
Case Study:
INTERNOVA TRAVEL GROUP
Discover how Avertium helps unburden Internova Travel Group's security team to have the space to start focusing on more strategic cybersecurity priorities.
In 2023, ransomware was the focus for many organizations. While ransomware is still a major concern, other threats such as botnets are beginning to draw attention. For some time, the leading force behind the most significant distributed denial of service (DDoS) botnet attacks has been Internet of Things (IoT) devices. This is a threat that won’t go away, as many IoT device manufacturers still release products that cannot be properly secured.
In 2022, we saw the Kraken botnet steal data from Windows hosts. We also saw the Emotet botnet return using TrickBot to install malware on infected Windows systems, attacking several organizations within the finance and education sectors. This year, researchers say that the era of botnets has arrived, as new threats and attack techniques emerge. [1]Microsoft reported seeing a growing trend in which DDoS attacks are being utilized to divert attention and mask more sophisticated attacks happening at the same time, such as data theft and extortion.
Due to the growing concern, organizations need to take action to protect their networks and data from botnets, however, before doing so, they need to understand the threats they face. Recently, the Mirai and HinataBot botnets have been the focus of discussion among security professionals. Let's explore the inner workings of both botnets to understand why.
[1] 2022 in review: DDoS attack trends and insights - Microsoft Security Blog
In September 2016, the creators of the Mirai malware launched a DDoS attack on the website of renowned security expert, Brian Krebs. Seven days later, they made the source code available to the public, in an effort to hide the source of the attack. The source code was immediately replicated by other cybercriminals and is thought to be the cause of the massive attack that caused the domain registration services provider, Dyn, to crash in October 2016. These high-profile attacks quickly earned Mirai notoriety.
|
Botnets are a collection of hijacked computer devices that are connected to form a network. This network is used to conduct various cybercrimes, such as data theft, server crashing, and malware distribution. The term “botnet” comes from the words “robot” and “network” and is typically the first step in a multi-stage attack. The bots are used to automate the process of carrying out malicious activities. |
Mirai works by scanning the internet for IoT devices running a simplified version of Linux on ARC processors. Mirai uses a dictionary attack of default usernames and passwords to gain access to devices that have not had their credentials updated. What’s interesting about Mirai’s 2016 attacks is that they were executed through IoT devices such as home routers, personal surveillance cameras, and air-quality control monitors. At the botnet’s peak, Mirai infected over 600,000 IoT devices.
Image 1: Mirai Attack Timeline
Source: CloudFlare
Once a device has been infected Mirai acts as a self-propagating malicious worm and continues to spread by scanning for and infecting other vulnerable IoT devices. The two main components of Mirai are a replication module and an attack module. Mirai initially compromised devices by brute-forcing a fixed set of 64 default login/password combinations that were commonly used by IoT devices. This low-tech attack was highly successful.
After Mirai’s source code was leaked, researchers at Imperva created a strong signature to identify Mirai’s activity on their network. After examining their logs, they found that the botnet was the source of several GRE floods that their service was able to contain. The attack was conducted with a hit-and-run approach, and the peak of the attack was 280 Gbps and 130 Mpps, which is a sign of a very powerful botnet.
The researchers also found that 49,657 distinct IP addresses hosted Mirai infected devices. The devices were primarily CCTV cameras – a popular choice of DDoS botnet herders. Other affected devices included DVRs and routers. The IP addresses were located in 164 countries and were highly dispersed, appearing in remote locations such as Somalia and Tajikistan.
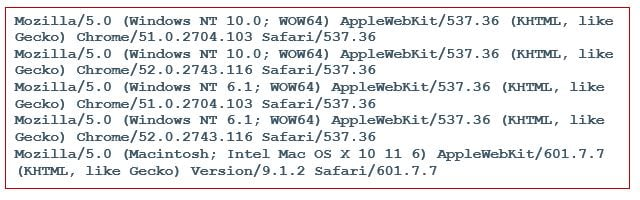
According to Imperva, Mirai’s command and control (C2) code is written in Golang, while its bots are written in C language. Mirai's attack function allows it to launch HTTP floods and different network (OSI layer 3-4) DDoS assaults. When executing HTTP floods, Mirai bots hide behind the following default user-agents:
Mirai can execute attacks on the network layer, such as GRE IP and GRE ETH floods, SYN and ACK floods, STOMP (Simple Text Oriented Message Protocol) floods, DNS floods, and UDP floods. The botnet also has bypass capabilities, which allows it to evade security solutions. It’s also important to mention that Mirai’s code contains traces of Russian-language strings even though its C2 interface is in English.
In March 2019, the Federal Bureau of Investigation (FBI) identified the creators behind the Mirai botnet and arrested them. This led to a decrease in the botnet's activity, yet the open-source code was still available, allowing other groups to create their own versions of the malicious software.
In March 2023, it was reported by Akamai's SIRT security researchers that they had discovered a Golang based malware called HinataBot in their HTTP and SSH honeypots. According to Akamai, the sample stood out because of its large size and the fact that it was difficult to identify. The malware was named after a character from the anime series Naruto, with file names like "<Hinata-<OS>-<Architecture>".
Believed to have been created by former Mirai hackers, HinataBot has been seen exploiting known vulnerabilities to breach routers and servers, and then, as with Mirai, employing them to launch distributed DDoS attacks. HinataBot is spread using different techniques, such as taking advantage of open Hadoop YARN servers and weaknesses in Realtek SDK devices (CVE-2014-8361) and Huawei HG532 routers (CVE-2017-17215).
