- ABOUT
-
-
About Us
Security. It’s in our DNA. It’s elemental, foundational. Something that an always-on, everything’s-IoT-connected world depends on.
Helping mid-to-enterprise organizations protect assets and manage risk is our only business. Our mission is to make our customers’ world a safer place so that they may thrive in an always-on, connected world.
-
Latest Avertium News
How Gartner's 2024 Cybersecurity Trends Can Guide Your Cyber EffortsGartner has identified its six top cybersecurity trends for the year, and they’re ones that healthcare leaders should consider. Of the six trends, here are the ones that Avertium finds most instructive and beneficial.
-
-
- SOLUTIONS
-
-
Governance, Risk & Compliance
GRC with context – not complexity. -
Attack Surface Management
No more blind spots, weak links, or fire drills. -
Managed XDR & SecOps
Detect, adapt, and attack with context. -
Microsoft Security Solutions
End-to-end support from strategy to daily operations to maximize your Microsoft Security.
-
-
- PARTNERS
-
-
Our Partners
Best-in-class technology from our partners... backed by service excellence from Avertium.
-
Partner Opportunity Registration
Interested in becoming a partner?
With Avertium's deal registration, partners can efficiently and confidently connect with Avertium on opportunities to protect your deals.
-
Latest Avertium Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- NEWS & RESOURCES
-
-
News & Resources
Dive into our resource hub and explore top
cybersecurity topics along with what we do
and what we can do for you. -
Latest Resource
Harnessing Copilot for Security: A Strategic Approach to Healthcare Cyber DefenseMicrosoft Copilot for Security analyzes and synthesizes high volumes of security data which can help healthcare cybersecurity teams do more with less.
-
-
- CONTACT
CYBERSECURITY STRATEGY
Take your cybersecurity strategy to the next level.
Avertium puts your cybersecurity strategy in the context of your business strategy, so your security investment is an investment in your business.
how we help
Cybersecurity Strategy Services
STRATEGIC SECURITY ASSESSMENTS
Get a comprehensive view of your
risk surface.
THREAT MAPPING
