Everything You Need to Know About the Data Extortion Group, Snatch
executive summary
Snatch, a data extortion group also previously named Truniger after the group’s founder, has been named as a ransomware operation to watch by the U.S. Cybersecurity and Infrastructure Security Administration (CISA) and by the Federal Bureau of Investigation (FBI). The group works with many partners and affiliates, with their primary goal being financial gain via data leaks.
Over the last couple of years, Snatch has demonstrated a consistent ability to evolve its tactics, taking advantage of emerging trends within the cybercriminal landscape and drawing lessons from the successes of various ransomware strains.
During this period, the threat group has focused its attention on several critical infrastructure sectors, including Information Technology, Food and Agriculture, and the Defense Industrial Base sector. Let’s take a look at Snatch’s tactics and techniques, as well as recommendations on how organizations can protect themselves from this kind of threat actor.
tir snapshot
- Emerging in 2018, Snatch operates under a ransomware-as-a-service (RaaS) model, but focuses on data extortion more than they focus on ransomware.
- At times, Snatch encrypts files but the group also exfiltrates sensitive data, increasing the pressure on victims of pay a ransom.
- According to intel provided by RedSense, Snatch is a long-standing threat group that has been under surveillance by RedSense analysts since 2019, operating under the moniker "truniger".
- One of the distinguishing features of Snatch is its use of Safe Mode to bypass traditional endpoint protection mechanisms.
- In addition to its technical capabilities, Snatch is known for its aggressive tactics, including victim shaming through the publication of stolen data on both clearnet and dark web platforms.
- In December 2019, Snatch was reported to be using a new ransomware variant which reboots the devices it infects into Windows Safe Mode to disable AntiVirus (AV) solutions. This variant also immediately encrypts files once the system loads.
- Throughout 2021, Snatch remained largely inactive, with only sporadic incidents involving the group being documented.
- Snatch emerged from a period of dormancy starting January 15, 2023 and on April 6, 2023, Snatch appears to collaborate with the alleged Chinese APT group Nokoyawa.
- Despite a brief hiatus in May 2023, Snatch returned aggressively, targeting new victims, and retroactively documenting past attacks.
- As of now, Snatch does not explicitly identify itself as a ransomware group, despite using a blend of ransomware tactics and data exfiltration.
- It's possible that the group is setting the stage for a ransomware-as-a-service collective to be an umbrella for all their extortion activities.
- To effectively safeguard data from Snatch and mitigate the risk of a threat actor leveraging remote access tools, organizations need to prioritize cybersecurity best practices.
snatch
Snatch, emerging in 2018, operates under a ransomware-as-a-service (RaaS) model, but focuses on data extortion more than they focus on ransomware. The group uses a sophisticated approach to extorting victims by combining data theft with encryption. At times, Snatch encrypts files but the group also exfiltrates sensitive data, increasing the pressure on victims to pay a ransom. The group behind Snatch, known as "Snatch Team," leverages various tools and techniques to achieve its objectives, demonstrating a high level of technical sophistication.
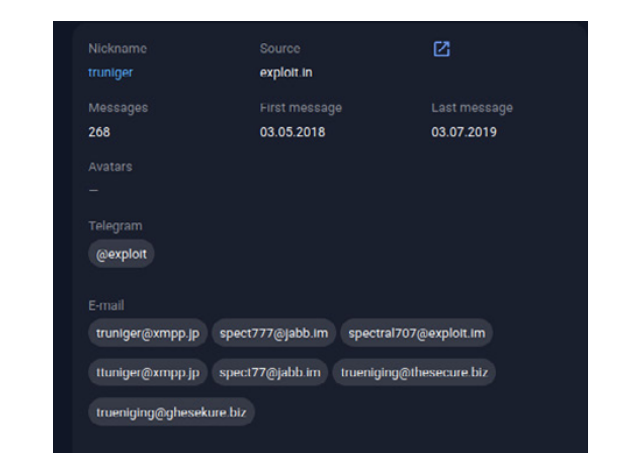
According to intel provided by RedSense, Snatch is a long-standing threat group that has been under surveillance by RedSense analysts since 2019, operating under the moniker "truniger." This alias includes Russian-speaking actors primarily engaged as access brokers on the underground forum called “exploit[.]in.” Following its notable April 2019 attack on the German IT services firm CityComp, the group has consistently evolved over the past four years.
