The Double Extortion Group, 8Base
Executive Summary
Meet 8Base, a stealthy ransomware group that evaded detection for over a year, only to resurface with an alarming surge in operations during May and June 2023. Operating since 2022, 8Base's recent attacks have targeted 67 entities, with a focus on business services, manufacturing, and construction sectors in the U.S. and Brazil.
During June 2023, 8Base’s tactics escalated to double extortion, pressuring victims to pay a demanded ransom. Possibly linked to the infamous RansomHouse group, 8Base's origins remain unclear. Yet, their efficient operations and affinity for targeting smaller businesses raise serious cybersecurity concerns. Let’s explore 8Base ransomware and their potential impact on the digital landscape.
tir snapshot
- The primary focus of 8Base's attacks rest in targeting small and medium-sized businesses (SMBs) within the Professional, Scientific, Technical sector (36% of known attacks) and the Manufacturing sector (17%).
- In May 2023, the gang launched their data leak site, adopting the self-proclaimed identity of "honest and simple" pen testers.
- During June 2023, the 8Base ransomware operation saw a significant surge in activity, targeting multiple companies across diverse industries and employing a double extortion strategy.
- Their targets span various industries, yet critical information about their identities, methodology, and motivations remain a mystery.
- The speed and efficiency of 8Base's current operations suggest a continuation of a well-established and mature organization, rather than the emergence of a new group. After analysis, some aspects of their current operations resemble ransomware incidents witnessed in the past, specifically incidents pertaining to the group, RansomHouse.
- VMware's Carbon Black team has raised suspicions that 8Base might be a derivative of RansomHouse, due to similar ransom notes used by both groups, as well as the almost identical language and content observed on their respective leak sites.
- VMware's discoveries indicate that 8Base operators have been involved in encryption attacks for over a year, but it is only recently, with the launch of their data leak site, that they are gaining recognition. As 8Base is just starting to draw attention from analysts, many aspects of the group's technical workings still remain unknown.
- Security professionals must remain vigilant and proactive in implementing robust cybersecurity measures to safeguard their organizations against emerging threats like 8Base.
8baSE
8Base, a recently identified ransomware gang, has been active since either March or April 2022. The ransomware group gained attention in May after targeting a total of 67 victims. The primary focus of the group’s attacks rest in targeting small and medium-sized businesses (SMBs) within the Professional, Scientific, Technical sector (36% of known attacks) and the Manufacturing sector (17%). Geographically, the most targeted countries are the U.S. and Brazil, with a notable focus in America and Europe. Additional sectors impacted to a lesser extent include:
- Wholesale/Retail
- Construction
- Healthcare
- ICT
- Financial/Insurance
- Transportation/Storage
- Organizations
- Agriculture/Forestry/Fishing
- Education
- Gov/Mil/LE
- Other Services
Image 1: Impacted Countries
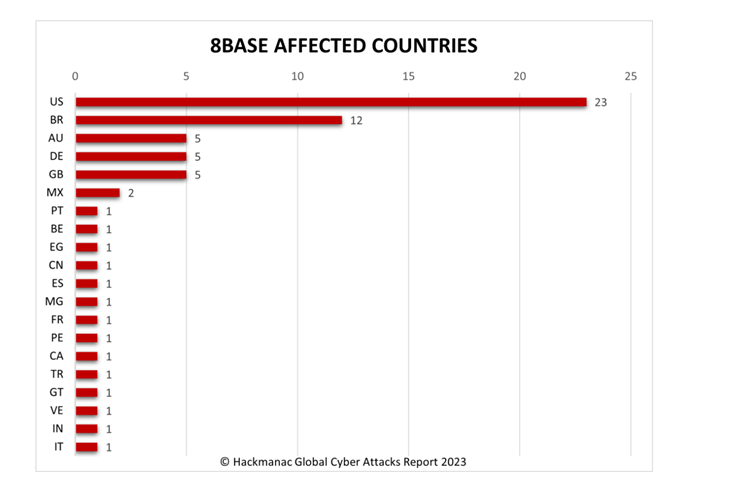
Source: Hackmanac
One of the group’s victims includes the Italian company SiComputer, which fell victim to an attack in March 2023, and had data published a month later. In May 2023, the gang launched their data leak site, adopting the self-proclaimed identity of "honest and simple" pentesters. On this site, they stated, "This list contains only those companies that have neglected the privacy and importance of the data of their employees and customers." However, 8BASE's Telegram channel presents differently.
Despite only creating the account on May 15th, the gang shared numerous posts featuring downloadable files containing what appears to be extensive sets of identifiable company records, employee IDs, driver's licenses, and passports from companies in South America, Panama, Australia, and the US. Among the alleged 8Base victims, there are at least half a dozen law offices and legal entities, along with those from the technology, agricultural, transportation, and financial sectors.
The latest victim appeared on the 8Base data leak site, on June 19th, is the Port Blue Hotel Group, a chain of exclusive hotels situated on the coast of Spain. The gang set a deadline of June 26th for the hotel group to pay an undisclosed ransom, or else their data would be exposed.