Attack the problems before they
attack you.
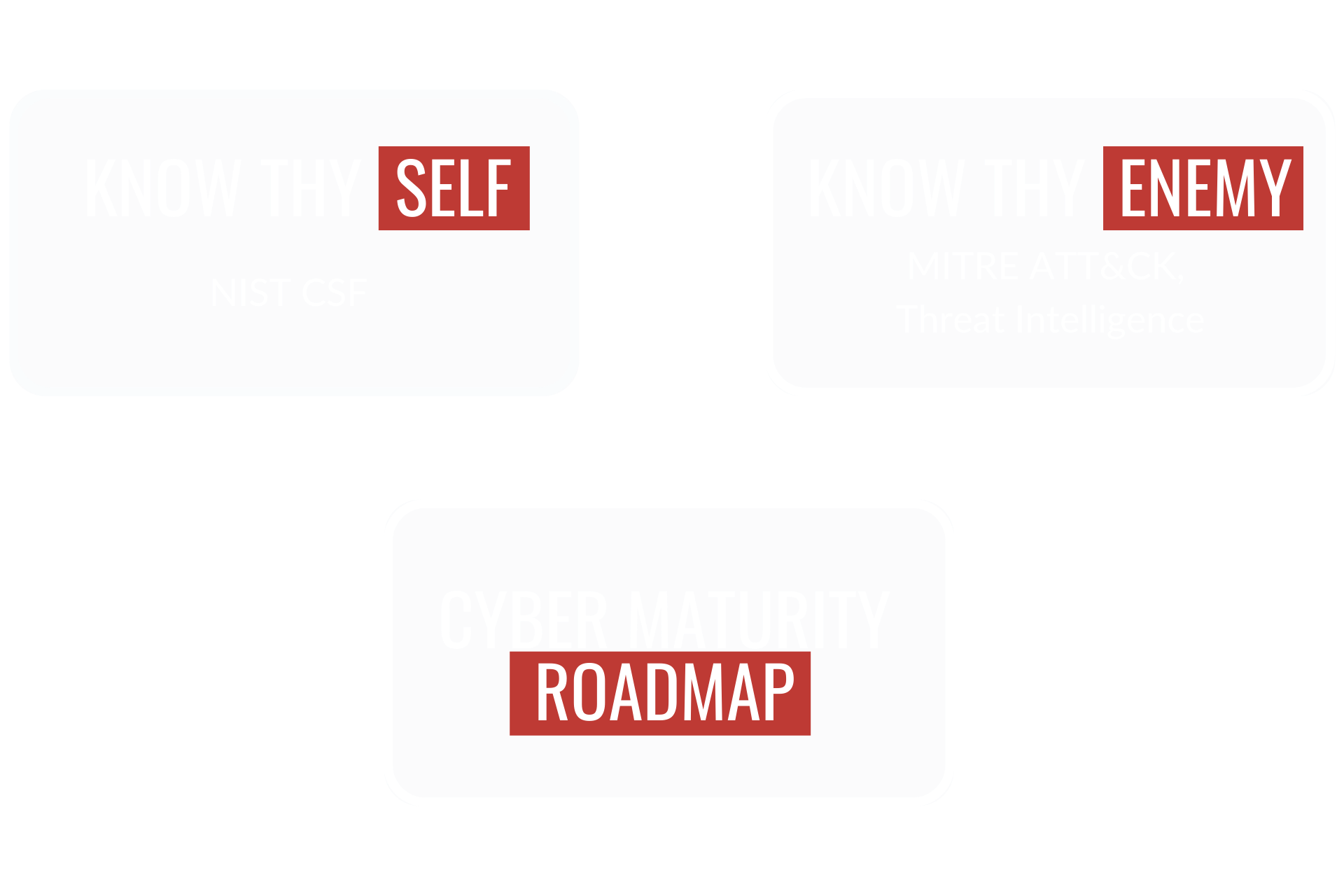
cyber maturity ROADMAP
Build a security program that endures and evolves alongside the threat landscape
To win the cyber war you must know yourself, know your enemy, and know what it takes to adapt, attack, and evolve with the chaos of today’s threat landscape.
-2.png?width=1920&height=1280&name=Cyber%20Fusion%20Engine%20Graphic%20(1)-2.png)
threat mapping
Leverage cyber threat intelligence (CTI) to get a more informed view of your most likely attack scenarios.
Threat Assessment
MITRE ATT&CK
cyber maturity roadmap
Take a more holistic, more measurable, and more structured approach to building and continuously improving your cybersecurity resilience.
Cyber Maturity Roadmap
Policy + Procedure Development
Virtual CISO (VCISO)
Training + Enablement
Tabletop Exercises
Business Continuity + Disaster Recovery Plan
They always advise us in the direction of a strong balance...
"It's been outstanding working with Avertium... I trust implicitly the leadership and the quality of resources that are brought to the table. They always advise us in the direction of a strong balance between how you mitigate risk and how you also keep the business going."
Avertium Customer
Avertium is flexible across the entire continuum...
"They can do everything from managing and monitoring my network from a security standpoint all the way to order and presentations. That’s one thing I’ve truly appreciated - Avertium has those levels of skills and they can be flexible across that entire continuum."
Avertium Customer
It's like working with your best friend!
"Avertium has been a critical part of our success as a company for the better part of 5 years now. Everybody from project and account management to the soc engineers are great, knowledgeable people to work with. Avertium provides a small town "family" feel that makes the working relationship smooth and effective."
Security & Risk Management | Avertium Customer
Our Approach
The cyber war is waged on many fronts. Winning the battle requires you to know yourself… winning the war requires you to know yourself AND your enemy . Show no weakness.


