Phobos Ransomware
executive summary
Since 2019, Phobos ransomware has targeted critical infrastructure sectors, with attacks resulting in the successful encryption of data and ransom demands totaling millions of dollars. Phobos operates as a ransomware-as-a-service (RaaS) model, facilitating various extortion campaigns that cause significant financial harm to victims.
A recent advisory issued by several U.S. cybersecurity and intelligence agencies, including the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Multi-State Information Sharing and Analysis Center (MS-ISAC), sheds light on the sophisticated tactics used by threat actors in deploying Phobos.
Phobos ransomware is often paired with various open-source tools like SmokeLoader, Cobalt Strike, and Bloodhound. These tools are readily available and are user-friendly across different operating environments, making Phobos and its variants a popular choice among threat actors. These recognizable tools are increasingly being utilized by threat actors in attacks targeting county governments, emergency services, educational institutions, and other entities.
Let’s look at Phobos ransomware, the ransomware’s tactics and techniques, as well as recommendations on how organizations can protect themselves from this kind of threat actor.
tir snapshot
- Phobos ransomware, first identified in 2019, started its operations as a variant of Crysis/Dharma ransomware, and has since evolved into one of the most prolific ransomware strains in recent years.
- The ransomware's authors leverage the RaaS model, allowing other cybercriminals to distribute the malware and conduct attacks on a wide range of targets.
- Phobos typically encrypts files on infected systems, rendering them inaccessible until a ransom is paid, often in cryptocurrency.
- Phobos ransomware utilizes a variety of tactics and techniques to infiltrate and compromise target networks. It is among the ransomware that is distributed through compromised Remote Desktop (RDP) connections.
- Phishing emails containing malicious attachments or links are a common method used by threat actors to deliver the Phobos ransomware payload.
- Once inside the network, threat actors deploy remote access tools to establish a foothold, escalate privileges, and maintain persistence.
- Phobos ransomware uses a standardized three-phase process, leveraging Smokeloader to decrypt payloads and deploy additional malware. Smokeloader manipulates API functions to evade network defenses and obfuscate command and control activity, ultimately unpacking and executing payloads from stored memory.
- The ransomware's impact extends beyond data encryption, which can lead to the disruption of critical systems and business operations. To mitigate the threat of Phobos and similar ransomware variants, organizations must prioritize strong cybersecurity measures.
Phobos Ransomware
Phobos ransomware, first identified in 2019, started its operations as a variant of Crysis/Dharma ransomware, and has since evolved into one of the most prolific ransomware strains in recent years. The ransomware’s authors leverage the RaaS model, allowing other cybercriminals to distribute the malware and conduct attacks on a wide range of targets.
Phobos variants, including Backmydata, Devos, Eight, Elking, and Faust, have targeted government agencies, healthcare facilities, educational institutions, and critical infrastructure organizations worldwide. The ransomware typically encrypts files on infected systems, rendering them inaccessible until a ransom is paid, often in cryptocurrency.
The group operates with sophisticated tactics and techniques, often leveraging social engineering and exploiting vulnerabilities in target networks. The malware's modular architecture allows threat actors to customize their attacks, making it challenging for cybersecurity defenses to detect and mitigate the ransomware. The use of legitimate tools and techniques, such as remote access tools and open-source reconnaissance tools, further complicates detection efforts, allowing threat actors to maintain persistence within compromised networks.
Tactics + Techniques
Phobos ransomware utilizes a variety of tactics and techniques to infiltrate and compromise target networks. It is among the ransomware that is distributed through compromised Remote Desktop (RDP) connections. This method of infiltration is not uncommon, considering that hacked RDP servers are readily available in the underground market at affordable prices. As a result, threat groups find hacked RDP servers to be an appealing and cost-effective means of spreading their ransomware.
Phishing emails containing malicious attachments or links are a common method used by threat actors to deliver the Phobos ransomware payload. Additionally, threat actors utilize brute-force attacks to gain unauthorized access to networks.
Once inside the network, threat actors deploy remote access tools to establish a foothold, escalate privileges, and maintain persistence. Data exfiltration, deletion of backups, and widespread encryption of connected drives are primary objectives of Phobos attacks, often accompanied by threats of data leakage to coerce victims into paying the ransom.