Image 1: Truniger's Original Exploit Profile
Source: RedSense
One of the distinguishing features of Snatch is its use of Safe Mode to bypass traditional endpoint protection mechanisms. By forcing infected Windows machines to reboot into Safe Mode, Snatch bypasses security software that typically remains inactive in this mode. This tactic highlights the adaptability and ingenuity of the threat actors behind Snatch, who continuously innovate to evade detection and maximize the impact of their attacks.
In addition to its technical capabilities, Snatch is known for its aggressive tactics, including victim shaming through the publication of stolen data on both clearnet and dark web platforms. This tactic aims to pressure organizations into paying the ransom by threatening to expose sensitive information to the public. The combination of data theft, encryption, and public shaming makes Snatch a threat that organizations must actively defend against.
timeline of attacks
In the summer of 2019, Snatch carried out a series of significant attacks, initially identified by analysts at RedSense. These attacks included the sale of 36 devices from a Canadian KIA dealership for $3000 USD, as well as unauthorized access to 170 devices within an Italian network of healthcare clinics, along with 13 GB of associated data.
Snatch facilitated the compromise of these victims' data and initial access privileges through the Exploit forum. According to information shared by users on Exploit, the leaked data, offered for free, contained copies of insurance checks, bank transfer details, and personally identifiable information (PII) of numerous Italian citizens.
RedSense researchers began to observe early patterns in the group's target verticals, notably Entertainment, Government, and Insurance sectors. The group's victims were spread across various countries, including Italy, Canada, Israel, Japan, Poland, France, China, and Australia.
On June 8, 2019, the group advertised Remote Desktop Protocol (RDP) access on the forum, targeting the Municipal Government of an unnamed Italian city.
In December 2019, Snatch was reported to be using a new ransomware variant which reboots the devices it infects into Windows Safe Mode to disable AntiVirus (AV) solutions. This variant also immediately encrypts files once the system loads. Although this is sometimes still erroneously reported in news reports as Snatch’s primary attack methodology, encryption-based malware is no longer being used by the group.
In the summer of 2020, despite a relative lack of communication from the group, more incidents involving Snatch ransomware attacks surfaced. Snatch reverted to using RDP brute-forcing as their initial method of attack. They then swiftly progressed from this initial breach to deploying a Meterpreter reverse shell and RDP proxy on a Domain Controller, allowing them to encrypt all victim systems in less than five hours.
Throughout 2021, Snatch remained largely inactive, with only sporadic incidents involving the group being documented. However, in November 2021, the group garnered attention when they were mentioned in an FBI advisory alongside other threat groups targeting Native American tribal entities since 2016, including REvil, Bitpaymer, Ryuk/Conti, and Cuba.
Towards the end of 2021, on December 21st, Snatch reappeared in the spotlight after claiming responsibility for an attack on the automotive company Volvo, resulting in the theft of research and development data. Throughout 2022, Snatch was linked to several new ransomware variants. Despite being primarily focused on extortion, the frequency of their attacks remained limited.
Snatch emerged from a period of dormancy starting January 15, 2023. During this period until April, they only targeted one additional victim, the French aerospace company Hemeria, on February 17, 2023. Their activity was sporadic, leading to near loss of access to their Telegram channel multiple times due to prolonged periods of inactivity.
On April 6, 2023, Snatch appears to collaborate with the alleged Chinese APT group Nokoyawa, according to RedSense's investigation. This suspicion arises from private chats referencing a partnership and overlapping victims featured on both groups' public blogs. Notably, Snatch targets critical infrastructure entities (Information Technology, Food and Agriculture, and the Defense Industrial Base sectors), a departure from its usual strategy.
Despite a brief hiatus in May 2023, Snatch returned aggressively, targeting new victims, and retroactively documenting past attacks. The group's approach now includes publicly exposing victim information to pressure for ransom payments.
tactics + techniques
Snatch uses a variety of tactics and techniques to infiltrate and compromise target networks. The initial attack vector often involves brute-force attacks against vulnerable services such as RDP allowing the threat actors to gain unauthorized access to network resources. Once inside the network, Snatch utilizes privilege escalation techniques to obtain administrative credentials and move laterally across the environment.
