (DLP) software to detect and block aggregation and exfiltration of sensitive data.
- Disable RDP - Where possible disable the use of Remote Desktop Protocol via GPO and do not allow users to install other remote access software.
- Maintain Backups - Back up all data and test those backups regularly. Even if you become the victim of a ransomware attack, your business operations won’t be severely interrupted, and your data will be retrievable.
- Install updates regularly – maintain patch management protocols and keep your operating systems and applications up to date. This action will deter threat actors from exploiting software vulnerabilities.
- MFA - Using phishing resistant MFA on all accounts, especially VPNs, webmail, and accounts with access to critical systems will prevent attackers from performing lateral movement inside a network.
- EDR - Deploy and monitor Endpoint Detection and Response or antivirus software and ensure that your analysts are trained to determine at what point of the cyber attack the detection relates to.
- Monitoring and Logging - Continuously monitor network traffic and maintain detailed logs for forensic analysis in case of an attack.
- Incident Response Plan - Should your organization be compromised; you will need a good incident response plan. Develop a comprehensive incident response plan that includes steps for containment, communication, and recovery in the event of a ransomware attack.
- Educate – user awareness training is essential for training employees on how to spot phishing attempts.
CVE-2020-0618
- Patch guidance for CVE-2020-0618 can be found in Microsoft’s advisory.
CVE-2019-1068
- Patch guidance for CVE-20219-1068 can be found in Microsoft’s advisory.
How Avertium is Protecting Our Customers
- Avertium offers VM to provide a deeper understanding and control over organizational information security If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Fusion MXDR is the first MDR offering that fuse together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.
- Avertium aligns your Cybersecurity Strategy with your business strategy, ensuring that your investment in security is also an investment in your business. Our Cybersecurity Strategy service includes:
- Strategic Security Assessments - Strengthening your security posture begins with knowing where your current program stands (NIST CSF, Security Architecture, Business Impact Analysis, Sensitive Data Inventory, Network Virtualization and Cloud Assessment).
- Threat Mapping – Leverage Avertium’s Cyber Threat Intelligence, getting a more informed view of your most likely attack scenarios (Threat Assessment and MITRE ATT&CK).
- Cyber Maturity Roadmap - Embrace a comprehensive, quantifiable, and well- organized approach to establishing and continuously enhancing your cybersecurity resilience (Policy + Procedure Development, Virtual CISO (VCISO), Training + Enablement, Tabletop Exercises, and Business Continuity + Disaster Recovery Plan).
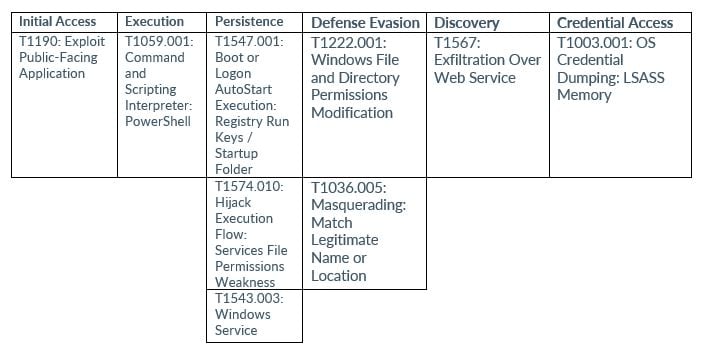
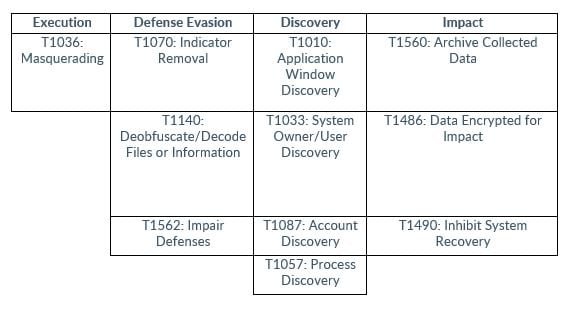
MITRE MAP
The TargetCompany/Mallox/Xollam
CryptNet
INDICATORS OF COMPROMISE (IOCs)
CryptNet
- SHA256
- 2e37320ed43e99835caa1b851e963ebbf153f16cbe395f259bd2200d14c7b775
- 1cc7283ee218081f2f056bd2ec70514e86b8dcb921342dc9aed69e7480dec18e
Mallox
- MD5
- 06e7ad104aef0633e4817e1159851d16
- 1b30d16d3e632130ced6dc8b403d4275
- 358d3a87ed243e4c9e95e41525d8a839
- 4339e52e9b1167955101805581aad0ff
- 982eea76139e00ac3499dc5075f31184
- e135c9c231bc82dcc7d4aa90616e8caa
- eb544a86cd780ad5973b72dc8f3e442f
- f8a9481b18f14339bad0cd4e3efeacfb
- SHA1
- 090d7476a0beffea8915e6534a947c957c878608
- 10ddbc228c564940d22a1b0424aeb55b48b4c0f7
- 60212fddfb3d5ed6b7bdc0ee08aa6e98faed2a8c
- 930b5fe5ceeffd3c84be48932b8c94ae4760da5b
- cf617de3d9d9279a1dec7ae157d451b45f97f0e9
- d4f5c84268597440256197462a4b53acd3c5b1be
- e39bf90a383548311753a116c346b47a0d63ad9d
- e5b8a0be4520050a1014a3fed9f500b3a430aec1
- A complete list of IoCs for Mallox can be found here.