During June 2023, the 8Base ransomware operation saw a significant surge in activity, targeting multiple companies across diverse industries and employing a double extortion strategy. On its data leak site, 8Base listed 35 victims, with some instances of announcing up to six victims simultaneously. This increase stands in contrast to March and April when the group had only a few victims listed.
tactics and technques
CONNECTION TO RANSOMHOUSE
Despite a recent significant surge in activity, 8Base has managed to maintain a relatively low profile. Using a combination of encryption and "name-and-shame" techniques, the group coerces victims into paying ransoms. Their targets span various industries, yet critical information about their identities, methodology, and motivations remains a mystery.
The speed and efficiency of 8Base's current operations suggest a continuation of a well-established and mature organization, rather than the emergence of a new group. After analysis, some aspects of their current operations resemble ransomware incidents witnessed in the past, specifically incidents pertaining to the group, RansomHouse.
In January 2023, Avertium published a Threat Intelligence Report featuring RansomHouse and their attacks. At the time, the group was a new operation and focused on breaching networks via vulnerabilities to steal their targets’ data. Despite their name, RansomHouse is not a ransomware operation but a data-extortion cybercrime operation – just like 8Base. In contrast to conventional ransomware tactics involving encryption, RansomHouse adopts a different approach by omitting the encryption phase altogether. Instead, they directly demand payment for the stolen data. Recent findings have revealed that while RansomHouse may not present itself as a ransomware group, they are associated with ransomware operations, engaging in the sale of stolen data.
Also, RansomHouse has been observed utilizing ransomware in their attacks, including White Rabbit and MARIO, both of which are linked to the cybercrime group FIN8. Additionally, the group does not accept responsibility for their attacks, instead they shift the blame towards the victim organizations, attributing the incidents to their supposed lack of robust security measures.
VMware's Carbon Black team has raised suspicions that 8Base might be a derivative of RansomHouse, due to similar ransom notes used by both groups, as well as the almost identical language and content observed on their respective leak sites. The groups even have the same FAQ pages. Despite high suspicions, the available evidence is insufficient to determine whether 8Base emerged from RansomHouse members or if it is merely another ransomware operation replicating templates from an established group, a practice not uncommon among threat actors. Also, when contrasting the two threat groups, there are only two significant distinctions: RansomHouse actively promotes its partnerships and openly recruits for collaborations, whereas 8Base does not. 8Base could be an offshoot brand or simply a copycat of RansomHouse.
Image 2: 8Base (Left) and RansomHouse (Right) Ransomware Notes

Source: VMware
8BASE TACTICS AND TECHNIQUES
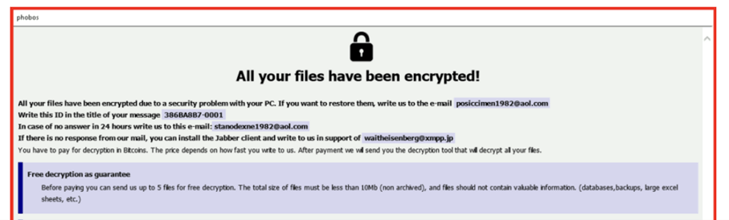
While investigating, researchers uncovered a Phobos ransomware sample using a ".8base" file extension on encrypted files. This raises questions about whether it was an earlier version of their ransomware or if 8Base uses different ransomware variants to target victims. A comparison of Phobos and the 8Base sample revealed that 8Base was utilizing Phobos ransomware version 2.9.1 with SmokeLoader for initial obfuscation on ingress, unpacking, and loading of the ransomware.
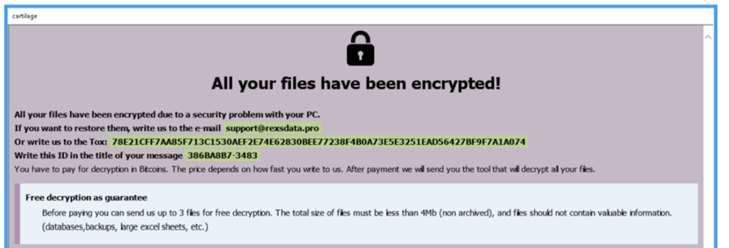
Since Phobos ransomware is available as ransomware-as-a-service (RAAS), the customization of certain parts, as evident in the 8Base ransom note, is not surprising. Although their ransom notes shared similarities, key differences included Jabber instructions and the presence of "phobos" in the top and bottom corners for Phobos ransomware, while 8Base used "cartilage" in the top corner, a purple background, and omitted Jabber instructions.
Image 3: Phobos and Jabber Instructions
Also, VMware’s investigation of an 8Base sample obtained from the domain admlogs25[.]xyz, appeared to have links to SystemBC, a proxy and remote administration tool. Other ransomware groups have previously utilized SystemBC to encrypt and obfuscate the destination of their Command-and-Control (C2) traffic.
VMware’s discoveries indicate that 8Base operators have been involved in encryption attacks for over a year, but it is only recently, with the launch of their data leak site, that they are gaining recognition. As 8Base is just starting to draw attention from analysts, many aspects of the group’s technical workings still remain unknown.
