Unraveling Scattered Spider: A Stealthy and Persistent Threat Actor Targeting Telecom Networks
Executive Summary
Scattered Spider, or UNC3944, is a financially motivated threat actor known for its clever use of social engineering tactics to infiltrate target devices. They are persistent, stealthy, and swift in their operations. Once inside, Scattered Spider avoids specialized malware and instead relies on reliable remote management tools to maintain access.
In December 2022, CrowdStrike uncovered a concerning campaign by Scattered Spider, targeting the telecom and business process outsourcing sectors to gain entry into mobile carrier networks. Since then, their activities have continued, and they even attempted to exploit an old malicious kernel driver vulnerability (CVE-2015-2291) in the Intel Ethernet diagnostics driver of a targeted system. Let’s explore Scattered Spider's tactics and techniques while highlighting essential security controls and detections.
tir snapshot
- In December 2022, Scattered Spider's focus was on organizations in the telecom and business process outsourcing (BPO) sectors, with the ultimate goal of infiltrating mobile carrier networks.
- The primary objective of their December 2022 campaign was to breach telecom network systems, gain access to subscriber information, and perform operations like SIM swapping.
- Initial access by the Scattered Spider is achieved through social engineering tactics. They use methods like phone calls, SMS, or Telegram to impersonate IT staff.
- In cases where Multi-Factor Authentication (MFA) was enabled, Scattered Spider used various techniques. They would directly engage the victim and convince them to share their one-time password (OTP).
- In a separate investigation conducted by CrowdStrike, Scattered Spider utilized compromised credentials obtained from a victim user to gain unauthorized access to the organization's Azure tenant.
- Scattered Spider has also focused on VMware ESXi hypervisors. In one case observed by CrowdStrike, they installed two specific tools, namely, the open-source rsocx reverse proxy and the Level remote monitoring and management (RMM) tool, on an ESXi appliance.
- Scattered Spider targets environments that are widely used by various industries and sectors, including Windows, Linux, Google Workspace, AzureAD, M365, and AWS.
- In 2021, Microsoft warned that adversaries were increasingly using legitimate drivers and their security vulnerabilities to execute malware.
- By January 2023, CrowdStrike observed Scattered Spider attempting to deploy a Bring Your Own Vulnerable Driver (BYOVD) attack via an old kernel vulnerability (CVE-2015-2291), leveraging vulnerable third-party drivers as a way to evade detection by EDR.
- BYOVD poses risks for organizations as it allows threat actors to exploit known vulnerabilities in third-party drivers, leading to system compromises, financial losses, and operational disruptions.
scattered spider
As previously mentioned, in December of 2022, CrowdStrike released a report detailing a targeted campaign orchestrated by Scattered Spider. Their focus was on organizations in the telecom and business process outsourcing (BPO) sectors, with the ultimate goal of infiltrating mobile carrier networks. Scattered Spider attacks have surged significantly, with a focus on nations like the United States, the United Kingdom, Germany, France, Italy, Canada, Australia, and Japan.
Starting in June 2022 and extending through the winter months, security researchers identified a total of five intrusions carried out by the attackers. The primary objective of their December 2022 campaign was to breach telecom network systems, gain access to subscriber information, and perform operations like SIM swapping. During that time, the threat actor successfully utilized CVE-2021-35464, a vulnerability in the ForgeRock AM server, to execute code and elevate their privileges over the Apache Tomcat user on an AWS instance. They achieved this by acquiring and leveraging the permissions of an instance role through a compromised AWS token.
Image 1: Five Intrusions
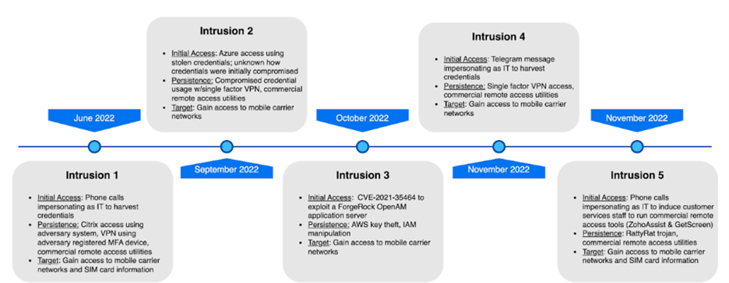
Source: Crowdstrike
tactics and technques
In the majority of investigations conducted by CrowdStrike, the initial access by the Scattered Spider was achieved through social engineering tactics. They used methods like phone calls, SMS, or Telegram to impersonate IT staff. The victims were then directed to either visit a fake website with the company logo, where they were tricked into entering their credentials, or to download a Remote Monitoring and Management (RMM) tool that would give the threat actor remote control over their system.
