Roaming Mantis, an Evolving Phishing Campaign
Roaming Mantis was introduced in March 2018 after the Japanese media reported the hijacking of DNS settings on routers located in Japan. The hijackers were redirecting users to malicious IP addresses which then led to the installation of Trojanized applications (facebook.apk and chrome.apg) that contained an Android banking trojan. What started off as a banking trojan, has quickly evolved into much more. Let’s take a look at Roaming Mantis and how mobile phishing campaigns develop into cyber threats for organizations.
roman mantis (2018-2021)
Between February and April 2018, researchers at Kaspersky Lab detected the Roaming Mantis more than 6,000 times with reports coming from just 150 unique users. This information suggested a disturbing event for some users, who were experiencing the malware in their network over and over again. Kaspersky Lab observed that more than half of the detections were targeting the Asian region. Because of the propagation of the malware via smartphones roaming between Wi-Fi networks, carrying and spreading infections, Kaspersky Lab decided to call the malware Roaming Mantis. Compromised routers were used to infect Android tablets and smartphones.
Tactics & Techniques
DNS hijacking helps distribute Roaming Mantis. DNS hijacking is when a victim attempts to access a website by way of a compromised router and is immediately redirected to a malicious website. The malicious website typically displays a URL that appears to look like the one you’re trying to access, making you believe that it’s genuine. In Roaming Mantis’ case, when you go to the website, which is hosted on a rogue server, a popup message appears that asks you to update to the latest Chrome version for a better browsing experience.
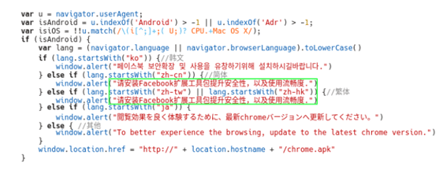
At this time, the number of target locales for the Roaming Mantis campaign is four: Korean, Simplified Chinese, Japanese and English (based on Android devices), with the HTML code containing an identical message in Traditional Chinese and Simplified Chinese. There were also several short code comments within the HTML code that were in Simplified Chinese.
Image 1: HTML Source for Roaming Mantis
When a device is booted via the internet, Roaming Mantis requests permission to be notified. After it receives the notification, it then gains access to account information, SMS/MMS and calls, audio records, external storage, etc.
Source: SecureList.com
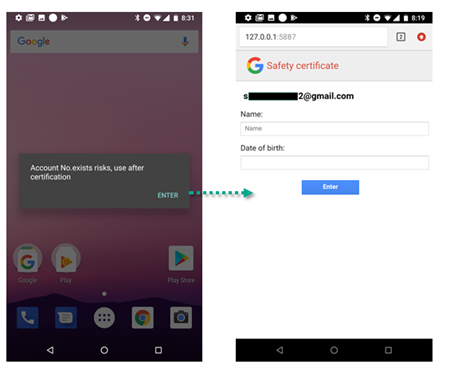
After Roaming Mantis is successfully installed, it overlays all other windows, with one carrying a message in broken English: “Account No.exists risks, use after certification”. Then, Roaming Mantis starts its own webserver, rendering a spoofed Google authentication page.
Image 2: Spoofing
This page was designed to trick victims into giving the threat actors behind Roaming Mantis access to their user accounts and eventually permission that grants access to the one-time codes needed for two-factor authentication. After analysis, Kaspersky Lab discovered that the malware contained references to application IDs that are popular in South Korea and linked to mobile banking and games.
Source: SecureList.com
One month after Kaspersky Lab published their report about the malware, Roaming Mantis added two dozen more languages to their attack list and improved the malware to attack devices running iOS. In 2018, Roaming Mantis’ ultimate goal was to steal user and take control over compromised Android devices. At the time, the malware was most prevalent in South Korea, as Korean was the first language targeted in HTML. The DNS hijacking makes it difficult for victims to detect that they are being attacked by cyber criminals.
See the list of languages Roaming Mantis added to their list in 2018:
|
Arabic |
Armenian |
Bulgarian |
Bengali |
Czech |
|
Georgian |
German |
Hebrew |
Hindi |
Indonesian |
|
Italian |
Malay |
Polish |
Portuguese |
Russian |
|
Sebo-Croat |
Spanish |
Tagalog |
Thai |
Turkish |
|
Vietnamese |
Ukrainian |
|
|
|
roaming mantis (2022)
Fast forward to 2022, Roaming Mantis has expanded and is now attacking in France and Germany for the first time. This time, the goal for Roaming Mantis is to install Wroba (a banking trojan), which is spyware and banking malware. Wroba is capable of replacing real apps with malicious versions so that bank credentials can be stolen and used by threat actors – financial motivation.