To maximize the impact of their attacks, Snatch conducts extensive reconnaissance to identify high-value targets and critical data repositories within the victim's network. This reconnaissance phase may involve the exfiltration of sensitive information to assess its value and potential for extortion. By understanding the network topology and security posture of the victim organization, Snatch can tailor its attack strategy for maximum effectiveness.
In addition to data theft, Snatch will sometimes use encryption to render critical files and systems inaccessible to the victim. The ransomware payload is designed to encrypt files using strong cryptographic algorithms, making it virtually impossible to recover data without the decryption key. To further complicate recovery efforts, Snatch may also delete Volume Shadow Copies and other backup mechanisms, preventing victims from restoring their files from backup.
Throughout the attack lifecycle, Snatch threat actors maintain persistence on compromised systems to ensure continued access and control. This may involve the installation of backdoors or remote access tools, allowing the threat actors to re-establish a foothold in the event of detection or remediation efforts by the victim organization. By maintaining persistence, Snatch can prolong its presence within the victim's network and continue its extortion activities over an extended period.
To evade detection and hinder forensic analysis, Snatch ransomware uses various evasion and obfuscation techniques. This includes the use of legitimate system administration tools and techniques, such as PowerShell and Windows Management Instrumentation (WMI), to blend in with normal network traffic and avoid detection by security solutions. Additionally, Snatch may employ anti-analysis measures to thwart reverse engineering attempts and hinder the development of effective countermeasures by security researchers and vendors.
tor site + telegram
Snatch runs a victim shaming website on both the clearnet and the dark web, publicly disclosing stolen data and ransom demands to pressure victims into paying. They also engage victims through email and Tox for ransom negotiations and extortion.
Operating on the Tor network allows Snatch to hide their activities from law enforcement, as their dark web site conceals their identities and locations. In addition to the dark web, Snatch uses encrypted platforms like Telegram for secure communication, aiding in evading detection during ransom negotiations and extortion attempts.
attack on kraft heinz
At the end of 2023, the Kraft Heinz Company investigated claims made by the Snatch regarding the theft of internal data, although the company stated that its systems were functioning normally. Snatch allegedly breached Kraft Heinz's IT infrastructure in August 2023 but did not specify the data obtained.
While the extent of the cyberattack remained unconfirmed, the gang employed double-extortion tactics, encrypting systems and threatening to leak or sell the stolen data unless a ransom was paid. During this time, the FBI issued warnings about Snatch's tactics. Recent victims included the Florida Department of Veterans Affairs and Modesto, California.
avertium's recommendations
As of now, Snatch does not explicitly identify itself as a ransomware group, despite using a blend of ransomware tactics and data exfiltration. It's possible that the group is setting the stage for a ransomware-as-a-service collective to be an umbrella for all their extortion activities. Therefore, attributing a particular malware or ransomware to the group, or classifying it as a ransomware group, remains challenging.`
To effectively safeguard data from Snatch and mitigate the risk of a threat actor leveraging remote access tools, organizations need to prioritize cybersecurity best practices:
- Audit and Monitor Remote Access Tools: Regularly audit remote access tools to identify authorized software and review logs for abnormal usage patterns.
- Secure Remote Access: Utilize security software to detect instances of remote access software being loaded only in memory.
- Enforce the use of authorized remote access solutions only from within the network over approved methods like virtual private networks (VPNs) or virtual desktop interfaces (VDIs).
- Additionally, block inbound and outbound connections on common remote access software ports and protocols at the network perimeter.
- Implement Application Controls: Manage and control the execution of software by implementing application controls. This includes allowlisting remote access programs and preventing the installation and execution of unauthorized software.
- Strictly Limit RDP Usage: Limit the use of Remote Desktop Protocol (RDP) and other remote desktop services. Audit network systems for RDP usage, close unused ports, and enforce account lockouts after a specified number of login attempts.
- Strengthen Credential Management: Reduce the threat of credential compromise by placing domain admin accounts in protected user groups, refraining from storing plaintext credentials in scripts, and implementing time-based access for accounts set at the admin level and higher.