The operators behind HinataBot have been active since December 2022. Initially, they tried to use a generic Golang-based variant of the Mirai botnet, but then switched to their own custom malware on January 11, 2023. Akamai stated that HinataBot is still in development and is advancing in complexity. Recently discovered artifacts contain more modular features and improved security measures to make them more difficult to analyze.
Despite only being in development since January 2023, HinataBot is considered to be more powerful than Mirai. During its peak, Mirai was able to bombard its targets with an obscene amount of traffic, reaching up to 623 Gbit/s for the KrebsOnSecurity website and almost 1 Tbit/s against the French web host OVH. This colossal surge of data was made possible by a collection of approximately 145,000 bots, which can target a victim with an impressive degree of coordination.
After Akamai researchers conducted a brief 10-second trial assaults to assess the comparative strength of HinataBot, their findings revealed that "If the botnet comprised only 1,000 nodes," the resultant UDP flood would register about 336 Gbps per second.” With less than 1% of the resources, HinataBot can already generate traffic that is nearly as intense as the most brutal attacks of Mirai.
Most malware is written in C++ or C language. HinataBot however, is written in Golang - an example of how threat actors are taking new approaches to writing malware. Golang is a relatively new language and is more difficult for security professionals to reverse, one of the factors making it more attractive to malware authors. According to Akamai, attackers take advantage of Golang’s exceptional performance, capacity for multi-threading, its cross-compilation support for different architectures and operating systems, and its ability to add complexity during compilation, making it more difficult to reverse engineer resulting binaries.
Similar to other DDoS botnets, HinataBot connects with a C2 server to listen for instructions and launch attacks directed at a target IP address for a specific period of time. In the initial stages, HinataBot utilized various protocols including HTTP, UDP, TCP, and ICMP to carry out DDoS attacks, but the most recent version only utilizes HTTP and UDP. It is not clear as to why the former protocols are no longer used.
Image 2: Discovering the C2 Server
Source: Akamai
HinataBot is a prime example of the dynamic threat landscape, particularly relating to botnets. Malware creators are constantly innovating their use of implementation methods, programming languages, and distribution strategies.
Like Mirai, HinataBot exploits old vulnerabilities and uses brute-force to gain access to systems using weak passwords. This demonstrates the importance of having robust password policies and timely patching. Since attackers often seek easy targets with maximum gains, increasing the difficulty of their success can enhance the security of both your infrastructure and the internet.
Because DDoS attacks are inexpensive to launch, they are becoming more frequent and more sophisticated. In 2022, we witnessed an unprecedented surge in botnet and DDoS attacks, primarily due to inadequately secured IoT devices. [1]A recent study conducted by Imperva revealed a significant uptick in the frequency of layer 7 DDoS attacks, with a staggering 81% increase in attacks that reached a minimum of 500,000 requests per second (RPS) over the past year. The study also revealed a threefold increase in application layer DDoS attacks from Q1 to Q2 of 2022, again highlighting the alarming rate at which DDoS botnet attacks are escalating.
Many don’t realize that IoT devices are mini computers linked to other vulnerable devices. Mirai was successful with attacks due to vulnerable IoT devices. Threat actors know that most organizations do not regularly monitor IoT devices such as printers, office phone systems, security cameras, or scanners. This security loophole enables the threat actors to infiltrate the environment unnoticed and evade detection. While researchers do not believe that HinataBot will be another Mirai, some might say that it’s too soon to draw that conclusion.
“I don't think we're going to see a case of another Mirai, unless they get creative in how they're distributing and their infection techniques. We're not going to see another 70,000 or 100,000-node, Mirai-like threat from the Hinata authors under their current tactics, techniques, and procedures.”
On the contrary, Seaman also stated “It may just be an introductory phase, right? They're grabbing at low hanging fruit so far, without needing to go out and do anything really novel yet." - Chad Seaman Principal Security Researcher at Akamai
There are several things that you can do to successfully monitor IoT devices:
The aforementioned techniques, in conjunction with a robust IoT security plan, should give your organization better control over IoT devices.
[1] 81% Increase in Large-Volume DDoS Attacks | Imperva
IP Addresses
Ports
File Names
Recent Hashes
Uncovering HinataBot: A Deep Dive into a Go-Based Threat | Akamai
Breaking Down Mirai: An IoT DDoS Botnet Analysis (imperva.com)
What is a Botnet? (kaspersky.com)
An In-Depth Look at the Emotet Botnet (avertium.com)
Flash Notice: Emotet Botnet is Back with New Spam Campaigns (avertium.com)
IoT-Based DDoS Attacks Are Growing and Making Use of Common Vulnerabilities - CPO Magazine
Inside the infamous Mirai IoT Botnet: A Retrospective Analysis (cloudflare.com)
FBI: How we stopped the Mirai botnet attacks | TechTarget
What was the Mirai botnet | Malwarebytes
New GoLang-Based HinataBot Exploiting Router and Server Flaws for DDoS Attacks (thehackernews.com)
Mirai Botnet Attack IoT Devices via CVE-2020-5902 (trendmicro.com)
Heightened DDoS Threat Posed by Mirai and Other Botnets | CISA
Mirai Hackers Use Golang to Create a Bigger, Badder DDoS Botnet (darkreading.com)
What is the Mirai Botnet? | Cloudflare
Defending Against IoT DDoS and Botnet Attacks: Tips for SLGs | StateTech (statetechmagazine.com)
2022 in review: DDoS attack trends and insights - Microsoft Security Blog
Defending against a growing botnet and DDoS epidemic in 2023 | VentureBeat
Mirai Botnet Shows Just How Vulnerable the IoT Really Is – IoT Security Foundation
Related Resource:
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.
COPYRIGHT: Copyright © Avertium, LLC and/or Avertium Tennessee, Inc. | All rights reserved.