In cases where Multi-Factor Authentication (MFA) was enabled, the Scattered Spider used various techniques. They would directly engage the victim and convince them to share their one-time password (OTP). Also, the threat actor used a method called "MFA push-notification fatigue," repeatedly sending MFA challenges to the victim until they eventually accepted the prompt.
In a separate investigation conducted by CrowdStrike, Scattered Spider utilized compromised credentials obtained from a victim user to gain unauthorized access to the organization's Azure tenant. Once inside, they created Azure Virtual Machines (VMs) to carry out activities involving credential theft and lateral movement towards on-premises systems. Once the threat actors gain access to a system, they try to add their own devices to the list of trusted MFA devices using the compromised user account. Scattered Spider uses the following utilities and remote monitoring and management tools to maintain persistent access:
- AnyDesk
- BeAnywhere
- Domotz
- DWservice
- Fixme.it
- Fleetdeck.io
- Itarian Endpoint Manager
- Level.io
- Logmein
- ManageEngine
- N-Able
- Pulseway
- Rport
- Rsocx
- ScreenConnect
- SSH RevShell and RDP Tunnelling via SSH
- Teamviewer
- TrendMicro Basecamp
- Sorillus
- ZeroTier
Because the above tools are not malicious, they evade generating alerts and are not commonly blocked by endpoint detection and response (EDR) technology.
NAMING PATTERNS
A recurring strategy observed is Scattered Spider’s use of a standard naming pattern, such as "DESKTOP-<7 alphanumeric characters>," when connecting their own systems to the victim organization's VPNs. Additionally, when setting up systems within the victim’s virtual desktop infrastructure, the threat actor imitated the organization's established naming conventions.
Also, Scattered Spider has focused on VMware ESXi hypervisors. In one case observed by CrowdStrike, they installed two specific tools, namely, the open-source rsocx reverse proxy and the Level remote monitoring and management (RMM) tool, on an ESXi appliance. In different instance, the threat actor used the open-source port scanner tool RustScan, executing it from a Docker container that was active on an ESXi appliance.
TARGETING WIDELY USED ENVIRONMENTS
Scattered Spider targets environments that are widely used by various industries and sectors, including Windows, Linux, Google Workspace, AzureAD, M365, and AWS. They gather information from SharePoint and OneDrive, seeking details like VPN and MFA information, guides, and help desk instructions.
In one case, they accessed Azure Active Directory and obtained user data, including privileged users. Scattered Spider uses different tactics like domain replication, WMI lateral movement, SSH tunneling, and remote access tools during investigations. They also download tools from websites like file[.]io, GitHub, and paste[.]ee using victim organization systems. As for exfiltrating data, they utilize the site transfer[.]sh.
A NEW TACTIC - BYOVD
By January 2023, CrowdStrike observed Scattered Spider attempting to deploy a Bring Your Own Vulnerable Driver (BYOVD) attack via an old kernel vulnerability (CVE-2015-2291), leveraging vulnerable third-party drivers as a way to evade detection by EDR. The BYOVD technique is when threat actors incorporate a kernel-mode driver with known vulnerabilities into their attacks to elevate privileges in Windows and exploit the system further. CVE-2015-2291 was fixed in 2015, but Scattered Spider may still be able to exploit it by placing an older version on compromised devices.
Device drivers have kernel access to the operating system. Because attackers exploit flaws in these drivers, this new tactic could allow Scattered Spider to run code with the highest privileges in Windows. Scattered Spider tried to use the BYOVD technique to evade Microsoft Defender for Endpoint, Palo Alto Networks Cortex XDR, and SentinelOne.
In 2021, Microsoft warned that adversaries were increasingly using legitimate drivers and their security vulnerabilities to execute malware. To counter this, Microsoft planned to block drivers with confirmed security flaws on Windows 10 devices using their Defender for Endpoint attack surface reduction (ASR) and Windows Defender Application Control (WDAC) technologies. This measure aimed to protect devices from exploits involving vulnerable drivers attempting to gain access to the kernel. Despite being highlighted by numerous security researchers in the past two years, the problem persists because Microsoft does not block vulnerable drivers by default.