Best Practices to follow:
- Maintain Offline Backups: Keep offline backups of critical data to minimize disruption and data loss during ransomware attacks.
- Enforce Password Policies: Require all accounts with password logins to comply with password policies, including longer passwords, hashed storage, and multiple failed login attempt lockouts.
- Enable MFA: Implement phishing-resistant multifactor authentication (MFA) for all services where possible, particularly for webmail, VPNs, and accounts accessing critical systems.
- Keep Systems Updated: Regularly update operating systems, software, and firmware to minimize exposure to cybersecurity threats, prioritizing patching known exploited vulnerabilities in internet-facing systems.
- Segment Networks: Segment networks to prevent the spread of ransomware, controlling traffic flows between subnetworks and restricting adversary lateral movement.
How Avertium is Protecting Our Customers
It’s important to get ahead of the curve by being proactive with protecting your organization, instead of waiting to put out a massive fire. Avertium can provide the following services to help keep your organization safe from Snatch Ransomware:
- Fusion MXDRis the first MDR offering that fuse together all aspects of security operations into a living, breathing, threat-resistant XDR solution. By fusing insights from threat intelligence, security assessments, and vulnerability management into our MDR approach, Fusion MXDR offers a more informed, robust, and cost-effective approach to cybersecurity – one that is greater than the sum of its parts.
- Avertium aligns your Cybersecurity Strategy with your business strategy, ensuring that your investment in security is also an investment in your business. Our Cybersecurity Strategy service includes:
- Strategic Security Assessments - Strengthening your security posture begins with knowing where your current program stands (NIST CSF, Security Architecture, Business Impact Analysis, Sensitive Data Inventory, Network Virtualization and Cloud Assessment).
- Threat Mapping – Leverage Avertium’s Cyber Threat Intelligence, getting a more informed view of your most likely attack scenarios (Threat Assessment and MITRE ATT&CK).
- Cyber Maturity Roadmap - Embrace a comprehensive, quantifiable, and well-organized approach to establishing and continuously enhancing your cybersecurity resilience (Policy + Procedure Development, Virtual CISO (VCISO), Training + Enablement, Tabletop Exercises, and Business Continuity + Disaster Recovery Plan).
- Minimizing the impact of a successful ransomware attack requires detecting it as early in the attack as possible. A Security Information and Event Management (SIEM) system can help an organization to accomplish this. Avertium offers a comprehensive SIEM-based approach that increases the potential for detecting a ransomware infection before it deploys. SIEM provides a holistic overview of a company’s IT environment from a single point of view in terms of its specific security events, empowering teams to detect and analyze unusual behavior.
- Note: We highly value your feedback. Kindly spare a moment to complete our feedback form, allowing us to enhance our services for our valued customers.