Additionally, Roaming Mantis has now shifted from using Java as a programming language, to using Kotlin. There are also two new backdoor commands, allowing Wroba to exfiltrate galleries and photos from compromised devices. Why would anyone want random photographs? Have you ever taken a picture of your driver’s license, insurance card, or debit card? Threat actors are willing to sift through massive amounts of images if it means they can receive just one pay day. They will also use stolen photos to blackmail their victims.
Tactics & Techniques
Roaming Mantis infects devices by sending a SMS text message to their victim. The language within the text tricks the victim into thinking that they are receiving a shipped package confirmation. They are then led to click on a URL, which redirects them to a phishing page designed to steal the victim’s credentials.
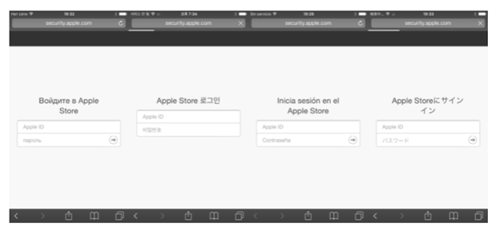
For iOS victims, the application isn’t downloaded. Instead, the malicious site displays a phishing page asking the victim to log back into the App Store immediately. The address that’s used looks like a credible Apple site and attempts to reassure the victim that all is well.
Image 3: Spoofed Apple Page
Source: Kaspersky.com
Not long after directing victims to the spoofed page, the threat actors ask for bank card numbers. If you are using a desktop computer or laptop, Roaming Mantis runs the CoinHive mining script, which mines cryptocurrency and distributes it directly to the attackers.
If you recall, our Threat Intelligence Report featuring Norton 360’s built-in cryptominer, stressed how cryptocurrency mining can cause your computer to run slow and use enormous amounts of power. Threat actors run cryptocurrency miners on hacked computers, so they don’t have to use their own resources – thus eventually destroying their victims’ devices.
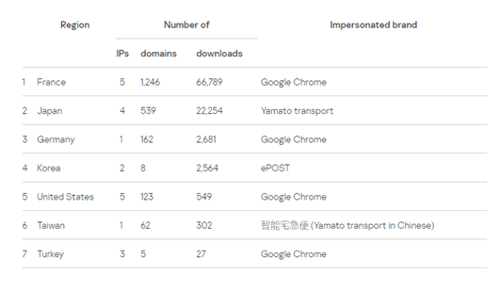
If an Android device is used, the victim will be redirected to a page that attempts to install malware disguised as an Android App. Here is a list of some of the apps used to deceive victims:
Image 4: Apps Roaming Mantis Impersonates
Source: Kaspersky Lab
To evade detection, Roaming Mantis threat actors use different obfuscation techniques in the landing page script. For example, the malware is now using a new method for retrieving the C2 by using the email POP protocol, as well as a command to assist in identifying research environments. Additionally, Roaming Mantis added a feature that avoids blacklisting – automatic generation of APK per download.
Right now, the malware appears to target France, Japan, India, China, Germany, and Korea. Researchers expect Roaming Mantis to continue in 2022 due to strong financial motivation. The threat actors behind the malware have used various malware families such as Heur: Trojan-Dropper.AndoidOSWroba. and other attack methods like smishing, phishing, and DNS attacks.
How Avertium is Protecting Our CUSTOMERS
Phishing campaigns like Roaming Mantis can create chaos for your organization’s cyber environment. As you can see, the malware began as a banking Trojan, but has evolved into much more and will continue to evolve. Roaming Mantis is the kind of threat that can easily penetrate your organization’s systems and networks via vulnerable employees. Every day unsuspecting employees receive text messages from threat actors pretending to be CEOs or stakeholders. Because the threat actors behind Roaming Mantis are financially motivated, it’s only a matter of time before Roaming Mantis makes its way into the U.S.
Don’t become overconfident and assume that an attack like Roaming Mantis won’t happen to you. Express the importance of being aware of phishing campaigns to your employees, especially during the onboarding process for new hires. Because people use their devices as their primary browsing source, it’s important to share this information with your employees. Keep your cyber environment secure by inquiring about the following Avertium services:
- Avertium offers Vulnerability Management to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium offers Zero Trust Architecture, like AppGate, to stop malware lateral movement.
- Avertium uses whitelisting tools like AppLocker to audit or block command-line interpreters.
- Avertium offers user awareness training through KnowBe4. The service also Incident Response Table-Top exercises (IR TTX) and Core Security Document development, as well as a comprehensive new-school approach that integrates baseline testing using mock attacks.
- Our partner, SentinelOne, offers Singularity Mobile as a way to combat mobile threats in real-time.