During investigation, CrowdStrike discovered several versions of a malicious driver, each signed by different certificates and authorities. Some certificates were stolen from NVIDIA and Global Software LLC, while others were self-signed as test certificates. The purpose of these actions is to disable the visibility and prevention capabilities of endpoint security products, enabling the threat actor to proceed without being detected. These driver samples are compact, 64-bit Windows kernel drivers, containing fewer than 35 functions.
Image 2: Example Driver with SHA256 Hash
![]()
Source: Crowdstrike
The sample driver's build time is set to January 1, 1970, at 00:01:35 UTC. It contains various status messages and calls to DbgPrintEx() to provide updates to the threat actor. The file is signed with a certificate issued to "Global Software, LLC" and has the following parameters:
- Serial number: 31 11 00 fb 8d ee 5e 09 37 6b 69 a8 f6 23 e0 ee
- Validity: From May 14, 2018, to June 18, 2021
Interestingly, this same certificate has been used to sign other malicious files since at least 2018, indicating that other threat actors may also possess copies of it.
other byovd attacks
In October 2022, two alarming incidents shed light on the dangers of Bring Your Own Vulnerable Device (BYOVD) attacks, highlighting the potential threats organizations face. Firstly, the BlackByte ransomware group utilized the CVE-2019-16098 vulnerability in Micro-Star's MSI AfterBurner 4.6.2.15658 to disable over 1,000 drivers, causing widespread disruption and damage.
Secondly, during the same month, the North-Korean state-sponsored APT Lazarus executed sophisticated spear-phishing campaigns targeting Belgium and the Netherlands. These campaigns strategically employed the BYOVD technique, exploiting the CVE-2021-21551 vulnerability in Dell's dbutil hardware driver.
Such attacks, exploiting known vulnerabilities in third-party drivers, exemplify the risks that BYOVD poses for organizations, allowing threat actors to compromise systems, inflict financial losses, and disrupt critical operations. It underscores the urgent need for organizations to bolster their defense mechanisms and implement robust security measures to mitigate these evolving threats.
mitre map
initial access |
execution |
defense evasion |
collection |
command and control |
| T1190: Exploit Public Facing Application | T1053: Scheduled Task/Job | T1106: Native API | T1056: Input Capture | T113: External Remote Services |
| T1059: Command and Scripting Interpreter | T1564: Hide Artifact | T1115: Clipboard Data |
avertium's recommendations
Please Note: The subsequent guidelines are based on CrowdStrike's comprehensive list of security controls, and we strongly advise their implementation.
MFA
- Layered MFA adds a phone call or text message to password-based authentication. Layered MFA may deter attacks, but attacks can still use MFA fatigue to penetrate those defenses. Modern, passwordless authentication methods such as Windows Hello, FIDO, or Microsoft Authenticator will effectively defend against MFA fatigue and advanced adversary-in-the-middle attacks.
- Avoid unsupervised MFA self-enrollment or reset and disallow any self-enrollment from external IP space.
- Allow only one trusted MFA device per user.
- Implement a global password reset and KRBTGT account reset twice per domain if compromise is suspected.
Monitoring
- Utilize custom rules and queries to identify compromised or vulnerable accounts and credentials, enhancing the ability to spot potential threats.
- Regularly review and monitor the health of Active Directory, paying attention to newly created accounts, changes to group memberships, and re-enabled accounts.
- Make use of the Protected Users Security Group in Active Directory to protect privileged accounts from NTLM (NT LAN Manager) usage, reducing security risks.
- Enable real-time alerting mechanisms to promptly detect and respond to known compromised credentials, enhancing the organization's security posture.
- Set up custom indicators of attack (IOAs) to configure alerts and blocks for any unauthorized or abnormal Remote Monitoring and Management (RMM) tools. This step is crucial since threat actors have demonstrated the use of a diverse range of RMM tools in their activities during previous investigations.
AWS Token Pivoting
- Ensure IMDSv2 is enabled on all EC2 instances to the extent possible (Note: Some products might still lack support for v2).
- Enable GuardDuty in all active regions (GuardDuty includes detections for abuse of EC2 instance credentials beyond an EC2 instance).
- Deprecate static IAM user access keys where applicable, favoring IAM roles instead.
CVE-2015-2291
- Even though activity surrounding CVE-2015-2291 seems to be targeting specific industries, all organizations should harden their defenses against the vulnerability.
- It is recommended that organizations conduct system scans to identify the targeted Intel driver and ensure that it has been updated to address CVE-2015-2291.
- Additionally, organizations should promptly apply patches to address all known vulnerabilities on their systems and implement an endpoint security solution across all devices.
Enforce Azure Conditional Access Policies (CAP):
- Block legacy authentication.