In conclusion, security professionals must remain vigilant and proactive in implementing robust cybersecurity measures to safeguard their organizations against emerging threats like 8Base. Understanding the group's tactics, target sectors, and potential associations with other threat actors can aid in developing effective defense strategies and incident response plans to mitigate risks posed by ransomware attacks.
mitre map
persistence |
discovery |
privilege escalation |
defense evasion |
impact |
| T1547.001: Registry Run Keys/Startup Folder | T1135: Network Share Discovery | T1134.001: Token Impersonation/Theft | T1562.001: Disable or Modify Tools | T1490: Inhibit System Recovery |
| T1027.002: Obfuscated File or Information: Software Packing | T1486: Data Encrypted for Impact |
avertium's recommendations
As long as data extortion remains feasible and not too challenging for threat actors, it will persist as a significant cyber threat. Although some may underestimate threat groups like 8Base due to their less sophisticated tactics, any disruption to an organization's operations can lead to severe consequences.
While data backups are essential, they alone may not be sufficient to protect your organization from losing valuable data. 8Base’s focus on data exfiltration instead of file encryption highlights the need to prioritize cyber security best practices and prevent unauthorized access to your systems and networks. Concentrating on fortifying your cyber environment against intruders from the outset provides greater leverage against data extortion groups. Implementing an intrusion prevention system (IPS) as a cyber security best practice can significantly enhance your organization's safety and resilience.
How Avertium is Protecting Our Customers
It’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. Avertium can provide the following services to help keep your organization safe from threat actors like 8Base:
- Fusion MXDR is the first MDR offering that fuse together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.
- Avertium offers Vulnerability Management (VM) to provide a deeper understanding and control over organizational information security risks. If your enterprise is facing challenges with the scope, resources, or skills required to implement a vulnerability management program with your team, outsourced solutions can help you bridge the gap.
- Avertium aligns your Cybersecurity Strategy with your business strategy, ensuring that your investment in security is also an investment in your business. Our Cybersecurity Strategy service includes:
- Strategic Security Assessments - Strengthening your security posture begins with knowing where your current program stands (NIST CSF, Security Architecture, Business Impact Analysis, Sensitive Data Inventory, Network Virtualization and Cloud Assessment).
- Threat Mapping – Leverage Avertium’s Cyber Threat Intelligence, getting a more informed view of your most likely attack scenarios (Threat Assessment and MITRE ATT&CK).
- Cyber Maturity Roadmap - Embrace a comprehensive, quantifiable, and well-organized approach to establishing and continuously enhancing your cybersecurity resilience (Policy + Procedure Development, Virtual CISO (VCISO), Training + Enablement, Tabletop Exercises, and Business Continuity + Disaster Recovery Plan).
indicators of compromise
- SHA-256
- 518544e56e8ccee401ffa1b0a01a10ce23e49ec21ec441c6c7c3951b01c1b19c
- 5BA74A5693F4810A8EB9B9EEB1D69D943CF5BBC46F319A32802C23C7654194B0
- e142f4e8eb3fb4323fb377138f53db66e3e6ec9e82930f4b23dd91a5f7bd45d0
- 5d0f447f4ccc89d7d79c0565372195240cdfa25f
- C6BD5B8E14551EB899BBE4DECB6942581D28B2A42B159146BBC28316E6E14A64
- 518544E56E8CCEE401FFA1B0A01A10CE23E49EC21EC441C6C7C3951B01C1B19C
- AFDDEC37CDC1D196A1136E2252E925C0DCFE587963069D78775E0F174AE9CFE3
- MD5
- 20110FF550A2290C5992A5BB6BB44056
- 9769c181ecef69544bbb2f974b8c0e10
- URLs
- wlaexfpxrs[.]org
- admhexlogs25[.]xyz
- admlogs25[.]xyz
- admlog2[.]xyz
- dnm777[.]xyz
- serverlogs37[.]xyz
- dexblog[.]xyz
- blogstat355[.]xyz
- blogstatserv25[.]xyz
- File Name
- 3c1e.exe
- d6ff.exe
- 9f1a.exe
Supporting Documentation
8Base Ransomware: A Heavy Hitting Player - VMware Security Blog - VMware
New ransomware gang 8BASE behind surge of May attacks | Cybernews
8Base ransomware group leaks data of 67 victim organizations - Help Net Security
8Base Ransomware Activity Spikes, Researcher Warn | Cyware Alerts - Hacker News
8Base ransomware gang escalates double extortion attacks in June (bleepingcomputer.com)
NCC Group Monthly Threat Pulse – May 2023 | NCC Group Newsroom (mynewsdesk.com)
Ransomware review: June 2023 (malwarebytes.com)
8BASE, THE NEWLY DISCOVERED RANSOMWARE GANG - Hackmanac
Everything You Need to Know About the Data Extortion Group, RansomHouse (avertium.com)
Emerging Ransomware Group 8Base Doxxes SMBs Globally (darkreading.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.