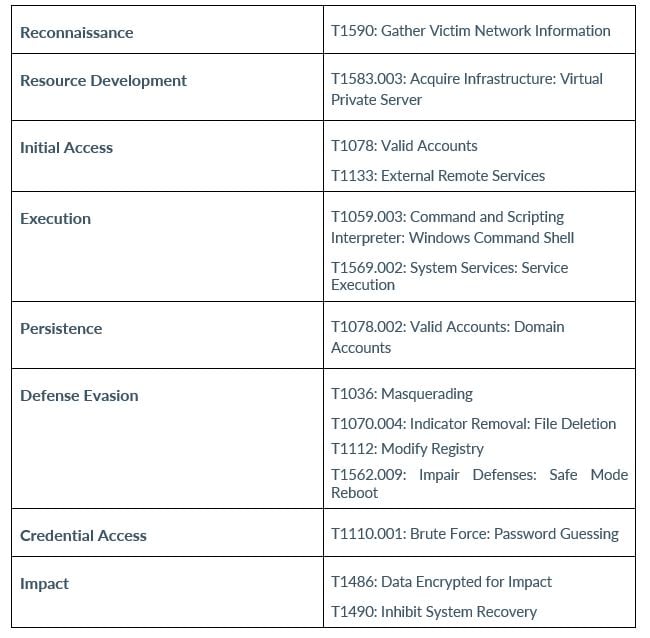
MITRE MAP
INDICATORS OF COMPROMISE (IoCs)
SHA256
- 329f295b8aa879bedd68cf700cecc51f67feee8fd526e2a7eab27e216aa8fcaa
- ab6b0d00ba8f8553c015743b9da8761a9b1fca750d3f73bda573a8fbc47dafa1
- 28125dae3ab7b11bd6b0cbf318fd85ec51e75bca5be7efb997d5b950094cd184
- 8c9fab558b3e9e21936a91422d9e2666f210c5fd7d9b0fd08d2353adb64a4c00
- 63c2c1ad4286dbad927358f62a449d6e1f9b1aa6436c92a2f6031e9554bed940
- 80cc8e51b3b357cfc7115e114cecabc5442c12c143a7a18ab464814de7a66ab4
- 36a4311ef332b0b5db62f8fcabf004fdcfbbde62f791839a8be0314604d814c4
- ae9cdbb717625506ed0df7af153dc2741395655aeb1da2f91079e3ea616af6a1
- eebc57e9e683a3c5391692c1c3afb37f3cb539647f02ddd09720979426790f56
- fe8ba1eaf69b1eba578784d5ab77e54caae9d90c2fb95ad2baaaef6b69a2d6cb
- 78816ea825209162f0e8a1aae007691f9ce39f1f2c37d930afaf5ac3af78e852
- d22b46ea682838e0b98bc6a1e36fd04f0672fe889c03d227cdeb5dcc5d76ae7c
- d0ddc221b958d9b4c7d9612dd2577bec35d157b41aa50210c2ae5052d054ff33
- 0ce4c4af321ff02928aacf105f03dead87e85003080586615755f278770f5adb
- c0f506e98f416412b3a9dcd018341afab15e36b15bac89d3b02ff773b6cc85a6
- 5f24536e48f406177a9a630b0140baadff1e29f36b02095b25e7e21c146098bb
- ebcded04429c4178d450a28e5e190d6d5e1035abcd0b2305eab9d29ba9c0915a
- e8931967ed5a4d4e0d7787054cddee8911a7740b80373840b276f14e36bda57d
Domain
- Mydatassuperhero[.]com
- snatch6brk4nfczg[.]onion
- mydatasuperhero[.]com
- snatch24uldhpwrm[.]onion
- imboristheblade@protonmail[.]com
- newrecoveryrobot@pm[.]me
- jimmtheworm@dicksinmyan[.]us
- doctor666@cock[.]li
- doctor666@mail[.]fr
Supporting Documentation
RedSense Intelligence Operations (2023). Snatch/Snatch Team: Threat Actor Profile [pdf document]. Retrieved from Yelisey Bohuslavskiy, February 21, 2024, Snatch Ransomware
joint-cybersecurity-advisory-stopransomware-snatch-ransomware_0.pdf (cisa.gov)
‘Snatch’ Ransom Group Exposes Visitor IP Addresses – Krebs on Security
A Closer Look at the Snatch Data Ransom Group – Krebs on Security
Kraft Heinz downplays Snatch ransomware crew's claims • The Register
Snatch ransomware reboots PCs into Safe Mode to bypass protection – Sophos News
Snatch ransomware - what you need to know | Tripwire
Dark Web Profile: Snatch Ransomware - SOCRadar® Cyber Intelligence Inc.
Snatch gang ‘consistently evolved’ in targeting multiple industries, feds say (therecord.media)
Critical Infrastructure Organizations Warned of Snatch Ransomware Attacks - SecurityWeek
US Government in Snatch Ransomware Warning - Infosecurity Magazine (infosecurity-magazine.com)
Snatch Ransomware Group Targeting Numerous Industries (speartip.com)
Snatch Ransomware Explained - CISA Alert AA23-263A (picussecurity.com)
Snatch Ransomware Reboots PCs into Safe Mode - AlienVault - Open Threat Exchange
FBI, CISA Issue Joint Warning on 'Snatch' Ransomware-as-a-Service (darkreading.com)
APPENDIX II: Disclaimer
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Avertium) is ultimately responsible for assessing and meeting Client's own compliance responsibilities. This report does not constitute a guarantee or assurance of Client's compliance with any law, regulation or standard.