EXECUTION AND PRIVILEGE ESCALATION
Once inside the network, Phobos actors execute additional payloads with elevated privileges, utilizing executables like 1saas.exe or cmd.exe. These commands allow for various Windows shell functions, granting control over system aspects with different permission levels. Threat actors exploit Windows API functions to bypass access controls, steal tokens, and escalate privileges, persistently attempting to authenticate until domain administrator access is achieved.
SMOKELOADER DEPLOYMENT
Phobos ransomware uses a standardized three-phase process, leveraging Smokeloader to decrypt payloads and deploy additional malware. Smokeloader manipulates API functions to evade network defenses and obfuscate command and control activity, ultimately unpacking and executing payloads from stored memory. This sophisticated deployment mechanism allows threat actors to execute malicious operations covertly.
ENCRYPTION
As for the encryption process, the researchers at Malwarebytes Labs analyzed the following sample of Phobos ransomware:
a91491f45b851a07f91ba5a200967921bf796d38677786de51a4a8fe5ddeafd2
They found that the ransomware is capable of encrypting files even without an internet connection, suggesting the presence of a hardcoded public key within its system. Each file undergoes encryption using either an individual key or an initialization vector, resulting in different ciphertexts for the same plaintext.
Image 1: Encryption Process
Source: Malwarebytes Lab
A wide range of files, including executables, fall victim to encryption. The threat actors append their email to the encrypted files, distinguishing them. Also, this specific variant of Phobos appends the extension '.acute' to the encrypted files, though other variants may use different extensions, typically following the pattern of .id[-][].
Upon analysis, Malwarebytes found that the encrypted content reveals no discernible patterns, indicating potential use of a stream cipher or a cipher like AES in CBC mode. This encryption process is illustrated in the transformation of a BMP file before and after encryption.
The encrypted file contains a distinct block at the end, separated from the encrypted content by padding bytes. The initial 16 bytes of this block vary for each file, possibly serving as an Initialization Vector. Additionally, a 128-byte block, consistent across files from the same infection, suggests the presence of an encrypted key uniquely generated in each run. Finally, a 6-character keyword, such as 'LOCK96', marks the conclusion of the encrypted file. Different versions of Phobos may use varying keywords, like 'DAT260'.
The ransomware code lacks obfuscation but uses AES encryption to protect certain constants and strings, decrypting them as needed. The AES key, although obfuscated, is hardcoded and imported whenever data decryption is required, with the Initialization Vector set to 16 NULL bytes.
Decrypted strings include a list of targeted file extensions and keywords. These extensions likely aid in identifying already encrypted files within the same ransomware family, with the extension for the current encryption round being hardcoded. Additionally, an encrypted string outlines the file extension formula, incorporating the Victim ID.
Before initiating encryption, the ransomware terminates a predefined list of processes to prevent them from impeding access to the targeted files. This list includes various processes such as database services (e.g., msftesql.exe, sqlservr.exe), desktop applications (e.g., excel.exe, outlook.exe), and communication tools (e.g., thunderbird.exe, skype.exe). These processes are systematically terminated to ensure smooth execution of the encryption process without interference from active applications or services.
ATTACKED TARGETS
Before initiating its malicious activities, Phobos checks the system locale, specifically examining the 9th bit of the output to identify systems with Cyrillic alphabets set as default, which it then avoids affecting. Both local drives and network shares are targeted for encryption, with Phobos first listing all files and comparing their names against hardcoded lists stored within the binary in AES encrypted form, separated by the delimiter ';'.
These lists include blacklists of system-related files and Phobos ransom note filenames, along with directories to skip, such as "C:\Windows". Additionally, there's a whitelist of file extensions, encompassing a wide range of formats from multimedia to document types, ensuring thorough encryption coverage during its operations.
Image 1: Phobos Ransomware Note
Source: Malwarebytes Lab
EXFILTRATION AND IMPACT
Phobos actors utilize WinSCP and Mega.io for file exfiltration, targeting legal, financial, and technical documentation for exfiltration. Following data exfiltration, threat actors hunt for and delete backups, preventing file recovery. Phobos ransomware encrypts all connected logical drives on the target host, continuing to search for and encrypt additional files while leveraging email, voice calls, and onion sites for extortion and communication purposes.