- Restrict logon by geographic region.
- Enforce multifactor authentication for all users.
- Enforce compliant devices.
How Avertium is Protecting Our Customers
- Avertium’s Capability Management Team is researching and considering the implementation of several SIEM detections for activity related to Scattered Spider:
- Please Note: These detections could have a high volume of false positives and are not a replacement for a proper security policy.
- We take pride in informing you that all our detections stem from our esteemed partner, SnapAttack. Just like Avertium, SnapAttack shares the mission to bring order to security operations amidst chaos. With a hacker mindset, SnapAttack combats cyber threats, offering you peace of mind and a secure environment.
- Please Note: These detections could have a high volume of false positives and are not a replacement for a proper security policy.
|
Script Executed on EC2 Instance |
Detects usage of the SendCommand api call to a managed instance |
|
Terminal Spawned via Special Administration Console |
Detects a terminal process spawned by the Special Administration Console. |
|
AWS STS AssumeRole Misuse |
Detects suspicious use of AssumeRole. |
- Fusion MXDR for Microsoft combines Avertium's Fusion MXDR approach with Microsoft Security Solutions, creating the first MDR offering that integrates all aspects of security operations into an active and threat-informed XDR solution. Leveraging Microsoft's comprehensive and cost-effective technology, Fusion MXDR for Microsoft delivers a release of cyber energy, encompassing implementation, optimization, ongoing management, and tuning.
- Avertium simplifies Governance, Risk, and Compliance (GRC) by providing contextual understanding instead of unnecessary complexity. With our cross-data, cross-industry, and cross-functional expertise, we enable you to meet regulatory requirements and demonstrate a robust security posture without any vulnerabilities. Our GRC services include:
- Cyber Maturity
- Compliance Assessments and Consulting
- Managed GRC
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
indicators of compromise
FileHash MD5
- 1e5ad5c2ffffac9d3ab7d179566a7844
- 56fd7145224989b92494a32e8fc6f6b6
- 6639433341fd787762826b2f5a9cb202
- 828699b4133acb69d34216dcd0a8376e
- f5271a6d909091527ed9f30eafa0ded6
FileHash SHA1
- 0272b018518fef86767b01a73213716708acbb80
- 10b9da621a7f38a02fea26256db60364d600df85
- 9ec4c38394ea2048ca81d48b1bd66de48d8bd4e8
- d8cb0d5bbeb20e08df8d2e75d7f4e326961f1bf5
- ec37d483c3c880fadc8d048c05777a91654e41d3
FileHash SHA256
- 3ea2d190879c8933363b222c686009b81ba8af9eb6ae3696d2f420e187467f08
- 4188736108d2b73b57f63c0b327fb5119f82e94ff2d6cd51e9ad92093023ec93
- 443dc750c35afc136bfea6db9b5ccbdb6adb63d3585533c0cf55271eddf29f58
- 53b7d5769d87ce6946efcba00805ddce65714a0d8045aeee532db4542c958b9f
- 648c2067ef3d59eb94b54c43e798707b030e0383b3651bcc6840dae41808d3a9
- 982dda5eec52dd54ff6b0b04fd9ba8f4c566534b78f6a46dada624af0316044e
- acadf15ec363fe3cc373091cbe879e64f935139363a8e8df18fd9e59317cc918
- cce5e2ccb9836e780c6aa075ef8c0aeb8fec61f21bbef9e01bdee025d2892005
IPv4
- 45.132.227.213
- 119.93.5.239
- 146.70.103.228
- 144.76.136.153
- 67.43.235.122
- 82.180.146.31
- 91.242.237.100
- 89.46.114.164
- 98.100.141.70
- 62.182.98.170
Note: A complete list of IoCs related to Scattered Spider can be found here.
Supporting Documentation
Scattered Spider IOCs – OccamSec
Analysis of an Intrusion Campaign Targeting Telco and BPO Companies (crowdstrike.com)
Threat Group UNC3944 Abusing Azure Serial Console for Total VM Takeover (thehackernews.com)
Scattered Spider Attempts BYOVD Attack | Cyware Alerts - Hacker News
Scattered Spider hackers use old Intel driver to bypass security (bleepingcomputer.com)
SCATTERED SPIDER Attempts to Avoid Detection with Bring-Your-Own-Driver Tactic (crowdstrike.com)
Sneaky hackers reverse defense mitigations when detected (bleepingcomputer.com)
Squashing SCATTERED SPIDER's Attacks in the Cloud | Threat SnapShot - YouTube
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.