Avertium’s Recommendations
To help prevent an attack
- Install antivirus software on all devices – not just computer and laptops but smartphones and tablets as well.
- Consistently update software on all devices.
- If you have an Android device, disable the installation of applications from sources you don’t recognize via the settings feature.
- Beware of unofficial firmware downloaded from sketchy websites and update router firmware.
- Change the default administrator on the router.
If your organization is attacked by Roaming Mantis
- Change all passwords for compromised accounts and cancel all bank cards.
- Via router settings, check the DNS server address. If it doesn’t match the one given by your provider then you need to change it back to the correct address. You can do this by going to your ISP’s website from a safe system.
MITRE TTPS
- [T1598] Phishing for Information
- [T1566] Phishing
- [T1212] Exploitation for Credential Access
- [001] Phishing for Information: Spearphishing Service
- [003] Phishing for Information: Spearphishing Link
- [T1071] Application Layer Protocol
Indicators of Compromise (IoCs)
Roaming Mantis – 2022
- 0aaf6aa859fbdb84de20bf4bf28a02f1
- 19c4be7d5d8bf759771f35dec45f267a
- 2942ca2996a80ab807be08e7120c2556
- 4fbc28088b9bf82dcb3bf42fe1fc1f6d
- 527b5eebb6dbd3d0b777c714e707659c
- 5bafe0e5a96b1a0db291cf9d57aab0bc
- ddd131d7f0918ece86cc7a68cbacb37d
- 1ec6768018b2a78115156517bff03485264ff529
- c9f9c541920ca07912dd9686700dc86d5d1d2f57
- 1e41a9f204ed3bf567eb955f9dae119213cdf4fa3c6dacaa9bb21e95dace021f
- 30bdf42374a5bb6a83be08f9667e0a9395e411f911dab08d9c0814d30fb0e260
Roaming Mantis – 2018
- 44.37[.]112
- 166.1[.]124
- 168.193[.]123
- 14.50[.]146
- 14.50[.]147
- 136.111[.]66
- 136.179[.]5
- 136.76[.]200
- 240.14[.]44
- ddns[.]net
- hopto[.]org
- 03108e7f426416b0eaca9132f082d568
- 1cc88a79424091121a83d58b6886ea7a
- 2a1da7e17edaefc0468dbf25a0f60390
- 31e61e52d38f19cf3958df2239fba1a7
- 34efc3ebf51a6511c0d12cce7592db73
- 4d9a7e425f8c8b02d598ef0a0a776a58
- 808b186ddfa5e62ee882d5bdb94cc6e2
- 904b4d615c05952bcf58f35acadee5c1
- a21322b2416fce17a1877542d16929d5
- b84b0d5f128a8e0621733a6f3b412e19
- bd90279ad5c5a813bc34c06093665e55
- ff163a92f2622f2b8330a5730d3d636c
- 19e3daf40460aea22962d98de4bc32d2
- 36b2609a98aa39c730c2f5b49097d0ad
- 3ba4882dbf2dd6bd4fc0f54ec1373f4c
- 6cac4c9eda750a69e435c801a7ca7b8d
- 8a4ed9c4a66d7ccb3d155f85383ea3b3
- b43335b043212355619fd827b01be9a0
- b7afa4b2dafb57886fc47a1355824199
- f89214bfa4b4ac9000087e4253e7f754
- 1bd7815bece1b54b7728b8dd16f1d3a9
- 307d2780185ba2b8c5ad4c9256407504
- 3e4bff0e8ed962f3c420692a35d2e503
- 57abbe642b85fa00b1f76f62acad4d3b
- 6e1926d548ffac0f6cedfb4a4f49196e
- 7714321baf6a54b09baa6a777b9742ef
- 7aa46b4d67c3ab07caa53e8d8df3005c
- a0f88c77b183da227b9902968862c2b9
Supporting Documentation
Roaming Mantis uses DNS hijacking to infect Android smartphones | Securelist
Roaming Mantis infects smartphones through Wi-Fi routers | Kaspersky official blog
Roaming Mantis reaches Europe | Securelist
Roaming Mantis Swarms Globally, Spawning iOS Phishing, Cryptomining | Threatpost
Roaming Mantis SMSishing campaign now targets EuropeSecurity Affairs
'Roaming Mantis' Android Malware Targeting Europeans via Smishing Campaigns (thehackernews.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.
READ OUR LATEST BLOG >>> THE ART AND SCIENCE OF THREAT HUNTING - A GUIDE TO PREVENTING CYBER ATTACKS
Learn what threat hunting is, what it has gained so much popularity, how your business can benefit from its true value, and more.