CONCLUSION
Phobos ransomware is a challenge for organizations across multiple sectors, as the ransomware’s threat actors use complex tactics to infiltrate networks, encrypt data, and demand ransom payments. From exploiting vulnerabilities in remote access protocols to using advanced encryption methods and obfuscation techniques, Phobos actors demonstrate a high level of sophistication in their operations.
The ransomware's impact extends beyond data encryption, which can lead to the disruption of critical systems and business operations. To mitigate the threat of Phobos and similar ransomware variants, organizations must prioritize strong cybersecurity measures, including secure remote access practices, comprehensive endpoint protection, regular data backups, and employee training to identify and respond to potential threats.
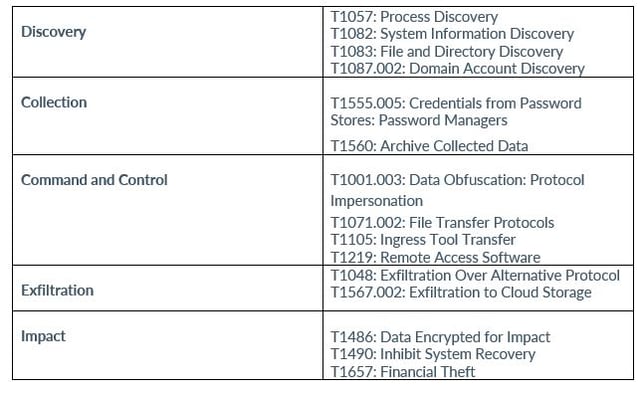
MITRE MAP
IOCs (INDICATORS OF COMPROMISE)
MD5
- 0900b61febed8da43708f6735ed6c11b
- 20d9fa474fa2628a6abe5485d35ee7e0
- 2809e15a3a54484e042fe65fffd17409
- 62885d0f106569fac3985f72f0ca10cb
- 69788b170956a5c58ebd77f7680fde7c
- 9376f223d363e28054676bb6ef2c3e79
- a567048dd823ff2d395ddd95d1fa5302
- b119cdd3d02b60009b9ad39da799ed3b
- db74cd067d4a0562b26ea4f10e943e3b
- e59ffeaf7acb0c326e452fa30bb71a36
- ecdf7acb35e4268bcafb03b8af12f659
- fe2d1879880466e24e76d8d0963feb93
SHA1
- 18ebb65842ccd3a1d1eeb597f2017267d47daaf9
- 33def89ad18a6c3dbaa4b5b5075a84a771157441
- 43683751209e85571072d953c0bdd44c883045ee
- 4a8f0331abaf8f629b3c8220f0d55339cfa30223
- 7332956debc4fb14a54d69b0b858bd5b04becac1
- 90b2cebbeb377480e321d8f38ea6de2fa661e437
- 93b0d892bd3fbb7d3d9efb69fffdc060159d4536
- a28af73bcfd4ebe2fe29242c07fec15e0578ec8a
- aed68cfa282ec2b0f8a681153beaebe3a17d04ee
- b092a6bf7fb6755e095ed9f35147d1c6710cf2c4
- c88fad293256bfead6962124394de4f8b97765aa
- cb37b10b209ab38477d2e17f21cae12a1cb2adf0
SHA256
- 0000599cbc6e5b0633c5a6261c79e4d3d81005c77845c6b0679d854884a8e02f
- 2704e269fb5cf9a02070a0ea07d82dc9d87f2cb95e60cb71d6c6d38b01869f66
- 32a674b59c3f9a45efde48368b4de7e0e76c19e06b2f18afb6638d1a080b2eb3
- 482754d66d01aa3579f007c2b3c3d0591865eb60ba60b9c28c66fe6f4ac53c52
- 518544e56e8ccee401ffa1b0a01a10ce23e49ec21ec441c6c7c3951b01c1b19c
- 58626a9bfb48cd30acd0d95debcaefd188ae794e1e0072c5bde8adae9bccafa6
- 7451be9b65b956ee667081e1141531514b1ec348e7081b5a9cd1308a98eec8f0
- 9215550ce3b164972413a329ab697012e909d543e8ac05d9901095016dd3fc6c
- a91491f45b851a07f91ba5a200967921bf796d38677786de51a4a8fe5ddeafd2
- c0539fd02ca0184925a932a9e926c681dc9c81b5de4624250f2dd885ca5c4763
- f1425cff3d28afe5245459afa6d7985081bc6a62f86dce64c63daeb2136d7d2c
- f3be35f8b8301e39dd3dffc9325553516a085c12dc15494a5e2fce73c77069ed
- fc4b14250db7f66107820ecc56026e6be3e8e0eb2d428719156cf1c53ae139c6
Domains
- adstat477d[.]xyz
- demstat577[.]xyz
- serverxlogs21[.]xyz
IPV4
- 147[.]78[.]47[.]224
- 185[.]202[.]0[.]111
- 194[.]165[.]16[.]4
- 45[.]9[.]74[.]14
Note: There are also several IoCs that are connected to 8Base ransomware. 8Base has been known to use Phobos ransomware in their attacks. You may find the complete list of 8Base IoCs here.