The TargetCompany
- SHA256
- 4f4ee2de8f18bf758d72ac288e61071e1be2ddc54a140cd512c97f5473461036
- 52c208f15dbe2f7e8e5bc1a12d4a579ecbdbaff0ca6134a31cfd4fa0f574c561V
- dd662fc0cd4ec73f79520dd15c5d771fb5eed2f41c6fe4f24c8af186c7a8da03
- 4d15aa5d68b0e8b081c18d0ee5c06cc1758d17246a8d01b3c8ac48d1ef07610b
- 5e10d57402829425c50d2b7b0c7210433e337e6477e9d90626287cbc97f8df72
- a96a3edd745708a6be84086feff906d72f7a2d7ce154037436cc236d1662b577
- cb9ad9670dcb82aa54a6526d35fee8ed1e63a1abbb29d2db2acb3f5e49b66aac
- 76e7050683f047ad7807f0fe903bac27cb043cef2981028cadbc6adce4b3cea9
- 937e8cf5c406f171696985b30f88d3e91f1d6c69e7489e2e4ea2609c641f7bd9
- 6d656133f5bac8282f31cc82ca0e3869692164a6907037aabc134736adc87b35
- 1cbaed19d1cea23187d6ac7a0d27af6f11ba84eda6e939c99250ed112cad3ff0
- 4efdb7795d40a6d561dea7b059291d78d0a9812d3957888e9997df0aac7b8afd
- 18d7fa5e19af651f0ad91eea15398110e031964ad759b3e3809fd0a0a71a2507
- f8417f60910e5ff5f83169f833a3c5321b5ad64c4b2f8fd196d6d8fd53deb77
- 8820fe6c0f2d9f702a91f92a275a534de63e88de46f2baa05d50d4d7855bf319
- ca0cb45269f4b45b22da052108d18724485d09165e69877f32a153563168fc8e
- A complete list of IoCs for the TargetCompany can be found here.
Supporting Documentation
Mid-Year Update to the 2023 SonicWall Cyber Threat Report | Threat Intelligence
Ransomware Attacks Skyrocket in Q2 2023 - Infosecurity Magazine (infosecurity-magazine.com)
Mallox Ransomware Group Escalates Cyber Threat with Enhanced Evasion Tactics (speartip.com)
CryptNet: Russian ransom gang makes its debut | Cybernews
Mallox Ransomware Exploits Weak MS-SQL Servers to Breach Networks (thehackernews.com)
Technical Analysis of CryptNet Ransomware - Security Boulevard
KB4535305 - SQL Server Reporting Services remote code execution vulnerability - Microsoft Support
New CryptNet Ransomware-as-a-Service Announced on RAMP | ZeroFox
Mid-Year Update: 2023 SonicWall Cyber Threat Report
PowerPoint Presentation (hivepro.com)
Threat Group Assessment: Mallox Ransomware (paloaltonetworks.com)
Xollam the Latest Face of TargetCompany (trendmicro.com)
Mallox Ransomware Group Activity Shifts Into High Gear (darkreading.com)
Ransomware Spotlight: TargetCompany - Security News (trendmicro.com)
documents.trendmicro.com/assets/txt/ransomware-spotlight-TargetCompany-terminated-IOCs-rwdW7GY.txt
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.