avertium's recommendations
- Secure remote access software by applying recommendations from the Guide to Securing Remote Access Software, focusing on secure design and default configurations.
- Implement application controls to manage software execution, including allowlisting remote access programs, to prevent unauthorized installations.
- Utilize intrusion detection systems for early threat detection, especially against threat actors manipulating firewall configurations.
- Strictly limit the use of RDP and other remote desktop services, auditing network systems and enforcing account lockouts.
- Employ phishing-resistant multifactor authentication and log RDP login attempts to enhance security.
- Disable command-line and scripting activities, review user accounts and access controls, and implement time-based access for administrative accounts.
- Maintain offline backups of data, regularly updating and testing backup and restoration processes.
- Ensure compliance with NIST password policies, including longer passwords and secure password storage.
- Utilize multifactor authentication for all services, particularly for webmail, VPNs, and accounts accessing critical systems.
- Segment networks to prevent ransomware spread, control traffic flows, and restrict adversary lateral movement.
- Identify abnormal activity with network monitoring tools and implement endpoint detection and response (EDR) tools for detecting lateral connections.
- Install, update, and enable real-time detection for antivirus software on all hosts.
- Disable unused ports and protocols, consider adding email banners, and disable hyperlinks in received emails.
- Encrypt all backup data, ensure immutability, and cover the entire organization's data infrastructure.
How Avertium is Protecting Our Customers
It’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. Avertium can provide the following services to help keep your organization safe from Snatch Ransomware:
- Fusion MXDR is the first MDR offering that fuse together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.
- Expanding endpoints, cloud computing environments, and accelerated digital transformation have decimated the perimeter in an ever-expanding attack surface. Avertium offers Attack Surface Management, so you’ll have no more blind spots, weak links, or fire drills. See every threat in your attack surface, every device, every entry point, and every vulnerability. Our Attack Surface Management services include:
- Risk Assessments
- Pen Testing and Social Engineering
- Infrastructure Architecture and Integration
- Zero Trust Network Architecture
- Vulnerability Management
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
- Note: We highly value your feedback. Kindly spare a moment to complete our feedback form, allowing us to enhance our services for our valued customers.
Supporting Documentation
#StopRansomware: Phobos Ransomware | CISA
#StopRansomware: Phobos Ransomware (cisa.gov)
Phobos Ransomware Analysis, Simulation and Mitigation- CISA Alert AA24-060A (picussecurity.com)
A deep dive into Phobos ransomware | Malwarebytes Labs
Phobos Ransomware Targeting U.S. Government and Critical Infrastructure (pcmatic.com)
overview-phobos-ransomware.pdf (hhs.gov)
Critical Infrastructure Organizations Warned of Phobos Ransomware Attacks - SecurityWeek
FBI, CISA Release IoCs for Phobos Ransomware (darkreading.com)
Another Phobos Ransomware Variant Launches Attack – FAUST | FortiGuard Labs (fortinet.com)
A deep dive into Phobos ransomware, recently deployed by 8Base group (talosintelligence.com)
Phobos (Malware Family) (fraunhofer.de)
Understanding the Phobos affiliate structure and activity (talosintelligence.com)
CISA Warns Phobos Ransomware Groups Attacking Critical Infrastructure - Security Boulevard
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.